Microsoft Defender For Cloud Apps is a CASB. One part of its job is to detect shadow IT. In big organizations, shadow IT refers to information technology (IT) systems deployed by departments other than the central IT department, to work around the perceived or actual shortcomings of the central information systems. Shadow IT often introduces security and compliance concerns (definition from Wikipedia).
For example, your company subscribe to M365 with Onedrive and some users don’t like Onedrive and work from DropBox. The IT department is not aware about that and so it is considered as Shadow IT.
This kind of Shadow IT can bring threats because you applied security and compliance policies only on products you provide to end users. In the above example, the IT department doesn’t know that some users are using Dropbox and nothing is deployed to protect information.
Microsoft Defender for Cloud Apps can help you to detect Shadow IT. It can get information from two sources:
- Logs import from your Firewall: often used to get information for external users (Wifi guest). It can help you to improve your blacklists
- Information gathered from Microsoft Defender for Endpoint (MDE): from MDE you can redirect web traffics to Microsoft Defender for Cloud Apps
Once the information are collected, you get all services used by users and a lot of statistics about them. In this topic, we will see how to collect information and how to use them.
Collect information in Microsoft Defender for Cloud Apps
To forward Microsoft Defender for Endpoint (MDE) signals to Microsoft Defender for Cloud Apps, navigate to security.microsoft.com. Click on Settings, Endpoint and Advanced features. Enable Microsoft Defender for Cloud Apps.
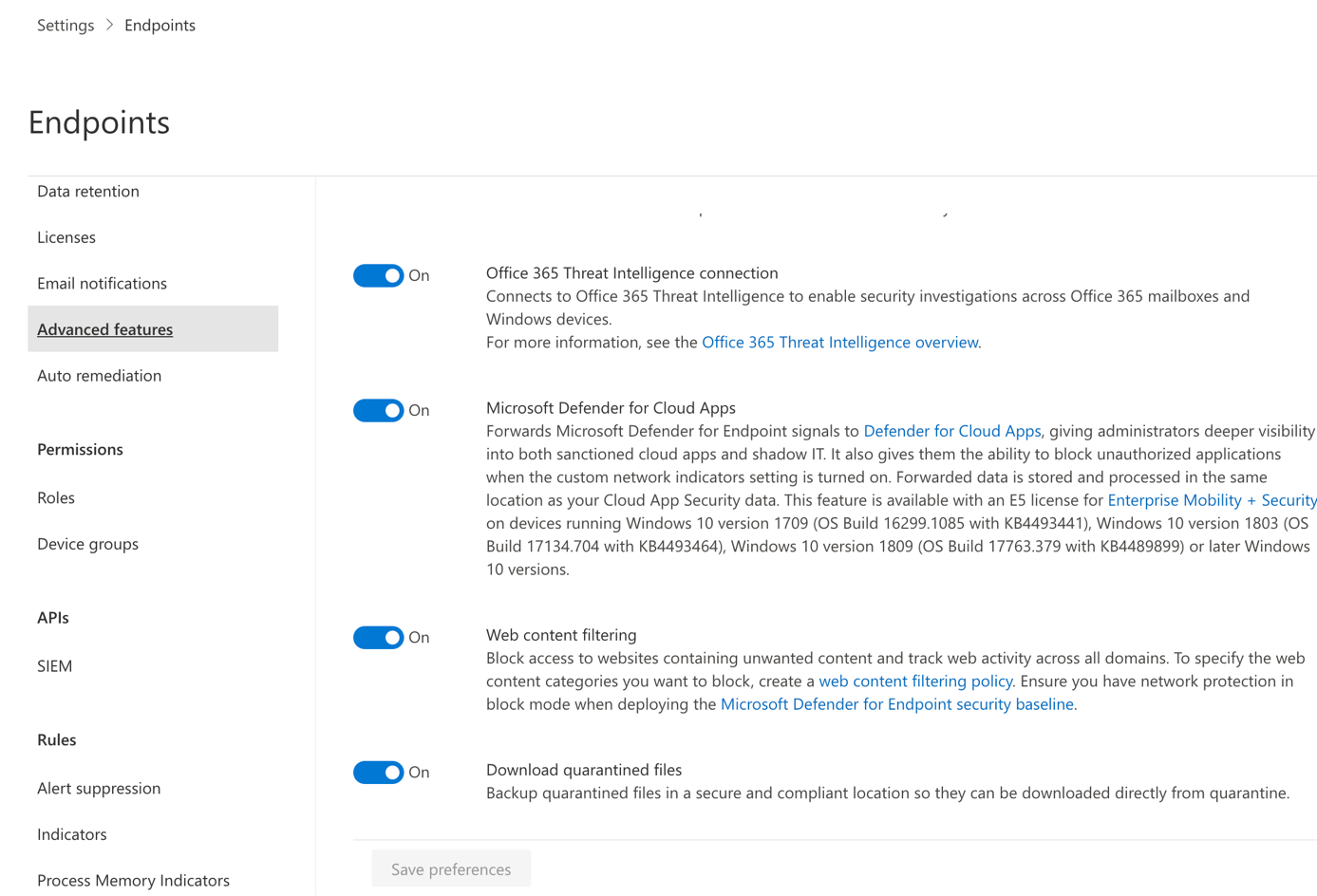
Once it is enabled, signals are forwarded, and Microsoft Defender for Cloud Apps starts to collect information.
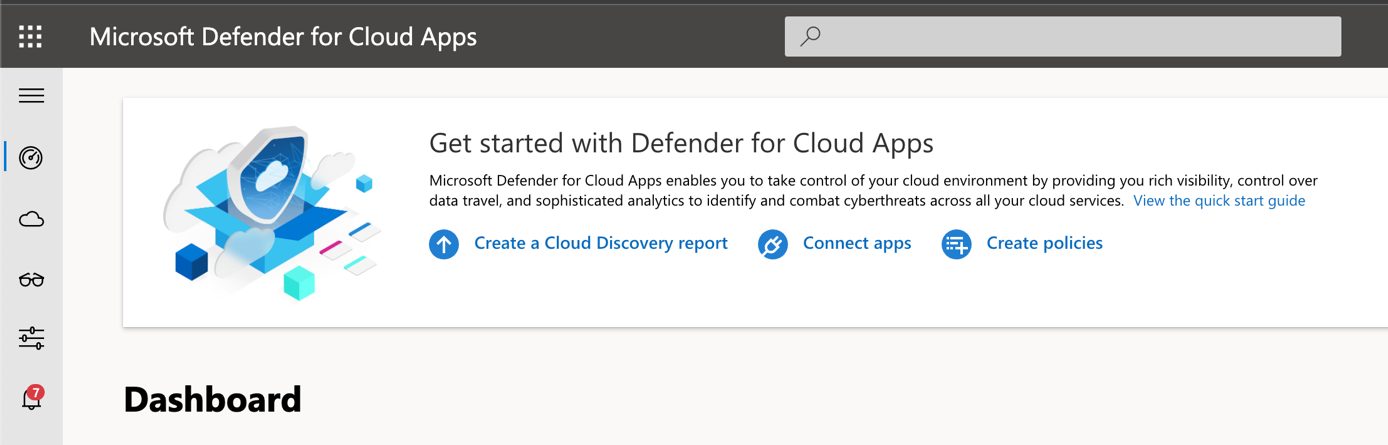
To get information from your firewall, open Microsoft Defender for Cloud apps. Then on the dashboard, click on Create a Cloud Discovery report.
In overview window, just click on Next.
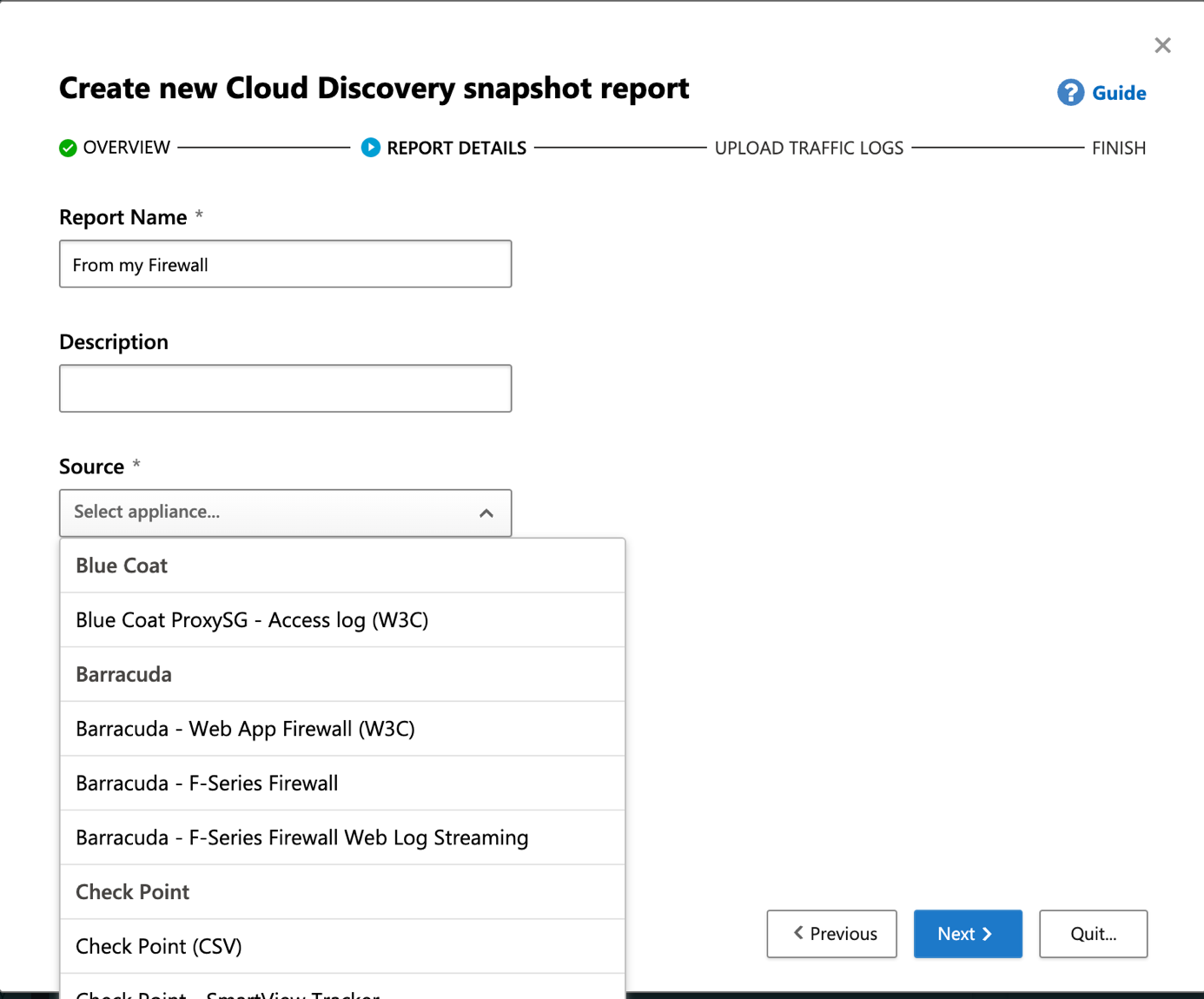
Provide a report name, a description and choose the model of your firewall. If your firewall is not in the list, you can import logs in CEF / syslog / W3C format.
Next provide the log file. After that, Microsoft Defender for Cloud Apps will process information.
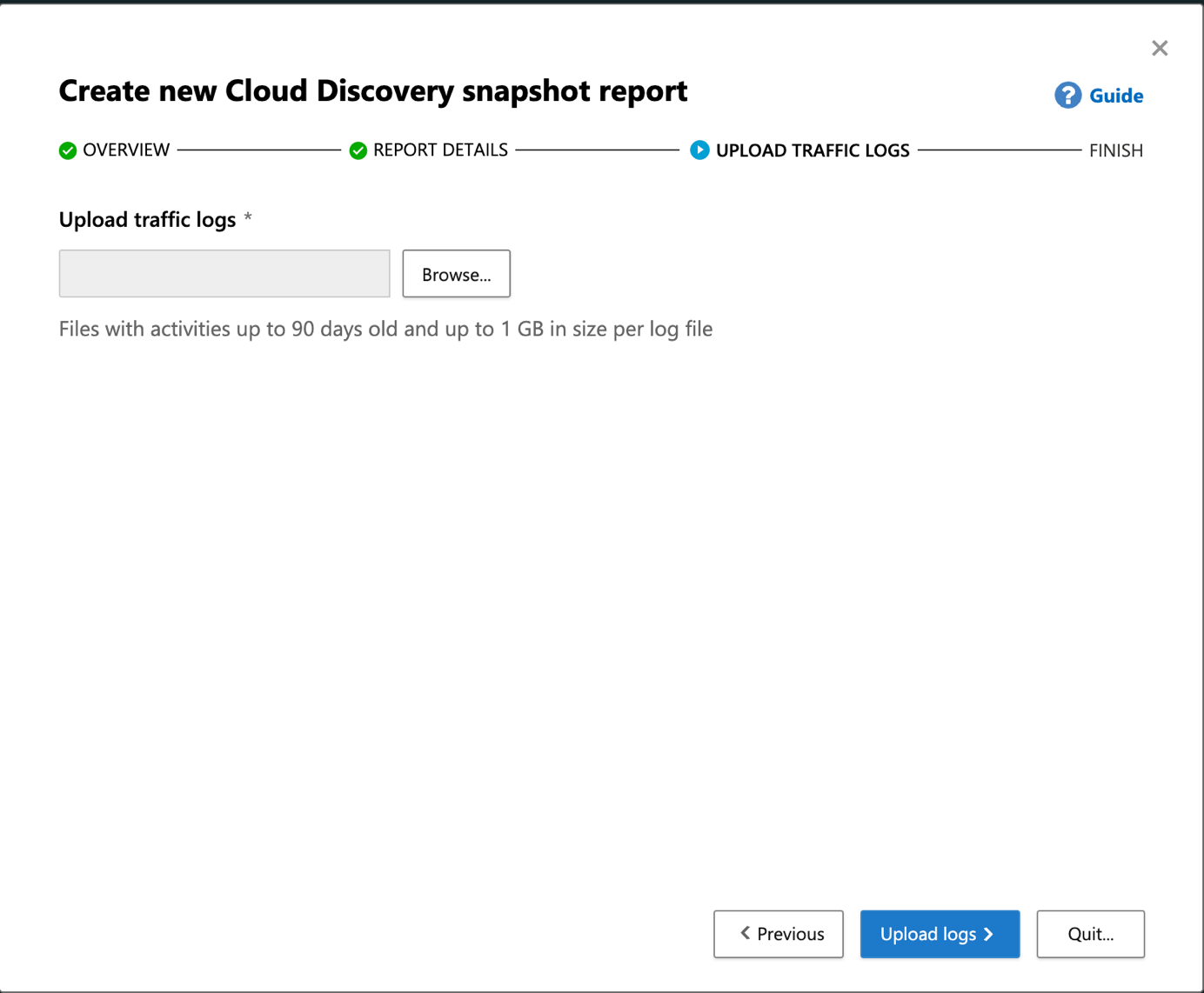
Investigate Shadow IT
Now that information are collected, you should get a dashboard with a lot of indications. You should get a list of discovered apps, the numbers, the users and so on.
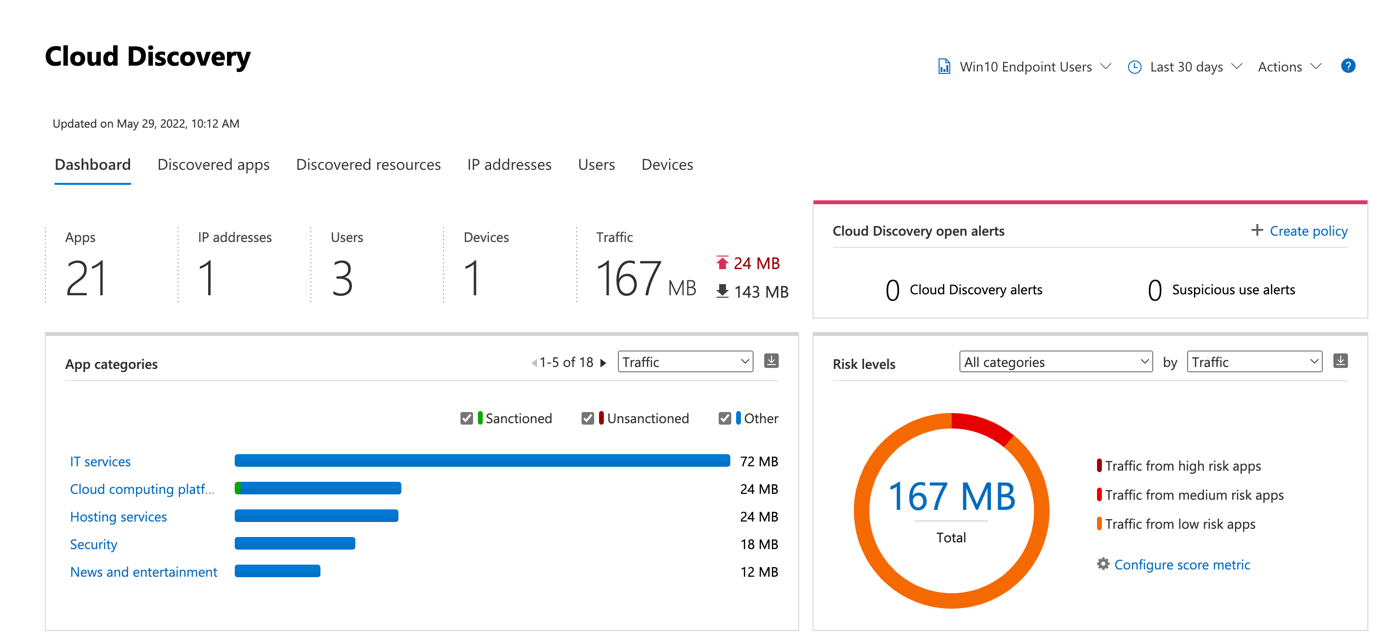
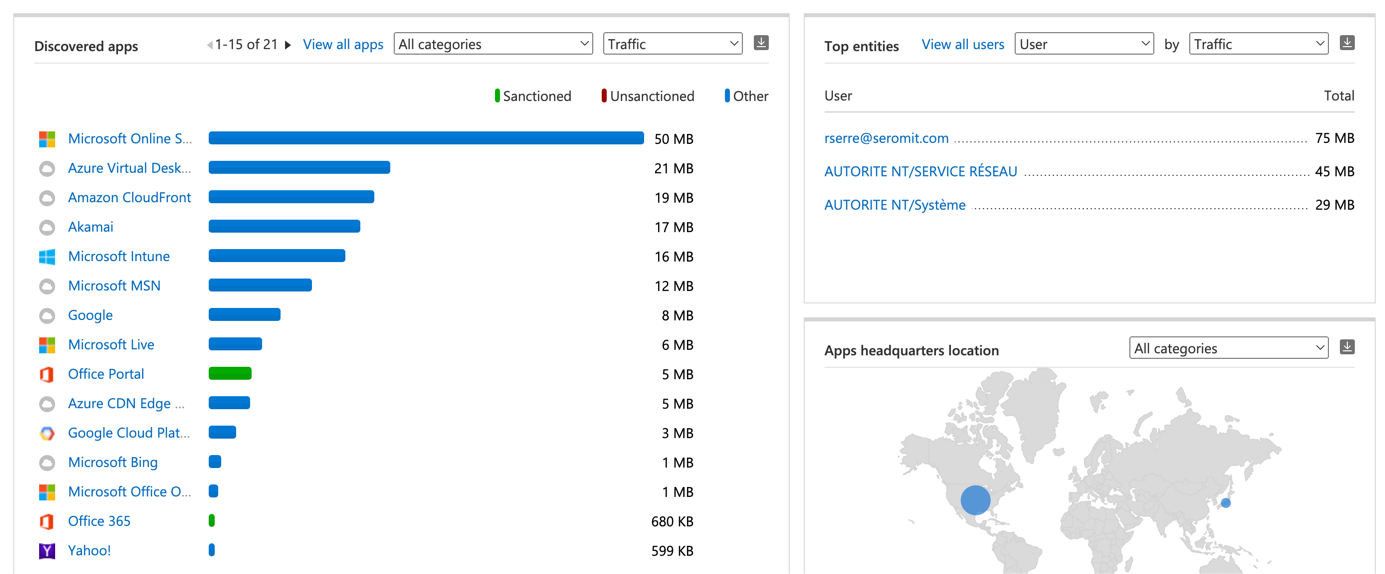
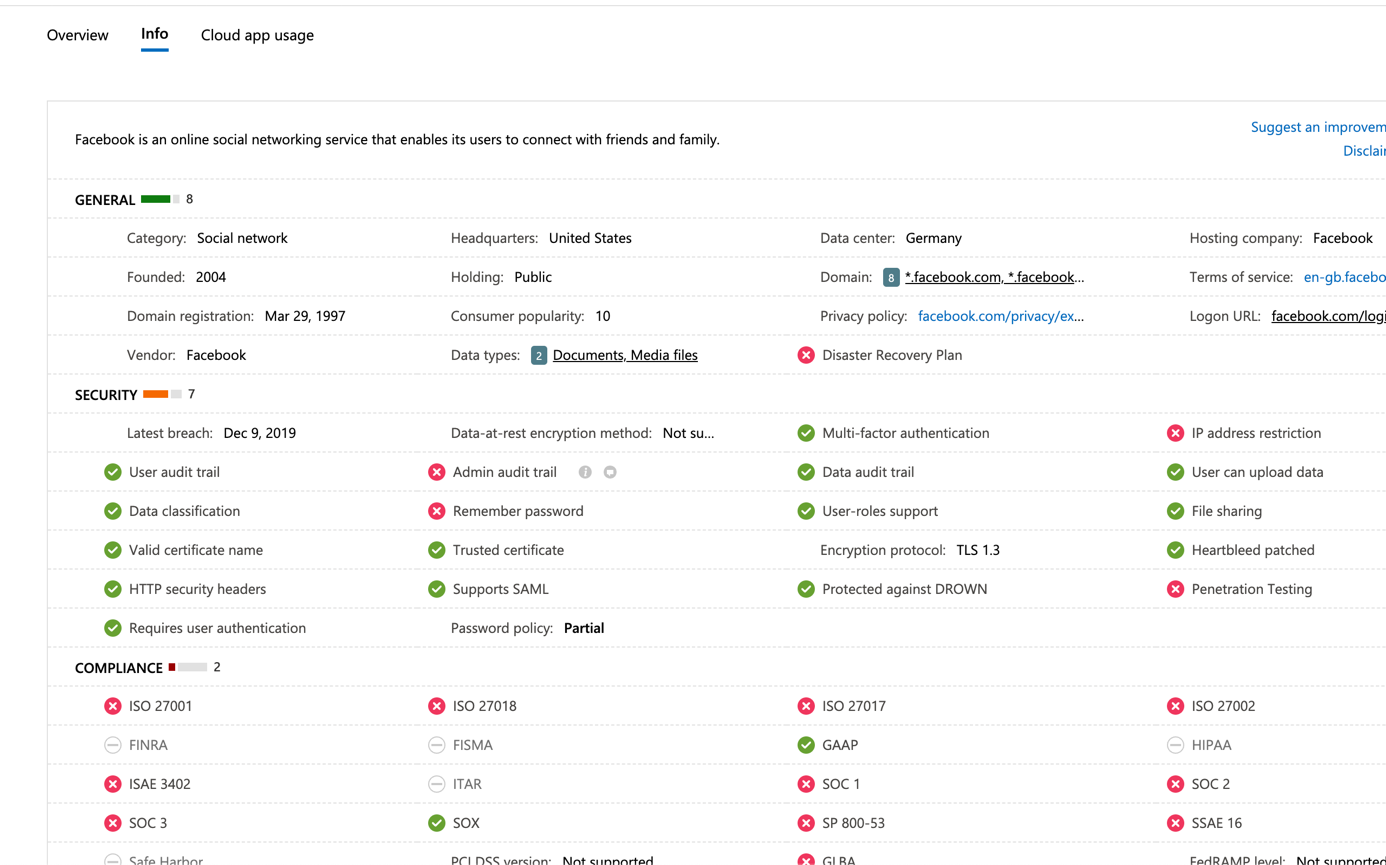
In discovered apps you should get the list of all applications used by your users. For each application you have a risk score, the traffic, the number of users that have used the applications.
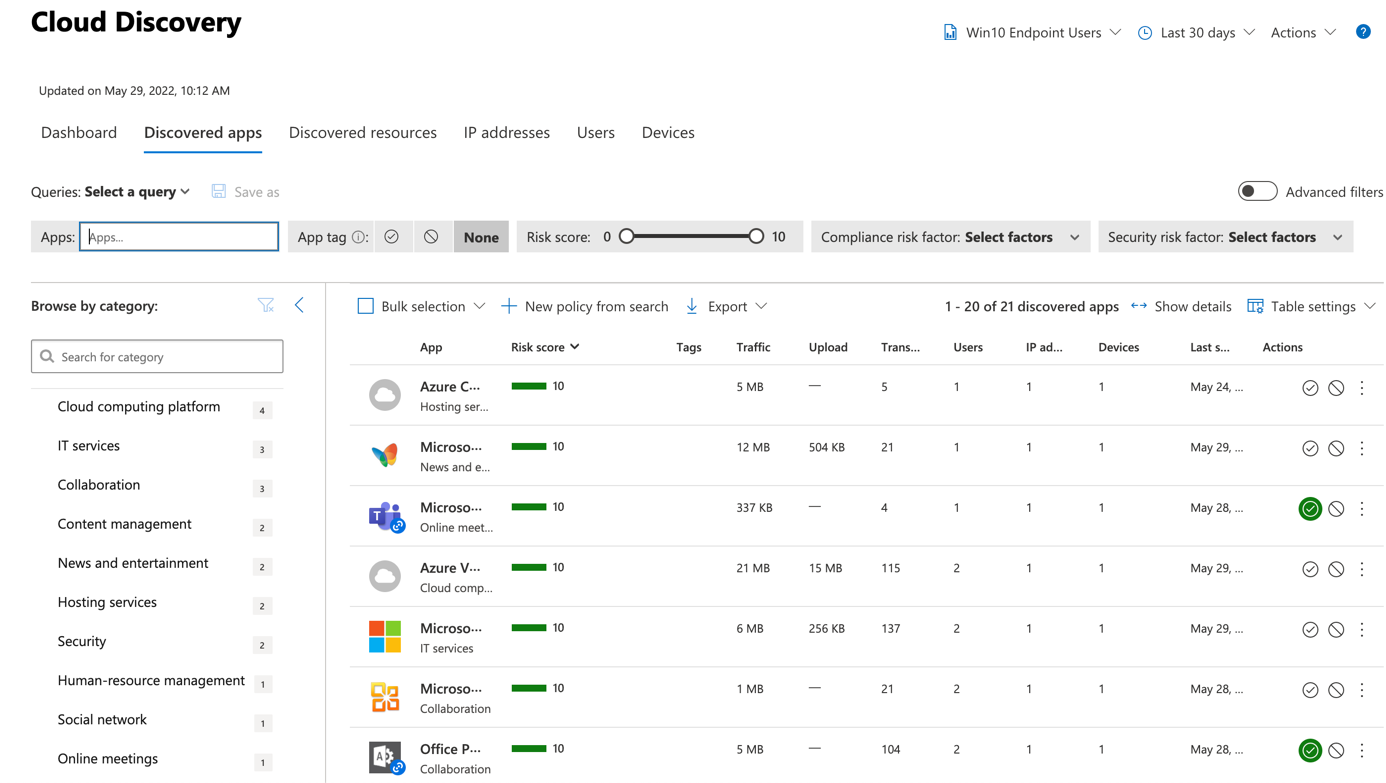
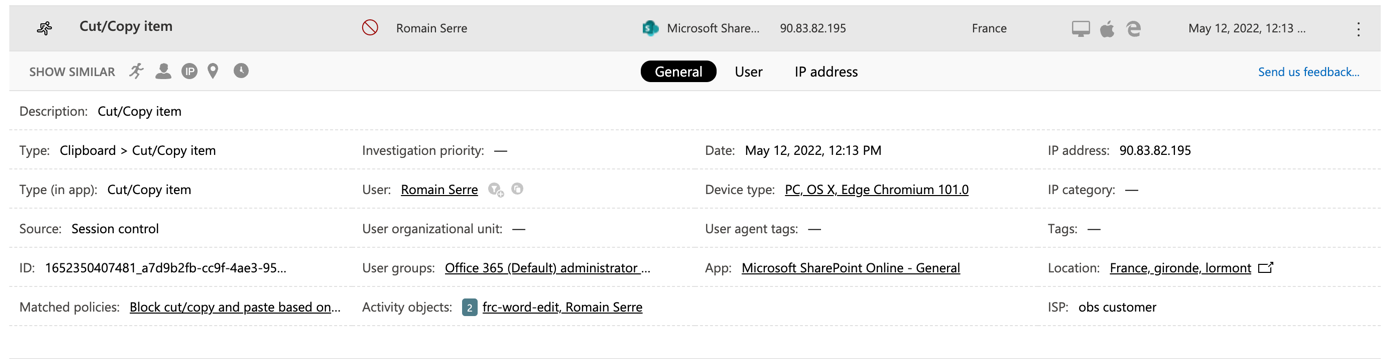
If you select an application, you can get advance information such as the detail of risk score. You can also get who are using the application and if there is any related alert.
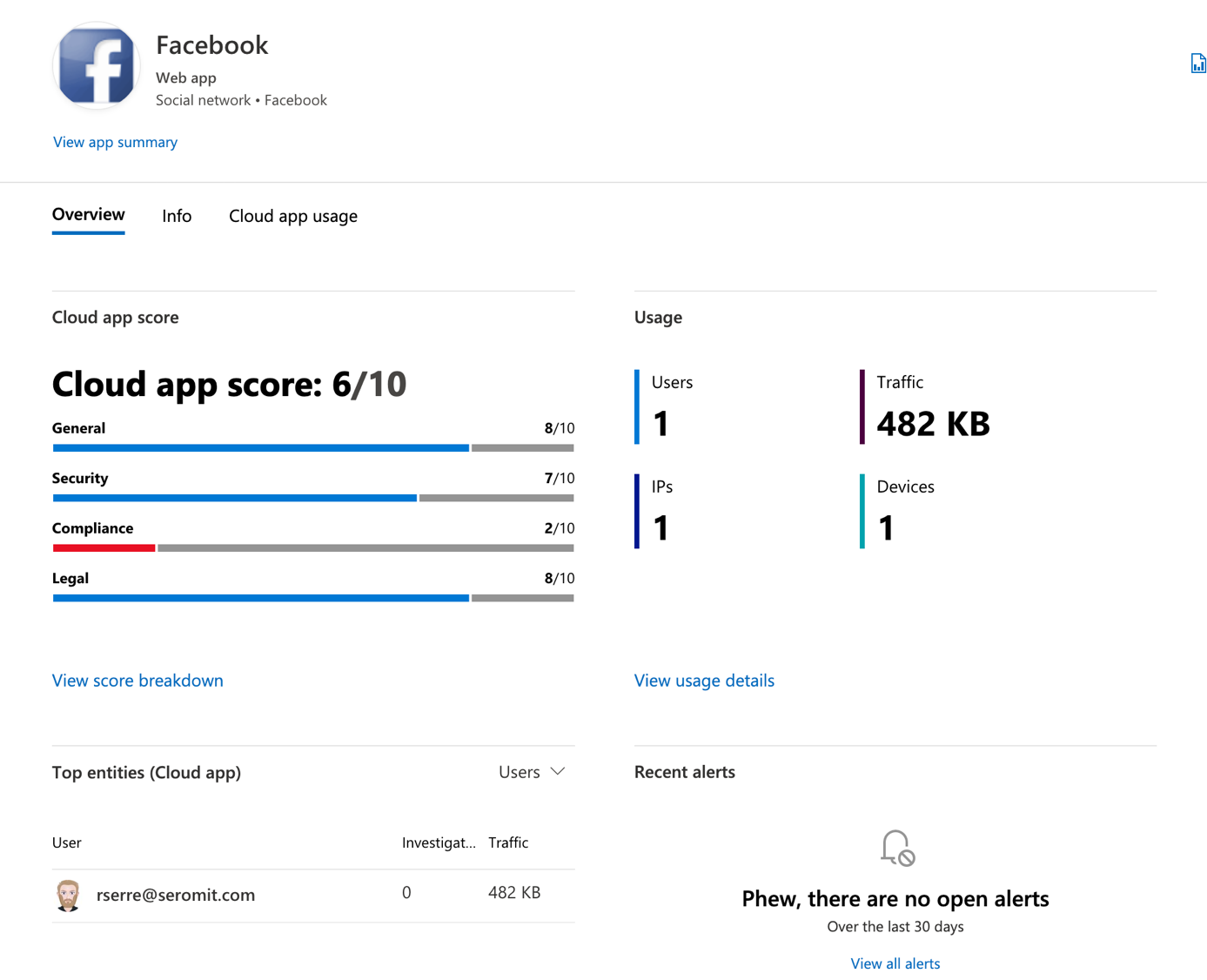
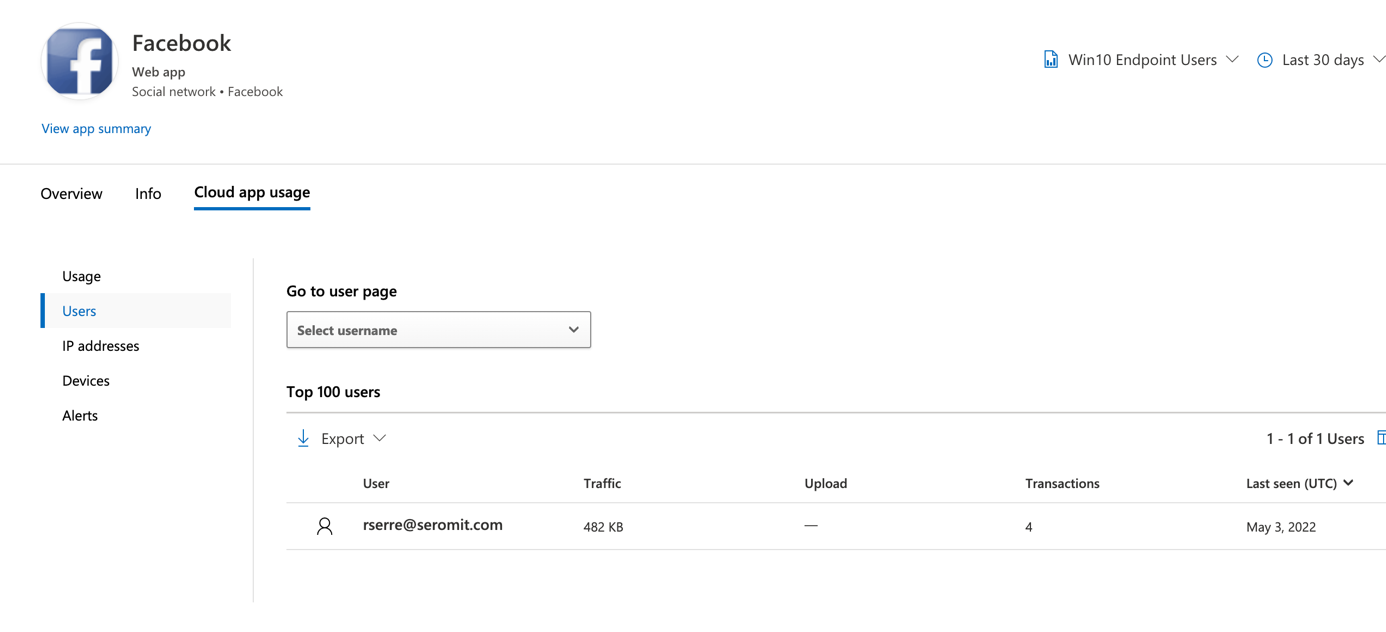
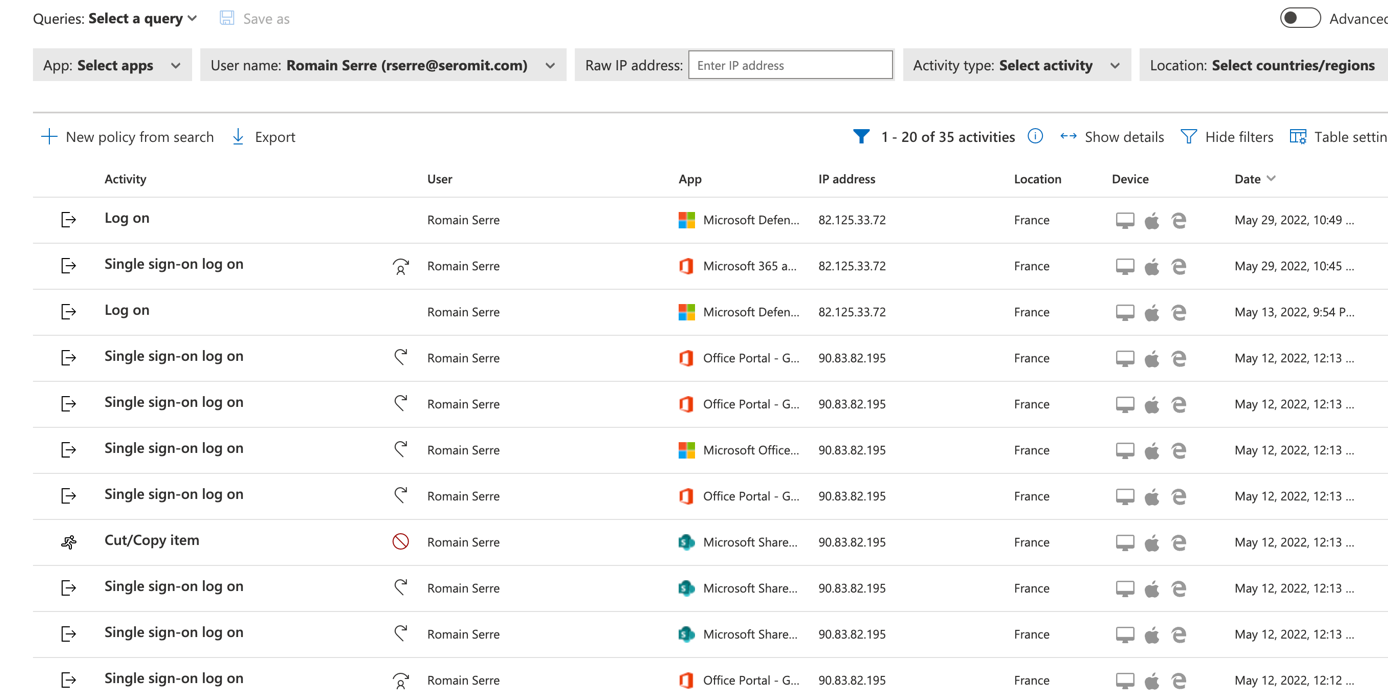
You can also get the same view user per user. That means that for each user, you can get application used
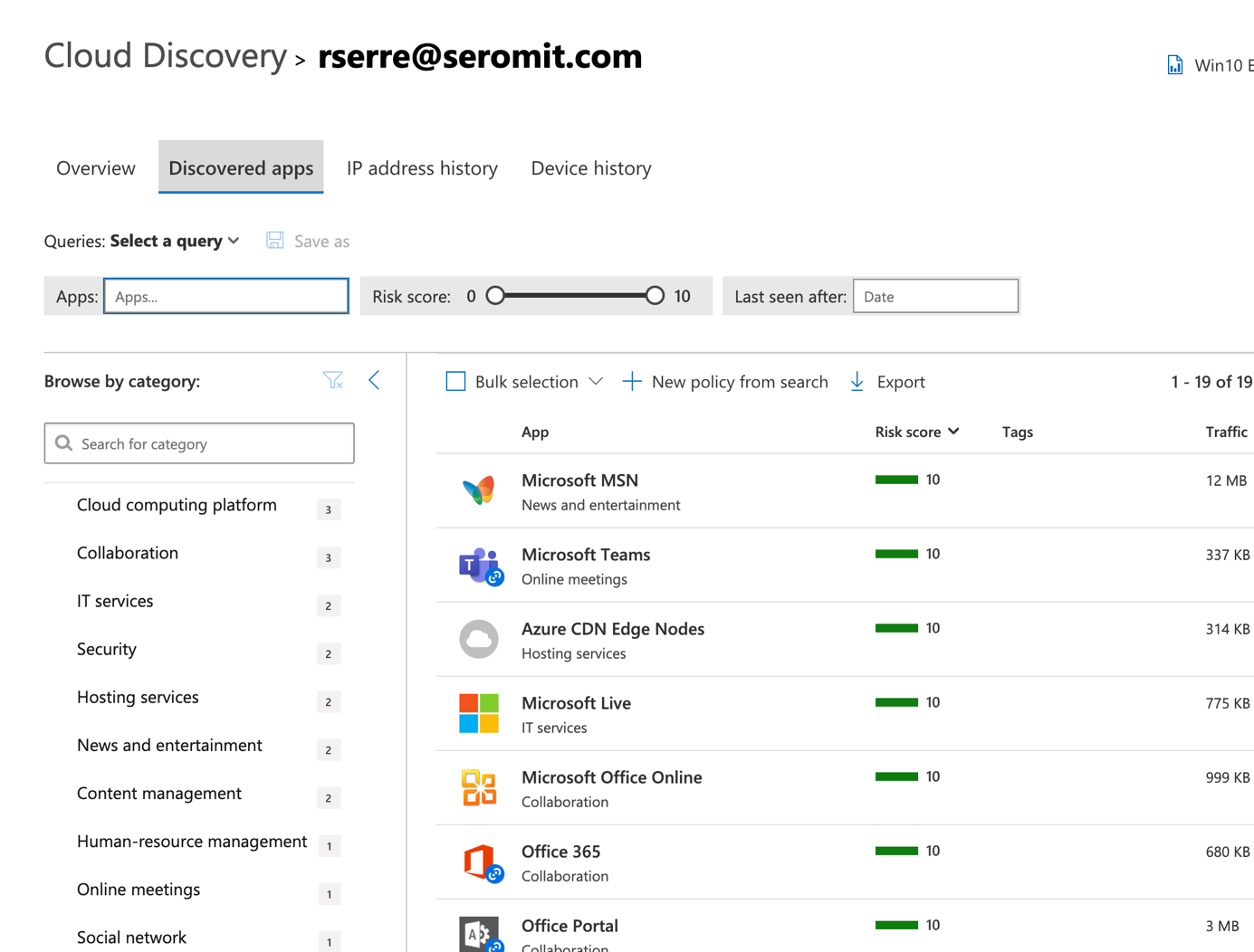
You can also get the devices from where the users connect to cloud services.
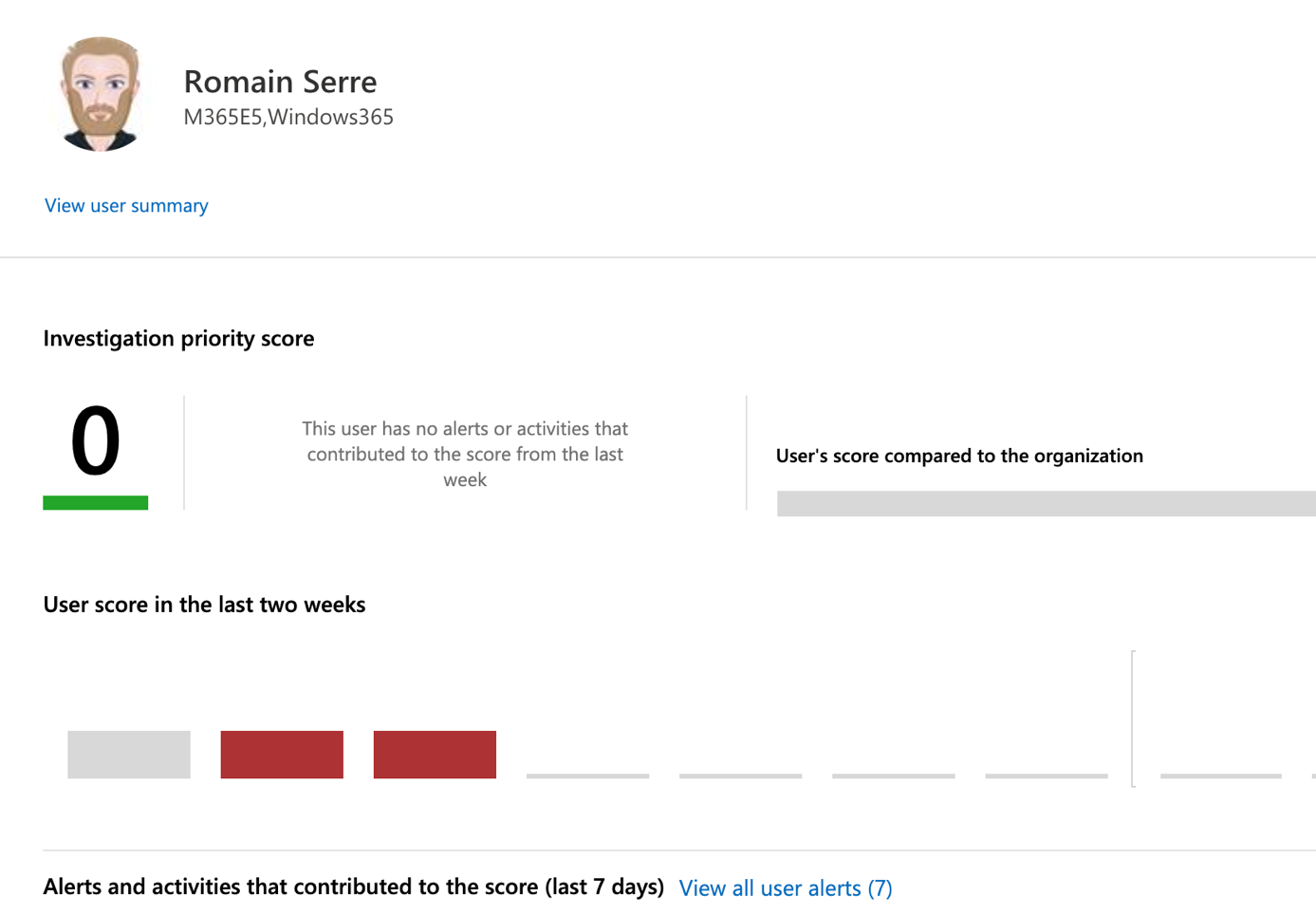
For each user, you have an investigation priority score. This score can be compared with other users in the company. If a user has a high score, you can investigate this user. The score is increased depending on activities or alerts.