What is Just in Time VM Access?
Just in time VM access enables you to lock down your VMs in the network level by blocking inbound traffic to specific ports. It enables you to control the access and reduce the attack surface to your VMs, by allowing access only upon a specific need.
How does it work?
Upon a user request, based on Azure RBAC, Security Center will decide whether to grant access. If a request is approved, Security Center automatically configures the NSGs to allow inbound traffic to these ports, for the requested amount of time, after which it restores the NSGs to their previous states.
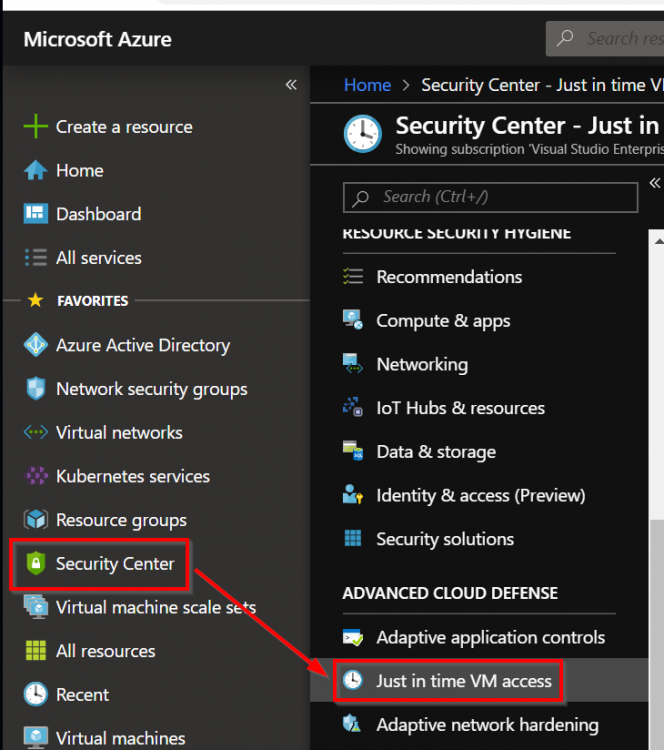
Let’s see how to configure Just in Time VM Access. First, navigate to the “Security Center” blade and click “Just in Time VM Access”:
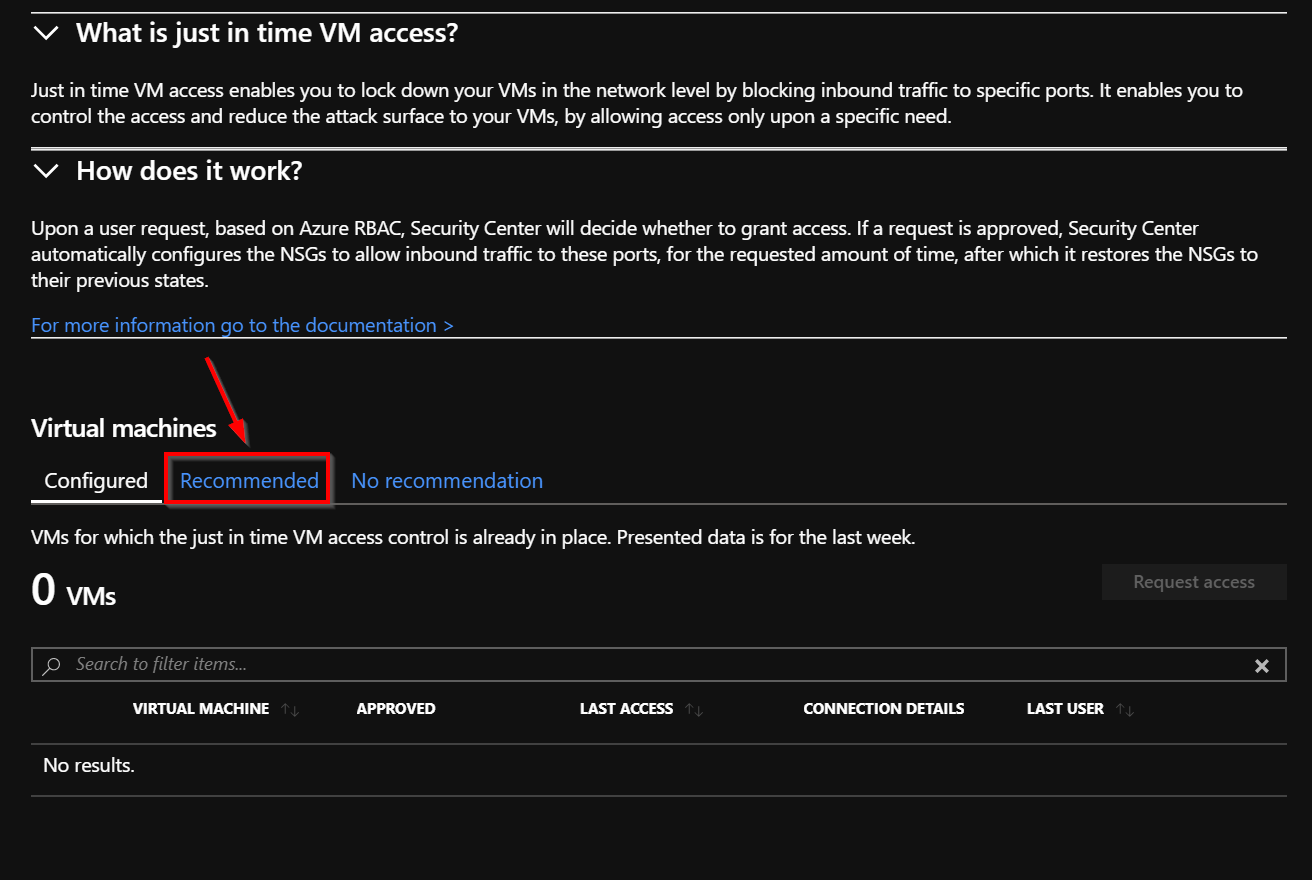
By default, no Virtual Machines are configured for JIT VM Access. You need to enable the feature, so select the “Recommended” tab:
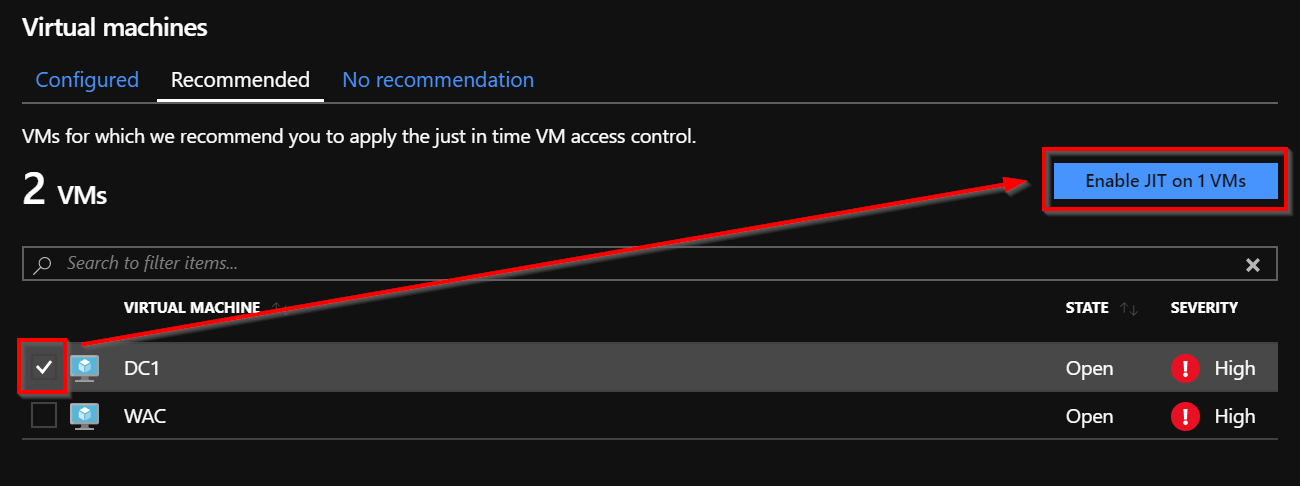
You should see your Virtual Machines in the following list. Select the VM for which the Just in Time VM Access must be enabled:
To enable the feature, you must configure the ports for which the JIT VM Access will be applicable. By design, there are some recommended ports:
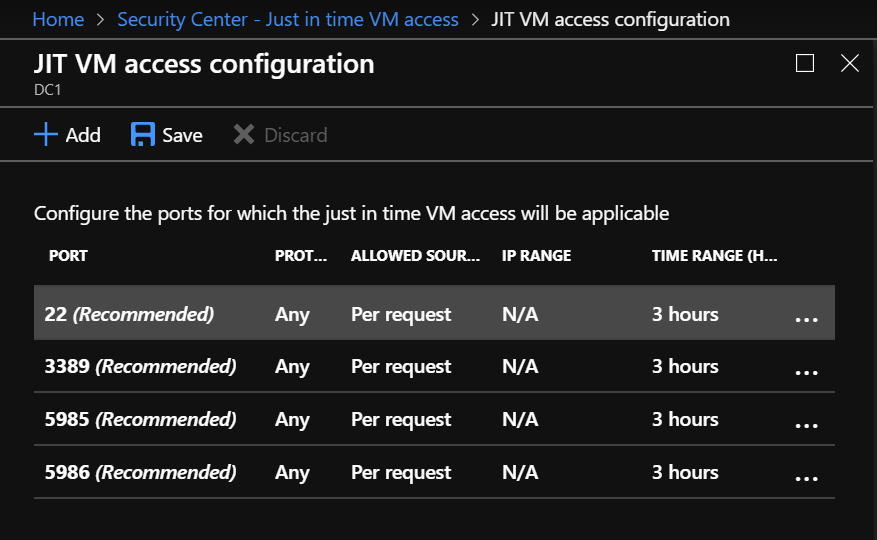
In my case, I removed these ports and click “Add” to add a new one:
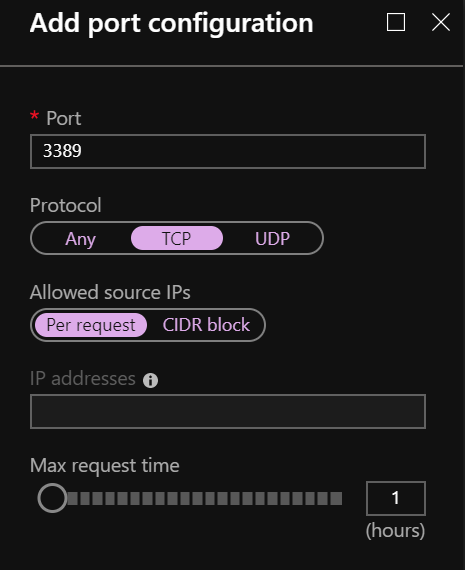
You can configure a max request time, which is the time remote access will be available for this protocol.
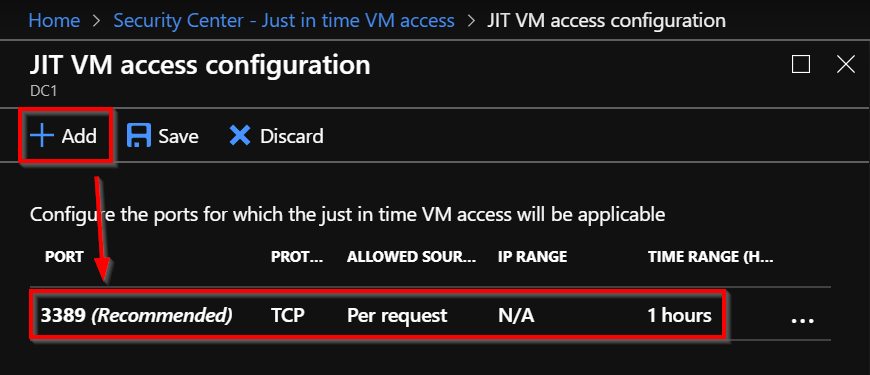
Once the port is added to the configuration, you can notice in the “Configured” tab that your Virtual Machine is visible:
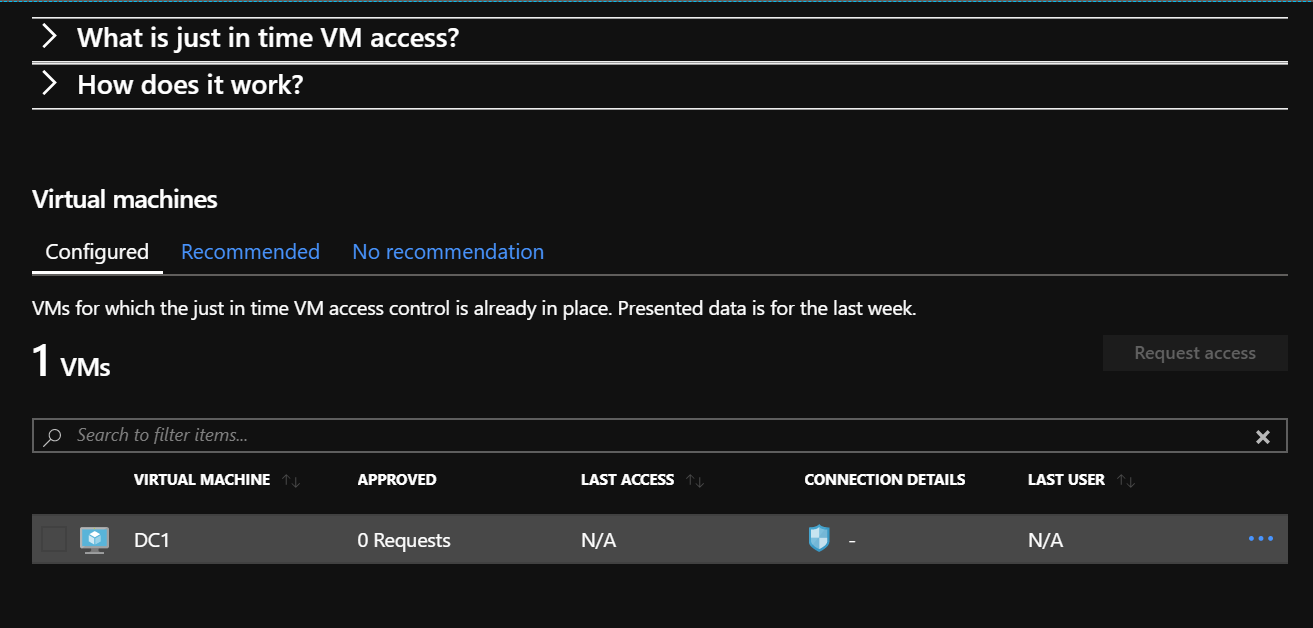
What does it mean? You can now try to run a remote session to this Virtual Machine through the RDP protocol but it will not work because 3389 is not allowed in the NSG.
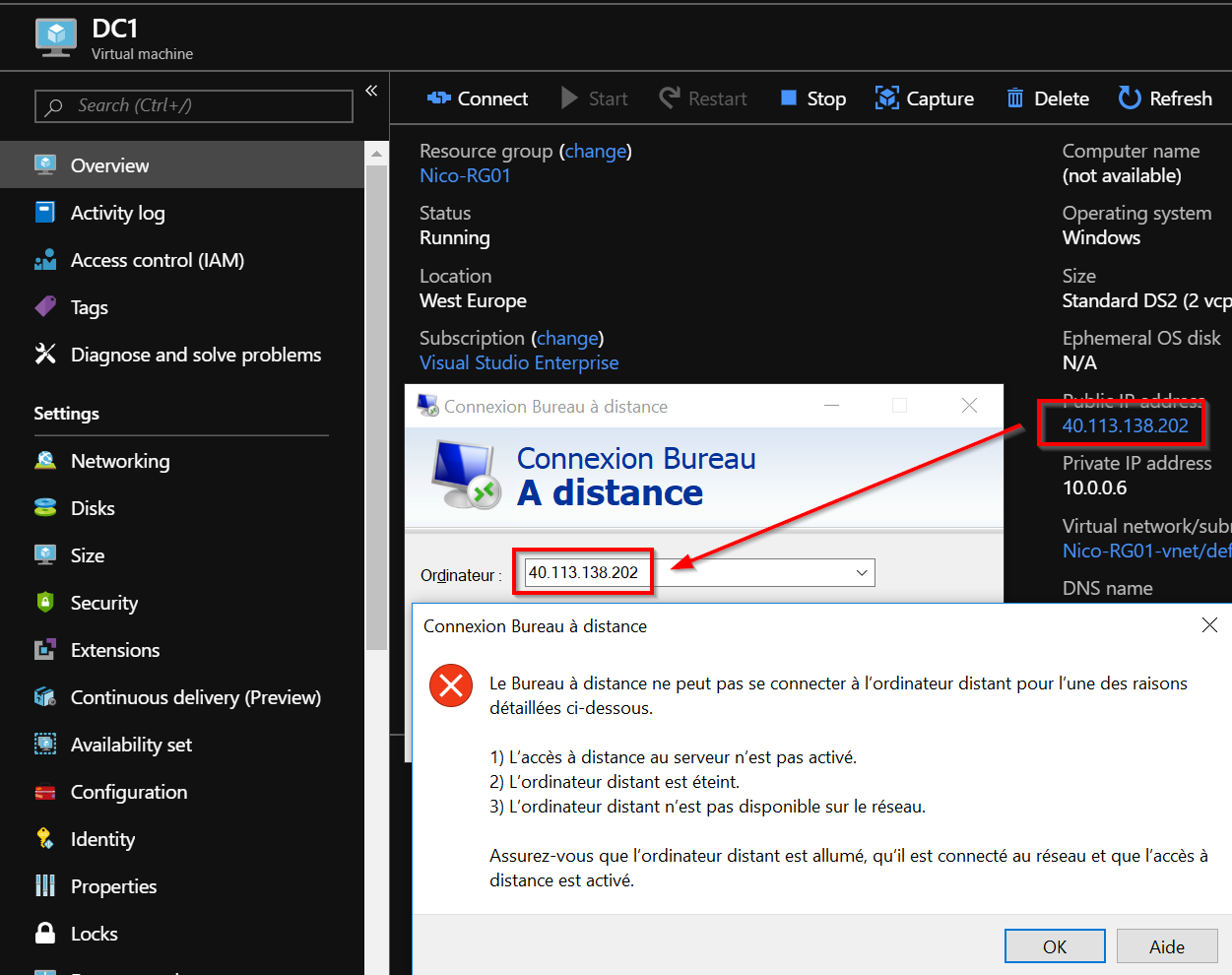
In order to allow access through 3389, we need to request an access. Go back to the security center blade and click “Request Access”:
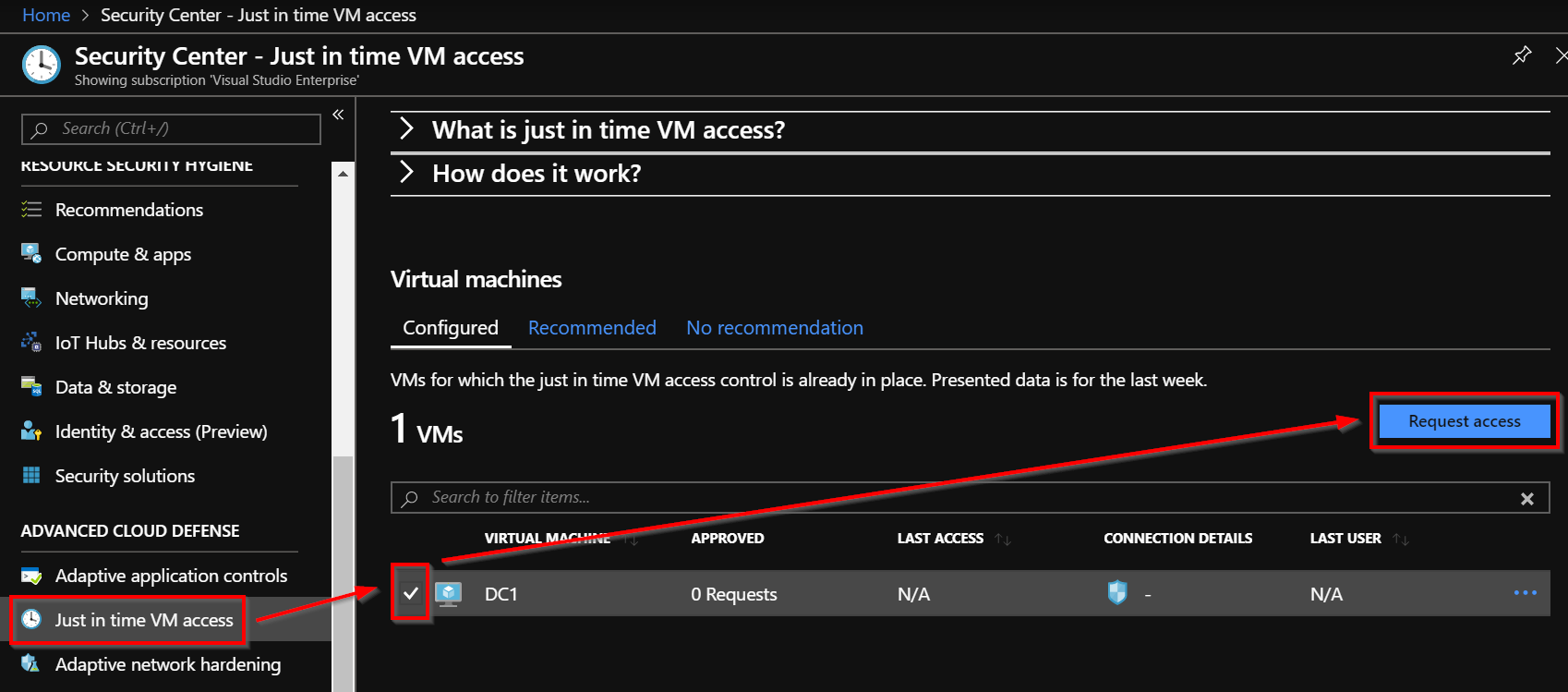
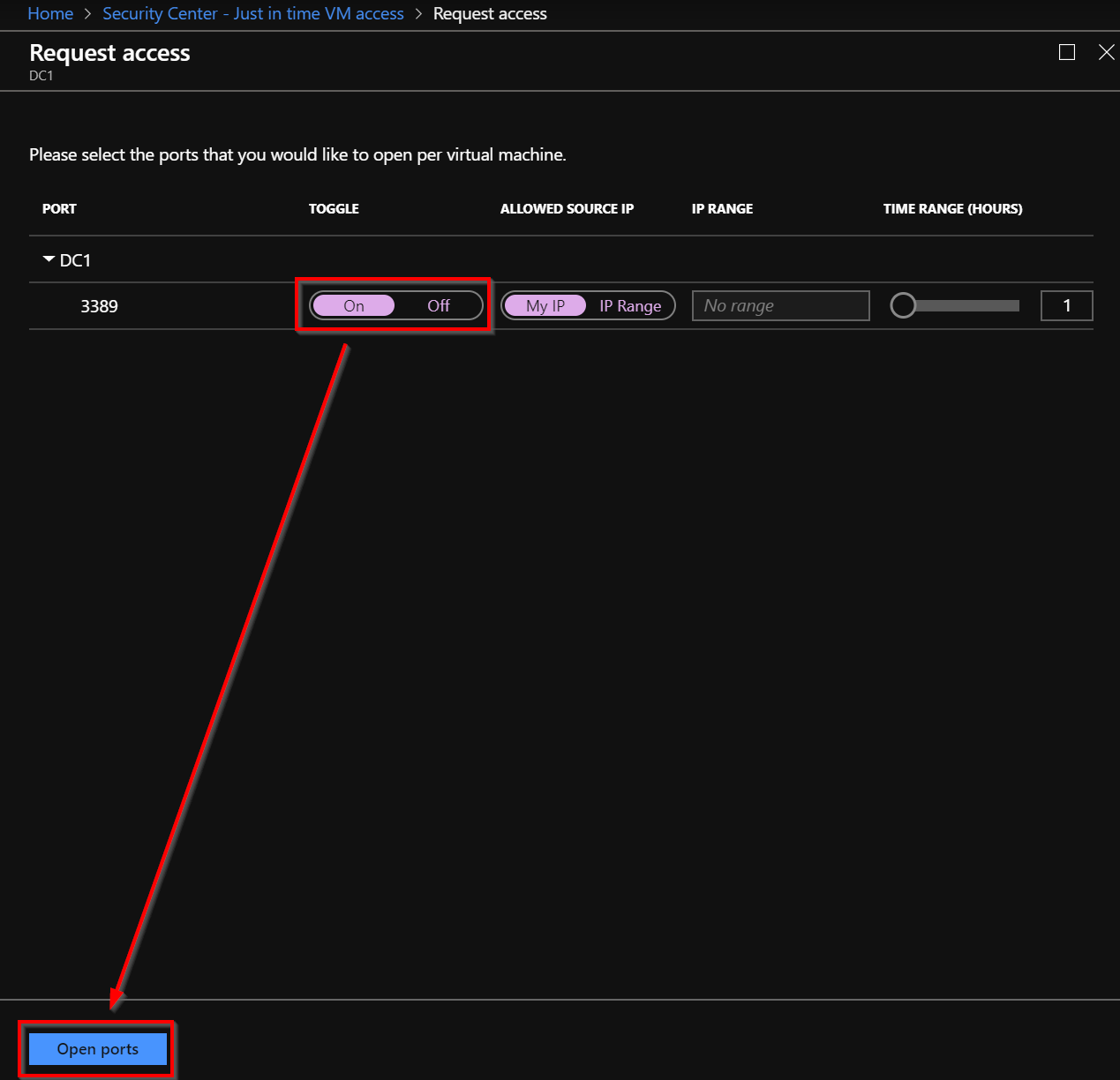
Now, you can open the port and you also can allow an IP range for 1 hour.
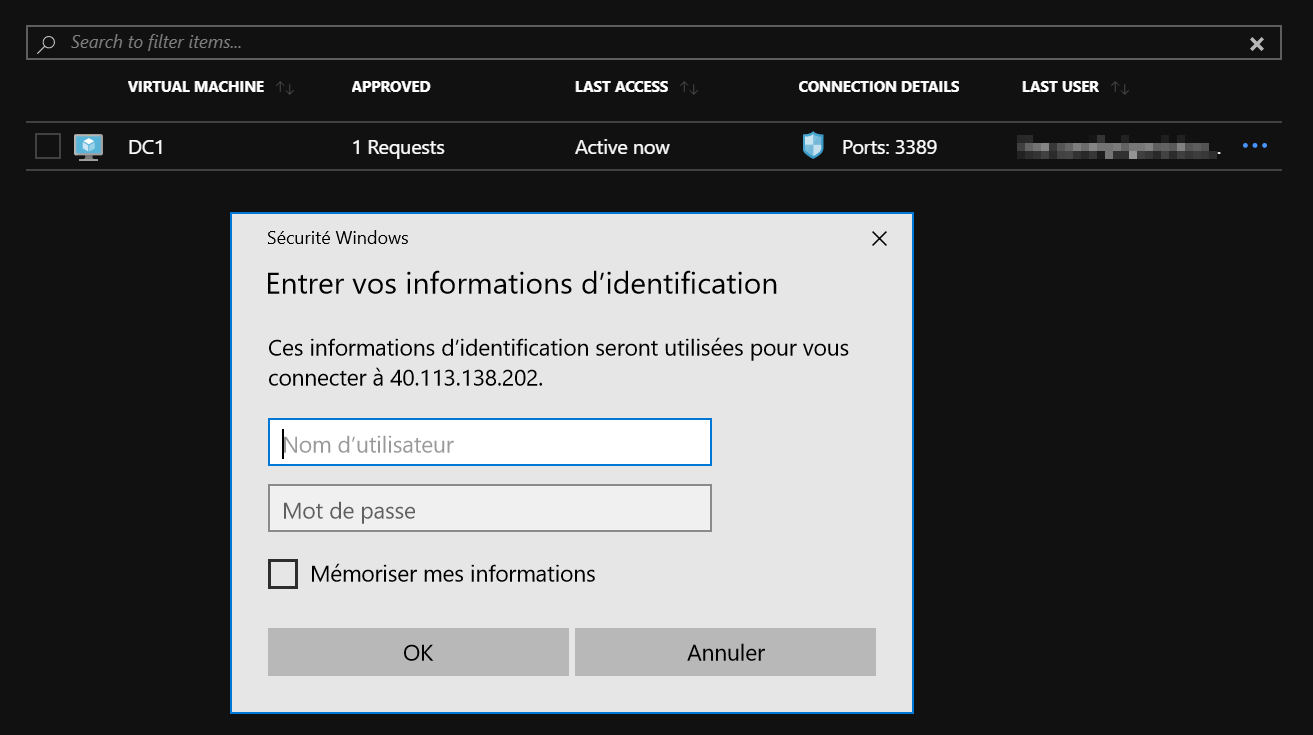
Let’s try once again to run the RDP session to this Virtual Machine, and now it works because 3389 is allowed in the NSG.
Conclusion
Azure Just in Time is a great and helpful feature that allow or deny access to your machines in Azure. Thanks to JIT VM Access, accessing to your Azure servers will be more secure.


