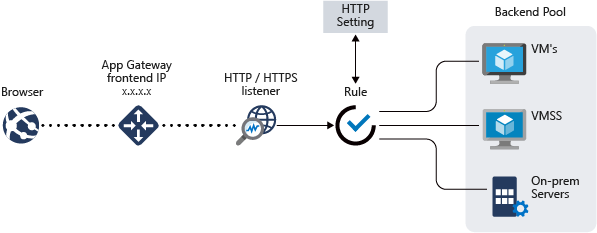
If you want to migrate IIS / Apache servers to Azure, and expose the sites publicly, you will need to protect these sites, as you do On-Premises. To do this, Microsoft has provided a PaaS service, the Application Gateway, which allows load-balancing traffic on the 80 and 443 web ports directly to one or more servers. Based on an URL, which will point to the public IP of the App Gateway, the listener that will be configured, will redirect the traffic, according to a defined rule, to a VM, an On-Premises server or a VMSS:
This service can also act as a Web Application Firewall (WAF) to protect against attacks, but also SSL Offloading, to only provide traffic on port 443, with an SSL certificate, and then, redirect internal traffic to another port, for example 8081.
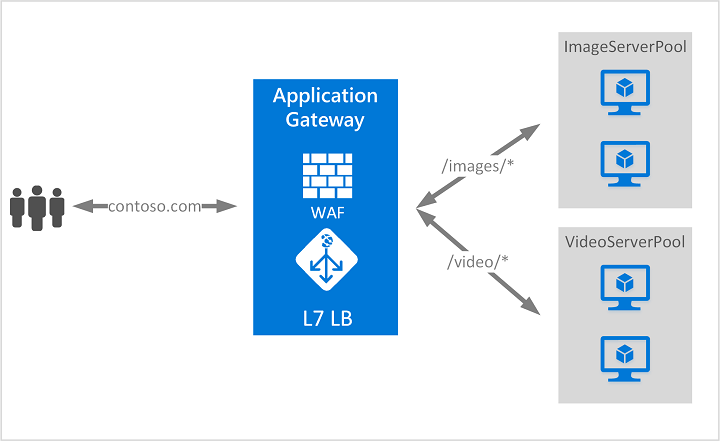
The advantage of this solution is that it is easy to set up and easy to manage. You will find all the necessary information for the App Gateway here: https://docs.microsoft.com/en-us/azure/application-gateway/overview
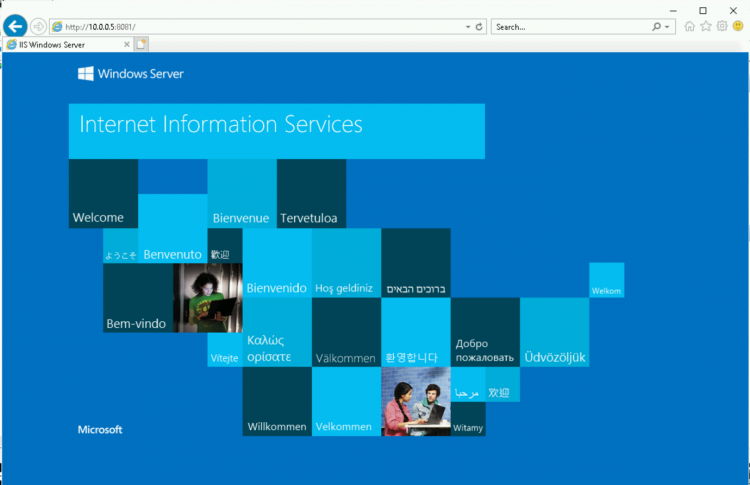
Here, we’ll just deploy an App Gateway + WAF. In the following article, we will see the configuration of the App gateway/WAF. I have already deployed an IIS server, which listens on port 8081, in HTTP:
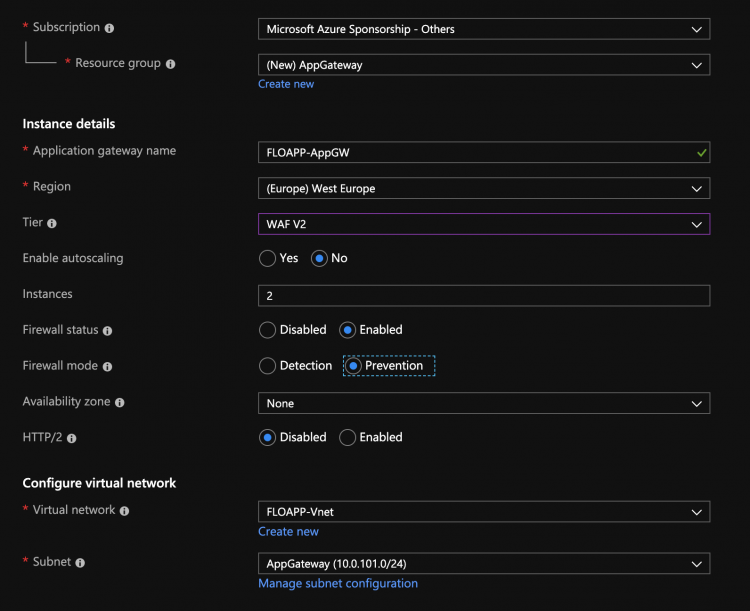
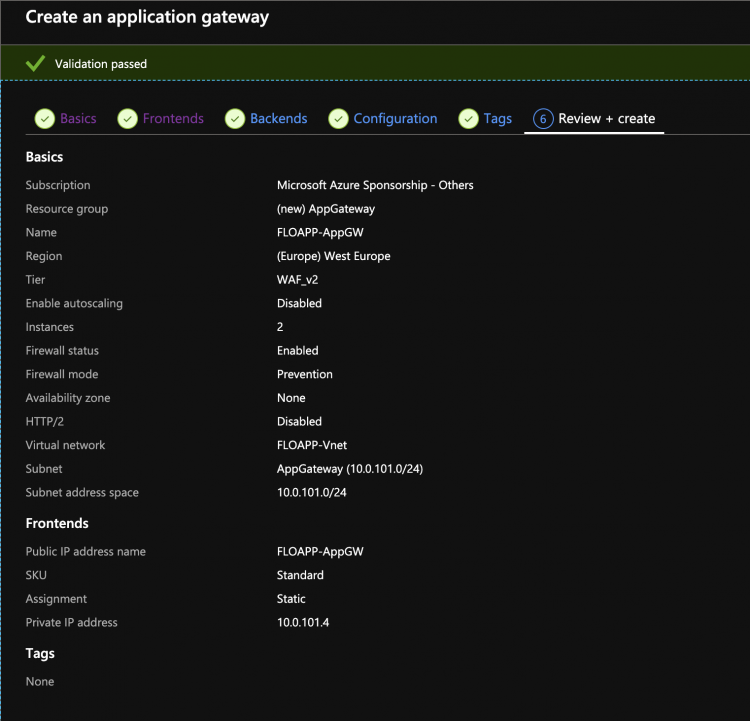
In the Azure portal, look for Application Gateway in the services, and create a new App Gateway. Here, I will choose the tier WAF V2 because it presents the fact of applying the changes much faster than the v1, among others. I disable here the auto scaling, and I choose 2 nodes, which is the minimum. Then choose a virtual network where your App Gateway will be linked:
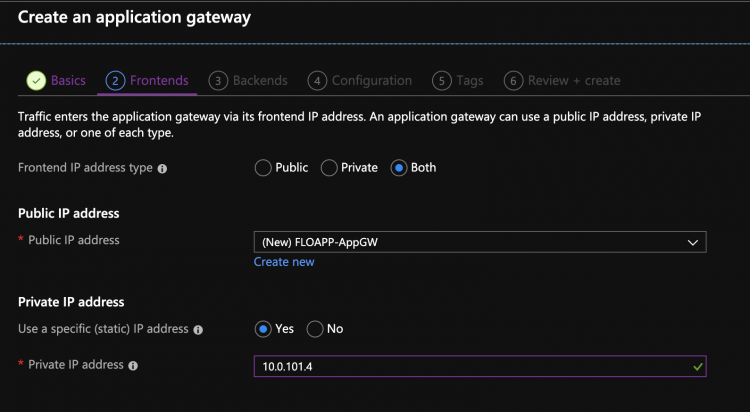
Then you need to create an IP public if the site needs to be publicly exposed, but you can also use a private IP:
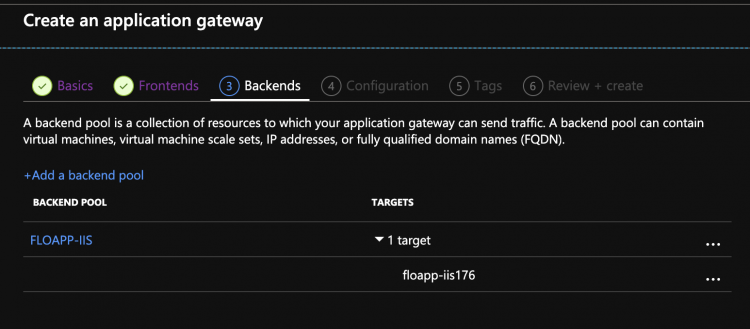
Then create your first Backend pool which will contain one or more servers where the website is hosted:
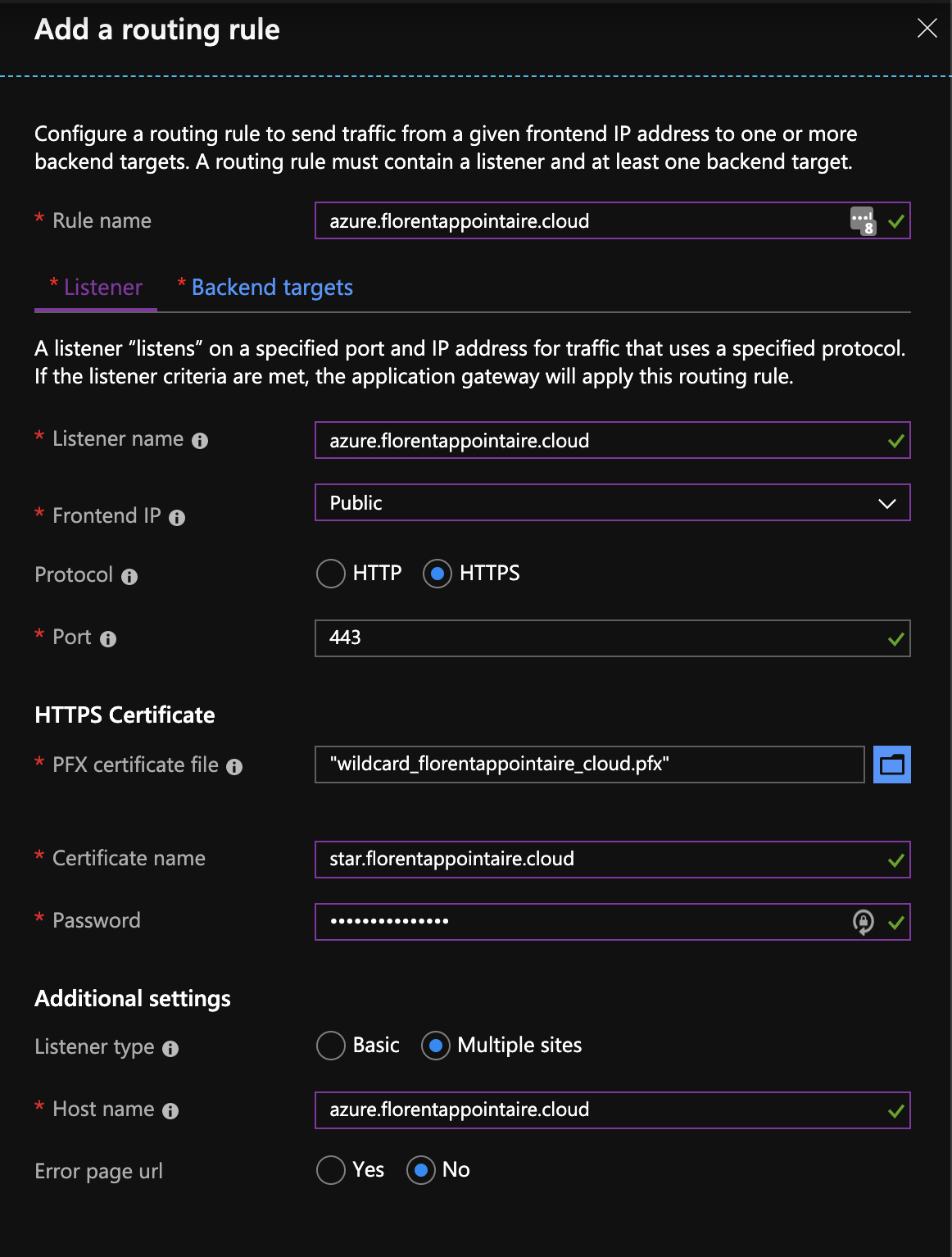
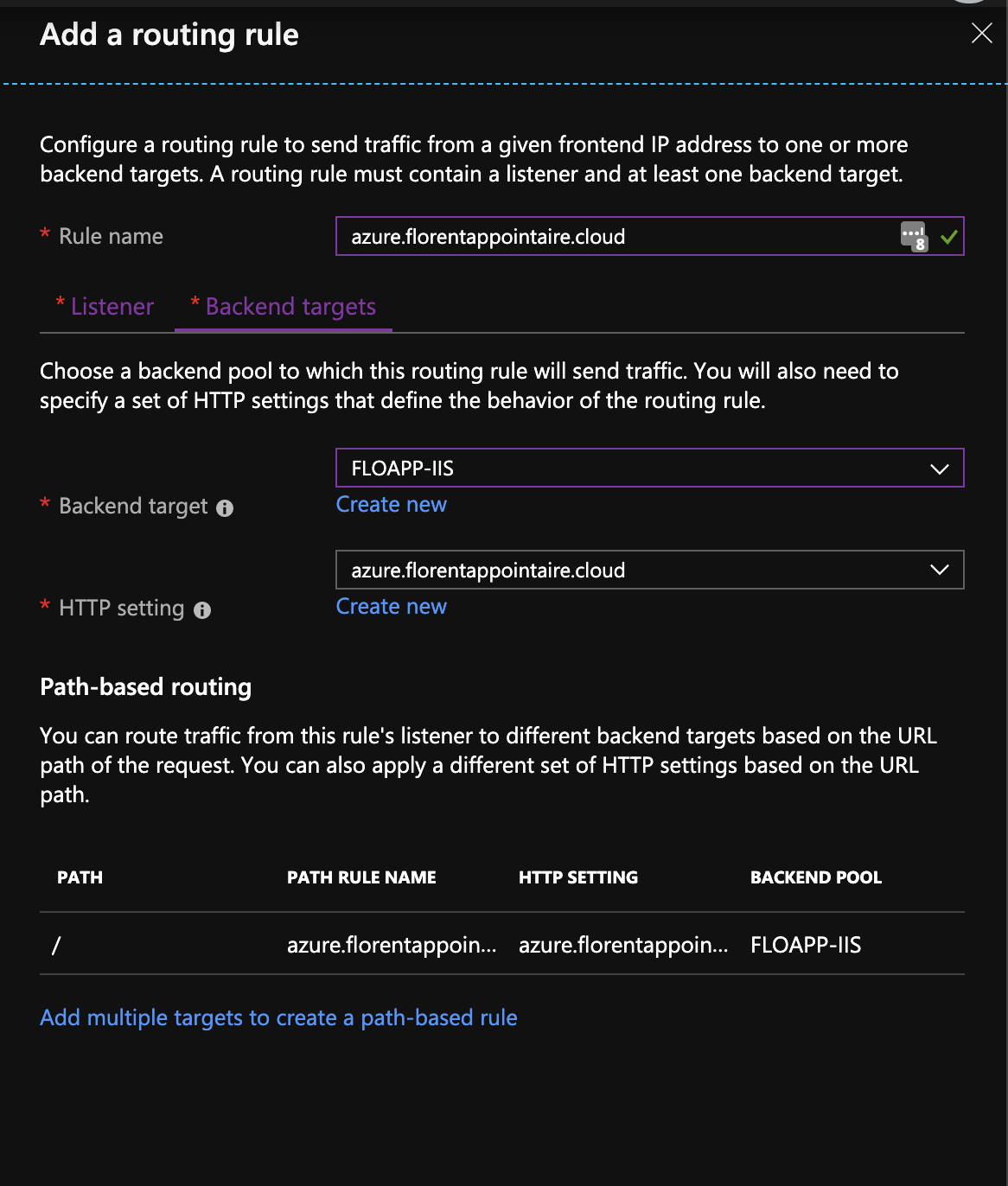
Then you have to add a routing rule. Give him a name (I usually give the name of the site that will be used by this rule). In this rule, there will be a listener, on port 443 in HTTPS, with a certificate (PFX mandatory), of type multi-site:
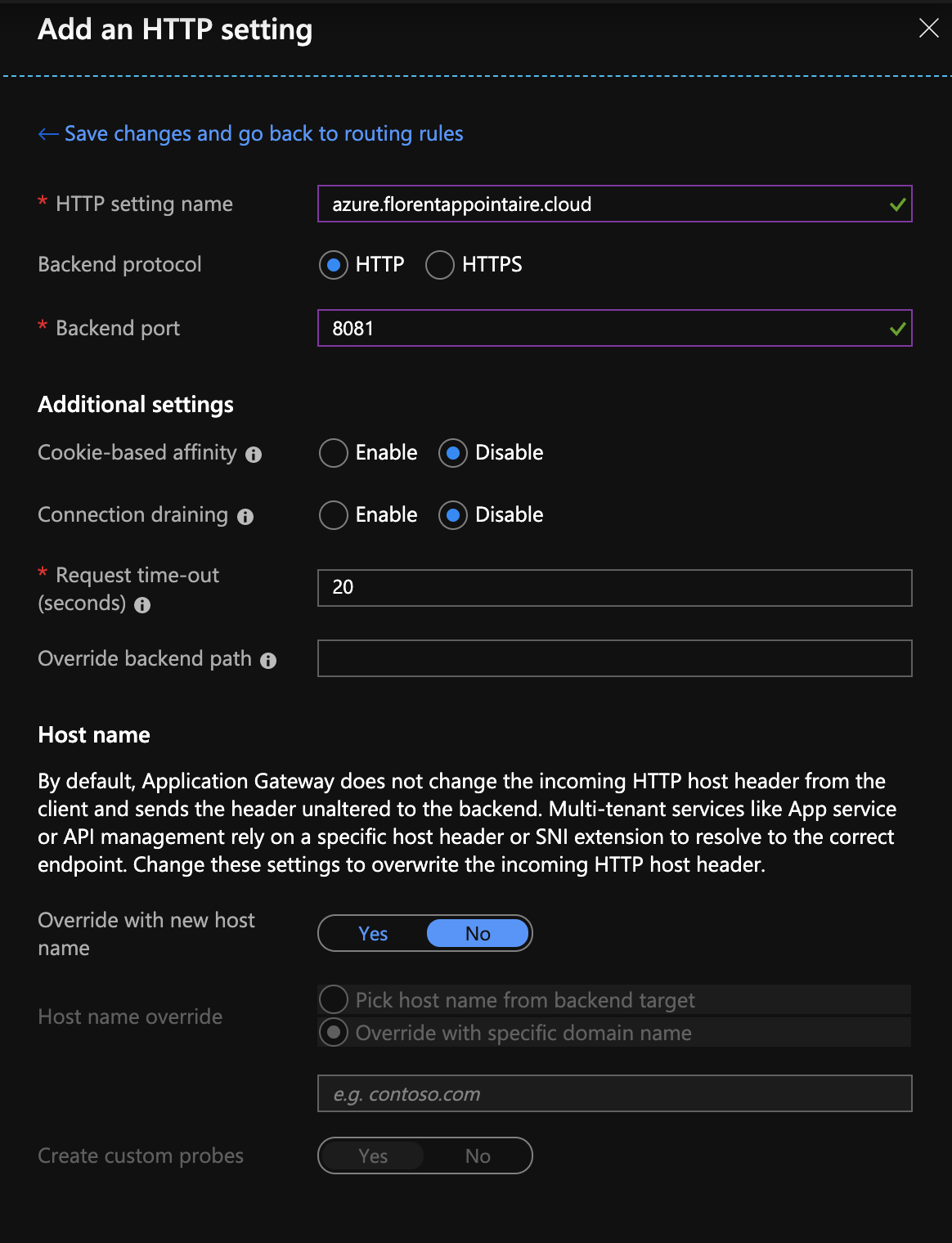
In the Backend target part, I created a new HTTP setting, to port 8081, in HTTP. It will be this port that will discuss with the website:
Finally, to finish, choose the backend you created before and the HTTP Setting created just before:
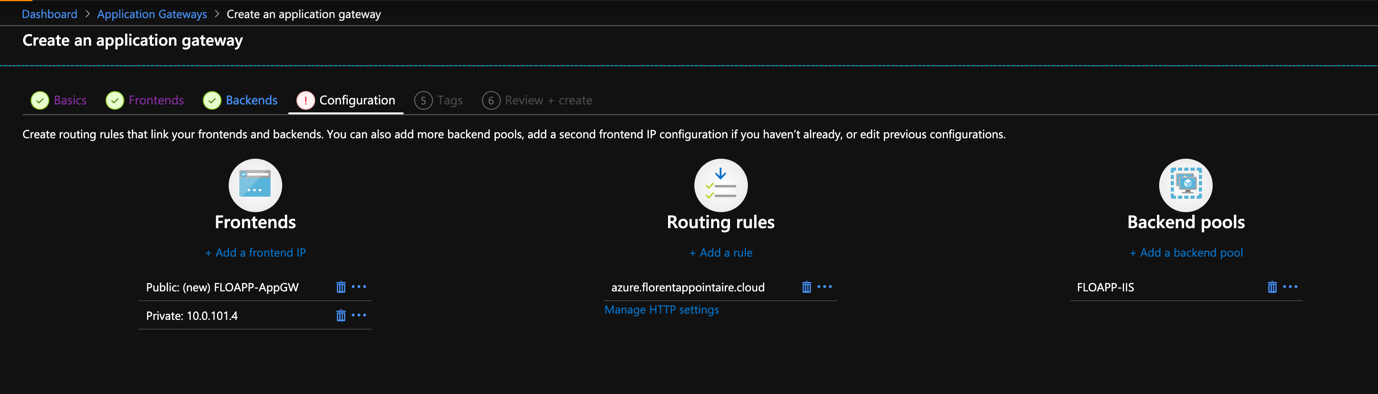
You now have everything you need to get through the deployment:
You can deploy your App Gateway/WAF:
To summarize, here are the important elements here:
- Backend pool: contains one or more servers, on the same VNet as the App Gateway, to an On-Premises IP, etc.
- HTTP Settings: set how to chat with the site that is backend
- Listeners: this is where we will tell which URL we are listening to, as well as the port and the certificate, if there is one
- Rules: the rule allows to orchestrate everything, taking the listener’s traffic, associating it with an HTTP setting, and pointing it to a backend pool
- Health probe (optional): allows to test if a site, in a backend pool, is functional or not and if it is therefore a candidate to display the requested site
The App Gateway is deployed and configured. I created my record azure.florentappointaire.cloud in my DNS, pointing it to the public IP of the WAF.
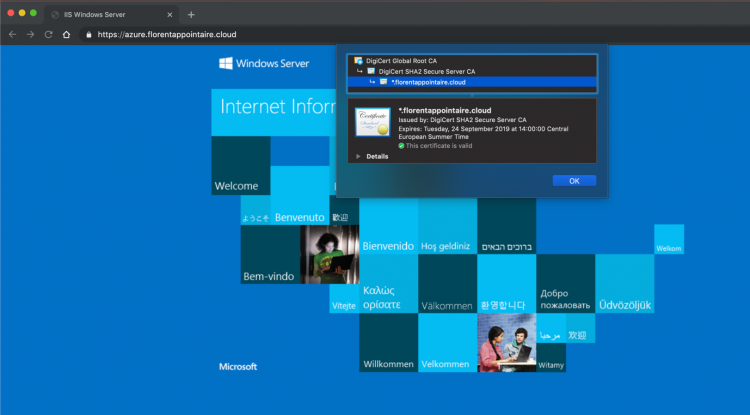
If I am now browsing https://azure.florentappointaire.cloud I should be redirected to my IIS server:
Here, I am in HTTPS, while my site is configured in HTTP. Note that if you have NSGs that are applied to your subnets / network cards, you will have to open port 8081 for example in the NSG of the IIS server and 443 in the one of the App Gateway.
You can also test the security of your WAF, using the Microsoft Security Risk Detection tool: https://www.microsoft.com/en-us/security-risk-detection/
If you have any questions, do not hesitate to contact me