To join a Linux VM to Active Directory, the SSSD (System Security Services Daemon) component is the recommended authentication method to use for newer Linux systems.
This solution is particularly useful if Linux instant-clones are used in your VMware Horizon because SSSD allows you to access remote directories and authentication mechanisms.
SSSD is used to connect a local system to external systems, such as:
- An LDAP directory
- An Identity Management domain
- An Active Directory domain
- A Kerberos realm
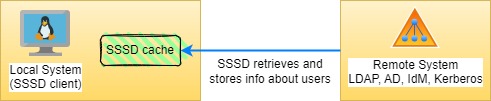
How SSSD works
The SSSD authentication process is based on two stages:
- Retrieves identity and authentication information when the client is connected to a remote provider.
- The authentication information is used to create a local cache of users and credentials on the client.
Authentication methods
There are different authentication methods that can be used for Linux virtual machines and the choice is based on the Linux distribution in use and the available infrastructure.
OpenLDAP Pass-through Authentication (PTA)
PTA can be used by any Linux distribution supported by the Horizon Agent to verify the user credentials against Active Directory using the pass-through authentication mechanism.
System Security Services Daemon (SSSD) Authentication
SSSD supports offline domain join with Active Directory for instant-cloned VMs running the following Linux distributions:
- Ubuntu 18.04/20.04/22.04
- RHEL 7.x/8.x/9.x
- CentOS 7.x
- SLED/SLES 12.x/15.x
PowerBroker Identity Services Open (PBISO) Authentication
PBISO supports offline domain join with Active Directory for instant-cloned VMs running the following Linux distributions:
- Ubuntu 18.04/20.04/22.04
- RHEL 7.x
Samba
Samba can be used by any Linux distribution supported by the Horizon Agent and supports offline domain join with Active Directory for instant-cloned. It is recommended to use Samba only for desktops running older distributions, use SSSD for newer distributions.
Pre-requisites
Before proceeding with the configuration, ensure the following prerequisites are met:
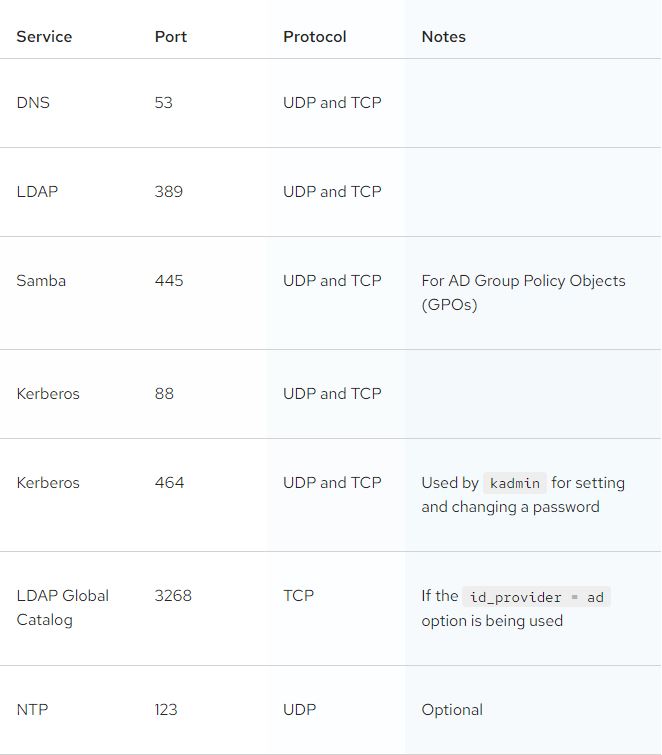
- Before discovering the AD domain to join, make sure the required ports are open in the Domain Controller and the Linux VM can access the DC.
- Both systems must be time synced to ensure that Kerberos can work correctly.
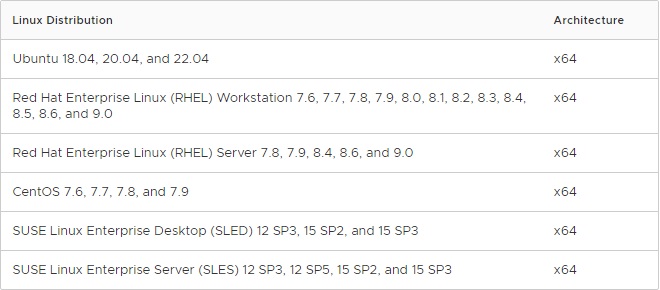
- If you work with VMware Horizon, make sure the used Linux OS is supported by the Horizon Linux Agent. Supported Linux distribution:
Install the NTP service to sync time
In this procedure the RHEL Linux distribution will be used.
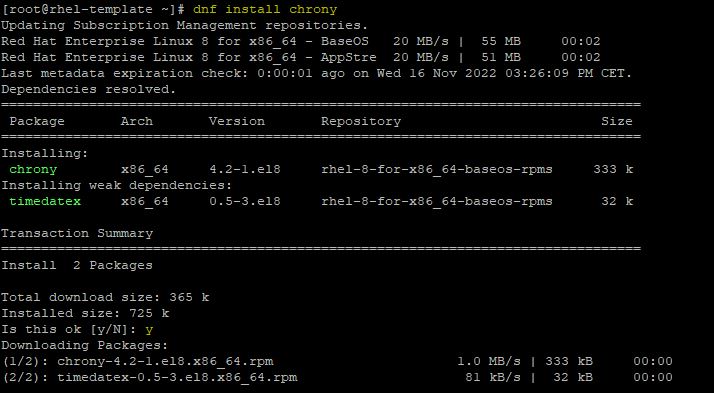
To avoid authentication issues, time among systems must be synced. From the Linux system console, install the appropriate NTP client package.
# dnf install chrony
Enable Chrony service.
# systemctl enable chronyd
Edit the file /etc/chrony.conf and make sure to specify the correct NTP server.
# vi /etc/chrony.conf
Restart the service.
# systemctl restart chronyd
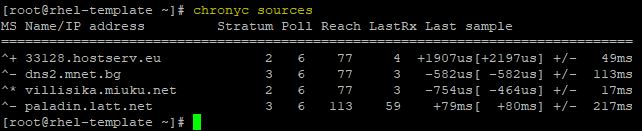
Check information about the time source configured in chrony.conf file.
# chronyc sources
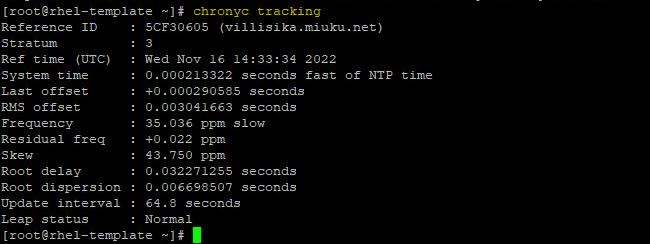
Run this command to get statistics about how far off the local system is from the reference server.
# chronyc sources tracking
Install packages for SSSD
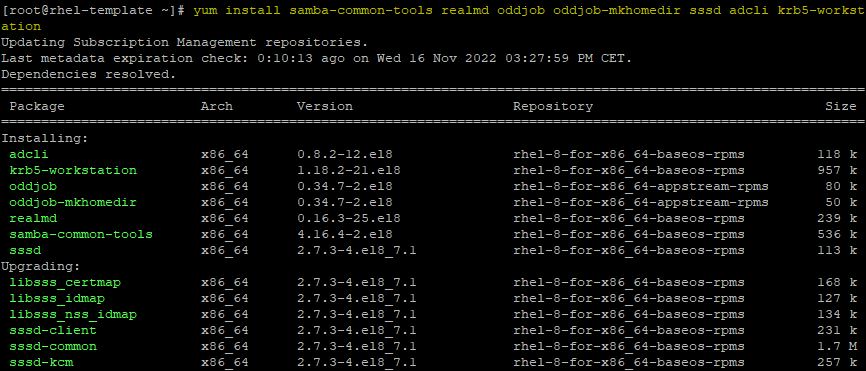
Install the following packages and type Y to proceed:
# yum install samba-common-tools realmd oddjob oddjob-mkhomedir sssd adcli krb5-workstation
Packages have been installed successfully.
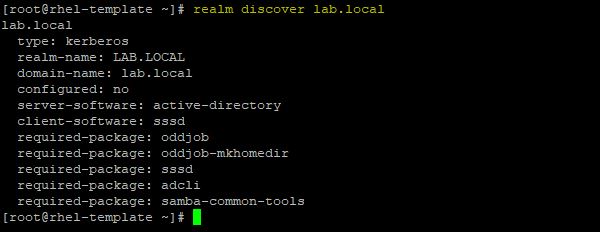
Run the following command to display info for a specific AD domain:
# realm discover lab.local
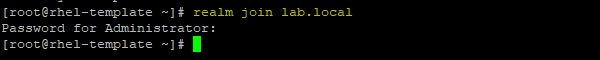
Join the system to the AD domain.
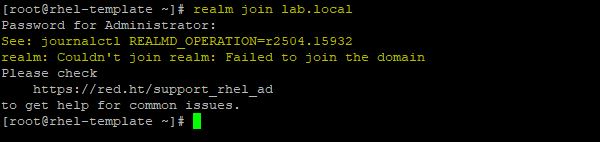
# realm join lab.local
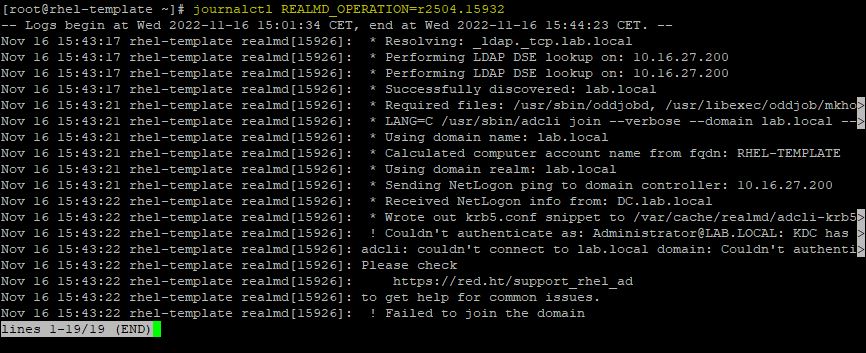
If you receive this error message, run the command reported in the description (journalctl REALMD_OPERATION=r2504.15932 in the example).
# journalctl REALMD_OPERATION=r2504.15932
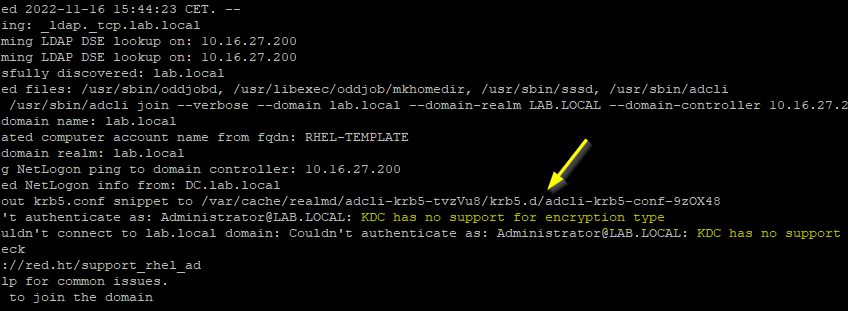
Press the right arrow in the keyboard to scroll left. In this case the error is “KDC has no support for encryption type”. This error occurs because in RHEL8 krb5 does not support RC4 anymore.
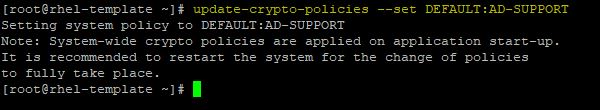
To fix this issue, run the following command:
# update-crypto-policies –set DEFAULT:AD-SUPPORT
Now try to join the system to the AD domain once again.
# realm join lab.local
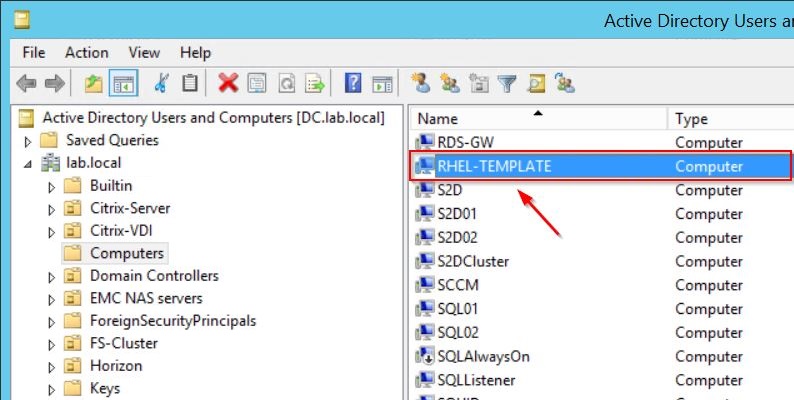
The Linux machine is now joined to the Active Directory using the SSSD component as you can see in the Active Directory Users and Computers console.
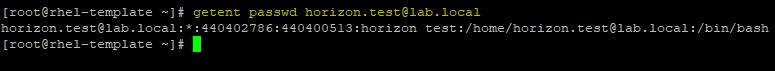
To check if the system is able to properly communicate with the domain, run the following command to display details for a specific user:
# getent passwd horizon.test@lab.local
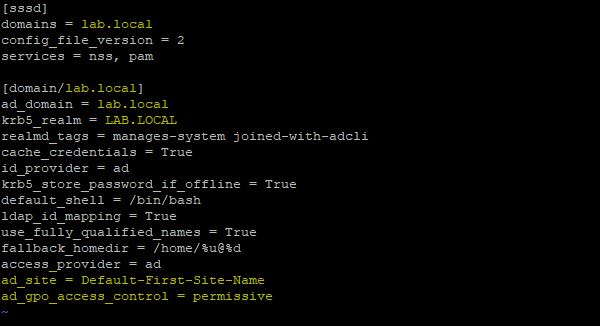
Now edit the file /etc/sssd/sssd.conf and make sure that mydomain is replaced with the correct DNS name of the AD domain. If you have multiple AD sites, specify the correct site name to avoid authentication errors. Specify also the mode in which the GPO-based access control runs (permissive value specifies that GPO-based access control is evaluated but not enforced).
ad_site = <sitename>
ad_gpo_access_control = permissive# vi /etc/sssd/sssd.conf
Configure Kerberos
To configure Kerberos, krb5 support libraries must be installed in the system (if missing, use the command yum install krb5-workstation to install the required package).
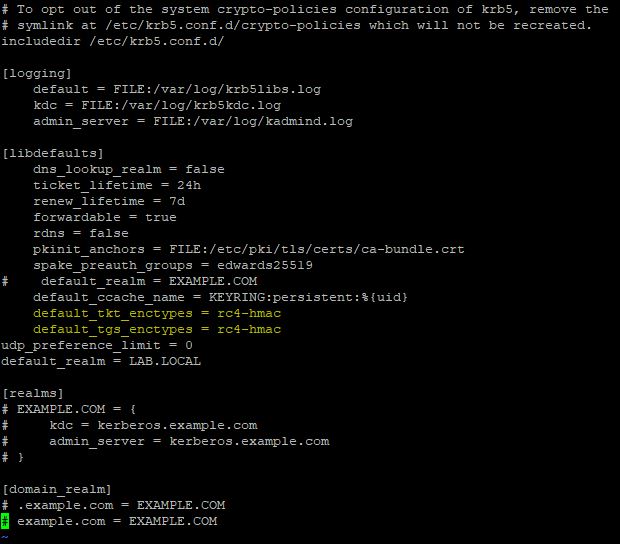
If you are using RHEL/CentOS 7.x, Ubuntu 18.04 or SLED/SLES 12.x distributions, edit the /etc/krb5.conf file and change the configuration to use only the rc4-hmac encryption algorithm. Add the following two lines:
default_tkt_enctypes = rc4-hmac
default_tgs_enctypes = rc4-hmac
# vi /etc/krb5.conf
Reboot the machine.
#reboot
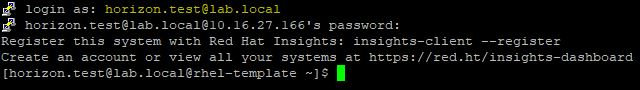
After the reboot, test the login to the Linux VM using an AD account.
The user is successfully authenticated against Active Directory.
Install Horizon Agent if required
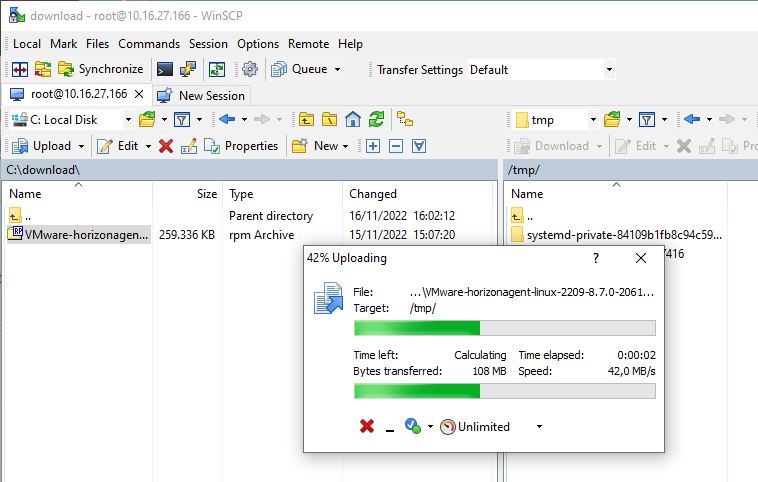
If the configured VM is intended to be used as Golden Image in a VMware Horizon environment, download the Horizon Agent from VMware website and copy it to the RHEL machine using a tool like WinSCP. Since Linux VDI supports Blast protocol only, if you use Thin Clients to connect your VDIs, make sure Blast protocol is supported.
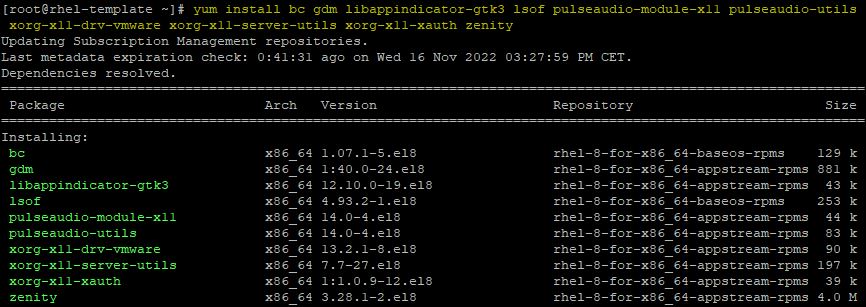
The Horizon Agent package has some dependencies that must be installed in the system before running the installation. Normally you need to install these packages only if the system has a minimal installation setup.
# yum install bc gdm libappindicator-gtk3 lsof pulseaudio-module-x11 pulseaudio-utils xorg-x11-drv-vmware xorg-x11-server-utils xorg-x11-xauth zenity
When the dependencies have been installed, install the Horizon Agent.
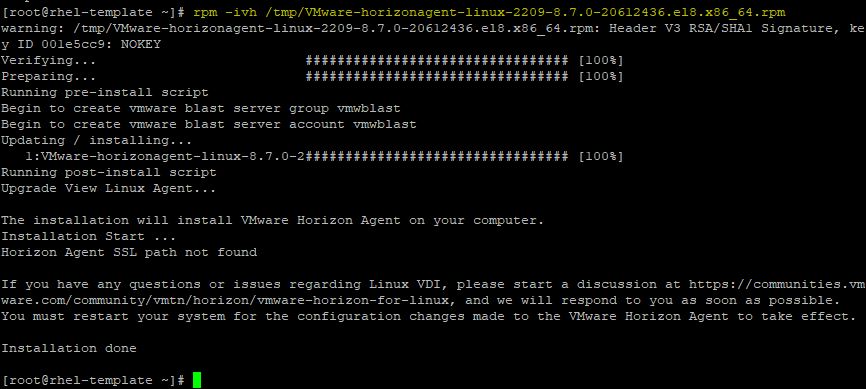
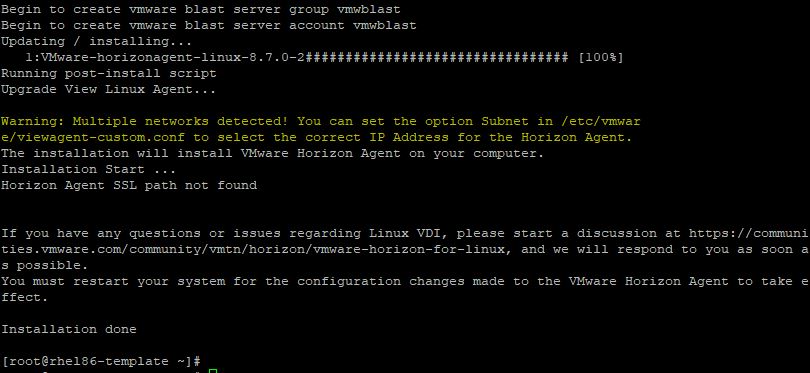
# rpm -ivh /tmp/VMware-horizonagent-linux-2209-8.7.0-20612436.el8.x86_64.rpm
If you have multiple networks, you may receive this warning during the Horizon Agent installation.
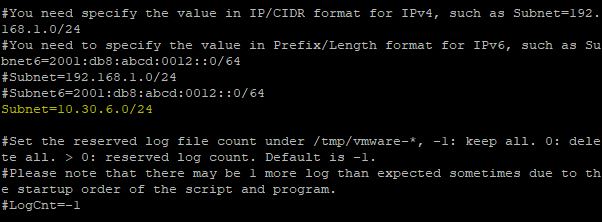
Edit the /etc/vmware/viewagent-custom.conf file and specify the correct subnet:
# vi /etc/vmware/viewagent-custom.conf
Enable also the following line:
OfflineJoinDomain=sssd
When the Horizon Desktop Pool is configured, the Linux instant-clone desktop will be created and joined to AD domain using SSSD. Use the AD credentials to login to the VDI.
Also the Linux instant-clone machine can be accessed by Active Directory users. For newer versions of Linux systems, SSSD is the recommended method of authentication against Active Directory.