Back in the old days of IT, only a very limited handful of people were accessing mainframe terminals, logging in directly on the computer. Often the mainframe was in a locked room with physical access control. Nowadays your colleagues are connecting from many different devices (e.g. personal laptop, tablet, phones), to several applications per day and from an unknown location. We read our emails on phones, chat with friends on our work laptops, and are often connected to open Wifi networks like in coffee shops, airports, hotels.
Today’s reality, in which personal and work lives are co-mingled, is far removed from the well-defined and well-controlled workplace environment and network perimeter of the past. Therefore security is no longer as simple as locking everyone in an office and trusting anyone inside this network perimeter. Your organization must be able to secure access to apps for any user while enforcing security on a different network, system, and data contexts and all should happen within an acceptable timeframe as Identity and Access Management should not slow down the product/software adoption.
What is IDaaS?
In a nutshell, IDaaS is a cloud-based IAM (Identity and Access Management) solution that secures access to applications and systems for an organization’s users, including employees, contractors, partners, customers, and even things (think of IoT).
It, therefore, solves modern requirements of identity without the limitations of the on-premises IAM model and helps organizations to realize the following benefits:
- Faster time to value SaaS solutions are up and running at soon as you sign up, and thus doesn’t require server and software installation;
- Reduce maintenance it’s up to the service provider to update the SaaS solution, you might not even be aware of any software change and it, therefore, reduces the load on your IT department;
- Limited manual integration SaaS solutions are built with everything you need to get going, so no more costly integration between components like network, backup, etc.;
- Cost flexibility as the SaaS solutions are typically charged per user per month, your organization is in control of the spending and pay only for the service used;
- Future proof every time new functionality is introduced (e.g. a new mobile app to secure access from mobile devices, MFA) you get the updates automatically without going to the whole street of planning, installing, performing regression testing, and so on and so forth.
The goal of IDaaS is to ensure users are who they claim to be and to give them the right access to assets at the right times with the benefits of cloud instead of on-premises IAM solutions.
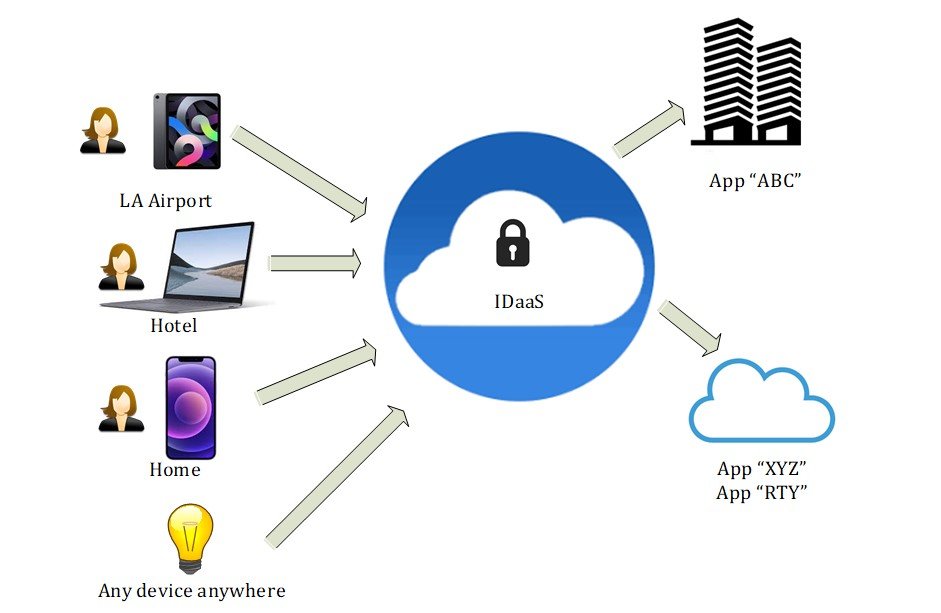
How IDaaS helps my organization?
IDaaS solves many identity challenges that organizations must address today, it enables rapid integration with cloud and on-premises applications by leveraging open standards such as SAML, OpenID Connect (OIDC) and application catalogs. It also consolidates access control regardless of where an application is hosted providing the means for organizations to go for hybrid IT.
On top of that it improves the security posture of your organization with capabilities such as Adaptative MFA and centralized IAM., but let’s discuss it further in the next chapter with SSO and MFA.
What are the building blocks?
Basically, IDaaS solutions contain four main building blocks:
- Directory: a critical component of any IAM solution, this is a database of entities (users, groups, and resources), metadata (configuration and policies), and audit data required by IAM. E.g. Microsoft Active Directory, Open LDAP.
- Single sign-on (SSO): login credentials exist to keep accounts secure but on the other hand, users have different accounts in hundreds of applications and as humans are lazy by nature (and especially with their password), remembering thousand of (secure) passwords seems not doable so people tend to use the same one, which then becomes a security risk. SSO permits to allow access to all applications with a single login (relying on SAML, OIDC) to federate users to third-party systems and applications.
- Multi-factor authentication (MFA): authenticating involves validating an identity, and simply relying on a username/password is not sufficient. To validate the identity of the user a second factor must be considered, such as:
– Something you have: security token, SMS on your phone, FIDO U2F key, etc.
– Something you are: think of biometrics
- Provisioning and workflows: how do make sure your users are provisioned to the system they need in order to log in? With provisioning, organizations cannot only control access to systems but also create, update and delete accounts and privileges based on the status of their users. It automates the account and privilege management of accounts (saving time and money). Moreover, workflows capabilities allow your organization to automate and orchestrate account provisioning (e.g. a certain training needs to be followed before being granted access to a system, or a document needs to be signed off before having a high-privilege role in an application).
Conclusion
With this article the goal was to introduce the concept of Identity as a Service, nowadays we’re all familiar with PaaS, SaaS, IaaS, but not that much with IDaaS, and since managing identity and permissions is a daunting task, investing in an IDaaS is definitely something to be considered.
And remember that we are always very good at granting access and, most of the time, really bad at revoking access which leaves somehow the kingdom not sufficiently protected 😉


