Microsoft released a new feature called authentication strengths that enables to define the authentication methods allowed for a group of users. This feature is used in conditional access to apply the policies to the right people.
In this topic we will see how to use authentication strengths in Azure AD.
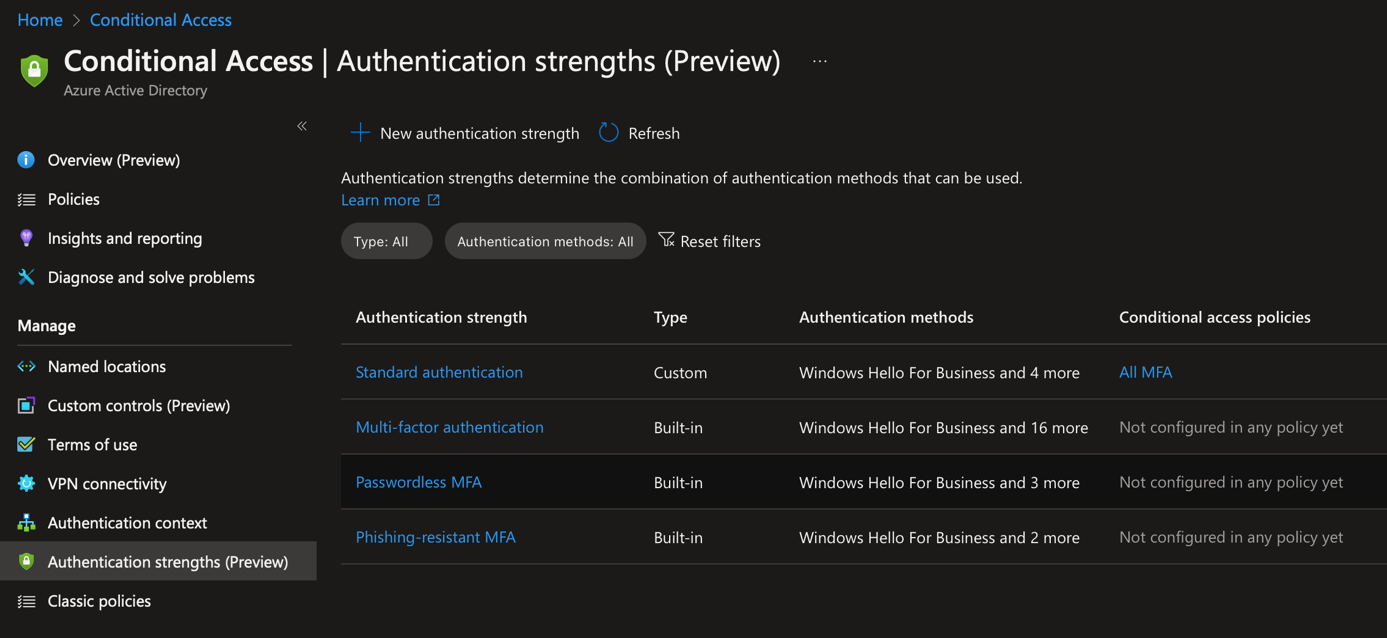
Create authentication strengths
Authentication strengths comes with three built-in policies:
- Multi-Factor authentication: all authentications that support MFA
- Passwordless authentication: Microsoft Authenticator (phone sign-in), FIDO2 and certificate-based authentication
- Phishing-resistant authentication: only FIDO2 and certificate-based authentication
You can also create your own custom policies. To do that, navigate in Entra (https://entra.microsoft.com) in Protect & Secure > Conditional Access > Authentication Strengths. From there, click on New authentication strength.
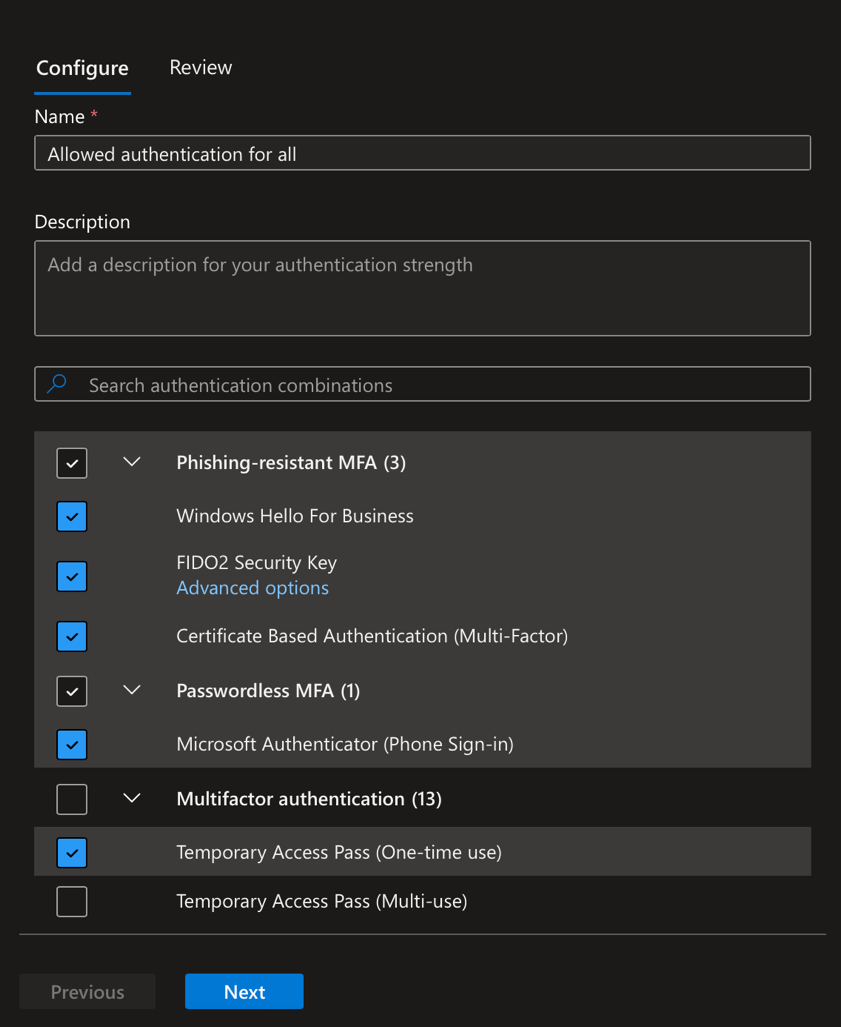
Then provide a name and select the authentication method you want to allow. Usually, I allow FIDO2, certificate-based, Microsoft Authenticator (phone sign-in) and temporary access password (One-time use).
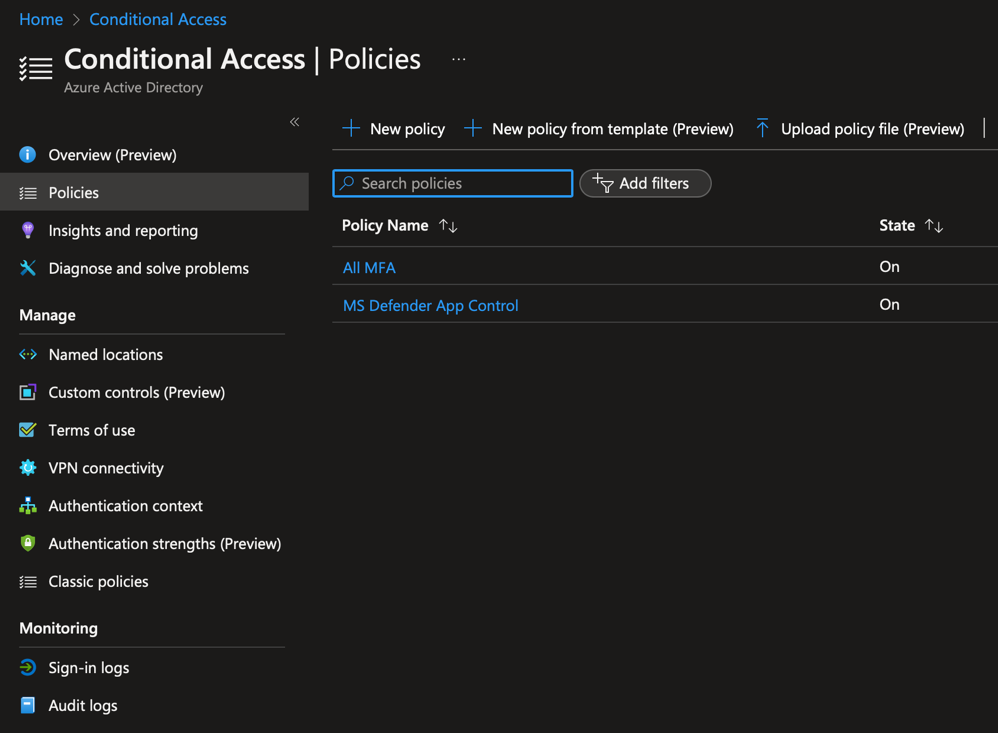
Use authentication strengths in conditional access
Now that the authentication strength is created, we can use it in conditional access. To do so, navigate into policies and create a new conditional access by clicking on new policy.
Provide a name to the conditional access:
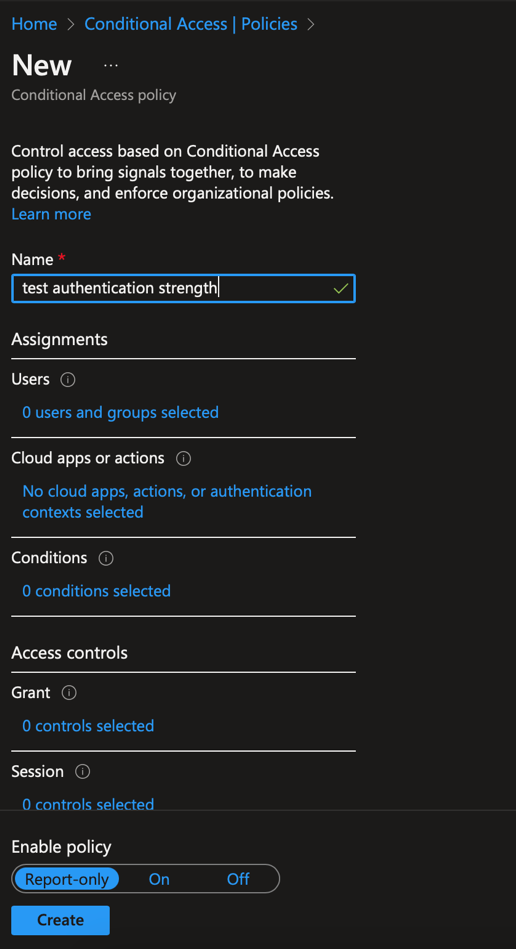
In users, select the groups, roles or users on which authentication strength will be applied.
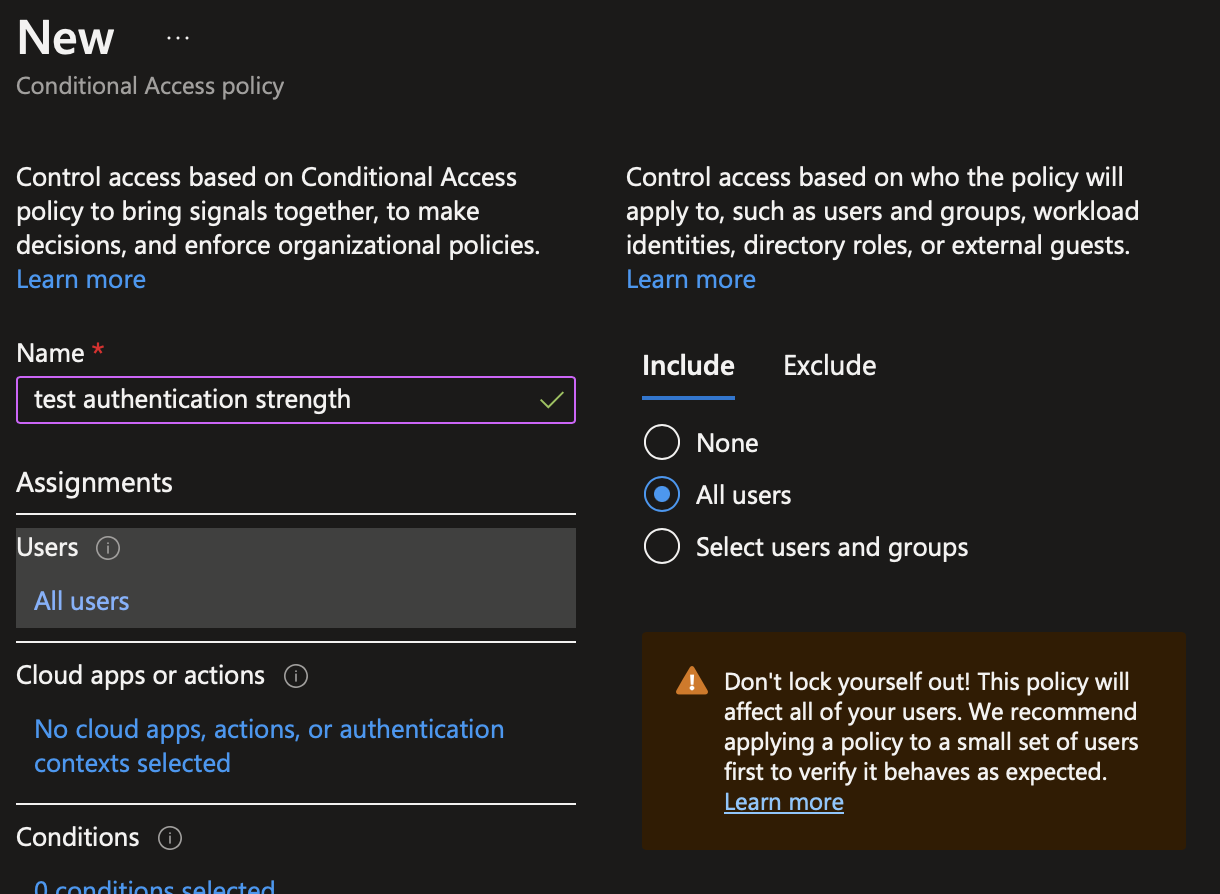
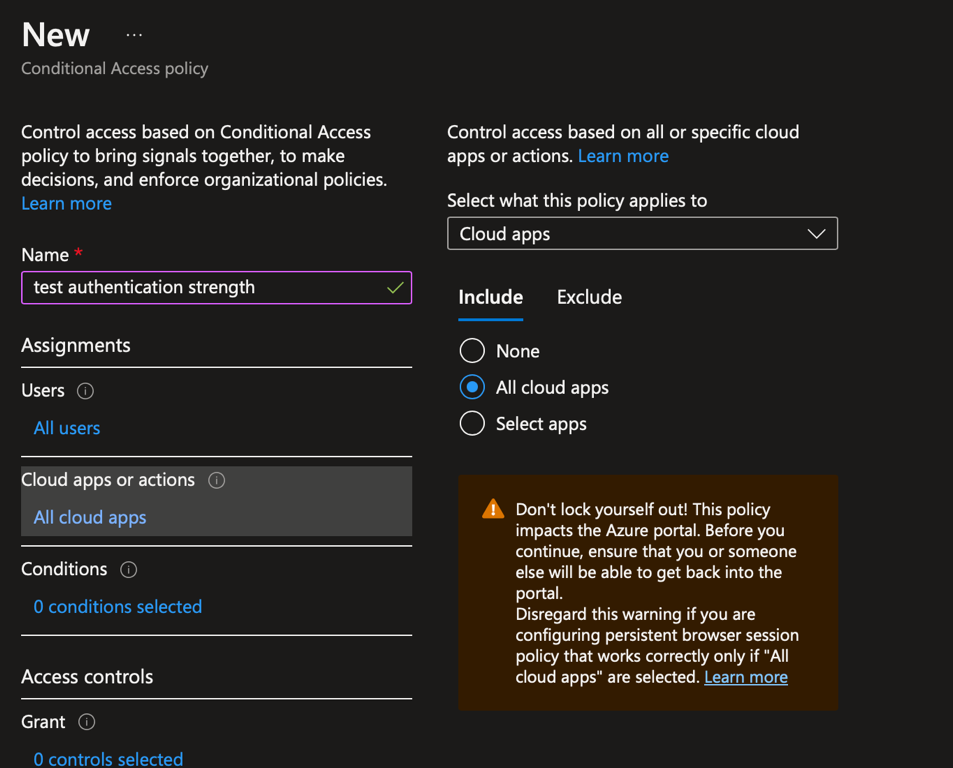
Usually when you create a conditional access to configure authentication, this policy is applied to all cloud apps. In this case, select all cloud apps in Cloud apps or actions. In any other cases, select the cloud apps on which the authentication strength will be applied.
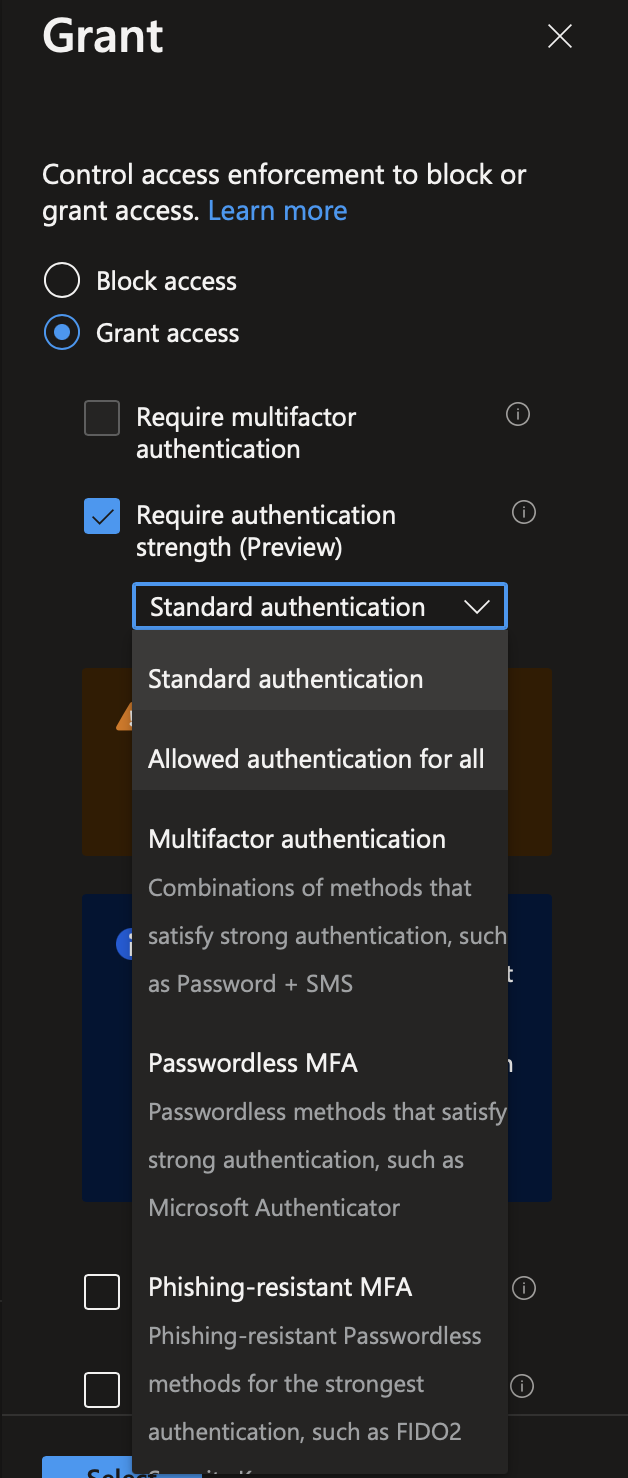
In grant, select grant access and tick require authentication strength. Then select the authentication strength you want to apply.
Once you have enabled this conditional access, the authentication strength will be applied to users.
My opinion
Authentication strengths is a great addition to Azure AD. Thanks to this feature you can disable easily deprecated or vulnerable authentication methods such as SMS or phone. You can also have different authentication strengths in your company. For example, for users that manage sensitive information you can enforce FIDO2 and certificate-based authentication. For users who don’t work on sensitive information, you can allow Microsoft Authenticator.
Currently authentication strength is still in preview, so use it in test environment. Once this feature is in GA, you should use this feature especially to disable SMS and phone authentication 😊


