Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. Azure Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
Azure Sentinel is your birds-eye view across the enterprise alleviating the stress of increasingly sophisticated attacks, increasing volumes of alerts, and long resolution time frames.
- Collect data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
- Detect previously undetected threats, and minimize false positives using Microsoft’s analytics and unparalleled threat intelligence.
- Investigate threats with artificial intelligence, and hunt for suspicious activities at scale, tapping into years of cyber security work at Microsoft.
- Respond to incidents rapidly with built-in orchestration and automation of common tasks.
Deploying Azure Sentinel
Open the Azure Portal and navigate to the Azure Sentinel blade. Click Connect Workspace to enable Azure Sentinel.
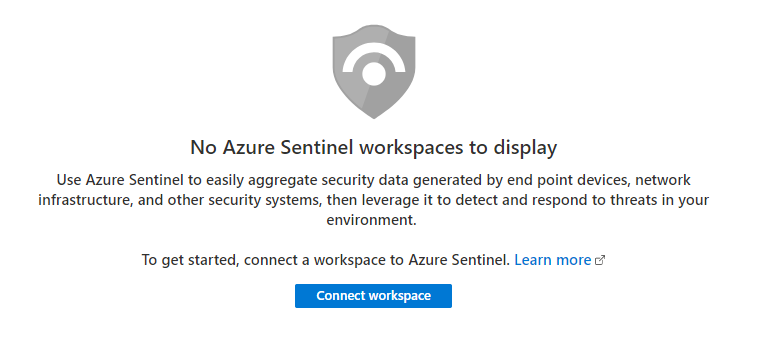
Azure Sentinel must be linked to a Logs Analytics Workspace, so if you do not have an existing workspace, you must create a new one.
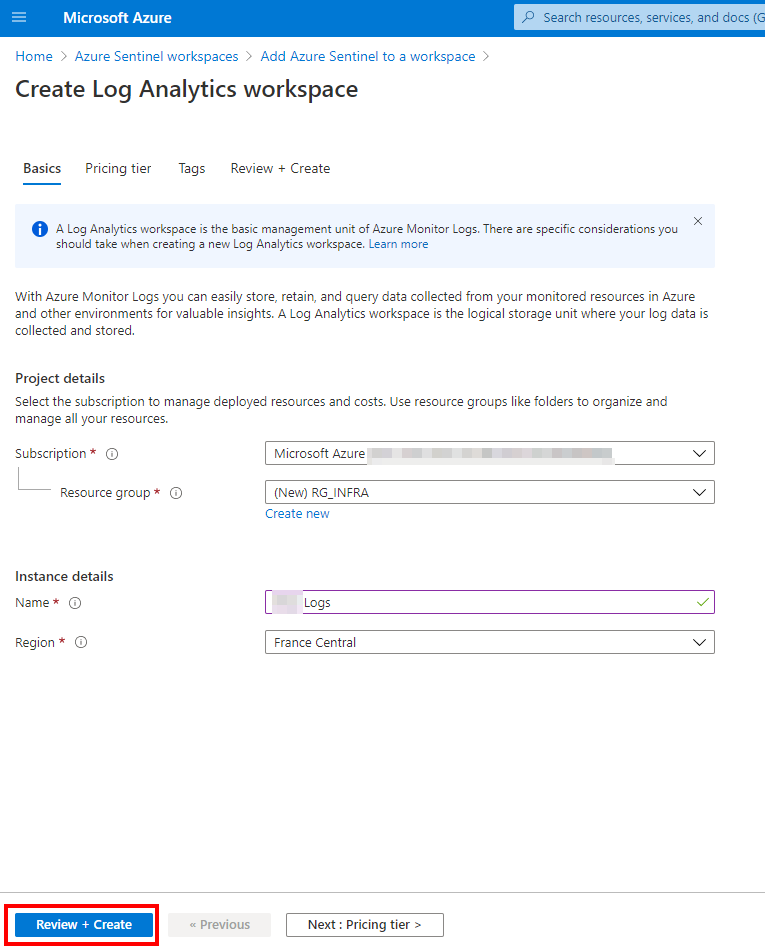
In order to create the workspace, select the subscription, a resource group and enter a friendly name.
After creating the workspace, refresh the list to select the workspace created previsouly
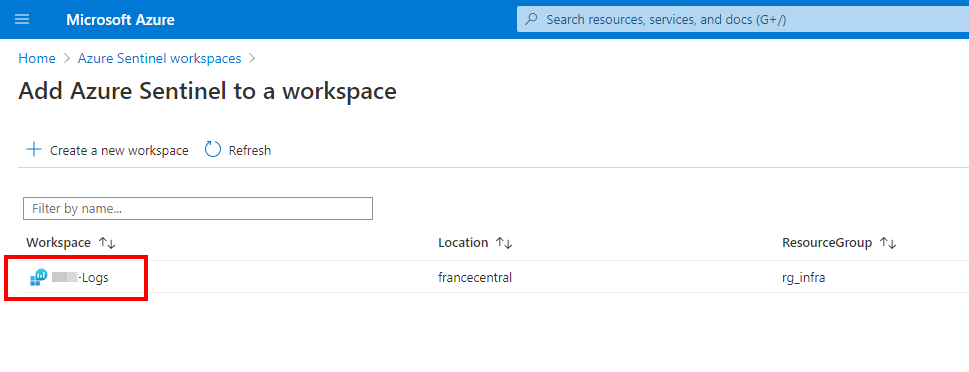
Before going deeper in the Sentinel blade, go to the Azure Active Directory blade to enable the diagnostic settings. Click Add diagnostic setting
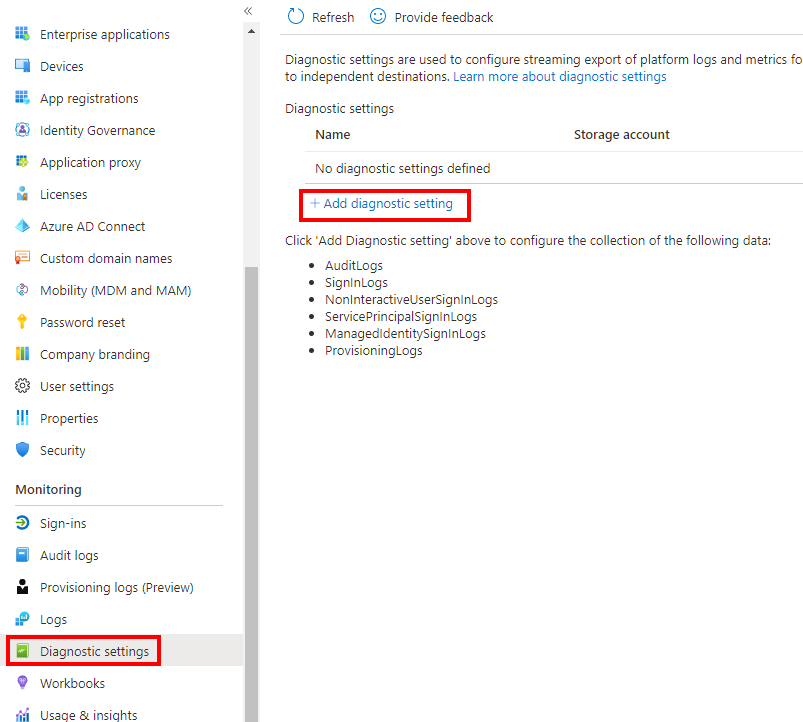
Then, you can collect all the data to the workspace
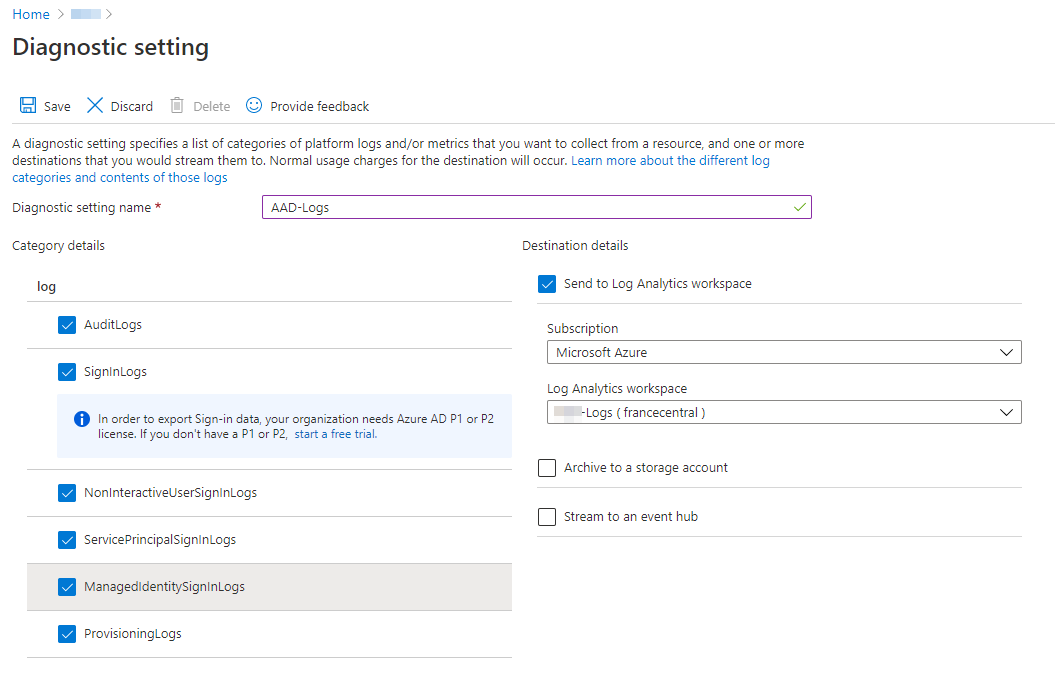
Save the settings and go back to the Azure Sentinel home page. Click Connect to collect data
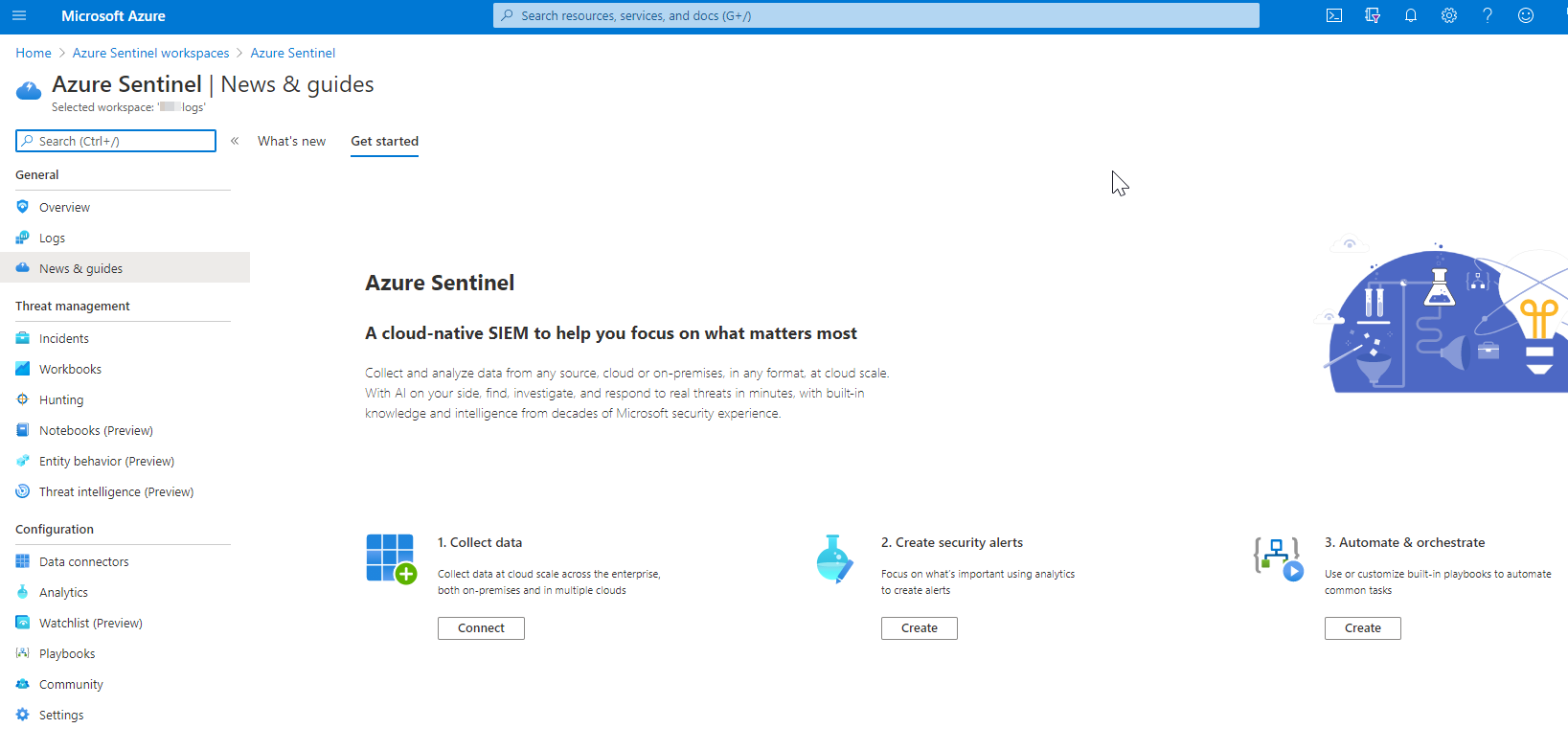
As a good starting point, it is great to enable Azure Active Directory connector to monitor the Azure AD health. Select Azure Active Directory connector and click Open the connector page
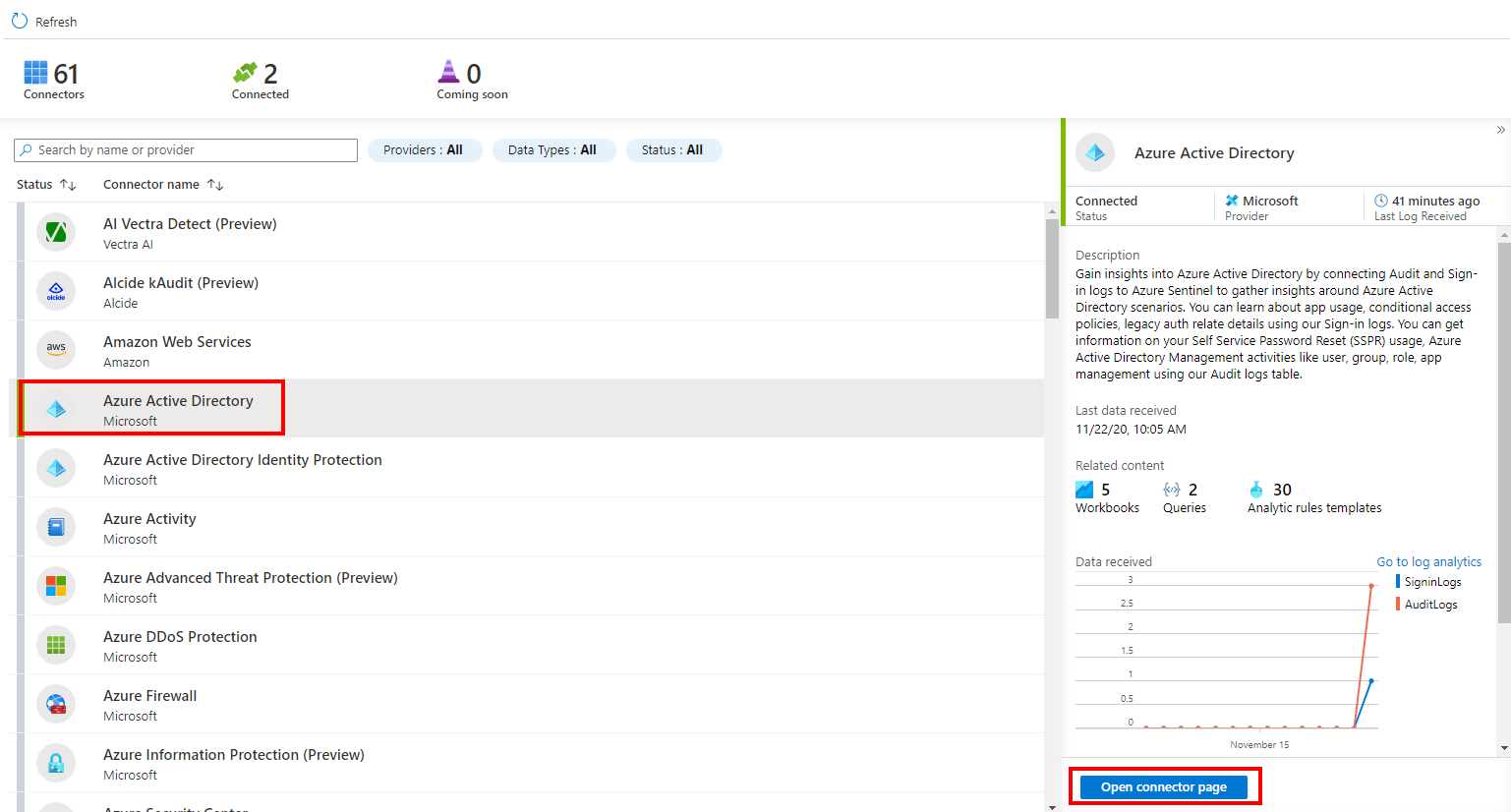
You must have tenant permissions to apply the following changes
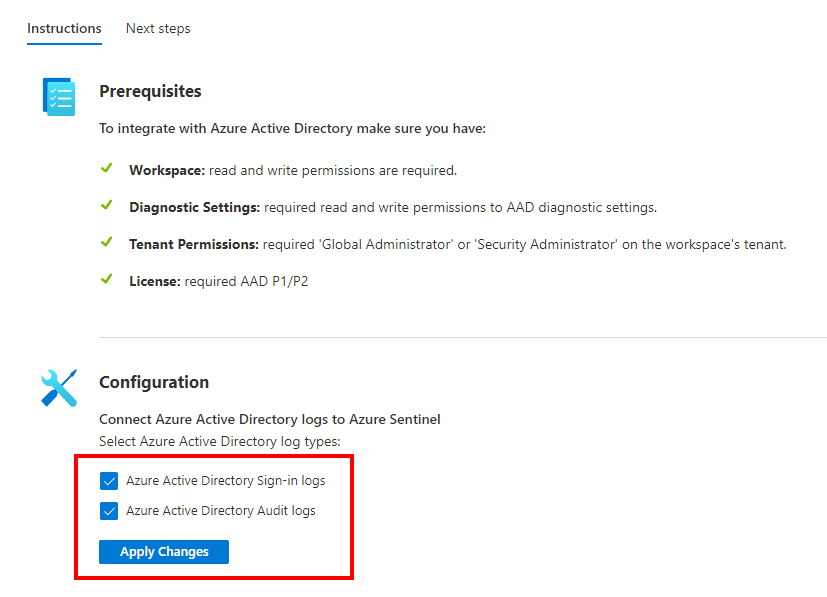
After applying the changes, go to the Next steps page to create a rule based on the templates
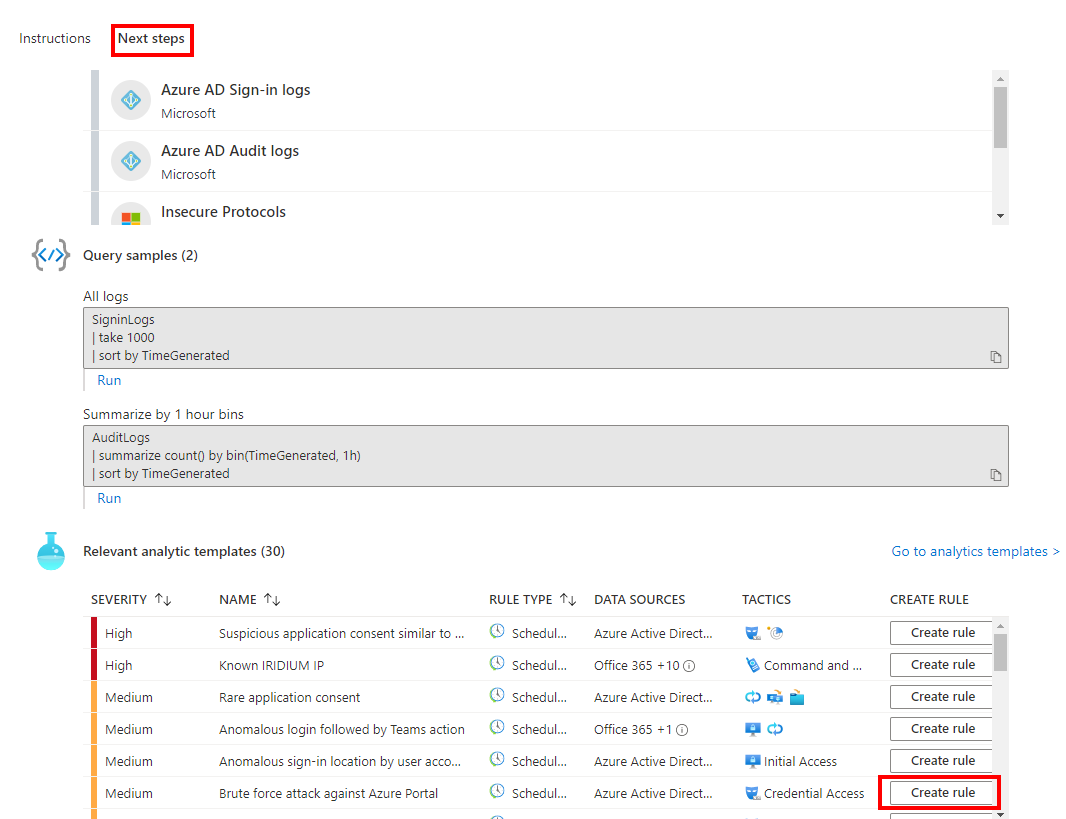
In this guide, I want to enable a rule about brute force attack agains Azure Portal. You can fill the fields in the wizard and enable the rule
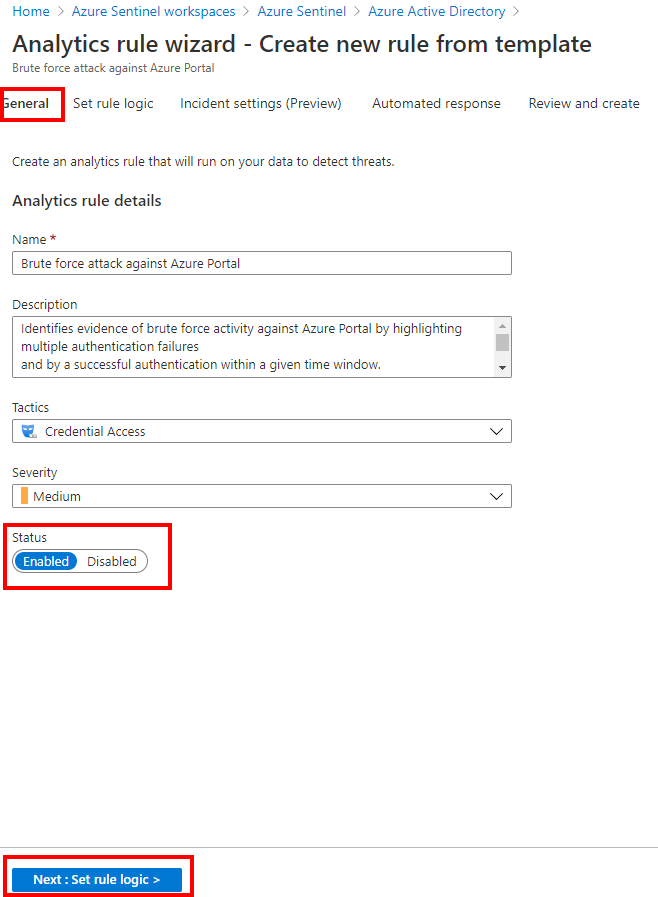
Depending your needs, you can adjust the rule and simulate the rule to see the potential results
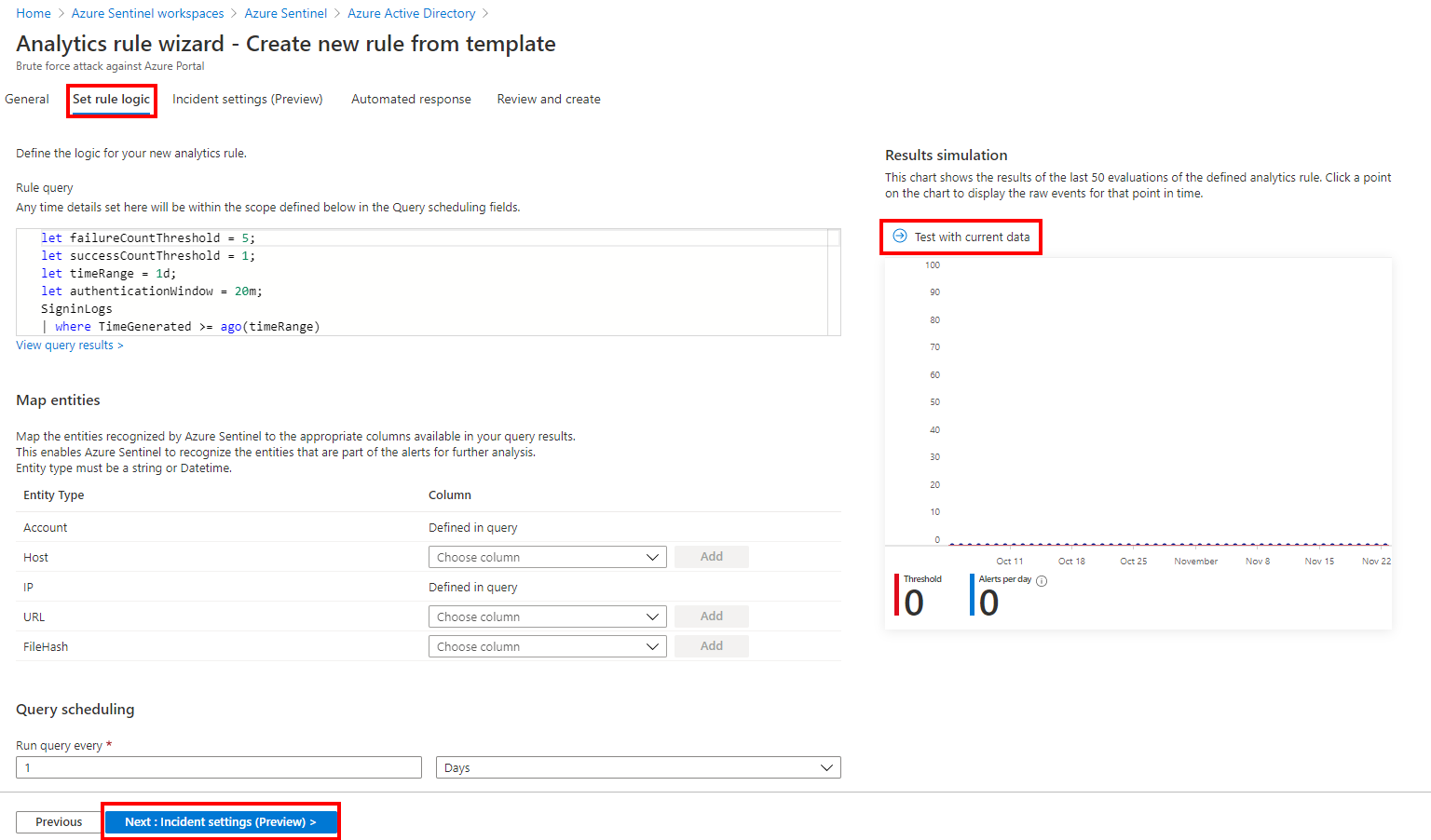
On the third page, you can group the alerts in a single incident
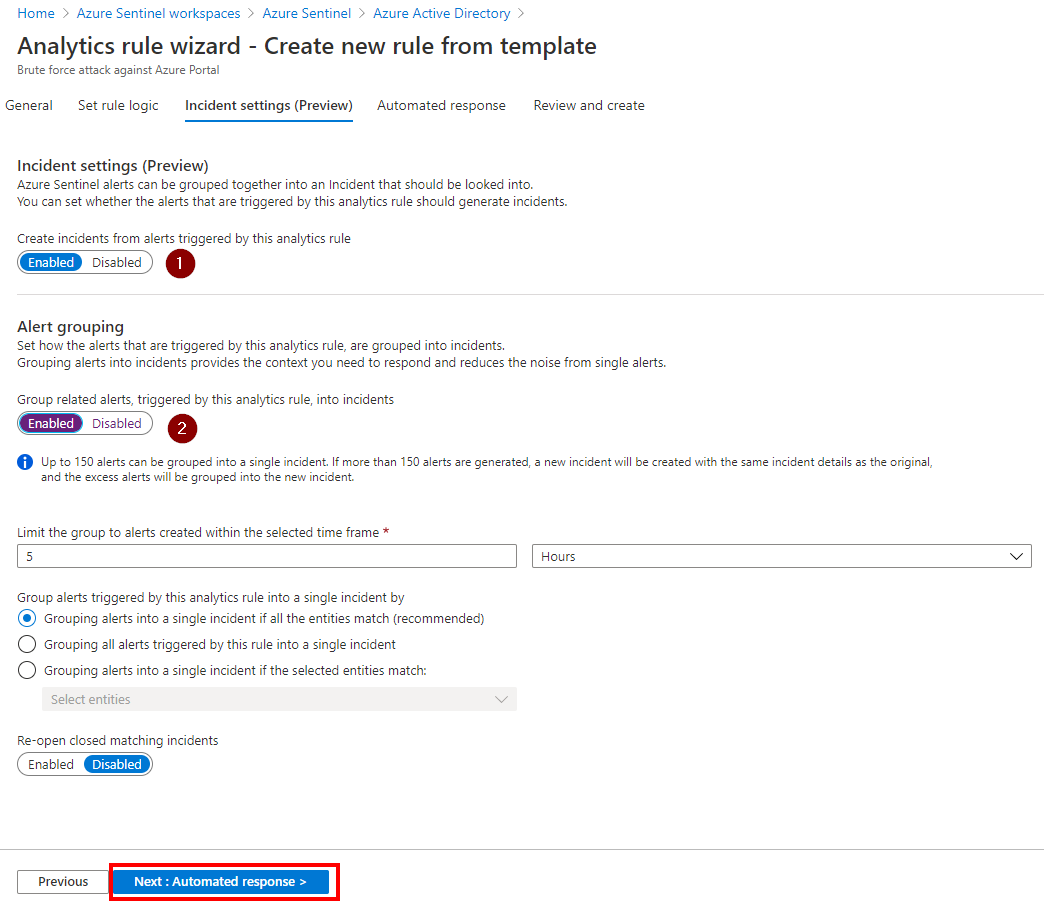
Then you can automate some actions with playbooks. Playbooks allow you run automation steps to schedule, automate, and orchestrate tasks and workflows.
Review the parameters and create the rule
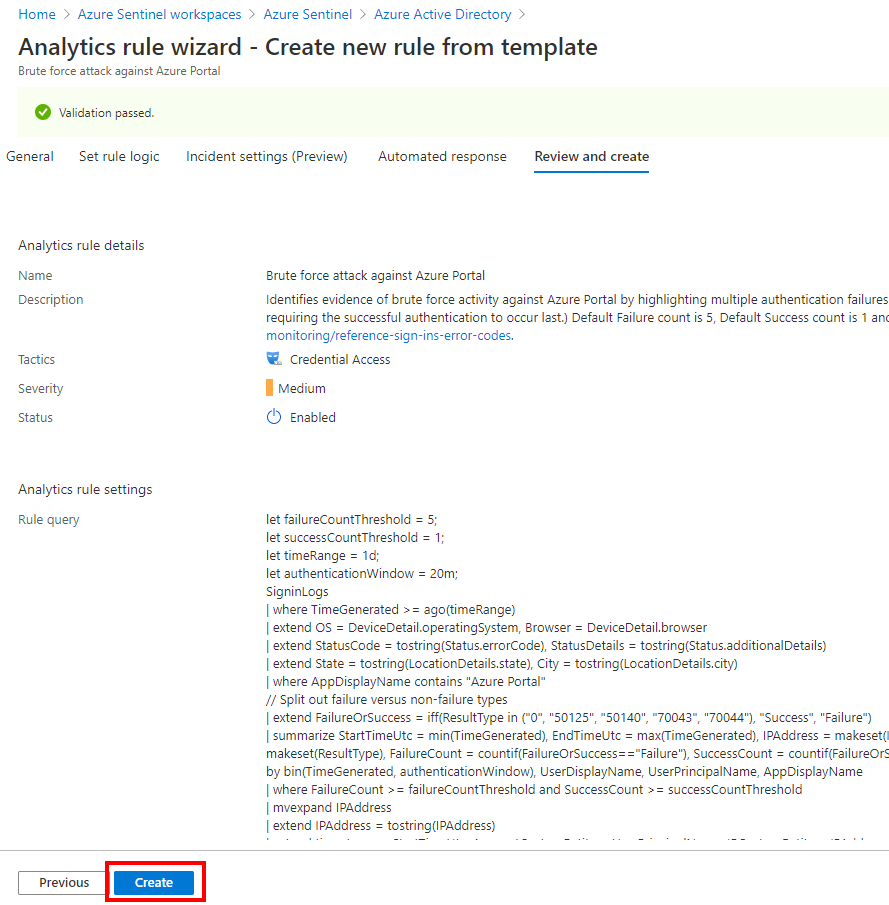
If you need to modify the rule, go to Analytics
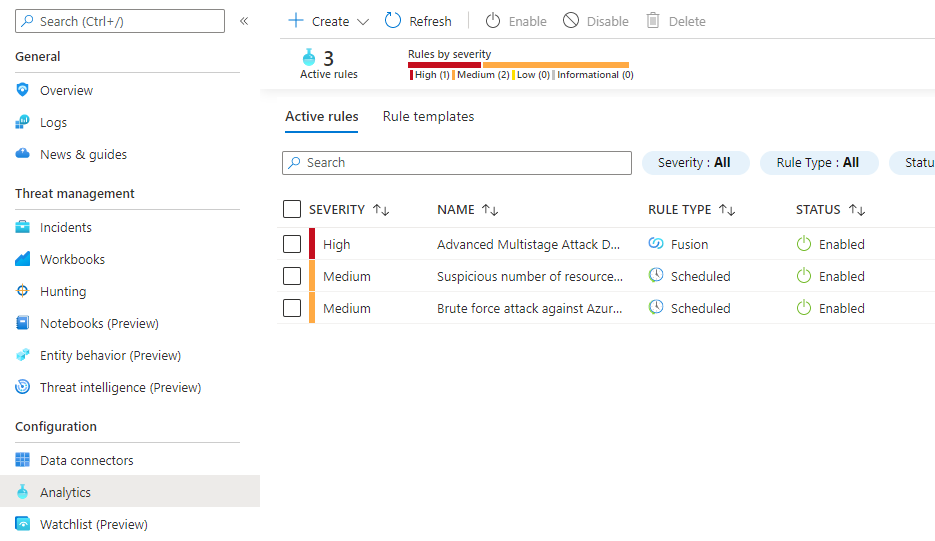
One of the great things with Azure Sentinel is the built-in dashboard templates. Go to the Workbooks blade and click View reports for the Azure AD connector and your data wyou will have dashboard
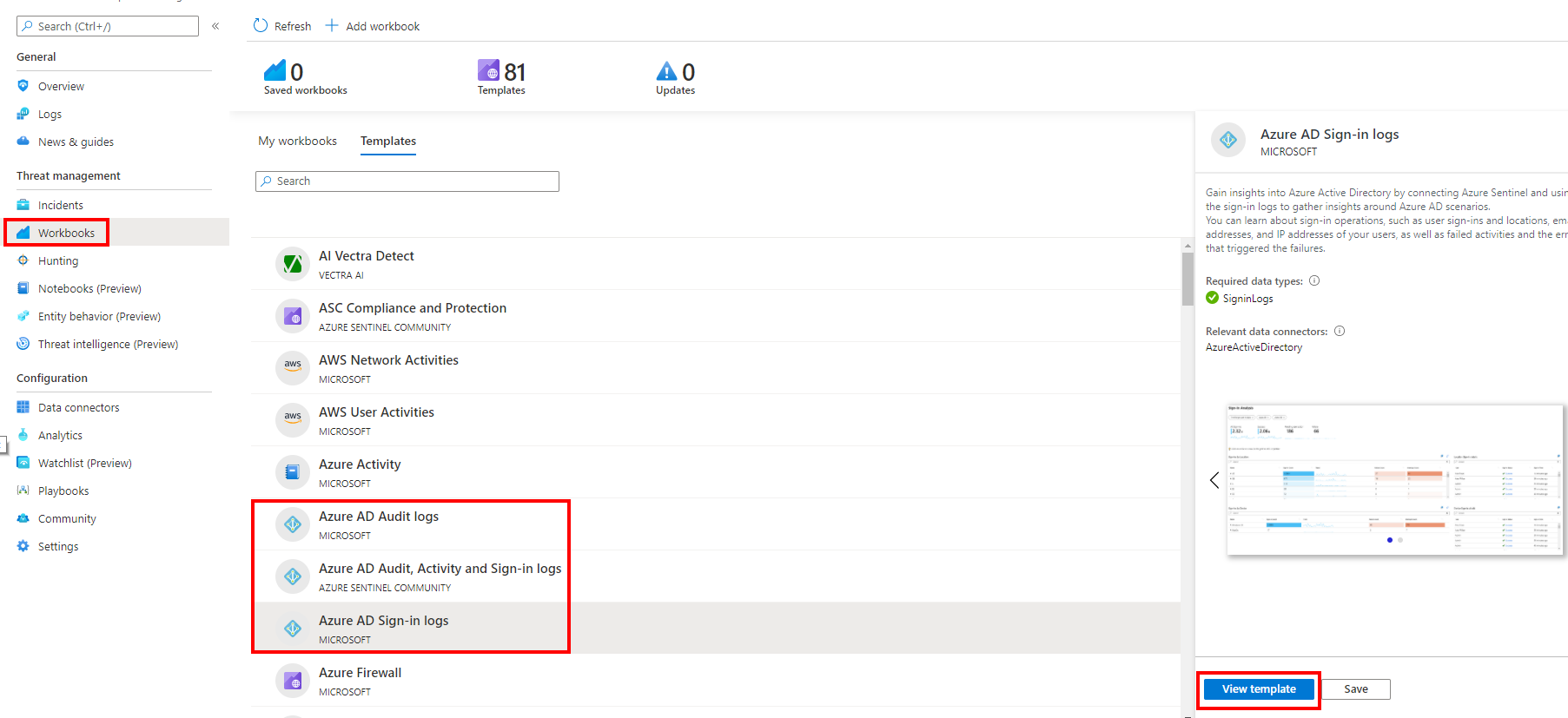
Wait few minutes until data are collected
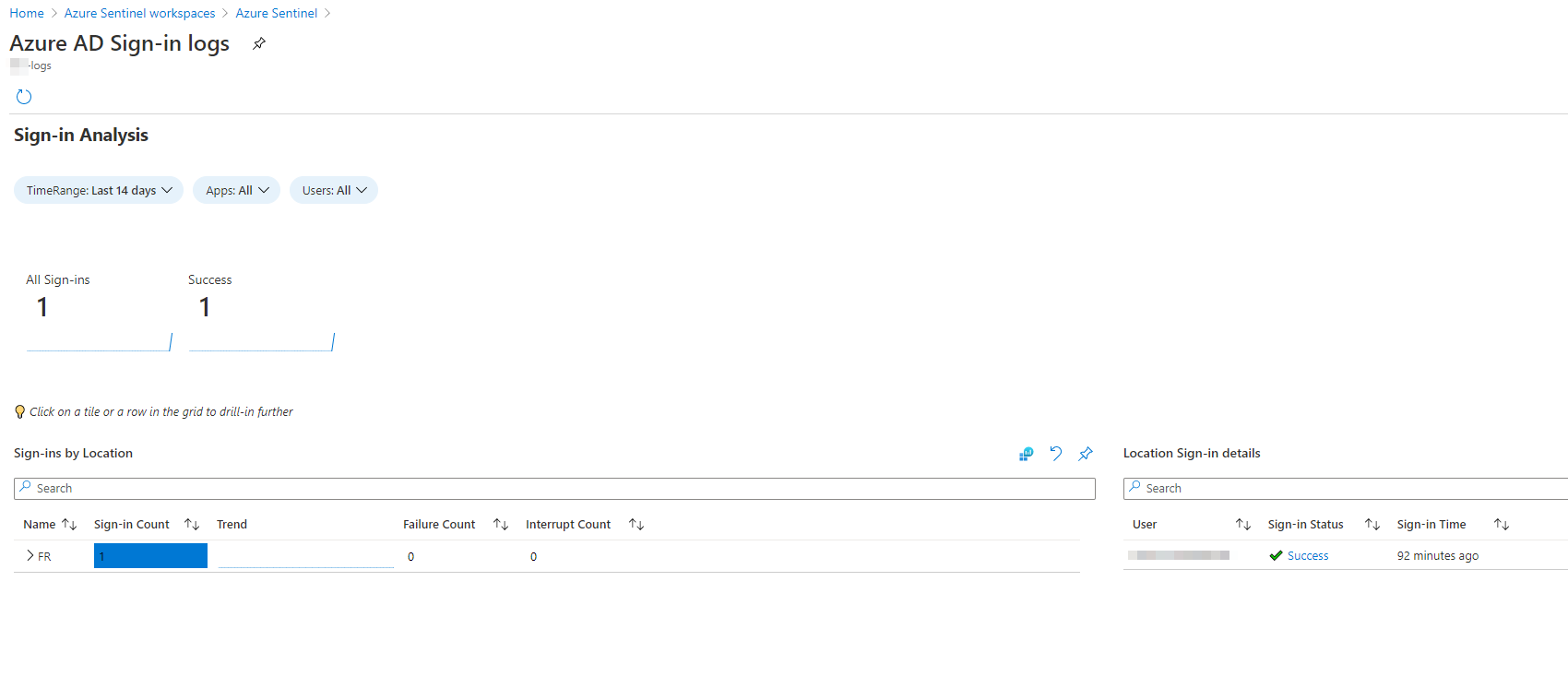
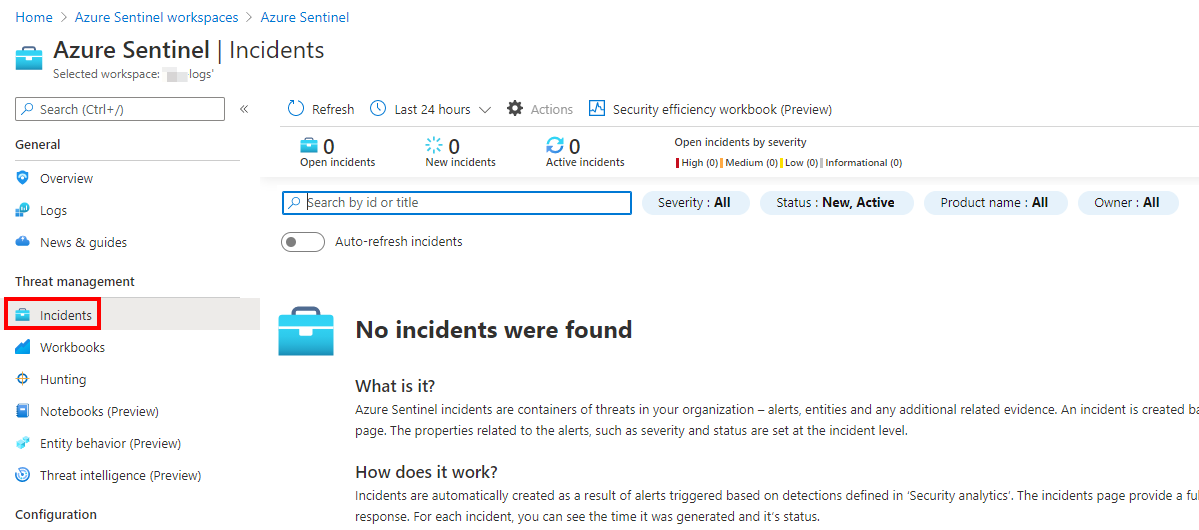
To finish, go to Incidents to check the new incidents