After the first article on how to deploy AKS we will check how to use an Application Gateway as an Ingress controller and a WAF. Why? To protect your websites 😊
To start, be sure to deploy your AKS cluster.
Now, you can deploy your Application Gateway, in Azure, with WAFv2 SKU:
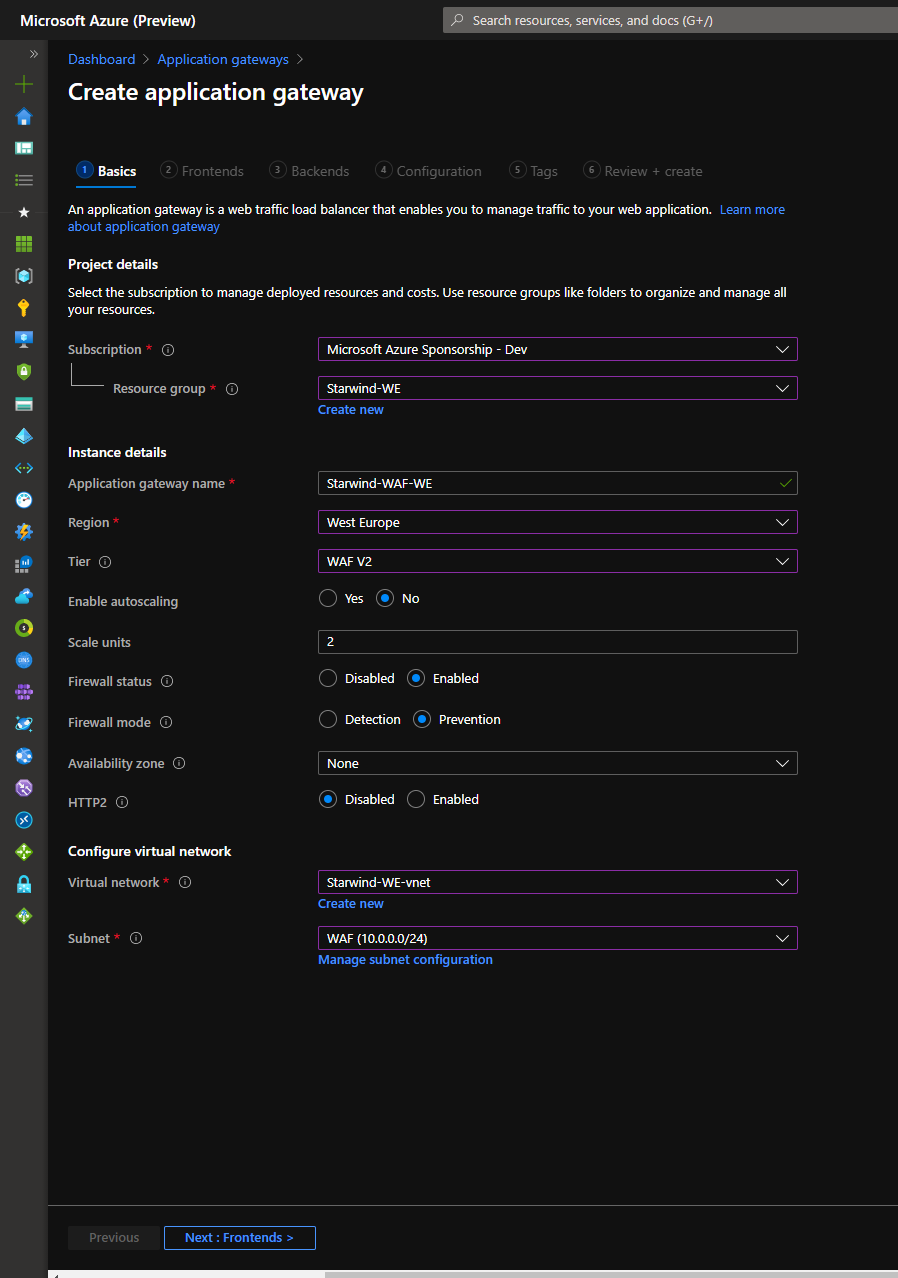
Create a public IP for this WAF:
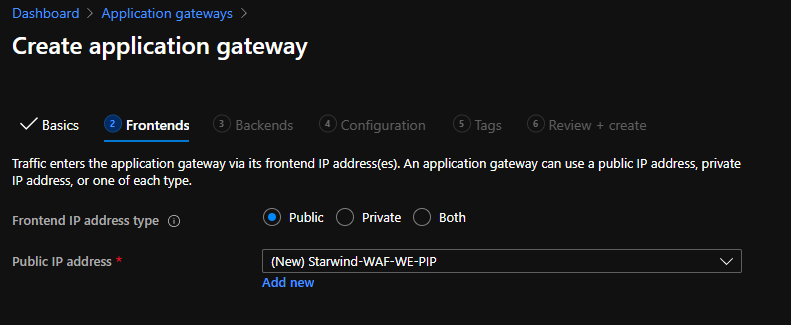
Create an empty backend pool (it will not be used, because of the integration as Ingress):
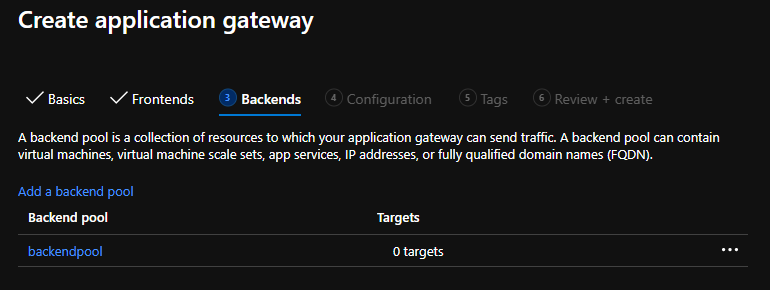
Create a routing rule1, with HTTP protocol (it will not be used, because of the integration as Ingress):
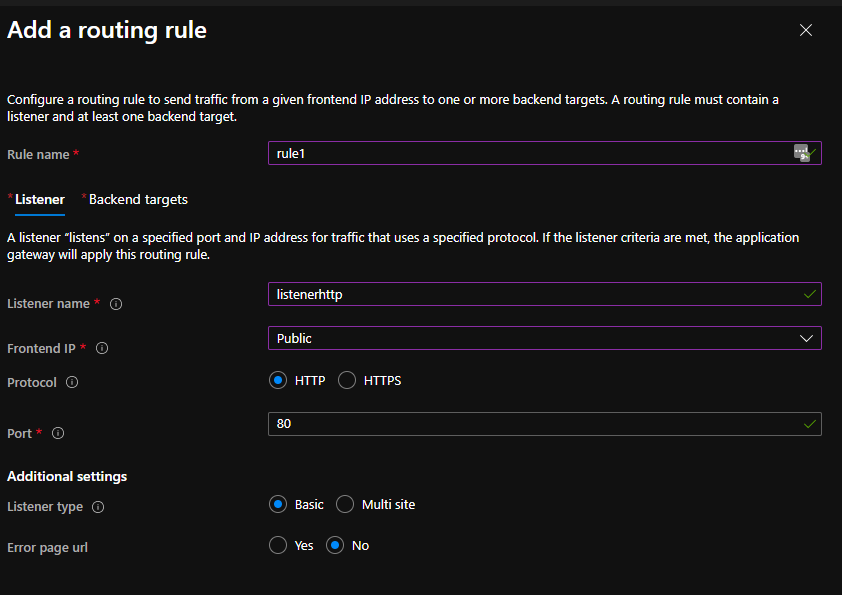
And the backend target (it will not be used, because of the integration as Ingress):
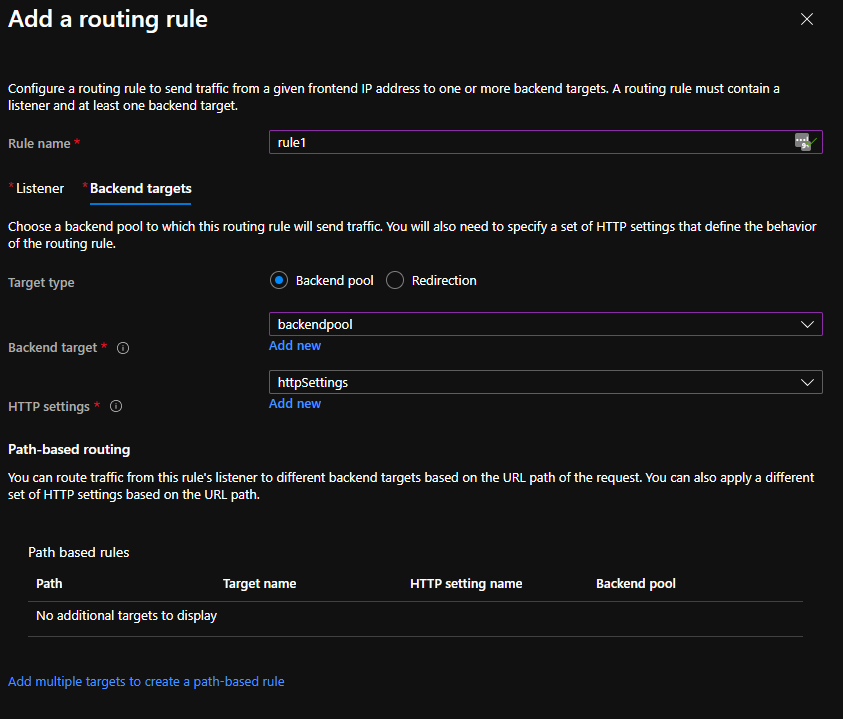
You will have this:
When the App Gateway has been deployed, go to your Azure AD, and get the name of your Service Principal:
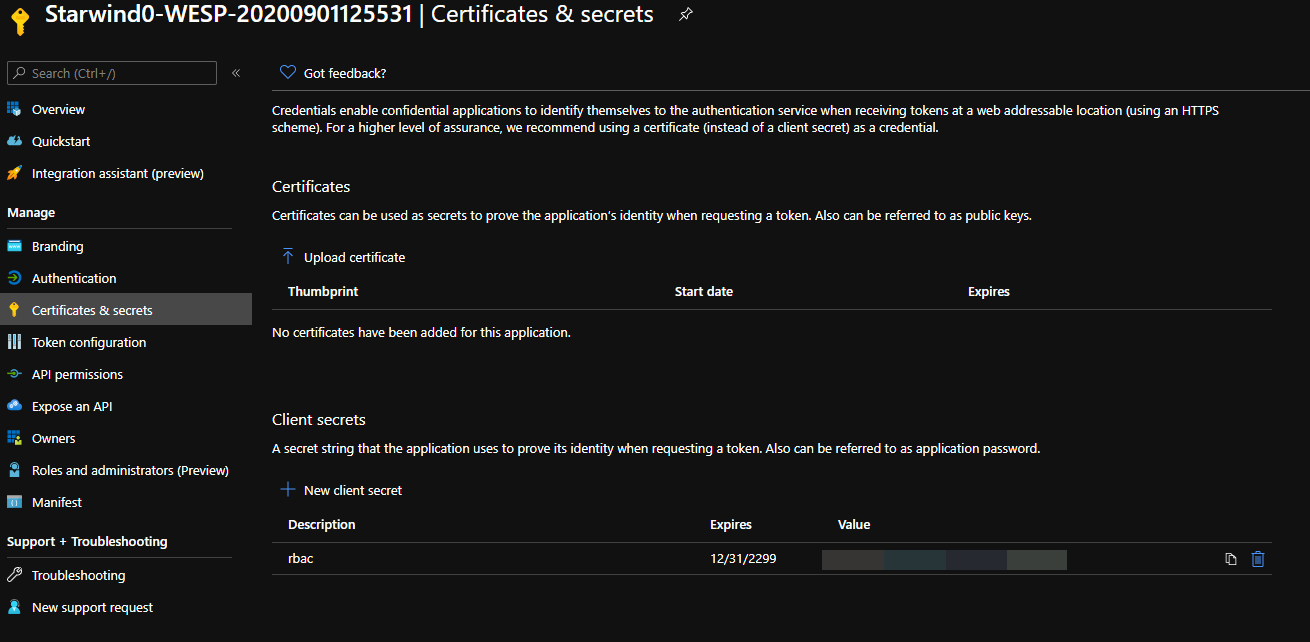
Get the application ID, and create a new secret:
Give to this Azure AD Service Principal, the Contributor right on the AKS Resource Group:
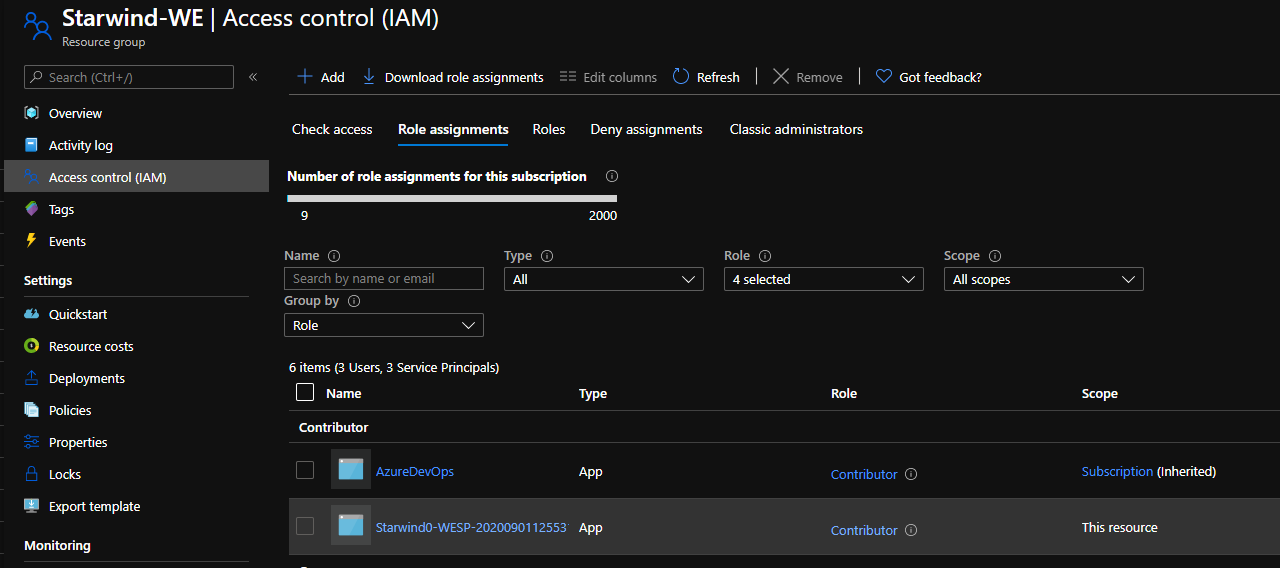
Now, connect to your AKS Cluster:
|
Execute the following command, to apply the deployment template rbac:
|
Convert your Azure AD Service principal secret to base 64:
|
Now, create 2 files, with the following content:
01-aadpodidentity-sp.yaml
|
02-aadpodidentitybinding.yaml
|
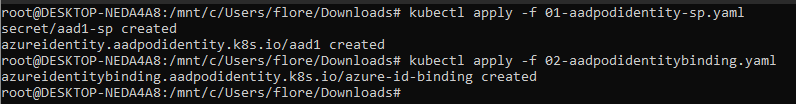
And apply them:
|
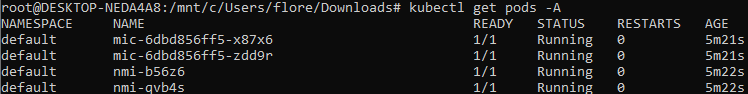
Pods are now running:
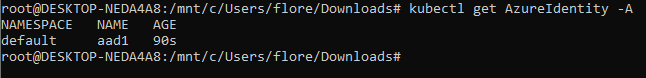
Now, we will convert the following connection string, to base64:
|
Copy this code with your values and go to https://www.base64encode.org/. Paste it and click to Encode. And get the result:
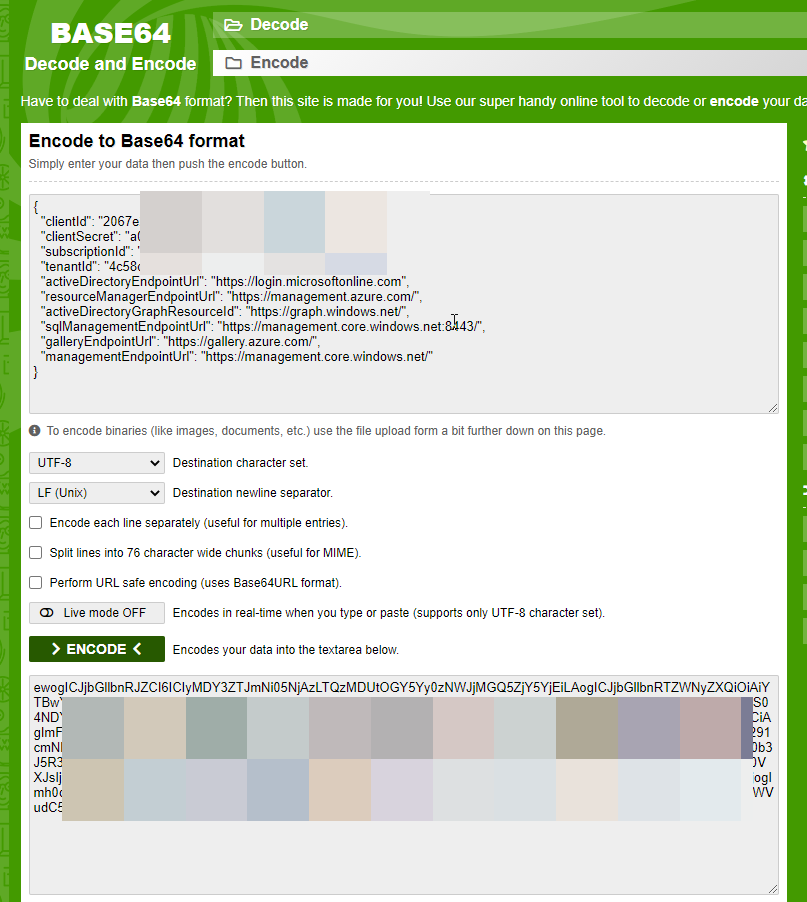
Create a new file, 04-helm-config.yaml, and paste the code, by replacing values, with your own:
|
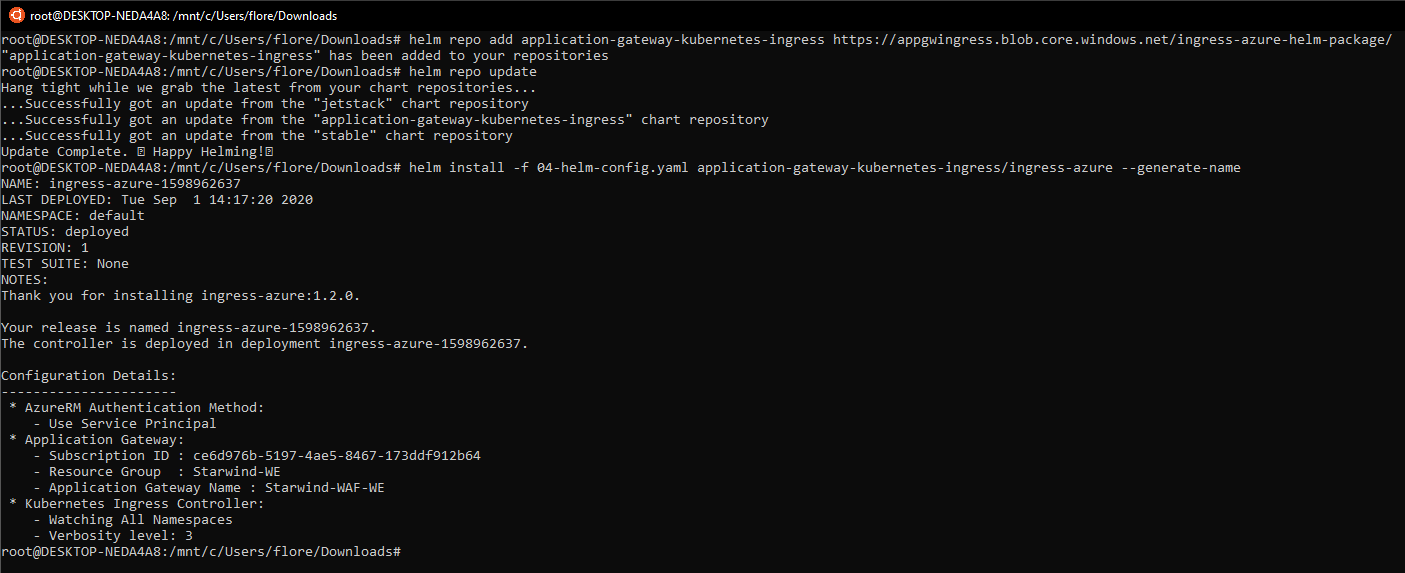
It’s time to apply this configuration, with helm:
|
The ingress pod has been deployed:
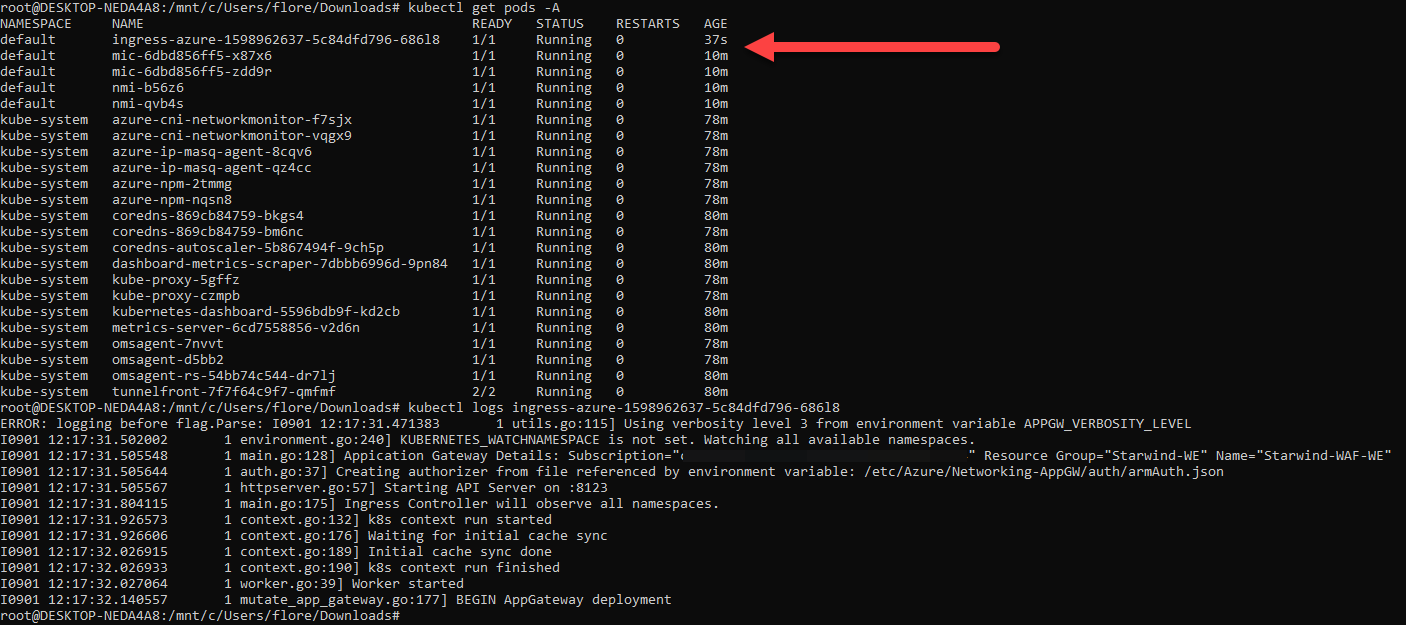
We will deploy a test application:
|
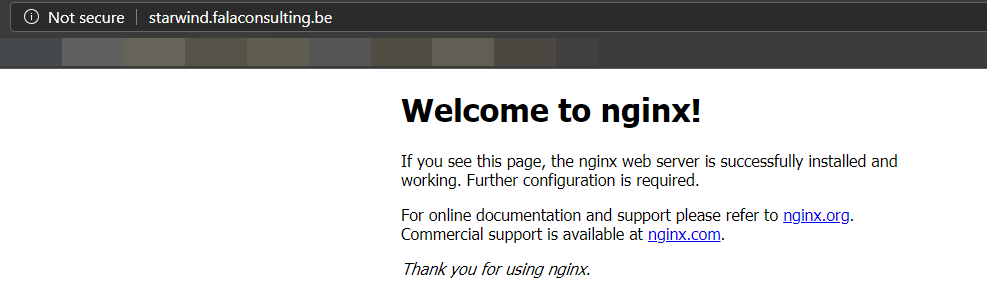
I created a DNS entry, starwind, that points to the public IP of my Application gateway. After few seconds, the deployment is finished on the Application Gateway:
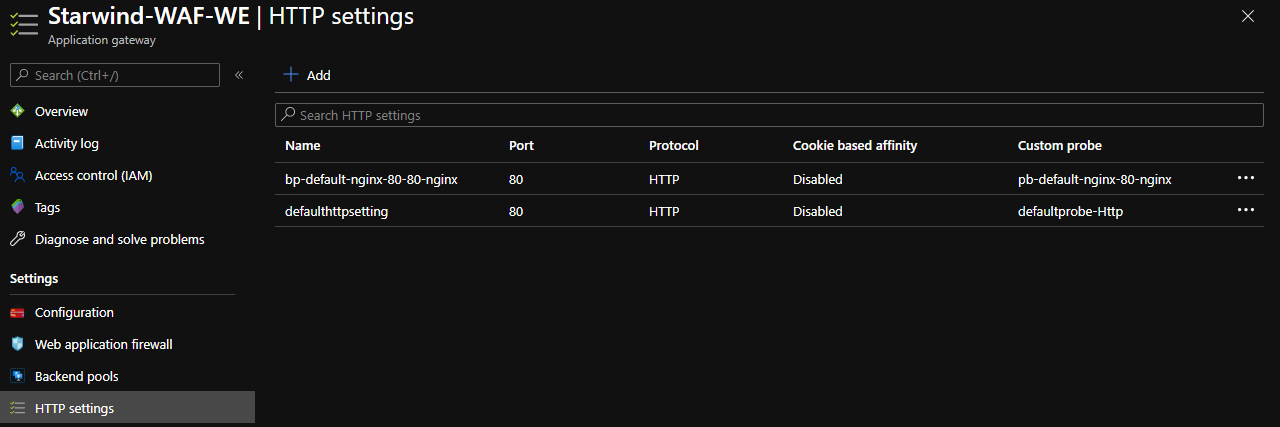
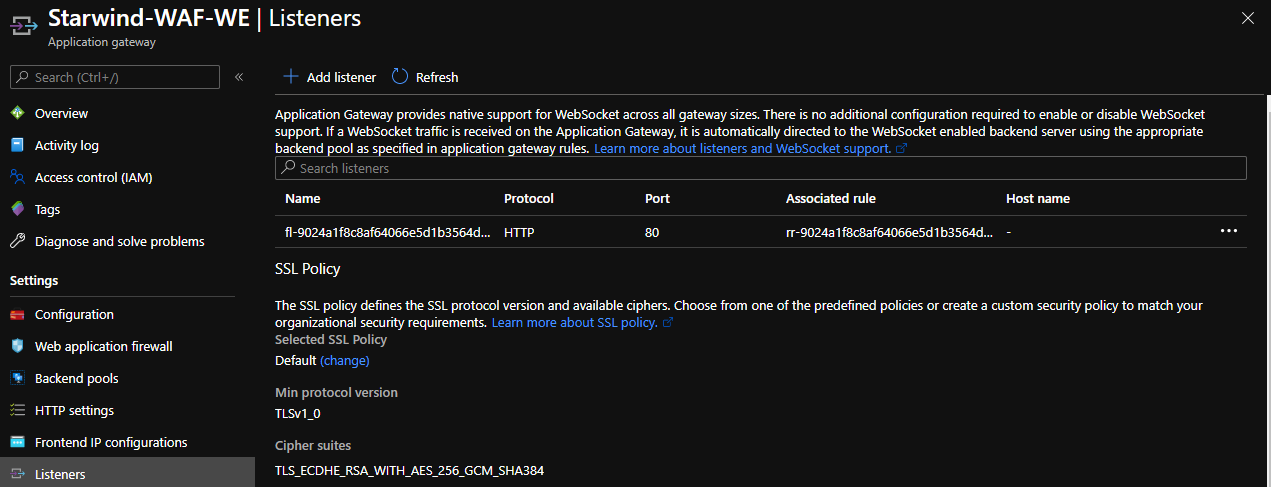
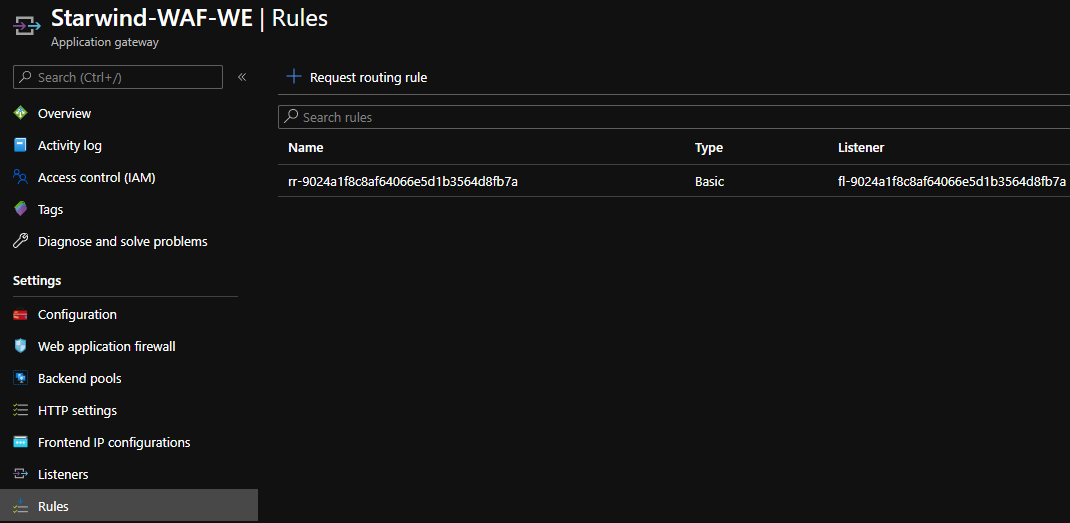
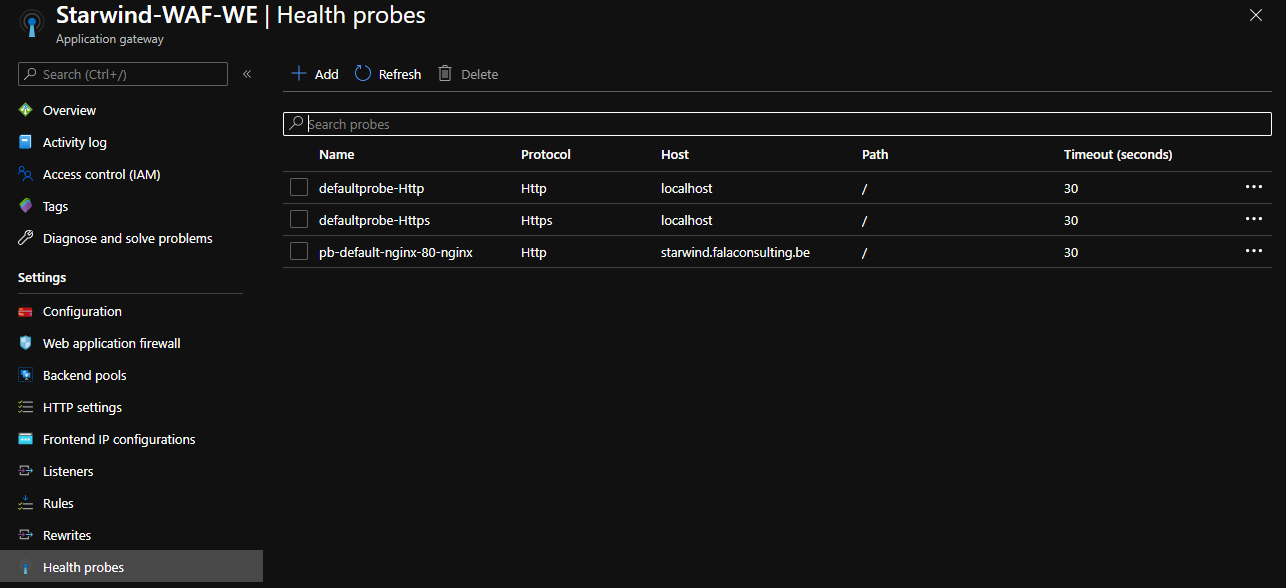
If you try to access your website, you should be able to see it:
In the next article, we will protect this website, with a Let’s Encrypt certificate, directly generated by AKS.


