Microsoft Defender For Cloud Apps is a CASB (Cloud Access Security Broker). As the name suggests, CASBs act as a gatekeeper to broker access in real time between your enterprise users and cloud resources they use, wherever your users are located and regardless of the device they are using.
CASBs do this by discovering and providing visibility into Shadow IT and app use, monitoring user activities for anomalous behaviors, controlling access to your resources, providing the ability to classify and prevent sensitive information leak, protecting against malicious actors, and assessing the compliance of cloud services.
In this topic, I’ll show you how to use Conditional Access and Microsoft Defender for Cloud Apps to restrict Copy / Cut / Past in Office Online.
N.B: This feature works great with Microsoft Edge or Google Chrome. However, with other browsers you can experience weird behavior. In addition, the activity restrictions work only for Office Online and not for Microsoft 365 Apps.
Add connected apps to Microsoft Defender for Cloud Apps
If you connect to Microsoft Defender for Cloud Apps for the first time, you should not have any connected apps. At the moment of writing this topic, only a small number of applications are supported to restrict activities. Obviously, Office Online is supported. To connect to Microsoft Defender for Cloud Apps, you can browse this URL: https://<YOUR TENANT NAME>.portal.cloudappsecurity.com/
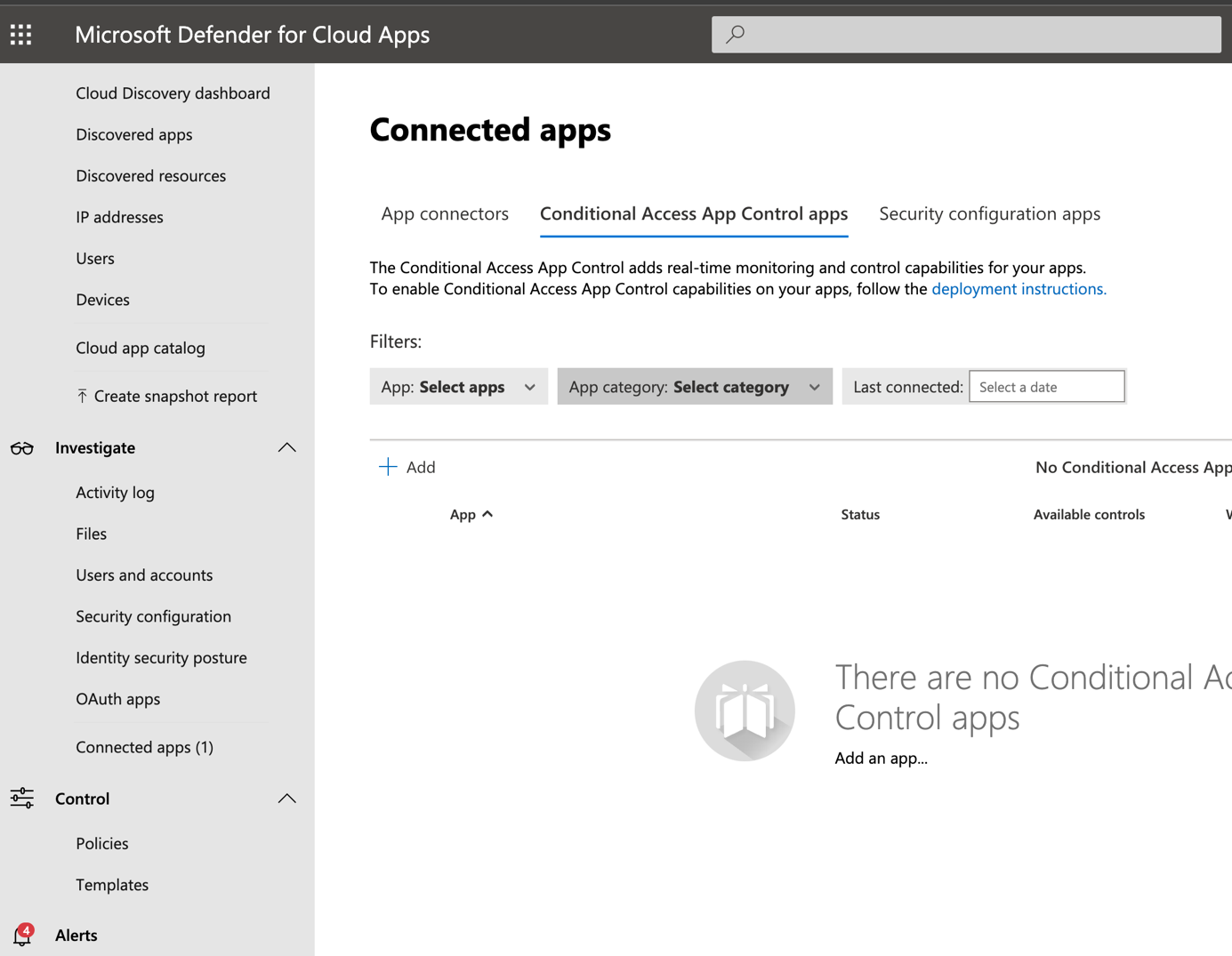
Next browse to Investigate and then connected apps. As the following screenshot, you should have nothing.
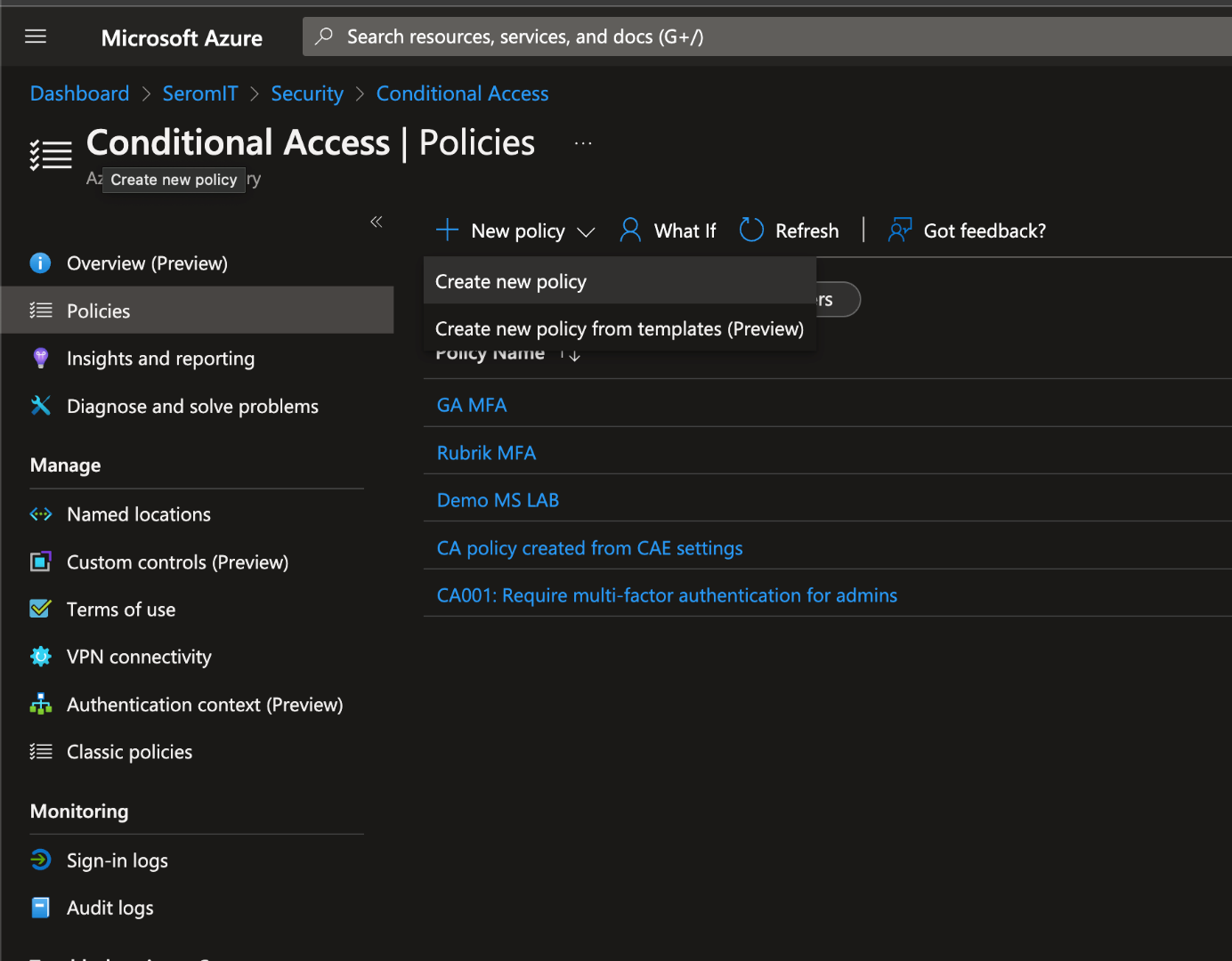
Now open your Azure AD console and navigate through Security and Conditional Access. Create a new policy.
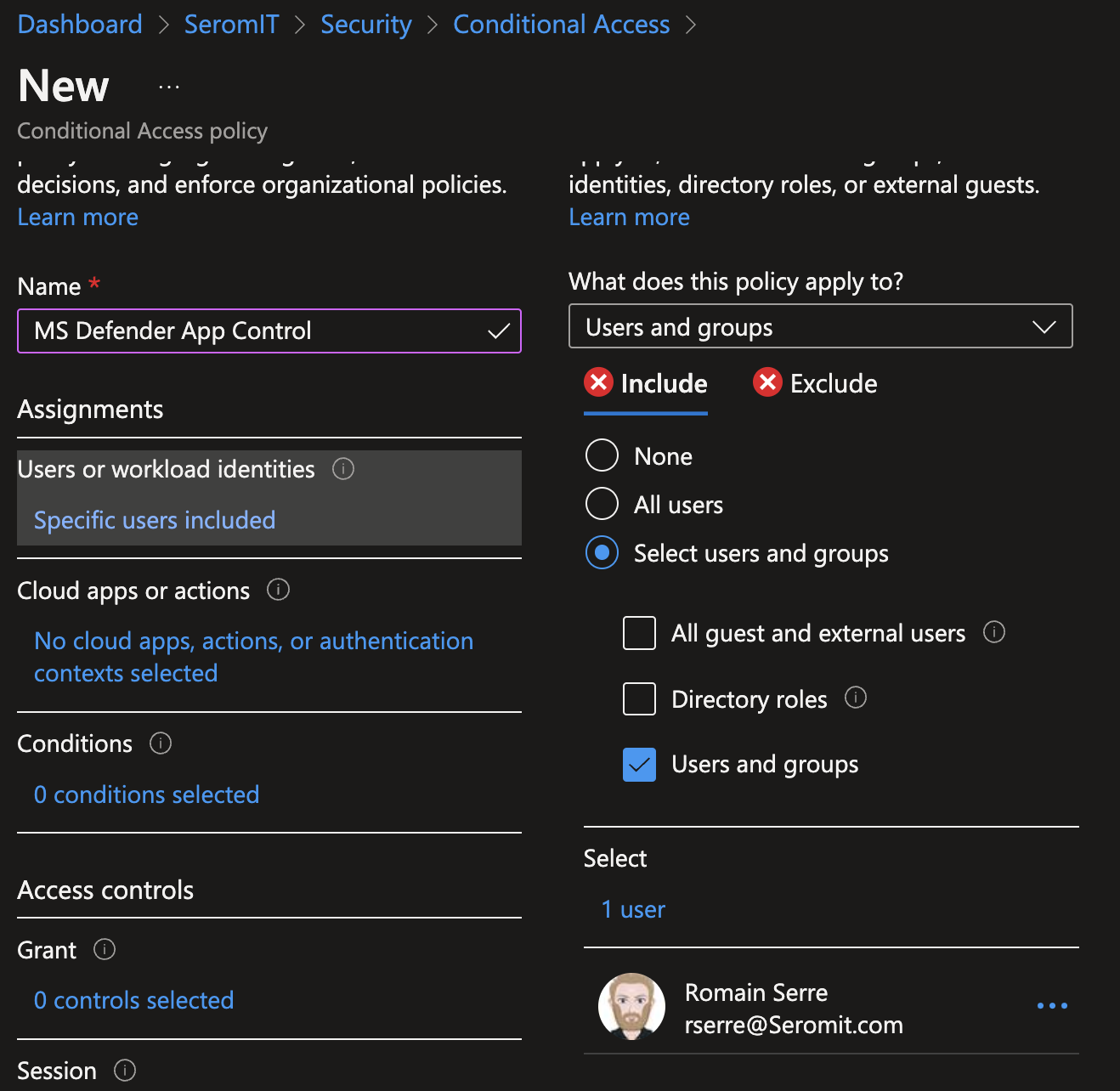
For a proof of concept, apply this policy to a small amount of users. Then when you will want to make it available for everyone, you will have to select more users or groups.
In Cloud Apps or Actions, select Office 365.
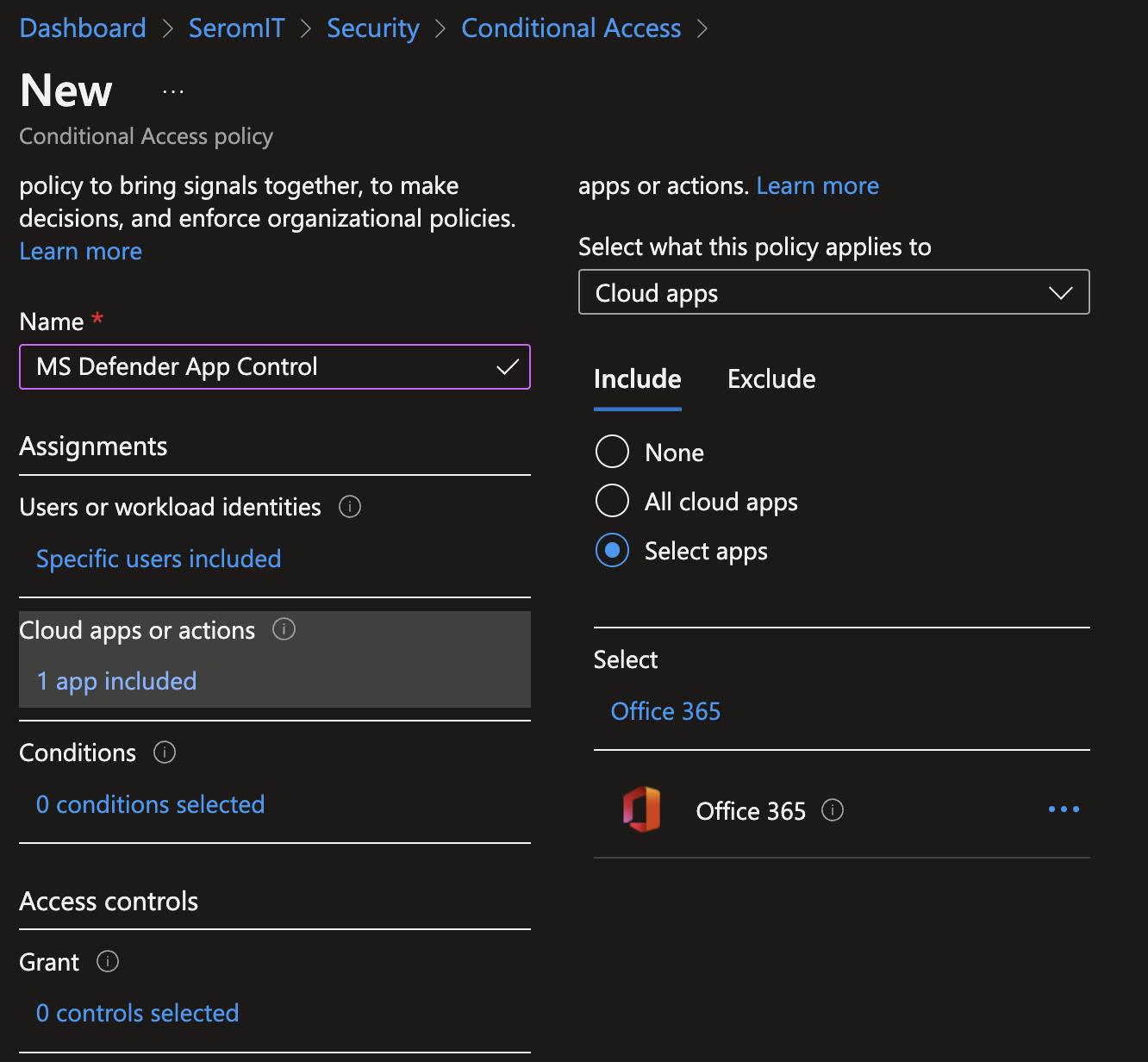
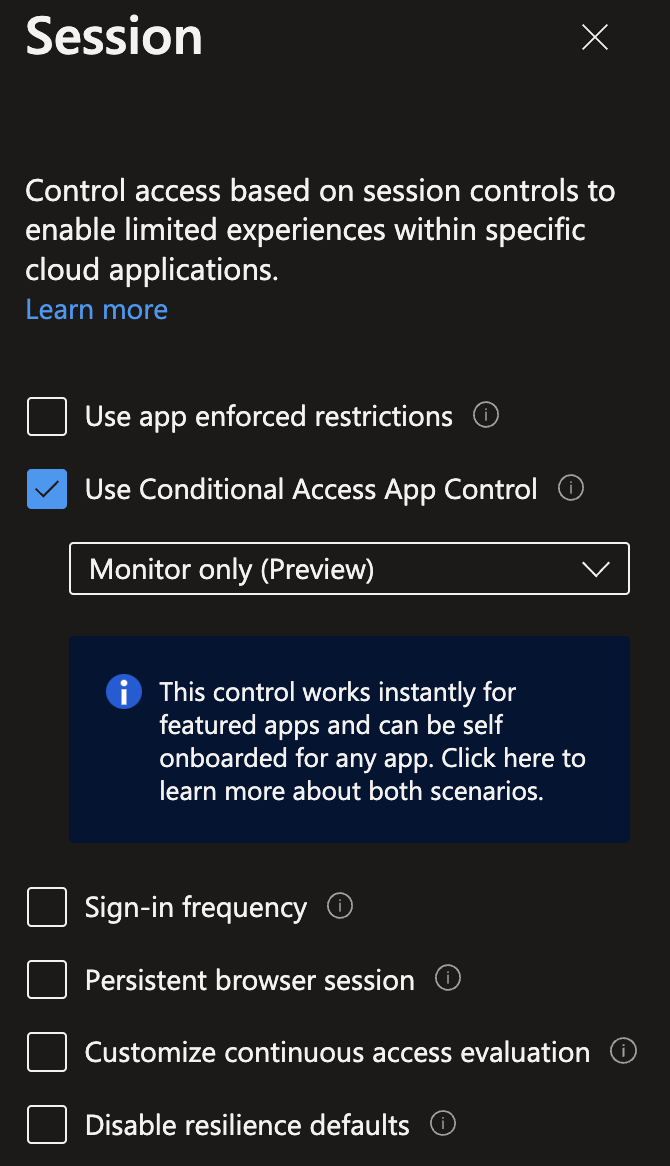
Then in session, enable Use Conditional Access App Control to Monitor. When this setting is set to Monitor you will raise alerts for activities you chose to check. Even if you configure in Microsoft Defender for Cloud Apps a blocked activity, while this above setting is set to Monitor, the action won’t be blocked.
To apply policies you define in Microsoft Defender for Cloud Apps, you will have to set this setting to Use Custom Policy to apply what you defined in Microsoft Defender for Cloud Apps.
Once the conditional access is applied, open Office Online.
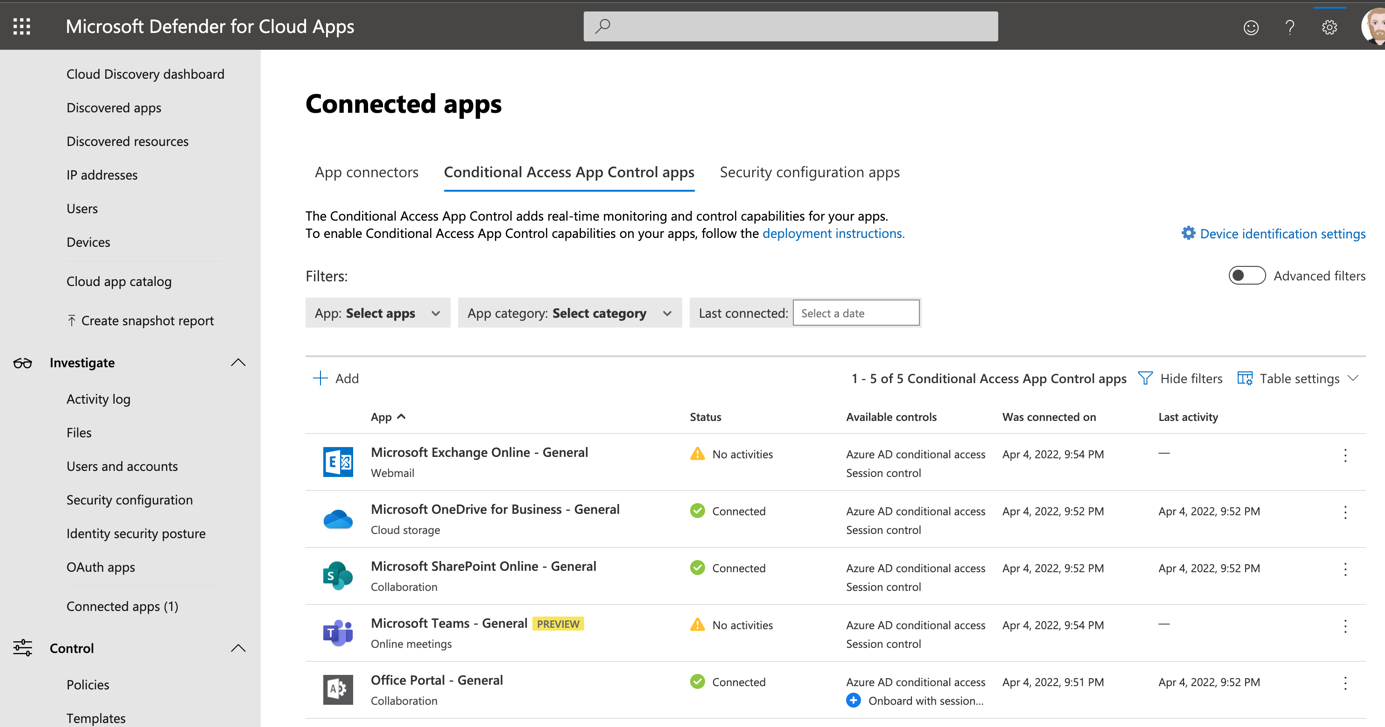
If you go back in Microsoft Defender for Cloud Apps, you should get some connected apps.
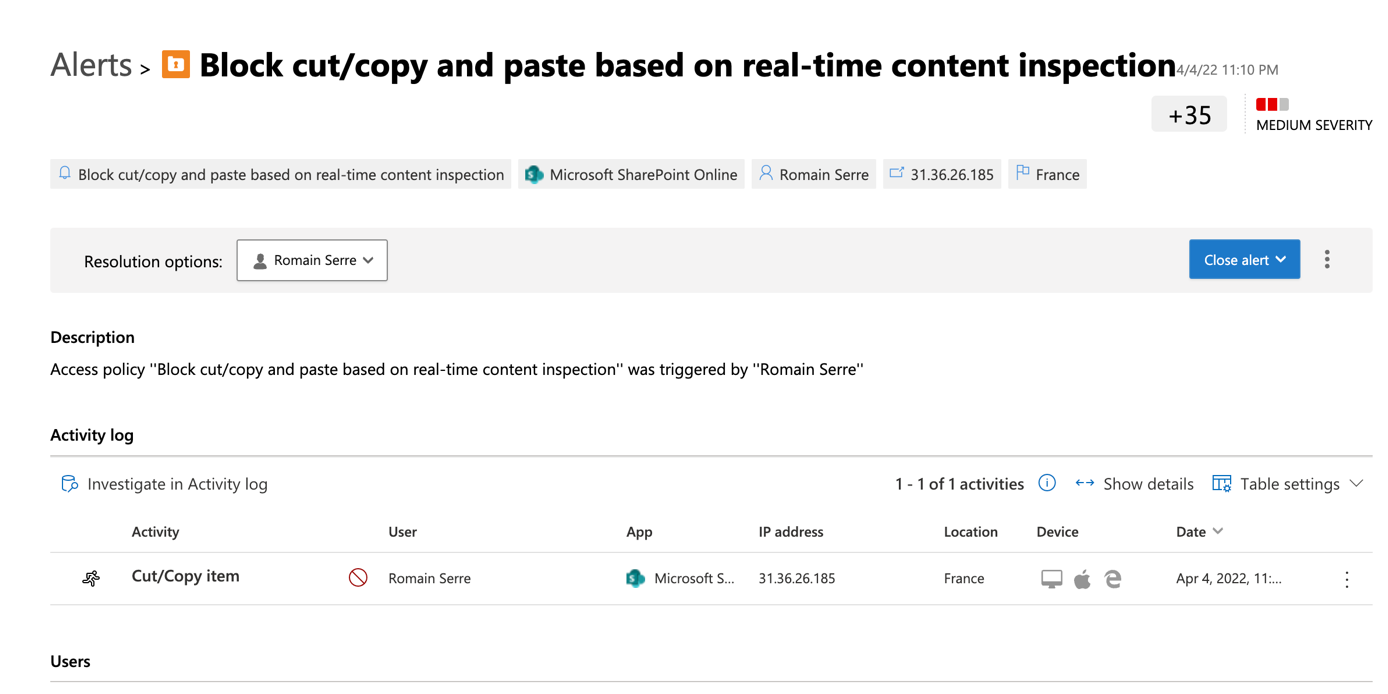
Block Copy cut and past in Office 365
Now that connected apps are available, navigate in Control and Policies. Here you can create several policies related to information protection, threat detection shadow IT and conditional access.
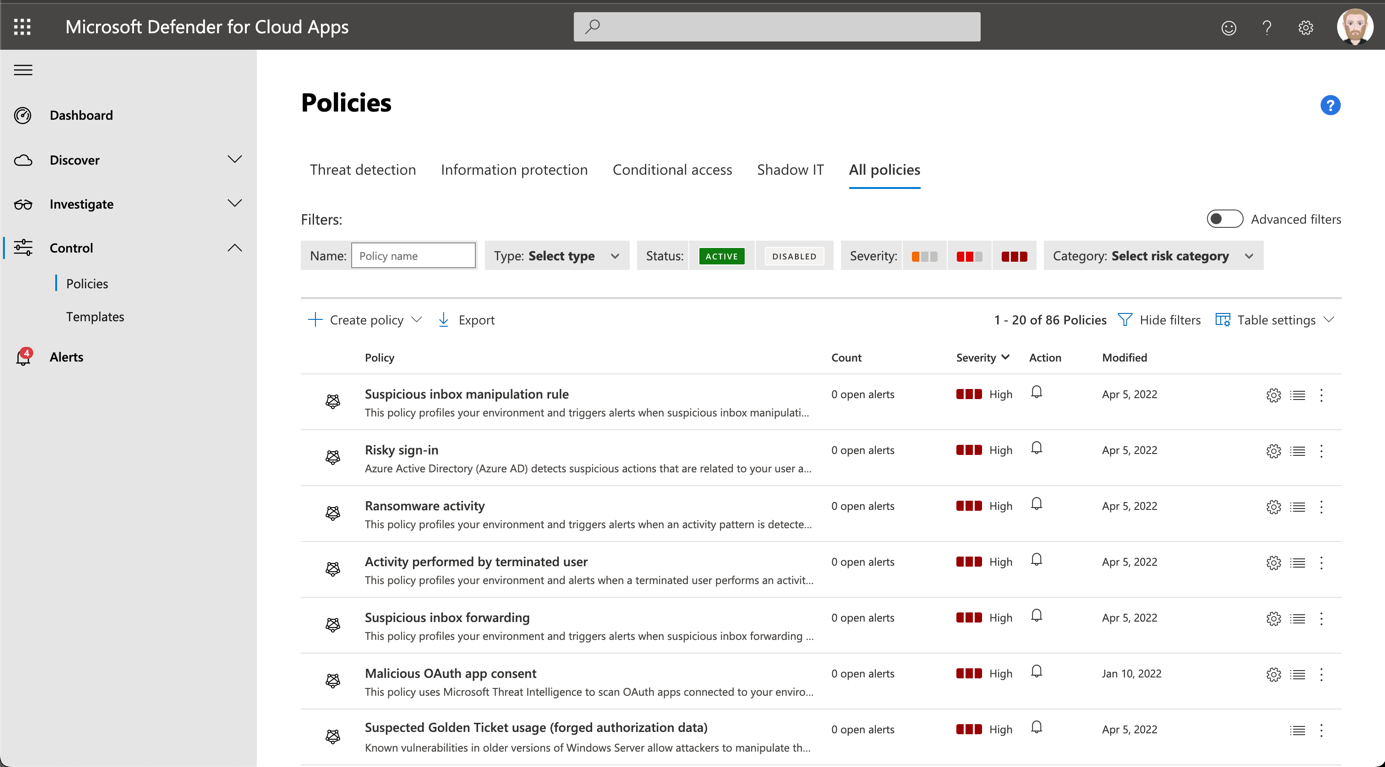
Navigate to templates and select session policy type. On the right of Block Cut/copy and paste based on real-time content inspection, click on the “+” button.
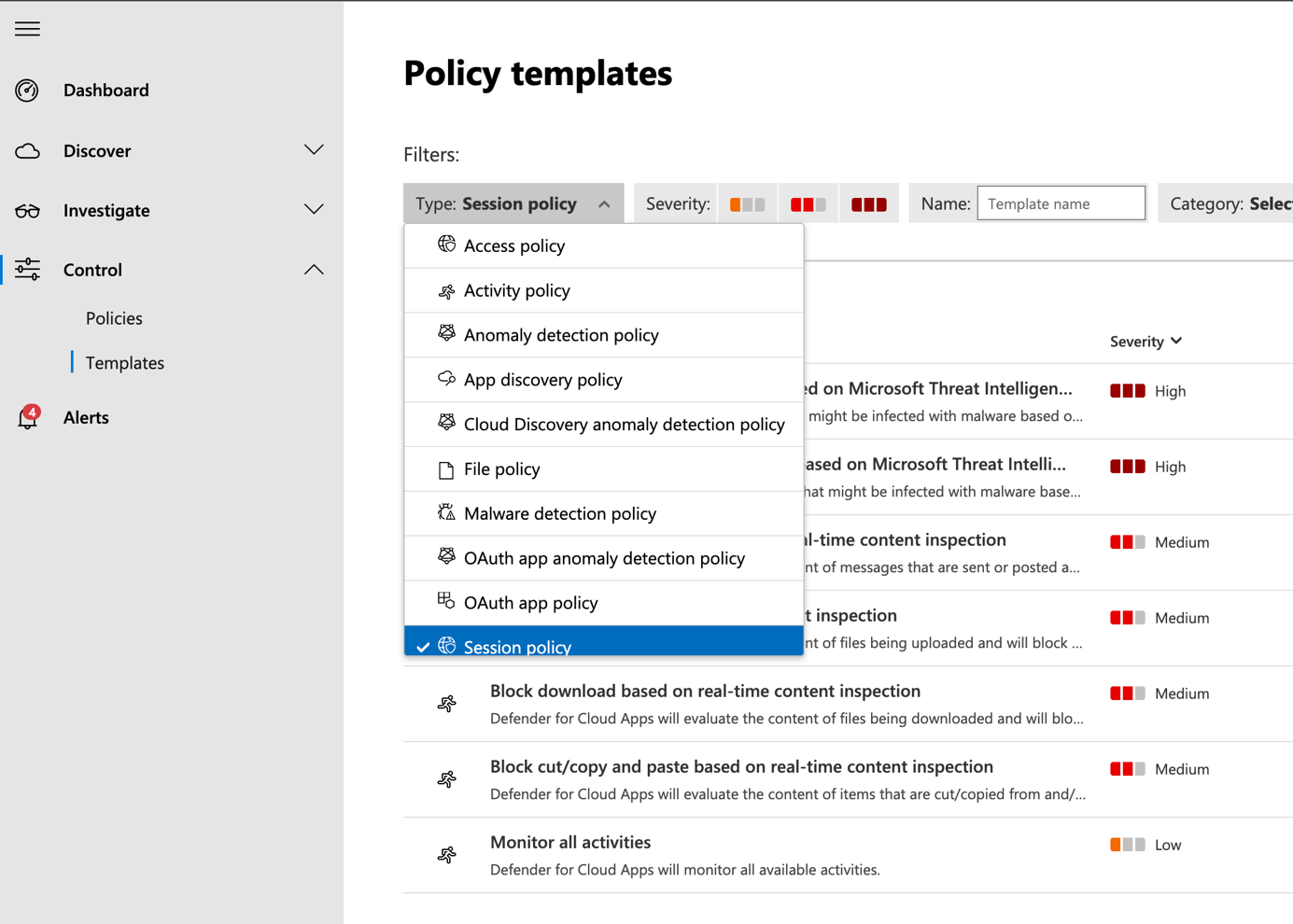
Provide a name for your policy and leave other settings as they are. If you browse all the settings, you can see, or policies are working. In Activities matching you get the request applied to raise an alert and block the activities. This policy applies to all devices that are not compliant in Intune and for selected activities.
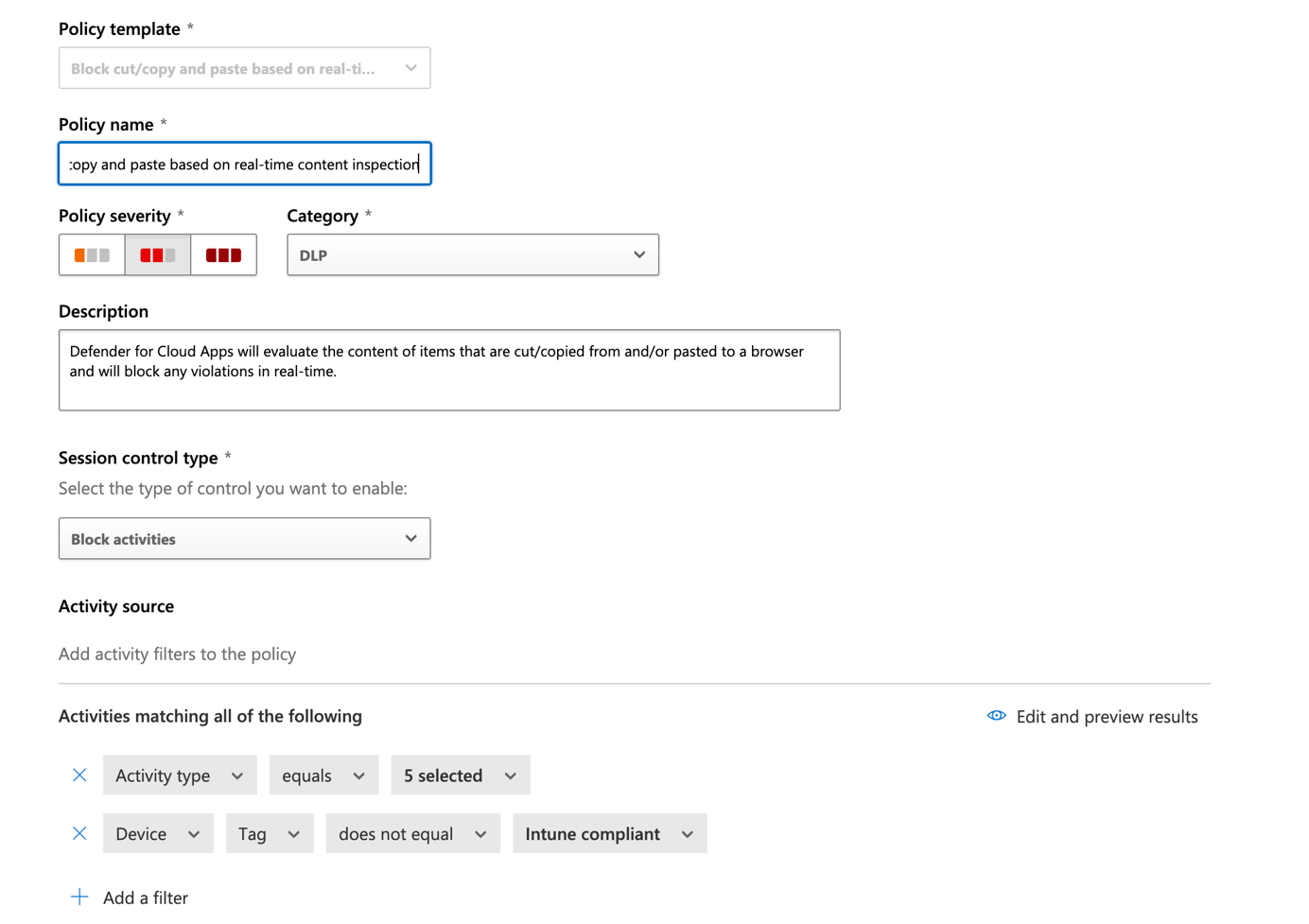
Now in Actions you can choose what happen for non-compliant devices where users are doing copy, past and cut. In this example, these activities are blocked, and a custom message is displayed to users. In addition, an alert will be raised in Microsoft Defender for Cloud Apps.
If you open again Office Online and you try to do a copy / cut or past, you should get a pop-up which indicates that the action is blocked.
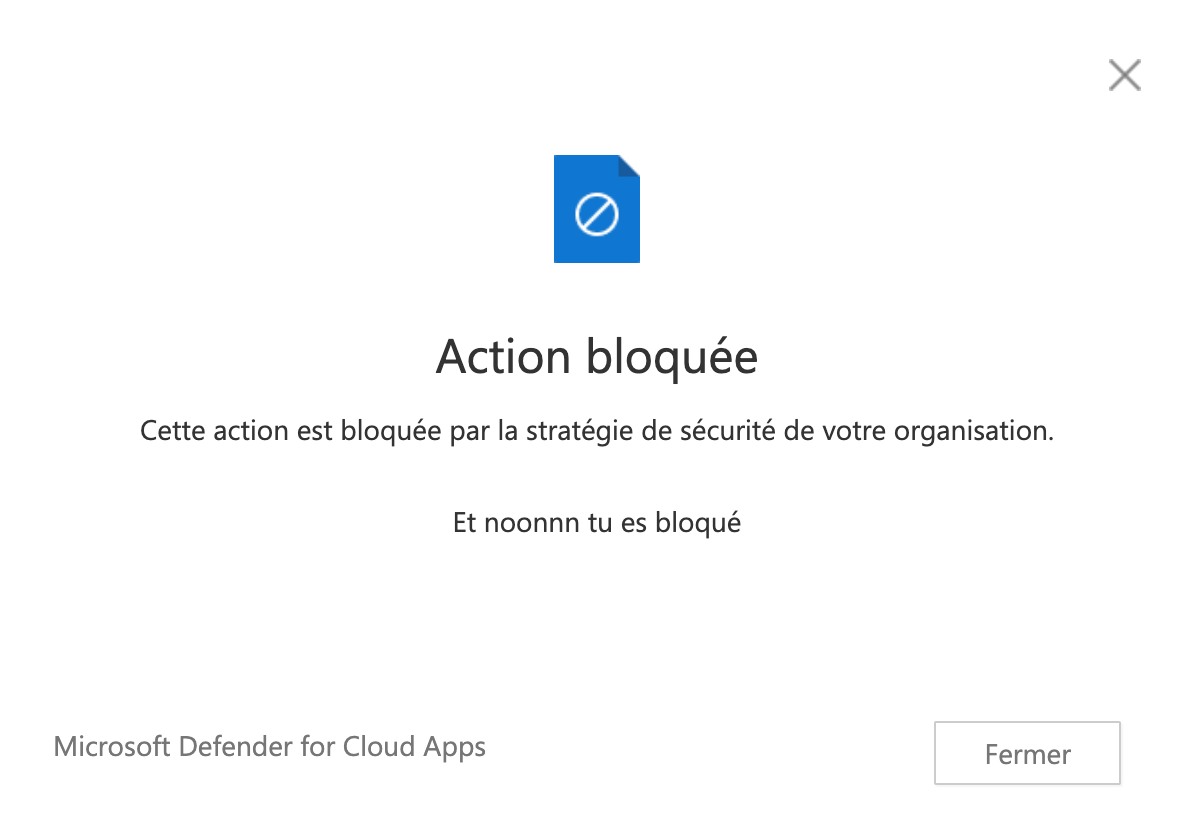
An alert should also be raised in Microsoft Defender for Cloud Apps.