From December 2015, Microsoft has given the possibility to create your own RBAC roles. I will show you today, how to do this. To start, connect via PowerShell to your Azure RM subscription:
| Login-AzureRm Select-AzureRmSubscription -SubscriptionId XXXXXXXXXXXXXXXXXXXXX |
When you are connected, you can get the list of Resource Providers that are available with the following command:
| Get-AzureRmResourceProvider | FT ProviderNameSpace,ResourceTypes |
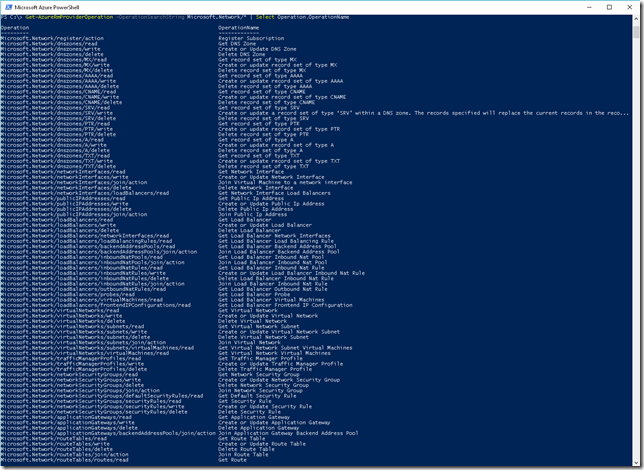
That I want here is pretty easy. The user/group that will be in the role that I will create will be able to create/delete network cards and read/join network security group as well as virtual network. I will use the Resource Provider Microsoft.Network to do this. To have the list of all available operations, use the following command:
| Get-AzureRmProviderOperation -OperationSearchString Microsoft.Network/* | Select Operation,OperationName |
Here, actions that interest me are the following:
- Network/networkInterfaces/read
- Network/networkInterfaces/write
- Network/networkInterfaces/delete
- Network/networkSecurityGroups/read
- Network/networkSecurityGroups/join/action
- Network/virtualNetworks/read
- Network/virtualNetworks/subnets/read
- Network/virtualNetworks/subnets/join/action
The first 3 bullets concerned the fact the create/read/delete network card, the 4th and 5th concerned the fact to read NSG and join them and, finally, the last 3 bullets are to read virtual networks, subnets and to get an IP in the pool.
To store network cards, the user need to have the right to write in the Resource Group, and so, to read it. You will add the following 2 lines:
- Resources/deployments/read
- Resources/deployments/write
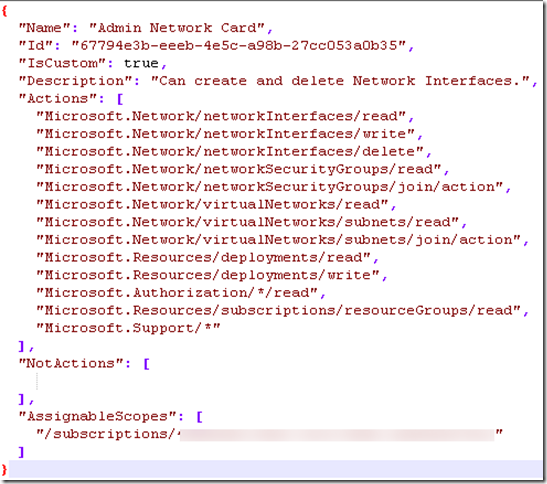
Now that we have all actions, we can create the following JSON file:
| { “Name”: “Admin Network Card”, “Id”: “67794e3b-eeeb-4e5c-a98b-27cc053a0b35″, “IsCustom”: true, “Description”: “Can create and delete Network Interfaces.”, “Actions”: [ “Microsoft.Network/networkInterfaces/read”, “Microsoft.Network/networkInterfaces/write”, “Microsoft.Network/networkInterfaces/delete”, “Microsoft.Network/networkSecurityGroups/read”, “Microsoft.Network/networkSecurityGroups/join/action”, “Microsoft.Network/virtualNetworks/read”, “Microsoft.Network/virtualNetworks/subnets/read”, “Microsoft.Network/virtualNetworks/subnets/join/action”, “Microsoft.Resources/deployments/read”, “Microsoft.Resources/deployments/write”, “Microsoft.Authorization/*/read”, “Microsoft.Resources/subscriptions/resourceGroups/read”, “Microsoft.Support/*” ], “NotActions”: [], “AssignableScopes”: [ “/subscriptions/XXXXXXXXXXXXXXXXXXX” ] } |
Obviously, modify XXXXXXXXXXXXX with the number of the subscription where it will be possible to use this role. You can add multiple subscription. You can also change the Name and Description
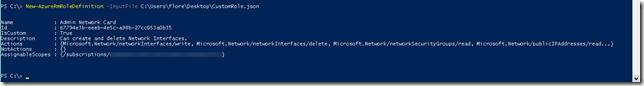
Save this file with the extension .json and use the following command to import it:
| New-AzureRmRoleDefinition -InputFile C:\Users\flore\Desktop\CustomRole.json |
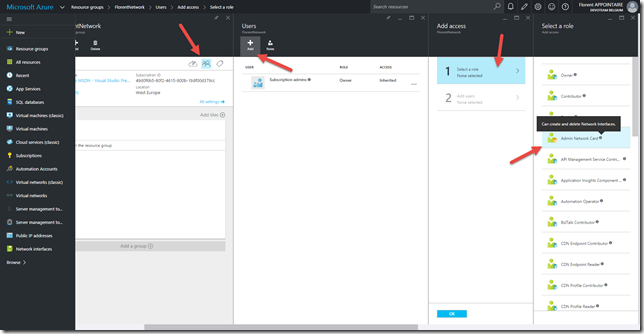
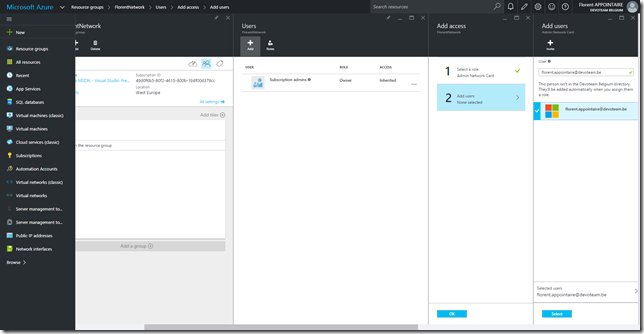
With an administrator account, go in the resource group where the role will be applied and add the new role by clicking on Access > Add > Select a role:
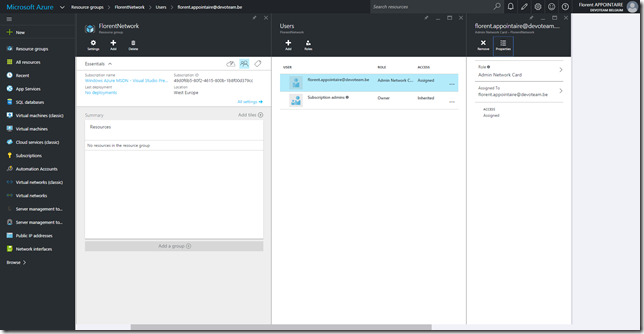
Add the account/group that will have the possibility to deploy network cards:
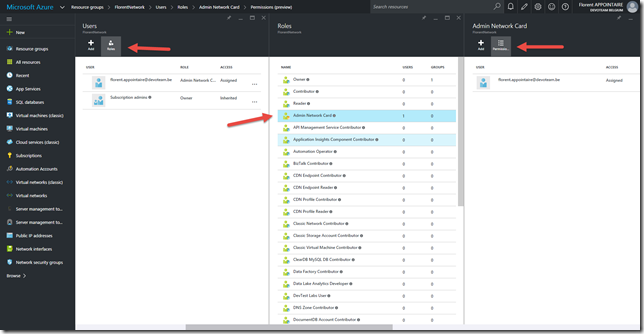
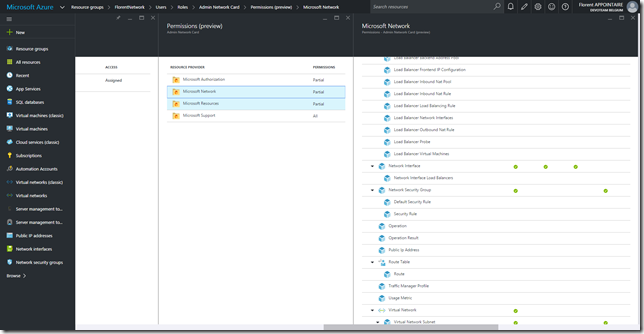
If you navigate to Access > Roles > Admin Network Card > Properties, you have the possibility to view permissions that will be applied on the RG:
Now, connect with the account who has rights to deploy a network card:
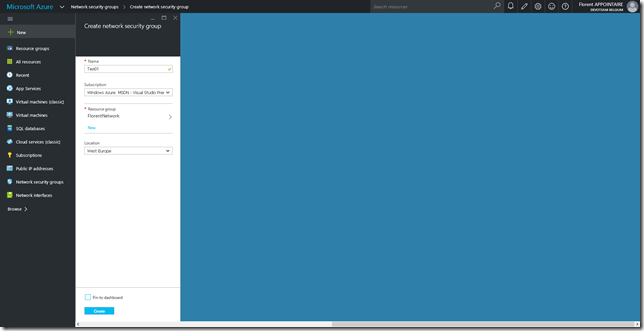
Try to create a NSG (we just have permissions to read/join a NSG):
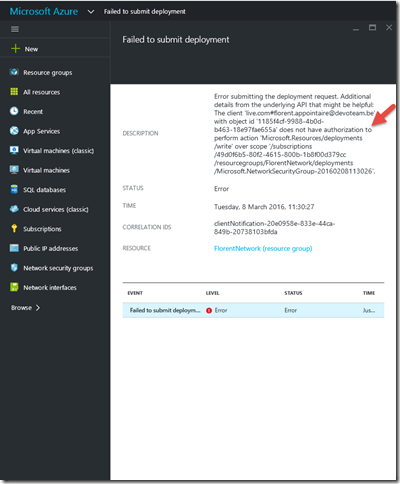
We have an error, it’s normal. The message is clear, we don’t have the good rights to do this:
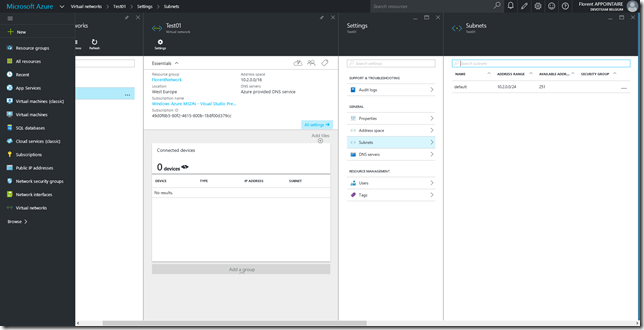
I will now create a virtual network with a subnet and a NSG, with an administrator account. I can now read NSG and virtual network that are in the Resource Groups where I have rights:
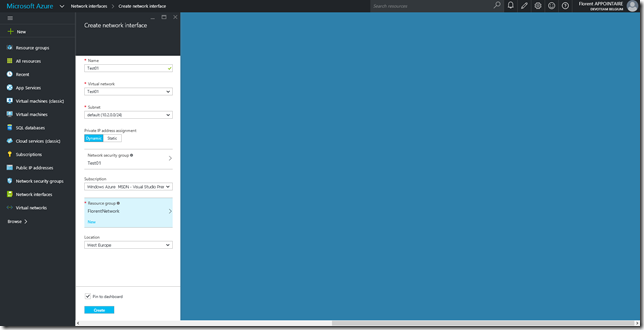
Try now to deploy a new network card that will have the possibility to be attached to a VM:
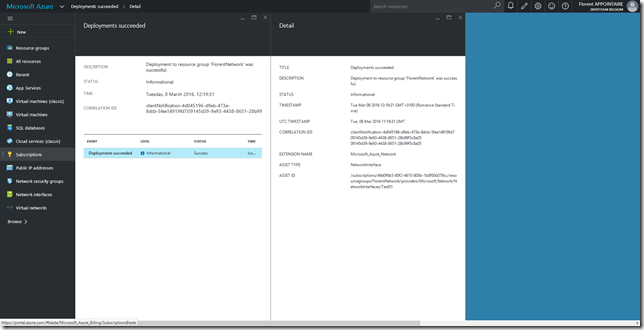
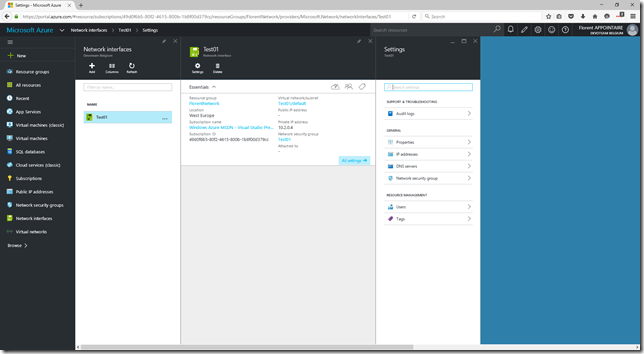
The deployment has been done successfully:
If you want to modify your role, without delete/create it, you just need to get his ID and insert it in your JSON file:
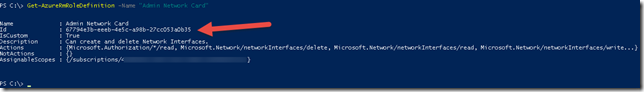
| Get-AzureRmRoleDefinition -Name “Admin Network Card” |
After, execute the following command to update it in Azure:
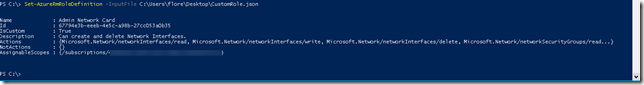
| Set-AzureRmRoleDefinition -InputFile C:\Users\flore\Desktop\CustomRole.json |
This new functionality will help you to give the good rights to the good peoples, without any impact on the production environment since it is not necessary to be co-administrator of the subscription 🙂