Introduction
In 2017, VMware has acquired VeloCloud, a company promoting SD-WAN technology (software-defined WAN) built for organizing secured and policy-based WAN networks. Let’s keep in mind, though, that VMware already had NSX solution for corporate on-premises and cloud network environments. However, VeloCloud solutions were meant to manage the WAN infrastructure for companies in need of organizing and managing access rights for the users from different locations across the globe, often from different devices, under different security conditions and through the channels of varying reliability. Under such circumstances, organizations resources as well as external SaaS solutions are usually located in geographically dispersed data centers. Today we’re gonna talk about VMware Secure Access Service Edge (SASE) infrastructure, designed specifically to solve the problems of the new times.
After the VeloCloud purchase, VMware has integrated their technology into its own ecosystem, uniting many of the components under the umbrella of SASE platform, extended through the means of other solutions and companies, some of which have also been bought or OEMed by VMware. SD-WAN concept allows WAN network virtualization aimed to separate network services from hardware and endpoint devices, adding more flexibility, simplicity in use, performance, security, and the possibility of fast scaling out in the cloud.
How Does it Work?
As a continuation of the MPLS technology, SD-WAN allows to utilize cheap and fast network channels to the utmost extent while preserving the required level of service. SD-WAN Edge hardware is much more affordable than traditional solutions, and its simplicity won’t require the assistance of a high-qualified specialist to connect new branches.
How did it even come to be? It’s quite simple. A modern approach to organizing network communication in hybrid infrastructures and remote environments ignores several problems that have emerged in the post-COVID world of remote work. For example, let’s take a look at the following cases:
Users connect each other throughout the world, but company policies often require them to connect to a corporate data center via VPN, which is bound to create routes that are way too long. For instance, the user is trying to connect to a Microsoft Teams conference (with a Point-of-Presence in the cloud just nearby), however traffic routes are still going through the company’s data center, which may be located thousands of miles away.
Users utilize the resources provided by external SaaS providers. Let’s say that an employee needs to download a file from the colleague abroad, located in the folder in Box service. This particular country may have a local Box data center, but that employee will still have to connect to the VPN of a corporate data center in another country, which is results in an extremely long and tedious route through a secured channel.
Admittedly, these problems needed to be solved, which is exactly how the SD-WAN concept came to be, eventually becoming embodied in the SASE infrastructure. The VeloCloud Dynamic Multi-Path Optimization (DMPO) technology enable you to automatically track addresses connected by the user, find apps, and redirect them to corresponding geographical locations of service providers, utilizing all connection channels at your disposal. Thanks to the integration with the tools for identifying applications, analyzing channel performance, prioritizing traffic, and dynamic routing, DMPO can create packet-by-packet connection to provide the user with maximum speed possible. This is the thing that allows to NOT stop a Zoom call in the middle or avoid errors common for synchronizing different services.
Essentially, SD-WAN is a platform for the SASE infrastructure.
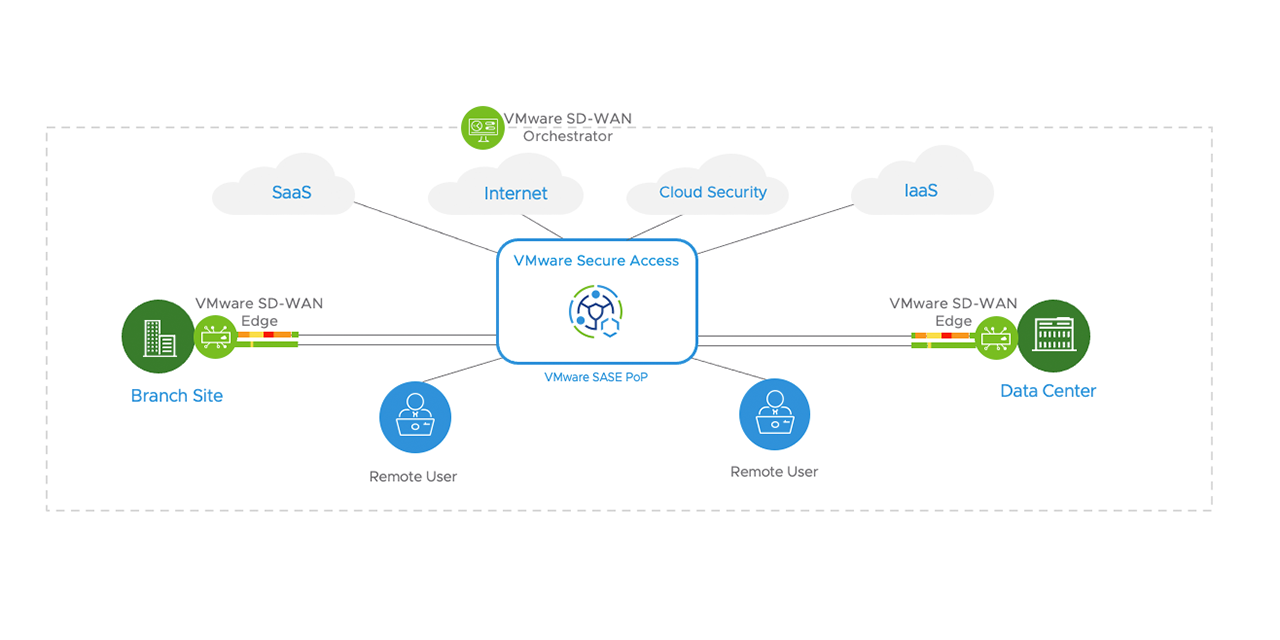
The idea of the concept is basically securing the connection to applications in geographical centers the closest to the cloud where these applications are located (public and service provider clouds). As of now, SASE has no less than 150 points of presence (PoP), wherein the cloud data centers’ hardware is actually located, providing the user with a secure and highly performative bridge to geographically localized applications’ SaaS services. Within this project, VMware has partners such as Equinix, that dispatch company’s hardware to their data centers as a co-location.
SASE components include the following solutions, open for purchase both separately and as a part of a package offered by a respective PoP:
- Gateway for the VMware SD-WAN cloud technology that is responsible for WAN networks virtualization as a means of separating software services from hardware. This component is provided by three products: VMware SD-WAN Orchestrator, a tool for managing the SD-WAN infrastructure; VMware SD-WAN Gateway, a distributed network of services gateways all over the world; and finally, VMware SD-WAN Edge – hardware and software tools for connecting to the on-premises and cloud services, for thorough packet analysis, and also for providing virtual network function (VNF) services.
- VMware Secure Access component for remote access within zero-trust network access (ZTNA) framework. This is practically a new level of VPN-alike solutions, which provides the user with brand new tools for accessing and protecting their cloud apps.
- VMware Cloud Web Security, an integrated solution based on such technologies as Secure Web Gateway (SWG), Cloud access security broker (CASB), Data loss prevention (DLP), URL filtering, and Remote browser isolation (RBI), implemented on the SASE PoP level for protecting direct access to SaaS applications and websites.
- VMware NSX Cloud Firewall, an implementation of VMware NSX next-generation firewall (NGFW) with extended functionalities such as DPI, IPS/IDS as part of the SASE services in order to guarantee additional security while accessing the on-premises applications based on the user identity.
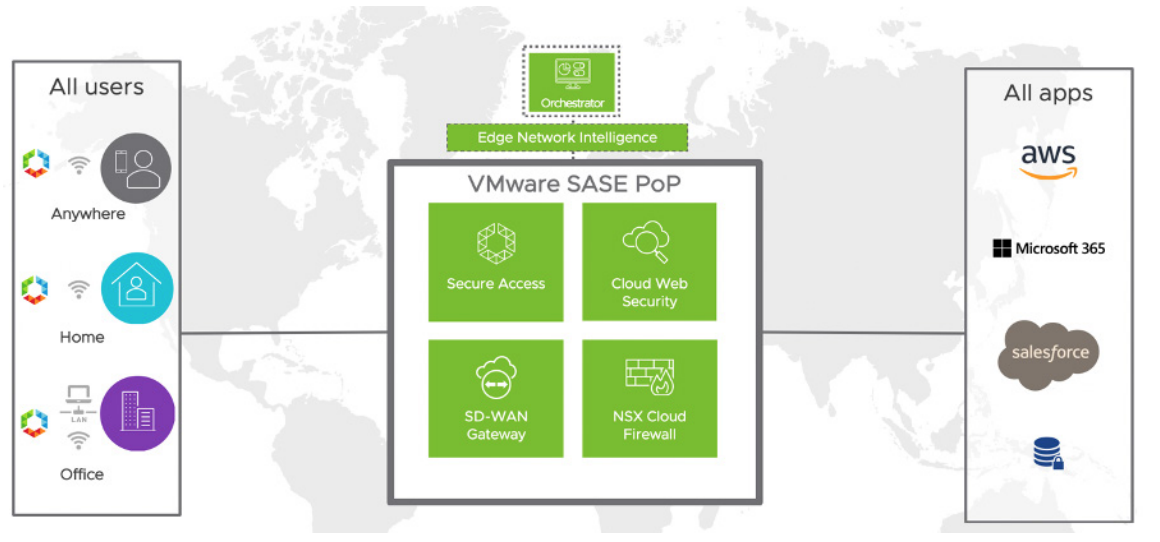
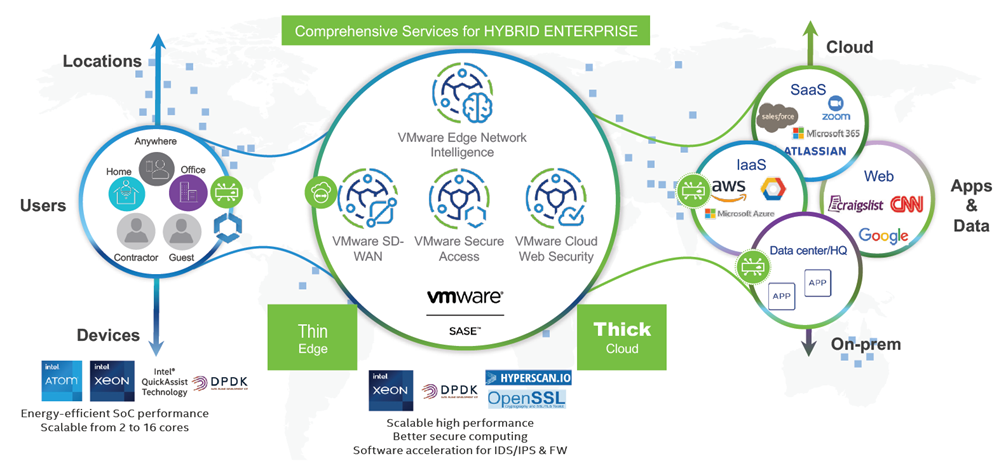
As you can see from this scheme, there is also one optional component within the SASE framework, which is called VMware Edge Network Intelligence (formerly known as Nyansa Voyance). It is a platform for monitoring connection activity and network flows as a part of the AIOps concept, which is offering to use AI/ML algorithms for analyzing network traffic in such scenarios as WAN-to-branch, WiFi/LAN, and on application level.
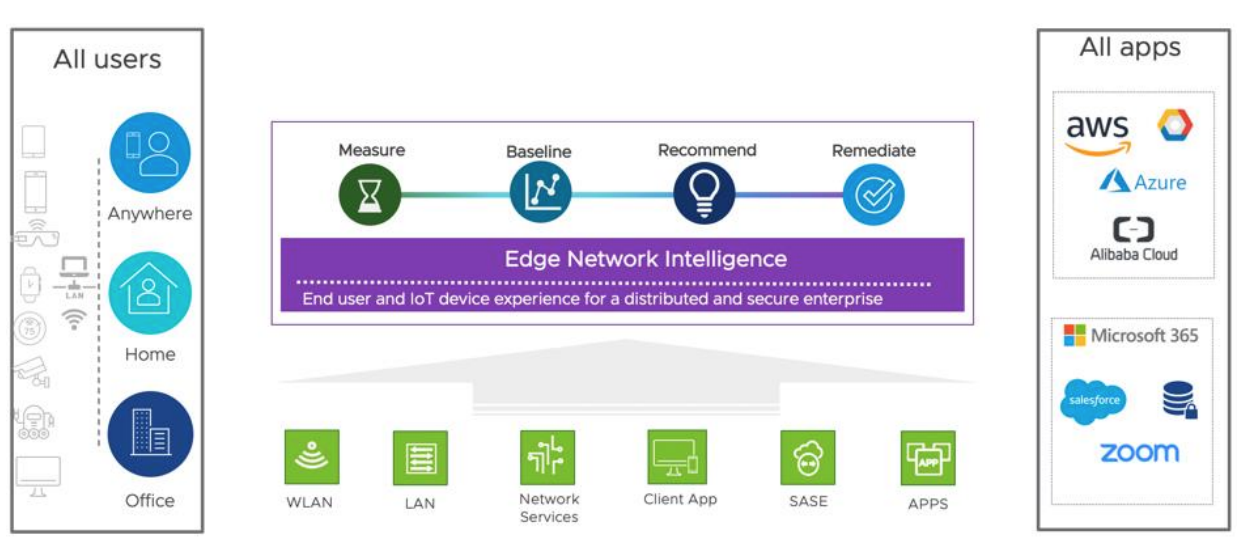
The concept of remote access needed by the users today is realized via ZTNA (zero-trust network access), that is giving trusted access right to a user based on their identity and applications working context, instead of geographic location and IP address. The main difference between ZTNA and VPN lies in the fact that ZTNA offers secured access for certain services and applications, not for the whole network as VPN does. This allows to isolate user access in the protected channels where applications can’t get data related to different network services.
If a vulnerable app is infected by malware, an attacker won’t be able to do to access other applications with the same access rights, thus not getting access to company’s confidential data. ZTNA technology is an integral part of the VMware SASE infrastructure.
VMware offers the following tools for admins to manage SASE:
- VMware Secure Access functions are realized with Unified Endpoint Management (UEM) and VMware SD-WAN Orchestrator;
- VMware Cloud Web Security and VMware NSX Cloud Firewall are managed via VMware SD-WAN Orchestrator.
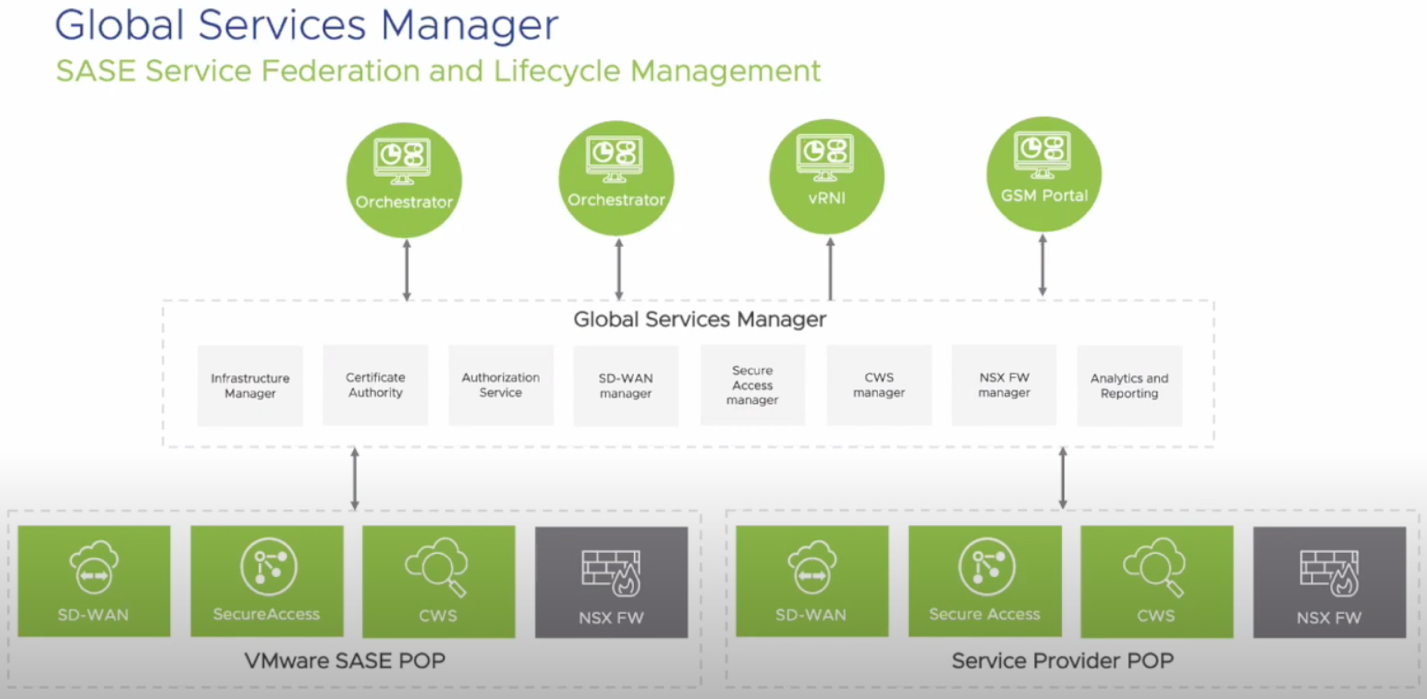
At the level of service providers offering the SASE infrastructure, these tools are integrated with the Global Services Manager functions, a tool for managing global infrastructure services and not just SASE:
Eventually, the SASE infrastructure can provide enterprises of different scale with the following benefits:
- Using cloud-native approach to deliver traffic in the most productive way within the framework of a hybrid infrastructure that utilizes both on-premises and cloud data centers;
- Offering unified secure access for remote users from different locations and branches;
- Offering contextual access based on the user’s identity, device location and security profile;
- Managing user security policies from one point.
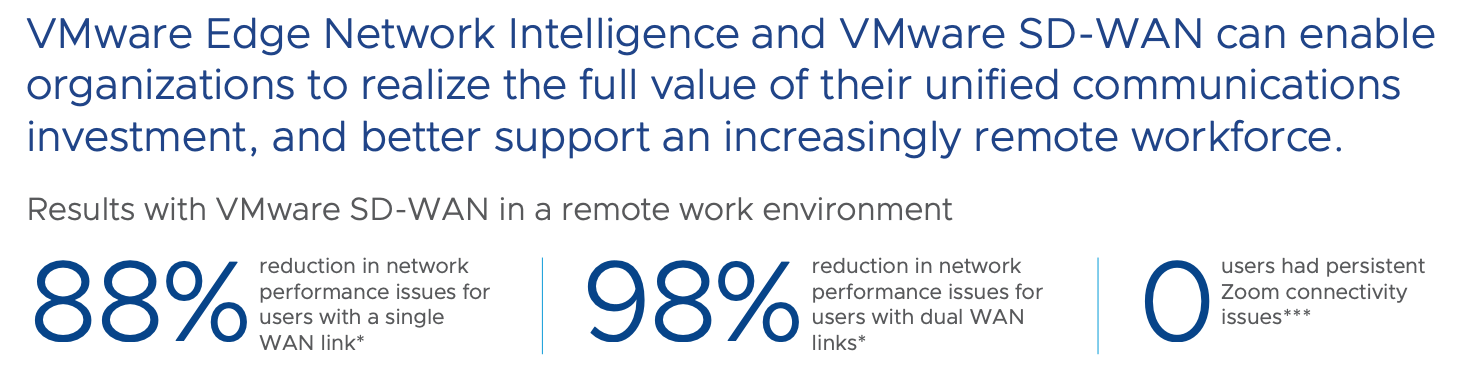
VMware gives some examples of several useful effects from configuring the SASE infrastructure and Edge Network Intelligence. Here, for instance, one of the datasheets on how this platform affects Zoom communications:
In Conclusion
Of course, you can find more details about the VMware SASE solution here. Also, you can take a look at a very interesting writing called “SASE and ZTNA for dummies”, where different use cases are analyzed in details.
If you want more specific practical examples of VMware SASE at work, check this video right here:
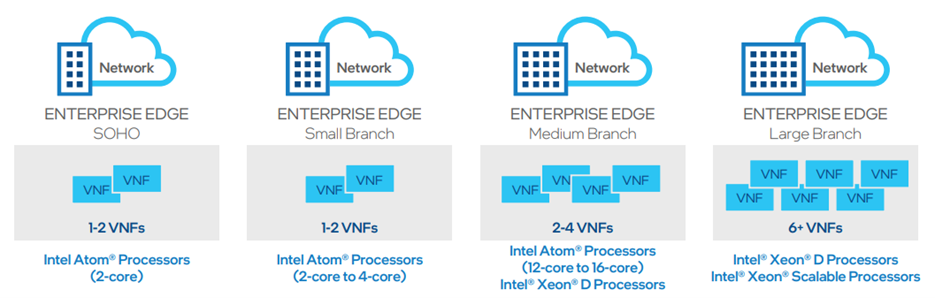
Furthermore, it won’t be excessive to take a look at “Intel architecture optimizes VMware SD-WAN Edge performance“. In this document, you can find all there is to know about using VMware Secure Access Service Edge (SASE) based on Intel hardware platforms. It describes the usage of VMware SD-WAN Edge solution on the base of various different Intel platforms based on Atom and Xeon CPUs. The necessary configuration of SD-WAN devices is explored through the optics of application requirements for the channels bandwidth and virtualized network services such as firewalls, IDS systems, etc. All these services operate as VNF (virtual network functions).