One of the important topics today which we’ll discuss today is a ransomware protection of your backups. It’s not that you don’t have backups. Everyone does. But the way those backups are protected and the way we can protect them is still evolving rapidly.
Whether you’re a small company, small business, or a big corporate business, the strategies of data protection are similar. The budget changes only.
While the backup software we all use today to backup our virtual and physical infrastructures is evolving, there is not much to improve. Many of those backup vendors has tweaked the backup jobs, scheduling of the backups, incremental/differential or synthetic backups, to the perfection.
The backup strategies itself are just perfect and using 3-2-1 backup rule you’re most likely safe (Keep three different copies of your media, on two different media, one of which is off-site).
The way that ransomware operates is usually that it not only encrypts your workstations and servers present on the local network, but usually also get to your backup server and (eventually) erases all the local (and/or) remote backups.
Protect your backup server
Your backups server = your fortress. It’s absolutely crucial NOT to join your backup server to Microsoft Active Directory (AD) but keep it separately from the rest of your network. Don’t use DOMAIN\Administrator for everything. Don’t let the ransomware the life too easy.
Every Admin should have its own access – When you need to track who is doing what, the best is to give each of your team-members access to the backup server with appropriate privileges. Follow the rule of “least privilege” for users who just needs to verify backup jobs or restore files.
I know it might not be simple to manage as many passwords and user names, but only with proper separation you can eliminate the majority of risks.
Offline Storage and other tips
The best storage Is invisible storage. You should use offline storage as part of your backup and protection strategy. Offline storage means any kind of storage which is not “plugged-in” all the time. Some vendors, such as Veeam Backup, have an option to disconnect some types of storage, but you can’t apply this to every type of storage. Let’s have a look at the options we have here.
Tape or tape library – If you’re still using tapes, good. You can have this type of storage completely offline when not being written or read from. You can rotate tapes, store them off site. This strategy is old, very old, but proved right in many scenarios when ransomware hits the house.
Virtual Tape Library (VTL) – While we’re here, I cannot mention StarWind’s VTL which is perfect for the scenario where you don’t have physical tapes, but using software which “generates” a tape library and allows you to connect/disconnect tapes as needed for backups and restores. The VTL software is installed on-premises with cloud and object storage tiering. It allows you to protect your backups from ransomware by keeping them “air-gapped” on virtual tapes.
Replicated VMs – Mot of the backup vendors out there offers replication. If you think of it, the replicated VMs are Powered off at the remote sites. They just sitting there and receiving new data which are “slip-streamed” in on regular basis when the replication job runs. So, the “offline-VMs” are up-to-date and ready to take over when your main site gets encrypted. Perfect protection
Storage snapshots of primary storage – If you have an array supporting storage snapshots, then use it as a protection! Ransomware most likely won’t be able to access your storage array admin panel, unless of course you’re using the same password everywhere. Usually there is a different authentication framework.
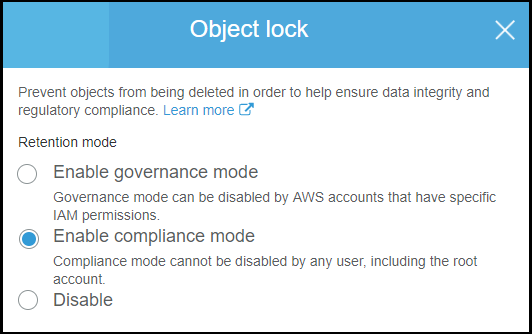
Cloud backups on object storage with immutability – those kinds of backups are not connected directly to the backup infrastructure and uses a different authentication mechanism (different password). Immutability feature by, Amazon S3 for example, allows using Object lock feature on a bucket where the objects are locked and cannot be deleted or overwritten for a fixed amount of time or indefinitely.
You can set two different modes:
- Governance Mode – users can’t overwrite or delete an object version or alter its lock settings unless they have special permissions. Via your root account, you can still grant some users permission to alter the retention settings or delete the object if necessary. You can also use governance mode to test retention-period settings before creating a compliance-mode retention period.
- Compliance Mode – an ultimate protection. The protected object version can’t be overwritten or deleted by any user, including the root user in your AWS account. When an object is locked in compliance mode, its retention mode can’t be changed, and its retention period can’t be shortened. Compliance mode helps ensure that an object version can’t be overwritten or deleted for the duration of the retention period.
Rotating hard drives (USB rotating media) – you can use Image level backups to protect physical workstations/servers and use an option to disconnect the USB after the backup job is finished.
Insider threads
You can have a malicious admin who gets fired to destroy company’s backups. It has happened many times and those admins were fined or even went to jail. Some backup vendors allow having an additional protection against accidental (or malicious) deletion of the cloud backups.
You can be in a situation where an attacker manages to delete tenant backup(s) from a cloud repository, or if the tenant deletes a backup from a cloud repository by mistake.
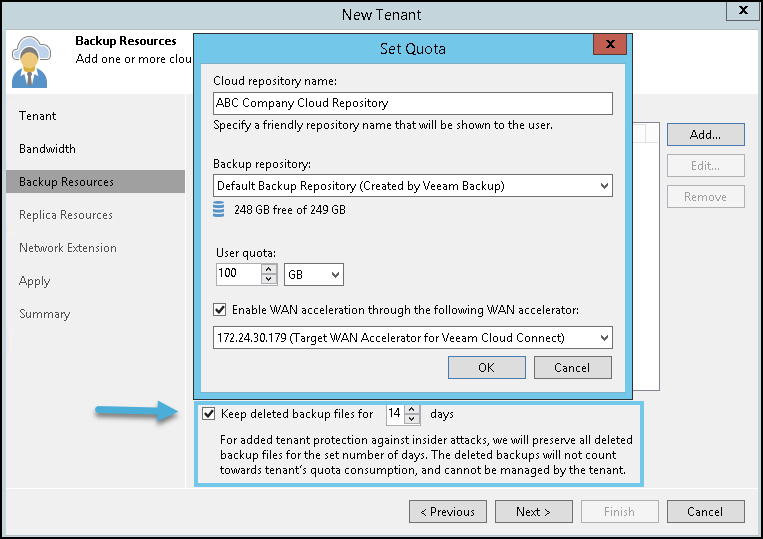
Note: Your cloud service provider has different client (tenants) within his datacenter where he stores those backups. The individual tenants are completely separated by the backup software. Each tenant’s backups do have a “recycle bin” where the deleted backups are moved. The SP enables the Keep deleted backup files for <N> days option in the properties of the tenant account.
Example from Veeam below. You can see the new tenant creation wizard and the checkbox for how long the recycle bin will holds deleted backups.
So, you’re able to recover deleted backups from the recycle bin and then do a traditional restore of VMs or files as usual. So even if your insider has wiped out all your backups and you have your cloud-connect backups deleted, it’s not all lost.
Final Words
We just scratched the surface on a couple of topics useful for ransomware protection. The list could possibly go on and on. There are certainly other ways and other architectural choices to protect you against ransomware and we do not claim ourselves as security experts.
It’s just most admins out there are not security experts either and learning their ways on-the-go. I hope that this post has helped to find ways to increase the protection against the ransomware problems which are on the rise. The situation isn’t going to change. The way we protect our backups can.