Azure Private Link is a new feature for PaaS services that allows you to create a private endpoint in your virtual network. Azure Private Link enables you to access Azure PaaS Services over a Private Endpoint in your virtual network. So, it means that the traffic between your virtual network and the service traverses over the Microsoft backbone network, eliminating exposure from the public Internet.
Benefits:
- A private IP for your PaaS resources
- Traffic to PaaS resources traverses the Microsoft network.
- Users access is restricted to the specific resource
- Private endpoints can be created to resources in different regions to the virtual network and even different tenants
Azure Private Link enables you to access Azure PaaS Services such as:
- Azure Storage
- Azure Cosmos DB
- Azure SQL Database
How does Azure Private Link work?
Below is the diagram from Microsoft Documentation:
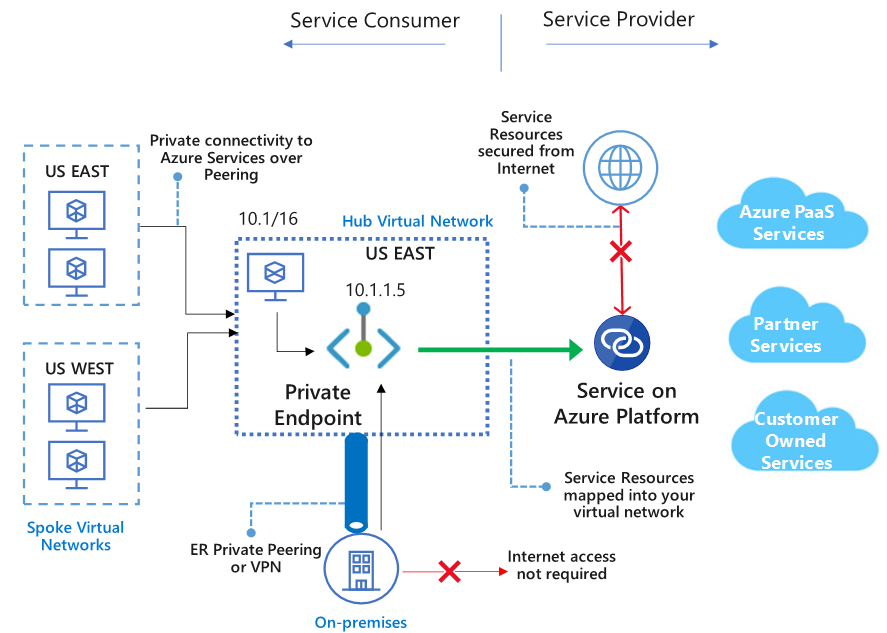
Azure Private Link creates an endpoint with a private IP address, so your traffic is flowing inside your Virtual Network and does not require NSG rules allowing outbound traffic beyond your virtual network.
For those of you who are wondering the difference between Private Link and Service endpoint, here is the key:
Service endpoints provide a way to lock down access to PaaS resources to a virtual network. However, you are still accessing a public endpoint. With service endpoints, you are also only locking down access to a service, not to a specific resource.
Getting Started
To set up a Private Link, first, we will create a Storage Account. Open the Azure Portal, and click “Create a Resource”:
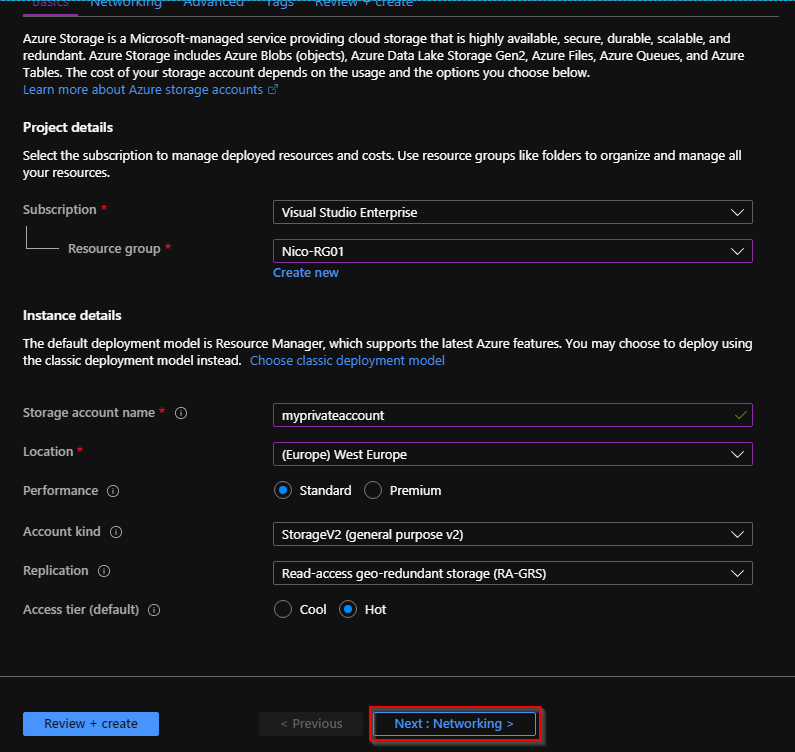
Enter a name, select the resource group and the location for this storage account, then click “Next”
In this tab, select “Private endpoint” and click “Add” in order to create a private endpoint:
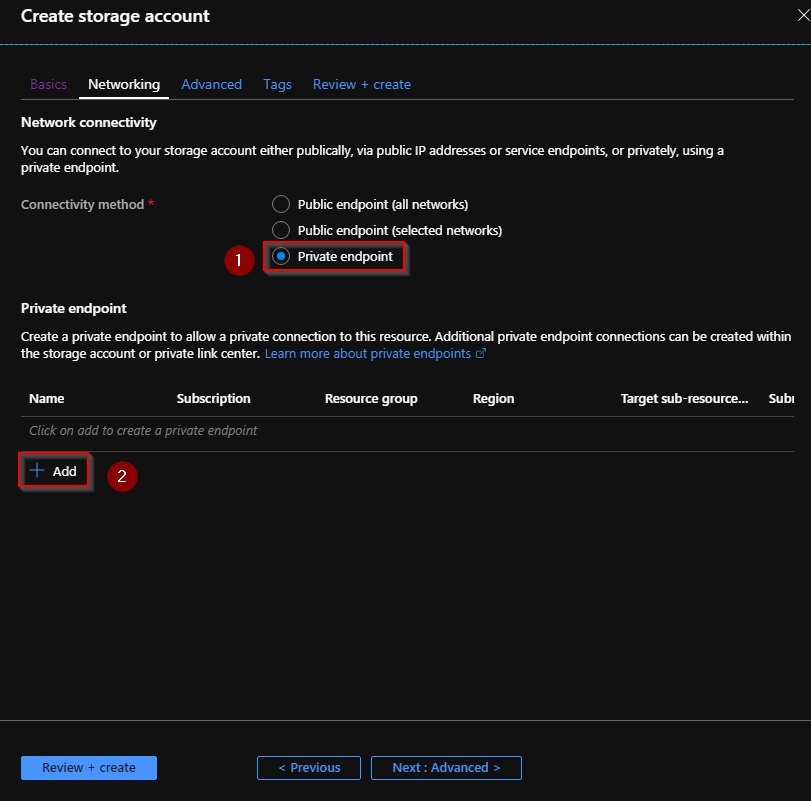
A new blade appears to create a private endpoint. Enter the following information:
- Subscription
- Resource Group
- Location
- Name
- Storage sub-resource
- Virtual Network and Subnet: Note that NSG will be disabled for this private endpoint.
- Private DNS Zone: You can integrate with an Azure Private DNS zone. This will allow you to resolve the address of the resource (see below), to its private IP.
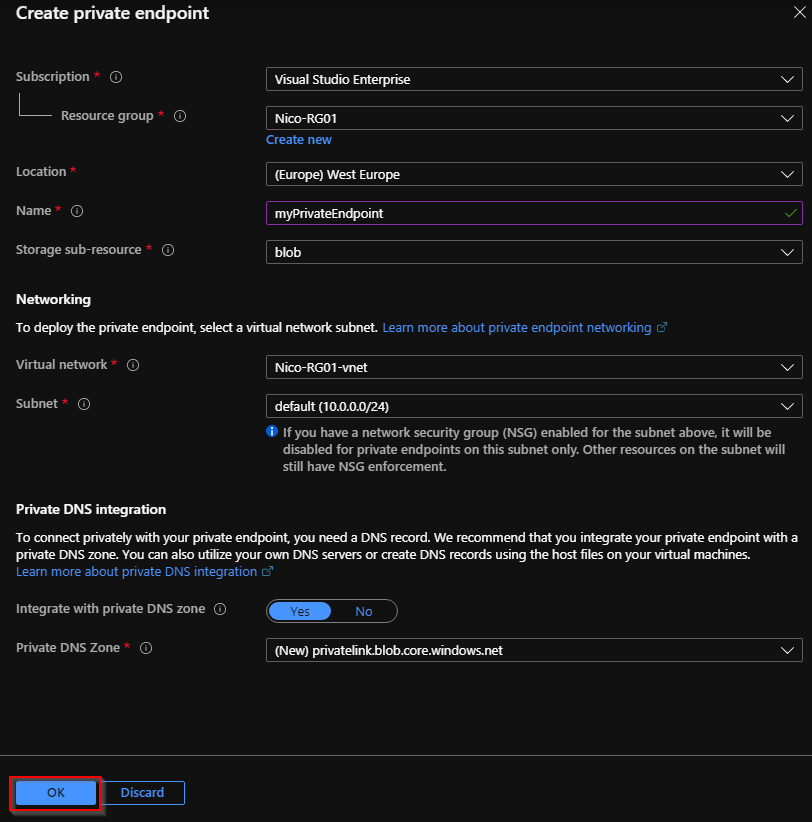
Click “OK” and confirm that your private endpoint is visible:
You can validate the wizard
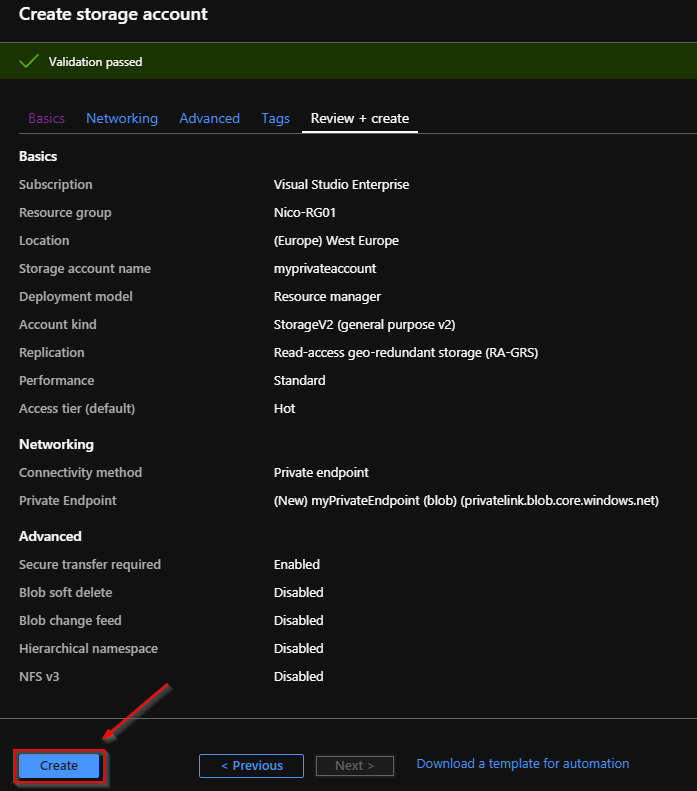
In this guide, I created the private link from the storage account wizard, but you also can create the private link from the Azure Portal, especially if you want to create a private link for other PaaS resources:
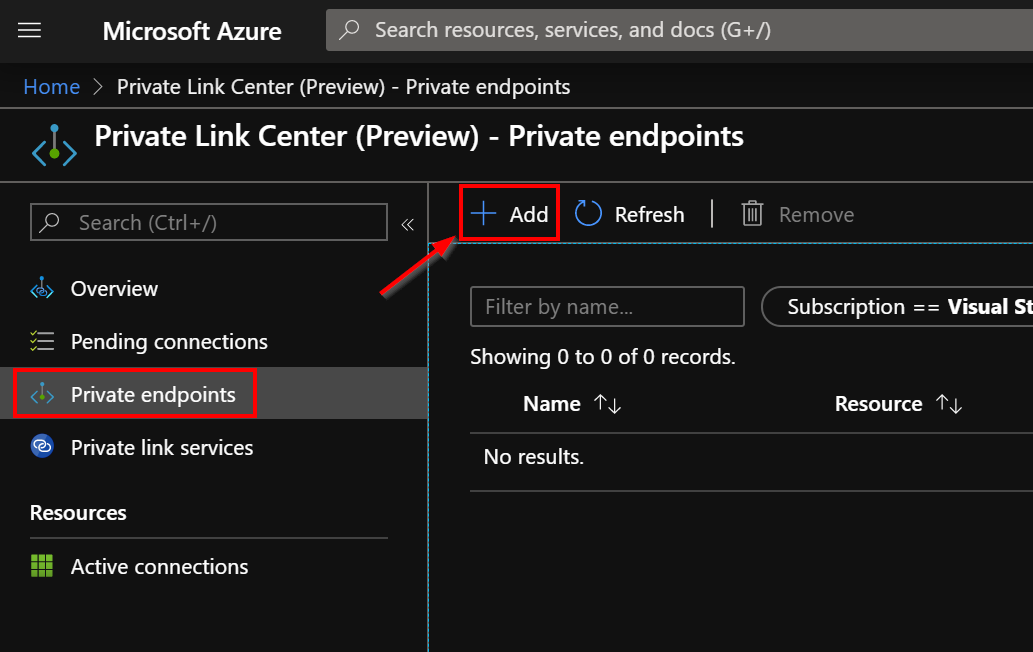
Now, we can test the private link. Copy the connection string for the storage account previously created:
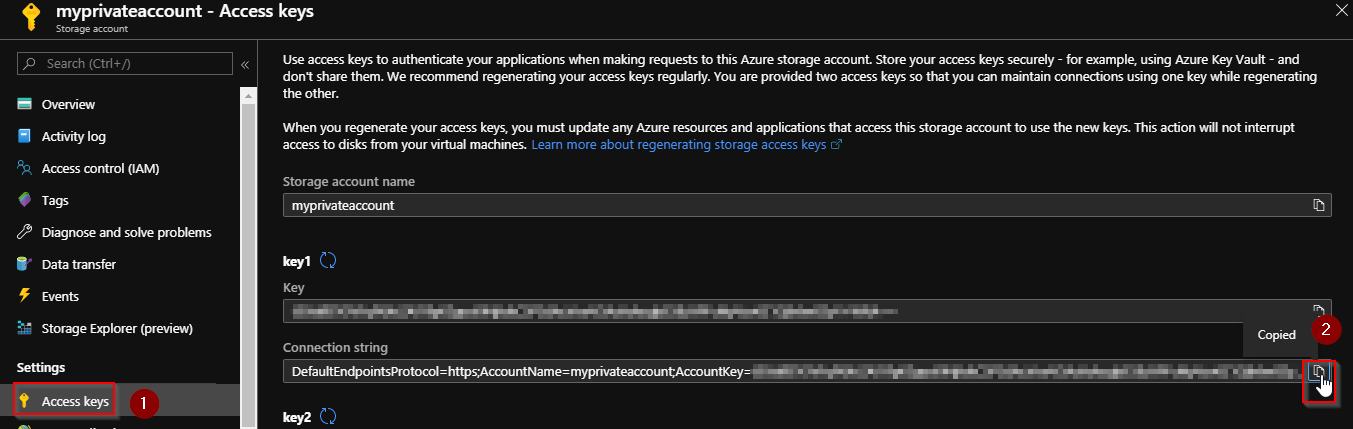
Start a Virtual Machine located in the same Virtual Network and run the following command:
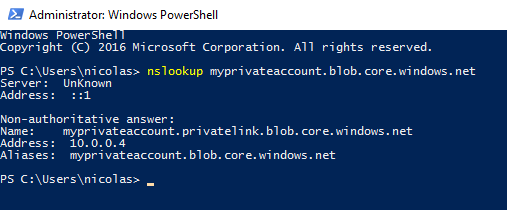
The output should display a private IP Address for the storage account. Now, I will download Azure Storage Explorer in order to test the connection using the private IP address.

Open Azure Storage Explorer from the Virtual Machine and paste the connection string that you copied previously:
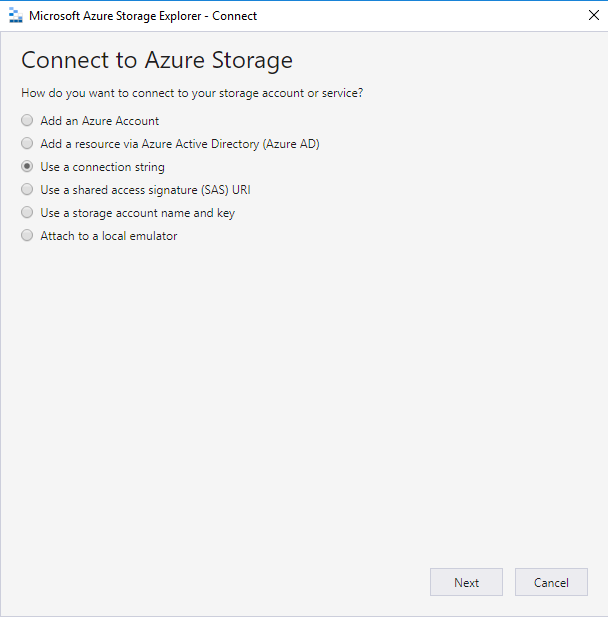
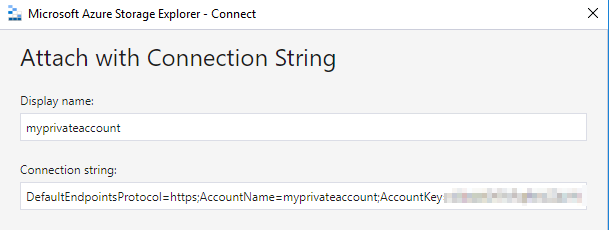
The connection should be in success and you should see the content of your Azure Storage Account:
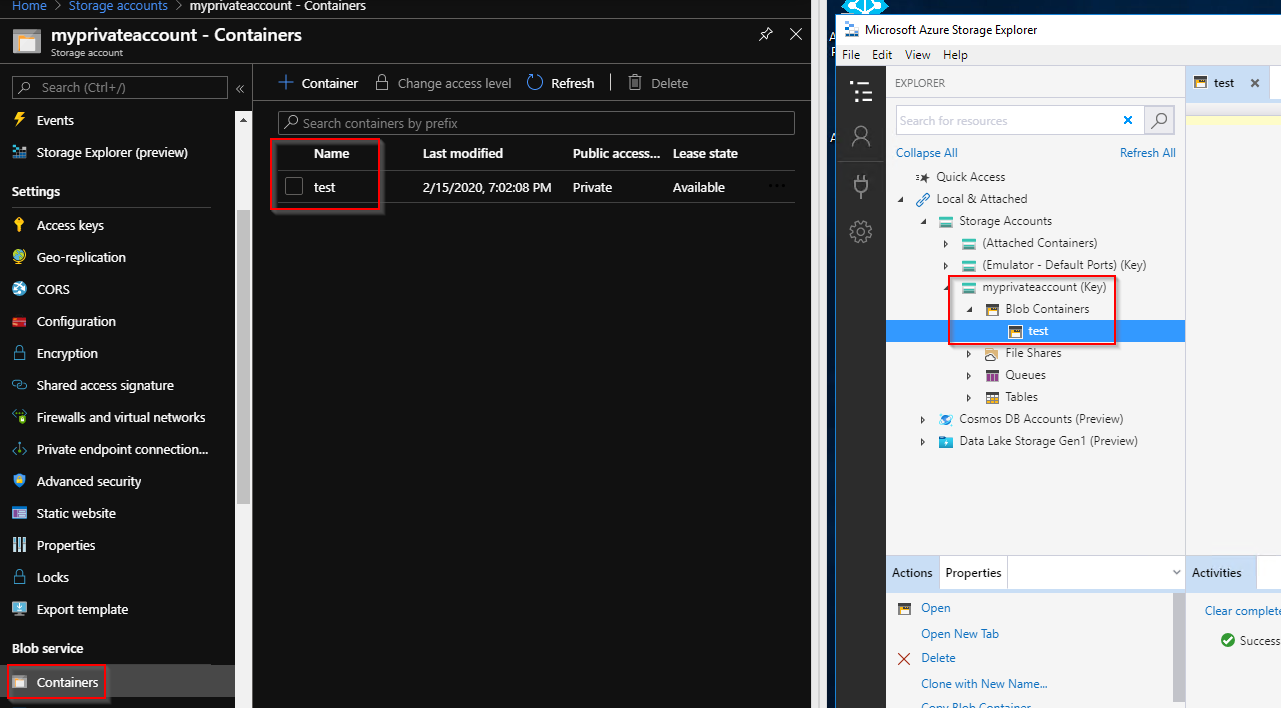
Conclusion
Thanks to the Azure Private Link, we can easily reduce the exposure of your PaaS services to the internet and secure the traffic between your network and Azure.


