Most organizations nowadays rely on one or more active directory domain(s), and having weaknesses in your active directory can endanger your whole organization.
Active Directory provides a wide range of functionalities to your organization such as authentication, authorization, DNS, etc. It somehow contains the keys to the kingdom and acts as the hub that links modern networking systems, including cloud resources with integration into Azure Active Directory Services. Take this into consideration and you will quickly understand the need for protecting your active directory to reduce the risk of credentials/identity theft and to protect the access to your critical systems holding sensitive data.
On paper, securing your active directory might be considered a complex task. However, fortunately, there are some tools to help you on that journey.
In this article, I will present one tool, called PingCastle, without going into all the technical details and without providing you with recommendations to fill the gaps discovered by this tool. The idea is just to help you demystify this activity 
Plan
The planning phase for the audit of your active directory is not that difficult, but you must make sure that you involve the right profiles from your organization and that the project is well known, and that you have a sponsor for that. This is important mainly because the report that the tool will generate becomes a sensitive document that contains the weaknesses of your system, and also because, depending on the findings, different people in the organization will be involved in remediation.
- Key questions:
- Who are the stakeholders?
- Target scope (e.g. all domains, one domain) and the responsible
- How we plan the remediations?
- Frequency of the audit?
Now Let’s Assess Your AD
First things first: head over to Download – PingCastle, download and extract the zip. In this zip file, you can find the PingCastle.exe that you can now run and follow the prompts. Note that you don’t need administrative privileges for running this tool, but you may get a few false positives if you have removed/denied domain user’s permissions on things like GPOs. To solve this potential issue, just grant you read permissions on the object that the tool complains about and re-run it. But please do not use Domain Admin privileges for such activity.
Within a couple of minutes, you will get an HTML report generated, as simple as that. now the fun begins.
Analyze
As I said, the “fun” begins: You just open the report and start your journey towards remediation (yes, I’m pretty sure that you will have findings
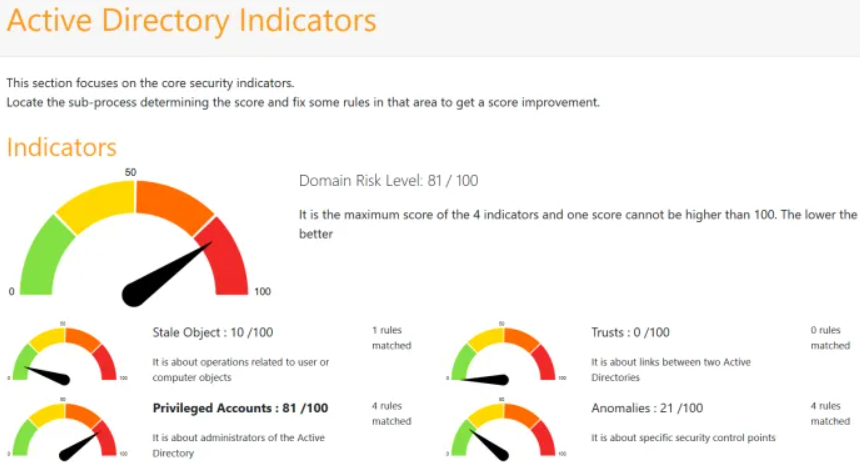
Figure – Report Summary
For each finding area, there are specific details, and that’s where you must spend most of your time: You don’t run an audit to see green flags, you run an audit to make sure that you understand the risk you take with the current setup that you have in place.
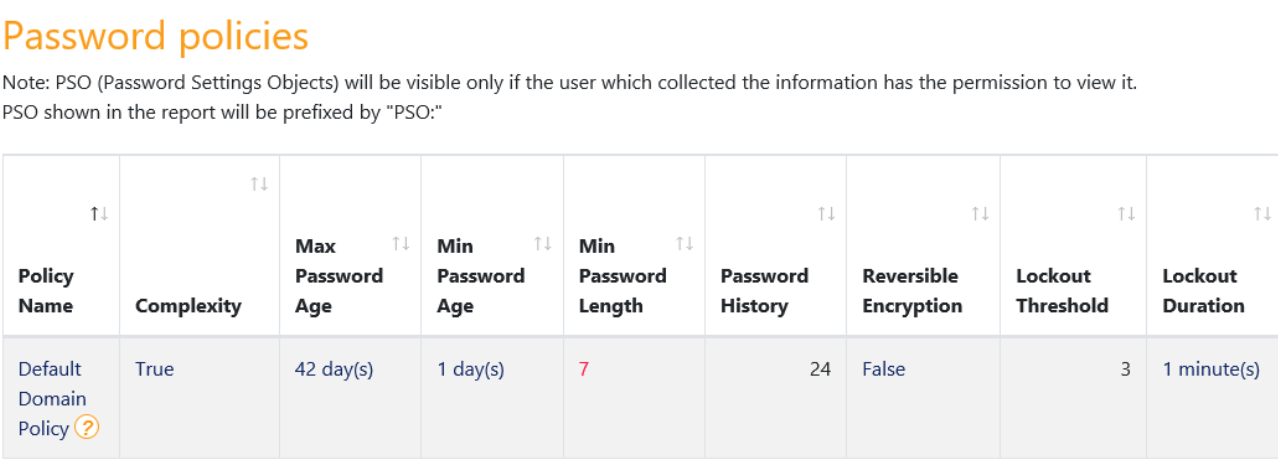
For each finding, you should create a task to build your remedial action plan, and ideally with each finding the risk associated should be assessed.
Figure – Example finding details
Summary
It will most probably be a long journey but the objective is to make progress, understand the risks you’re facing, have a better view of your organization’s security posture, and improve as you go. Such exercise will definitely enhance your security posture on one hand and help you define a better process for later on the other.