One year ago, Microsoft introduced the general availability (GA) of Azure Front Door, a scalable and secure entry point for web applications and a global HTTP(s) load balancer. https://azure.microsoft.com/en-us/blog/azure-front-door-service-is-now-generally-available/
You can use Front Door with Azure services including Web/Mobile Apps, Cloud Services and Virtual Machines – or combine it with on-premises services for hybrid deployments and smooth cloud migration. With Azure Front Door, you can use the following features:
- Accelerate application performance
- HTTP(s) load balancer
- Increase application availability with smart health probes
- URL-based routing
- Multiple-site hosting
- Session affinity
- TLS termination
- Custom domains and certificate management
- Application layer security
- URL redirection
- URL rewrite
- Protocol support – IPv6 and HTTP/2 traffic
In this article, I will create a Front Door for a highly available global web application called “WebApplicationMaster”.
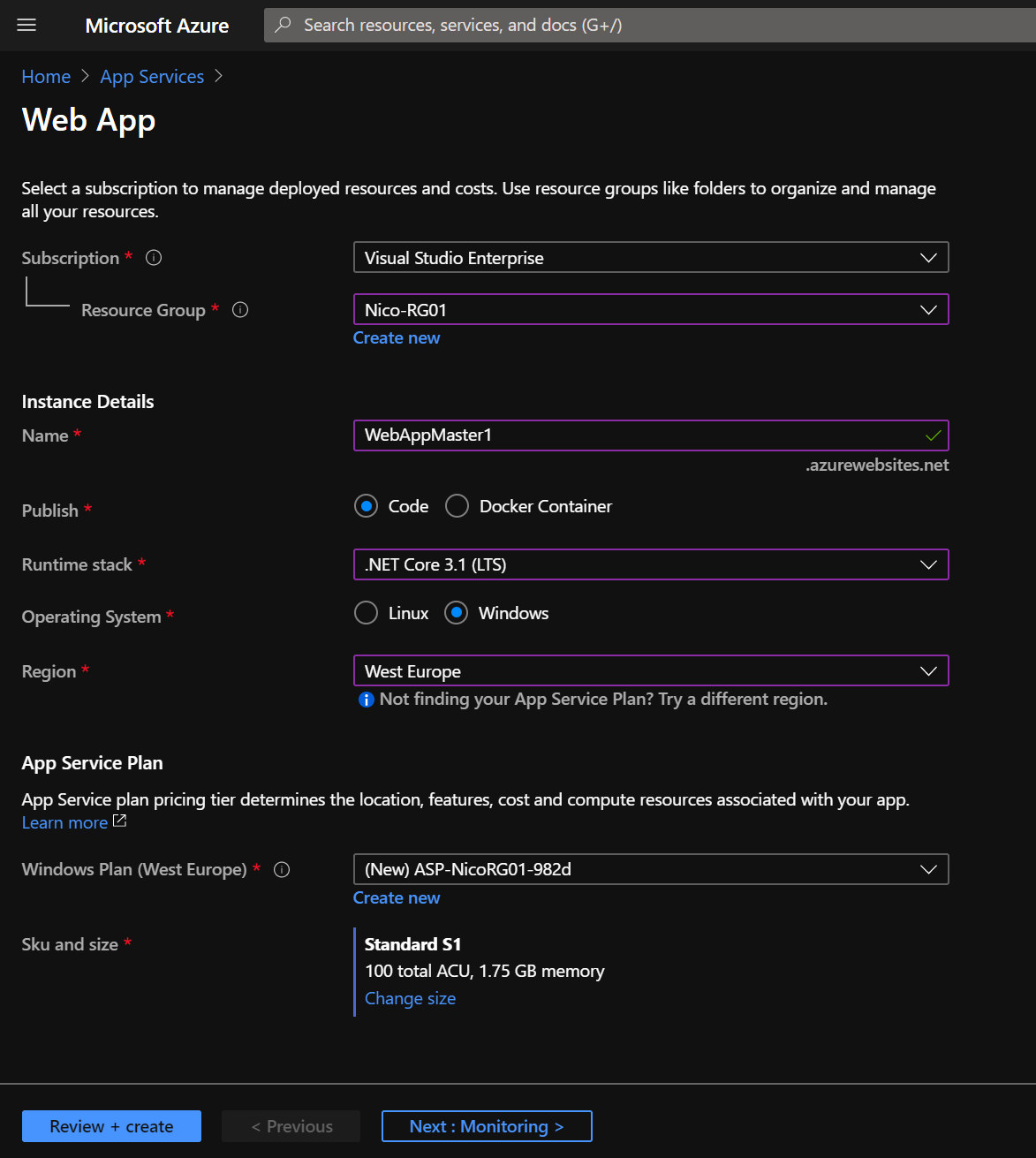
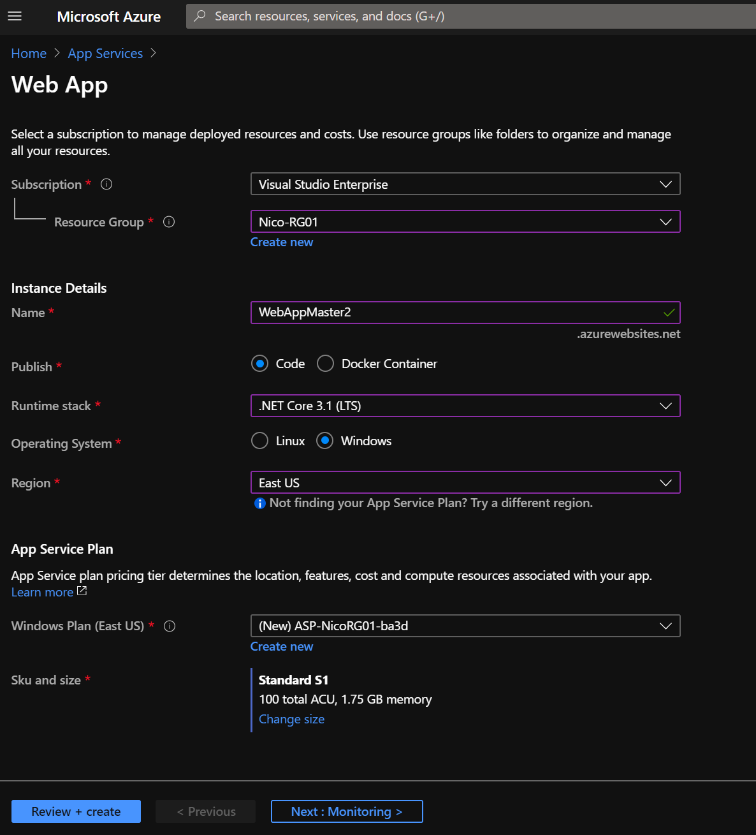
First, I create two WebApp that run in different Azure regions and both the web application instances run in Active/Active mode.
- Sign in to the Azure portal
- From the home page, select “Create a resource”.
- Select “Web” then “Web App”.
WebAppMaster1 is located in West Europe region and WebAppMaster2 is located in East US region.
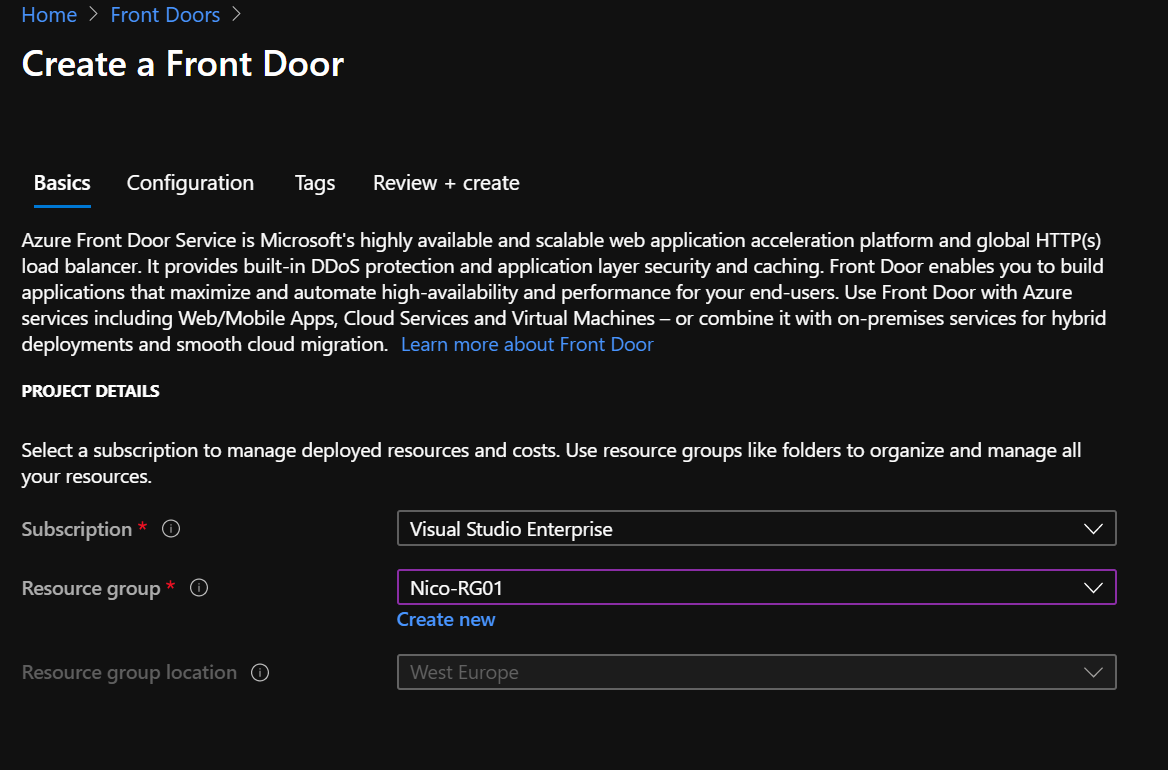
Next, I create a Front Door for my application
Select the subscription and a resource group
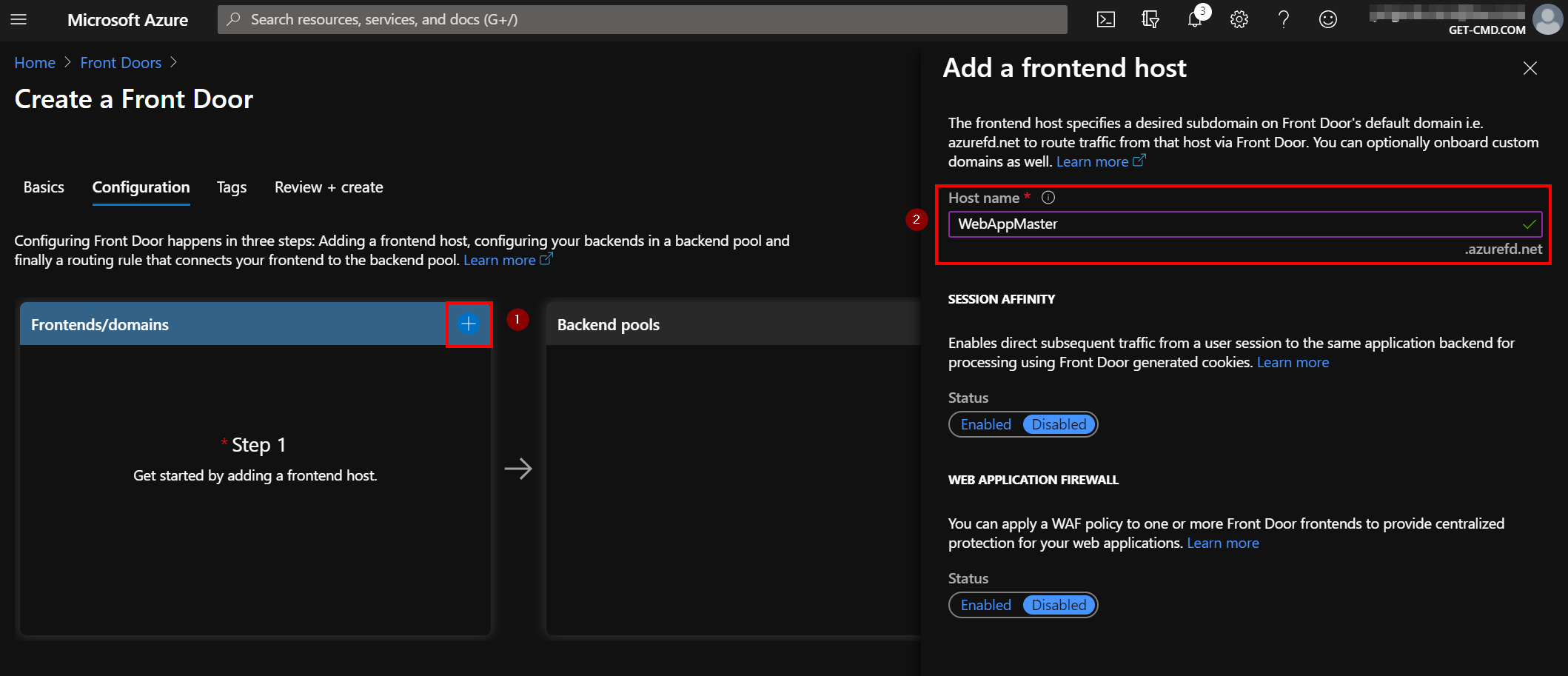
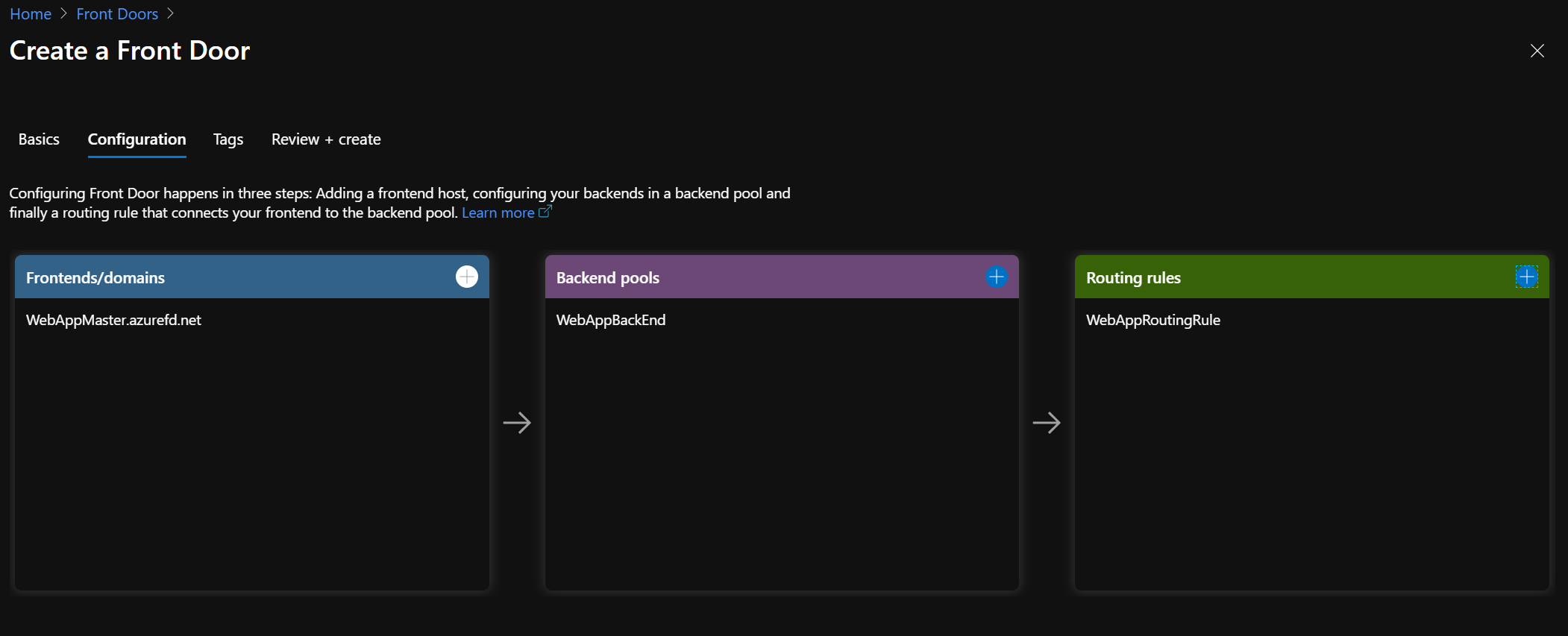
On the next page, add a frontend host
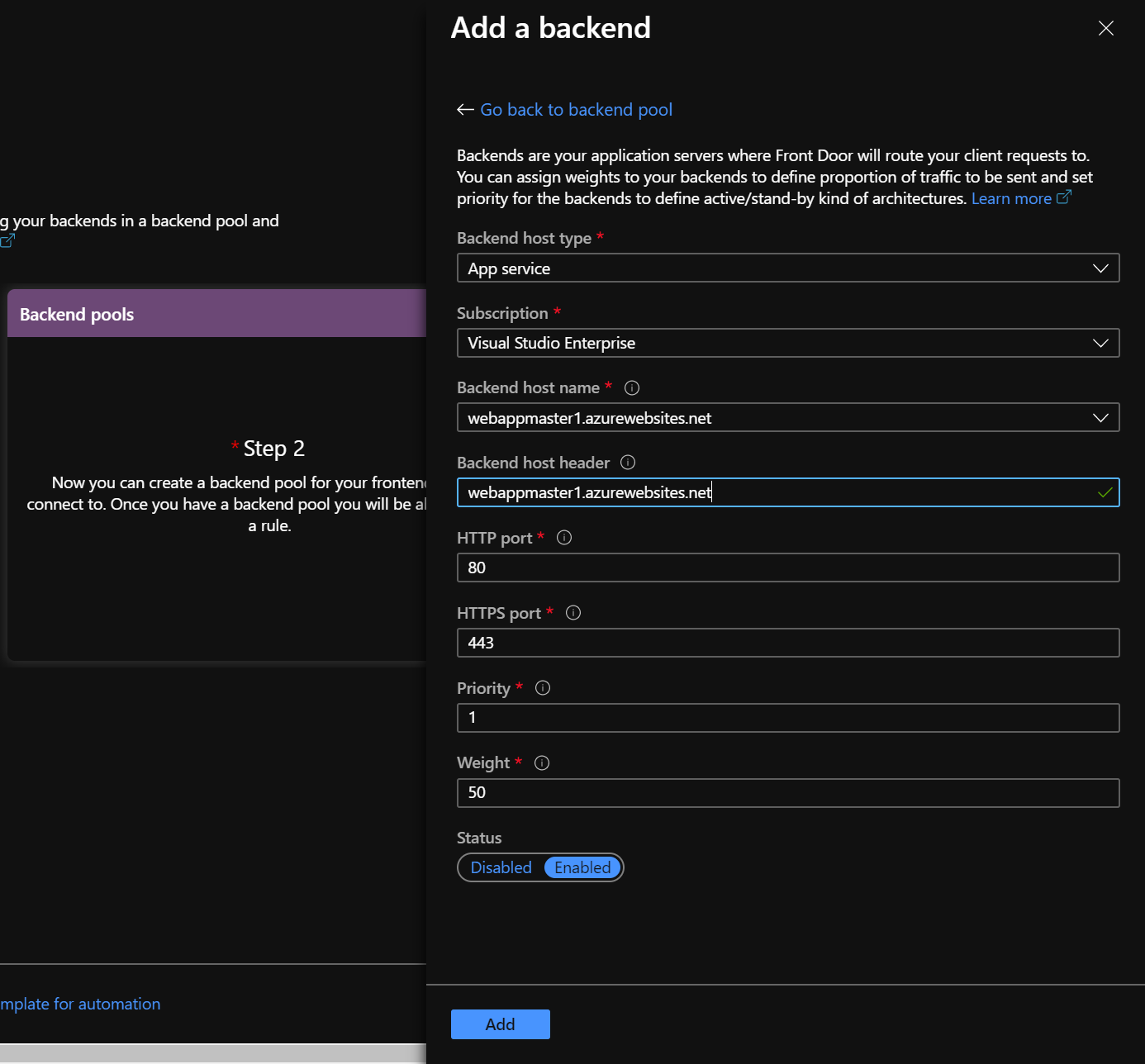
Next, add a backend that contains both WebApp
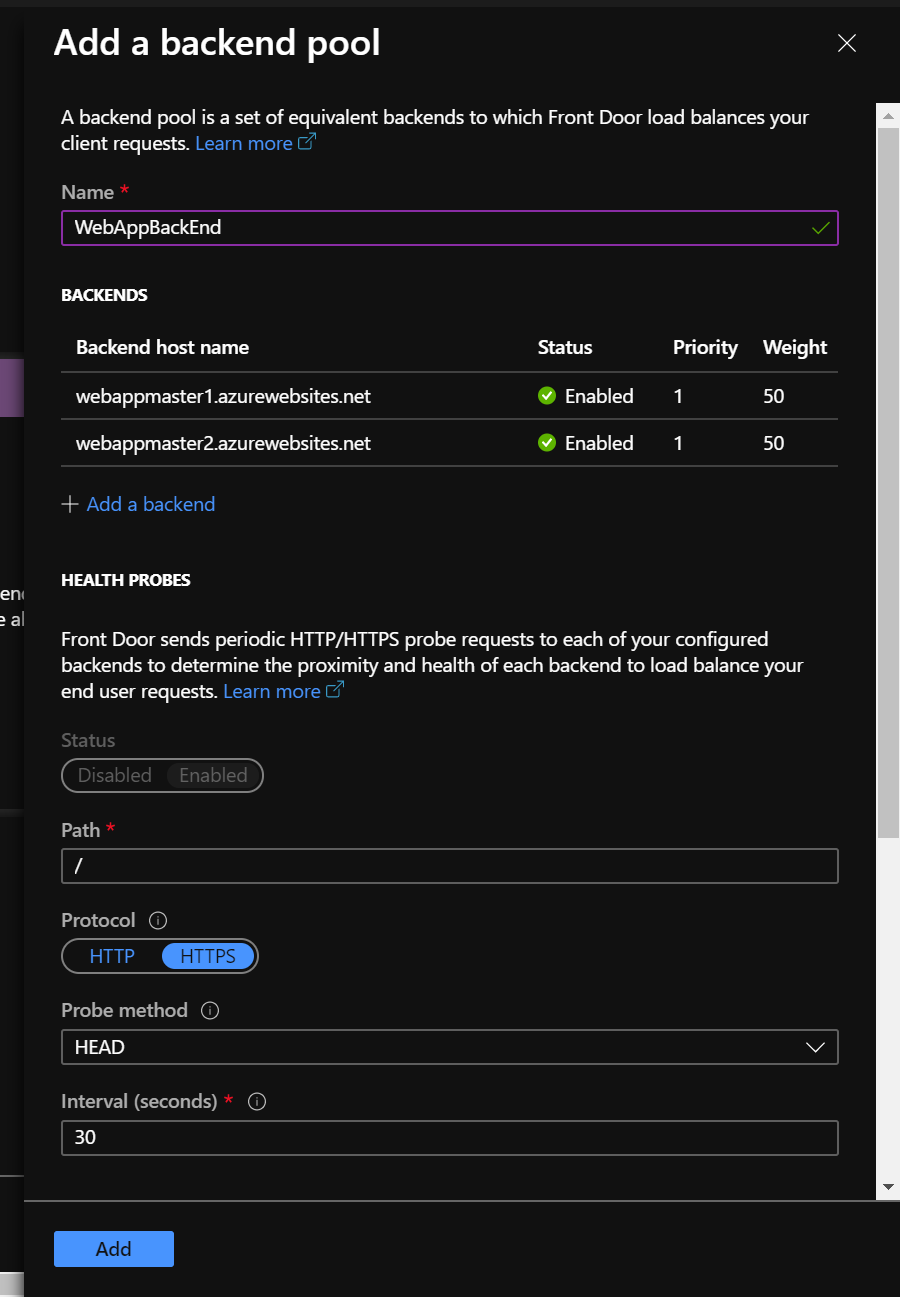
Add the second WebApp and validate the page
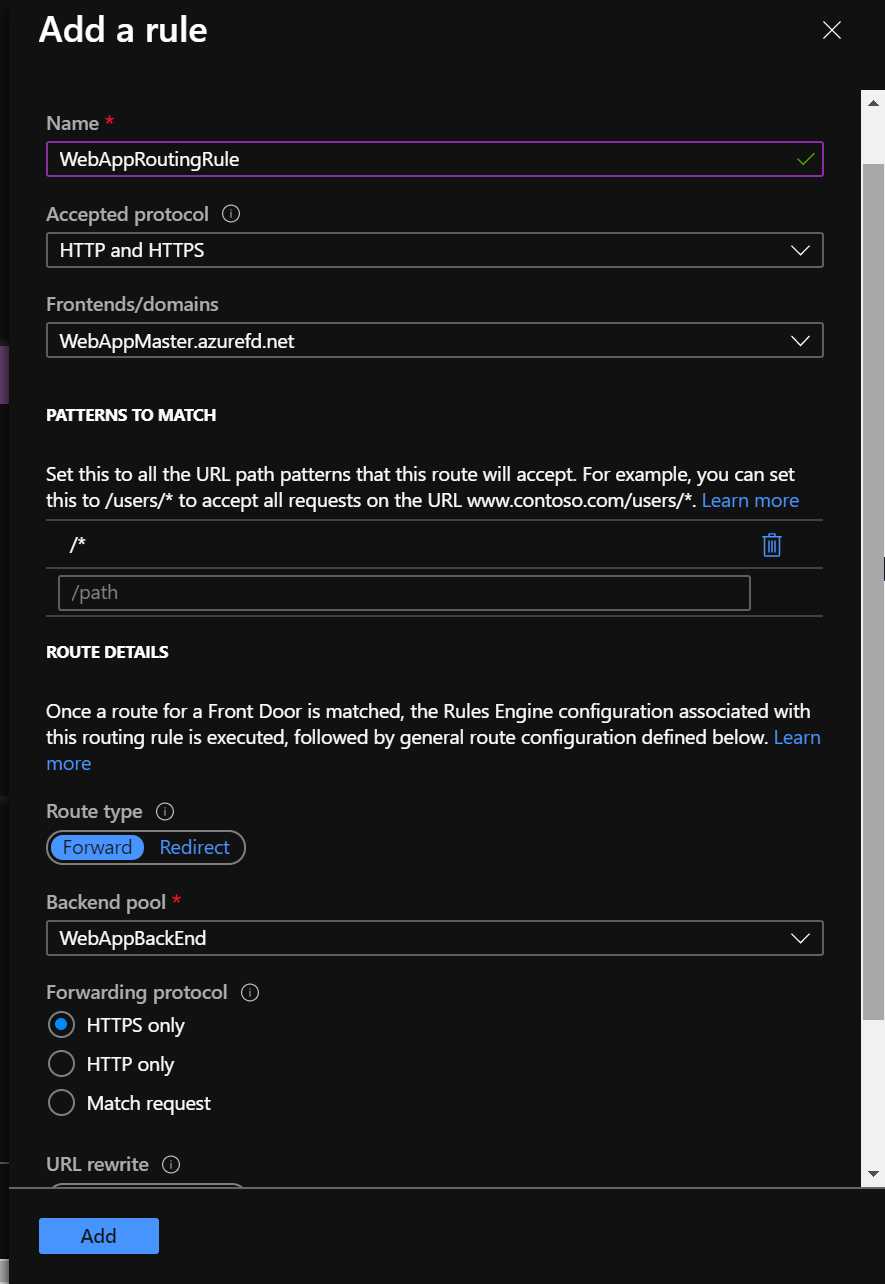
And finally, you must add a routing rule. A routing rule maps your frontend host to the backend pool. The rule forwards a request for “WebAppMaster.azurefd.net” to “WebAppBackend”.
You should have something similar to this screenshot
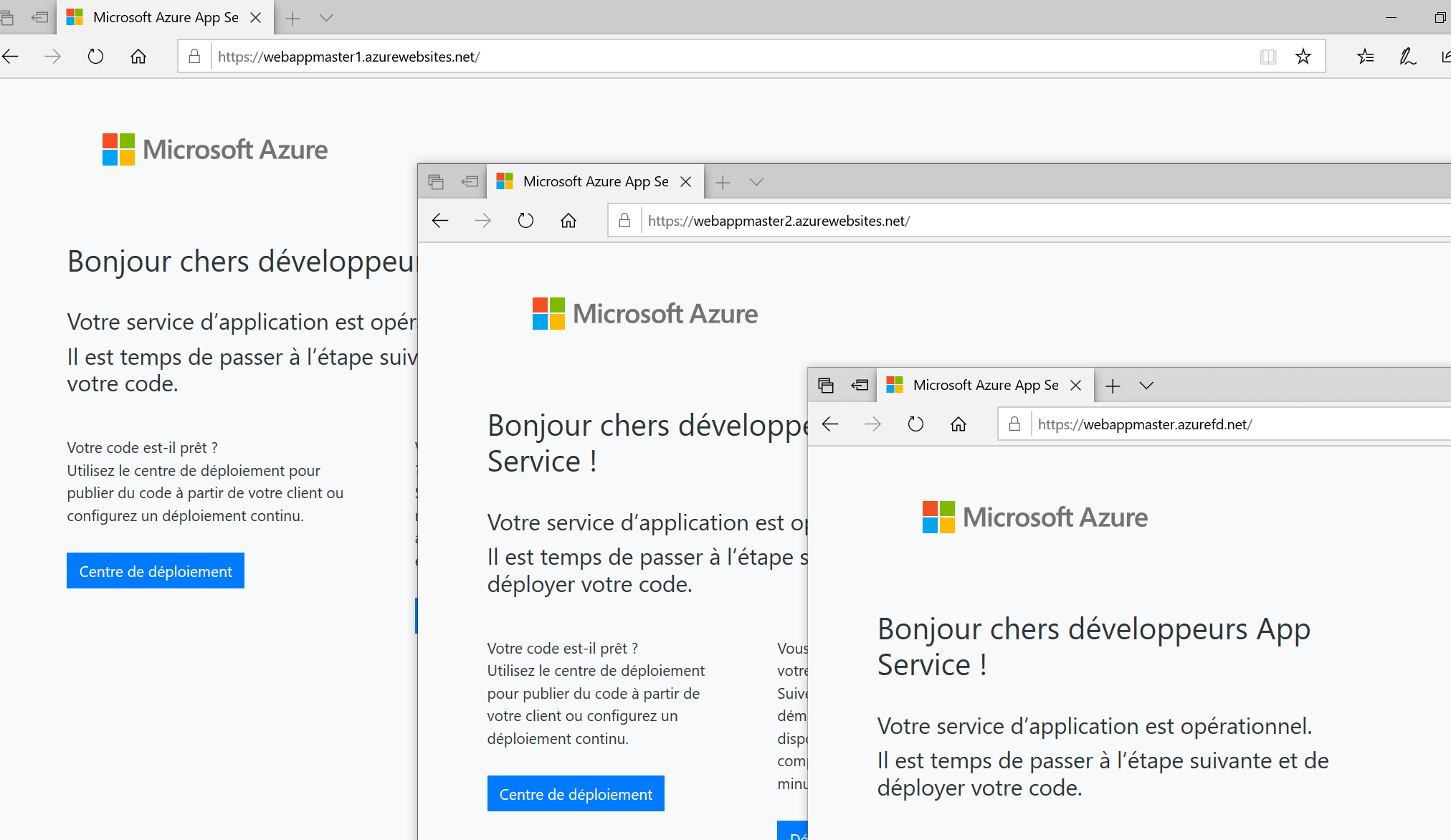
It is time to test Azure Front Door. First, I can confirm that both WebApp are up and running
Then, I browse to https://WebAppMaster.azurefd.net. Of course, in the Front Door configuration, you can use your customer domain instead of “azurefd.net”.
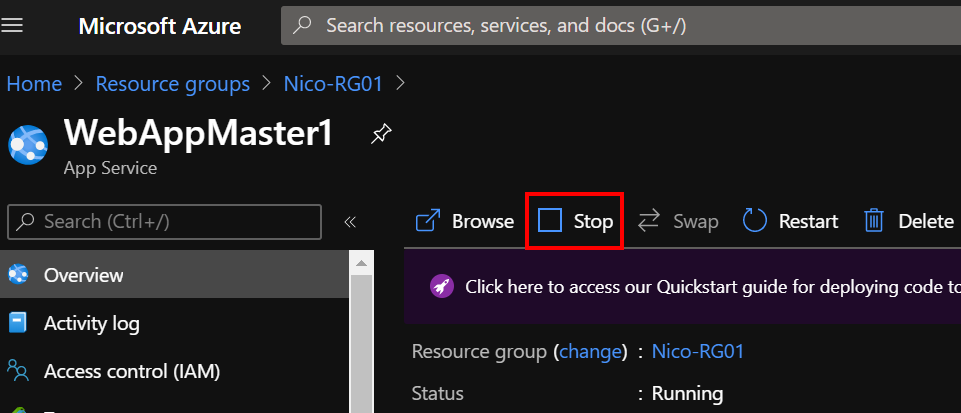
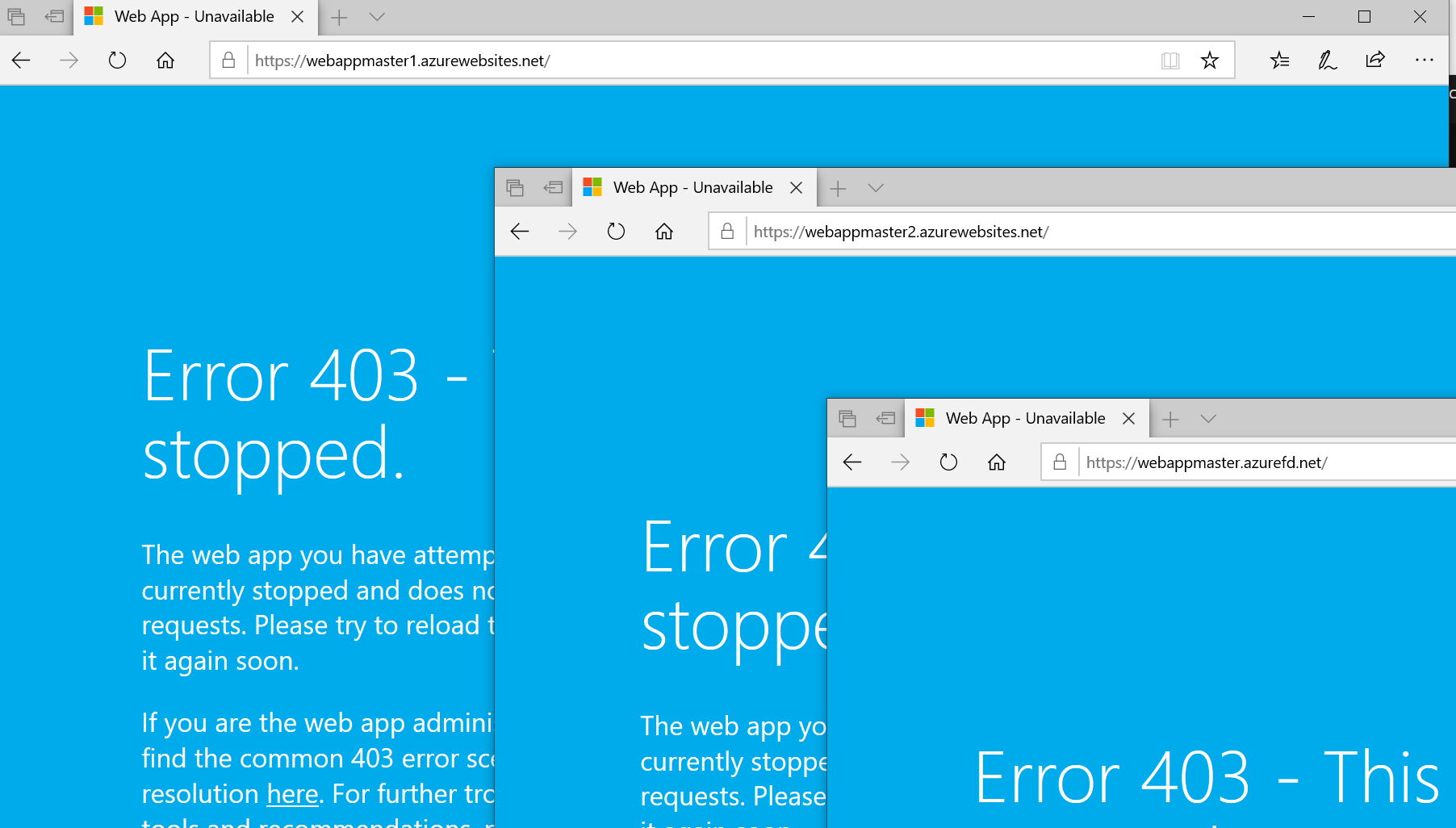
Next, stop the first WebApp to confirm that Azure Front Door is redirecting your traffic
Traffic is redirected to the second WebApp
And then, stop the second WebApp to confirm that Azure Front Door is showing the 403 status code.
Next step is to add Web Application Firewall Policy, so start both WebApp and go back to the home page to search “Web Application Firewall Policy”
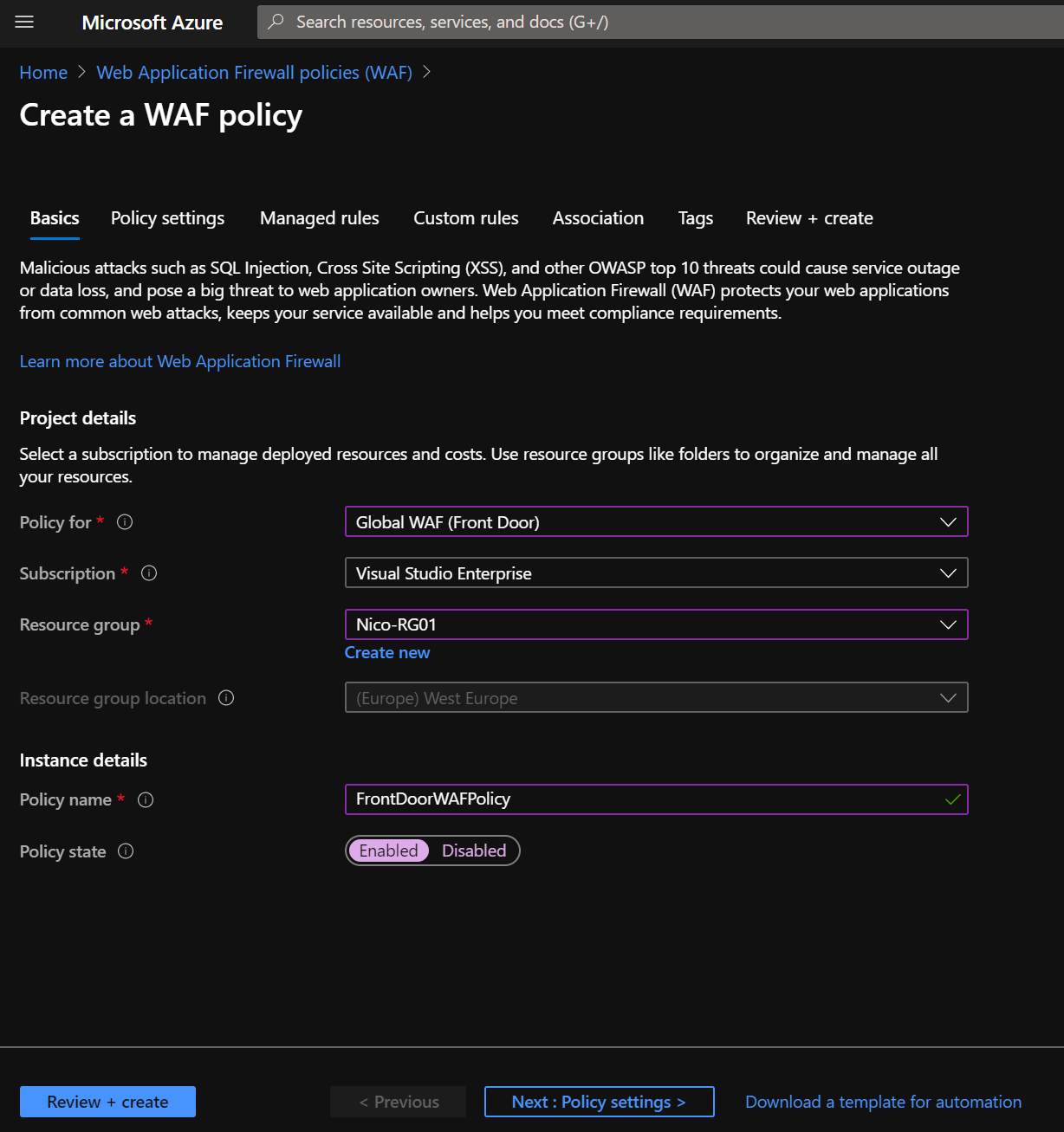
On this blade, you must select the purpose of the policy which is Global WAF in this case, then add a friendly name to this policy.
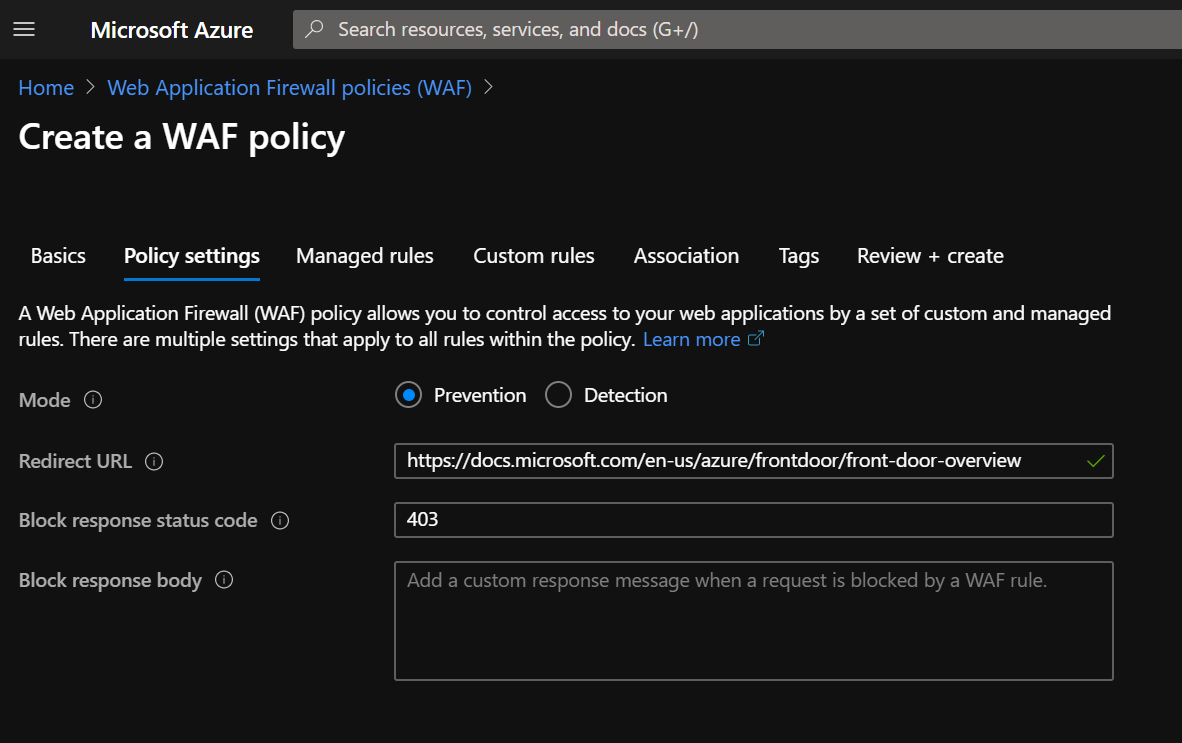
On this page, we add a “redirect URL” to the official Microsoft documentation and select “Prevention” instead of “Detection”. Later, we will add a customer rule to redirect the traffic to this page.
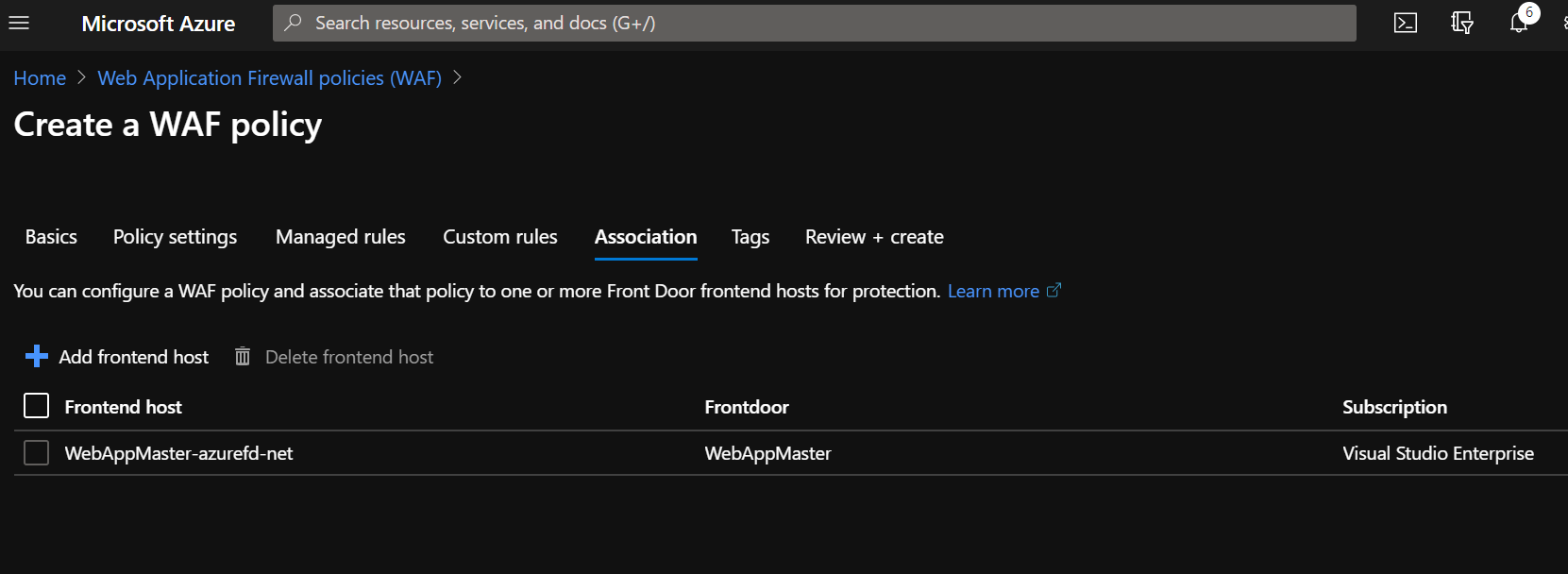
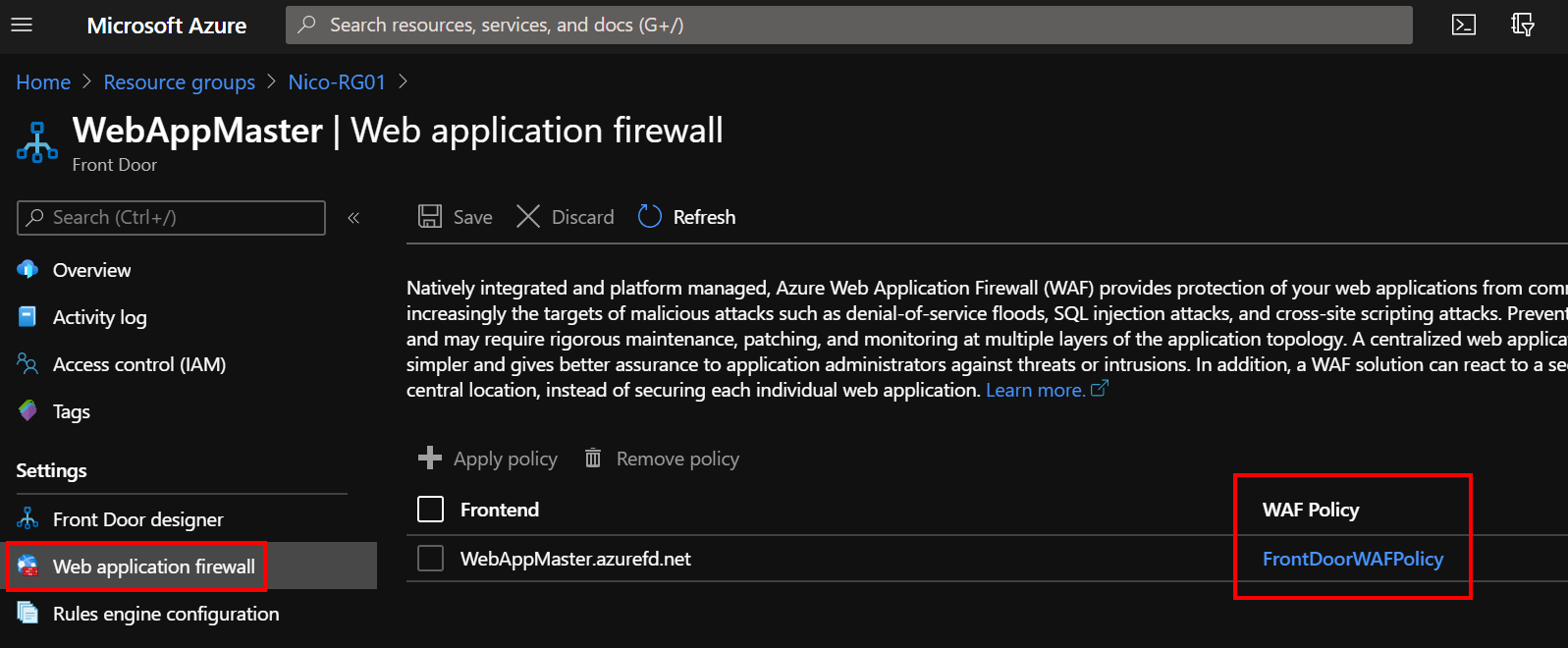
Associate the WAF policy to your frontend and confirm in the Azure Front Door blade that the WAF policy appears
Here, I edit the WAF policy in order to add a customer rule that will redirect French traffic to the Microsoft documentation website.
Add a friendly name to this rule, add a priority and configure the conditions. In my case, I want to redirect French traffic based on the geo location.
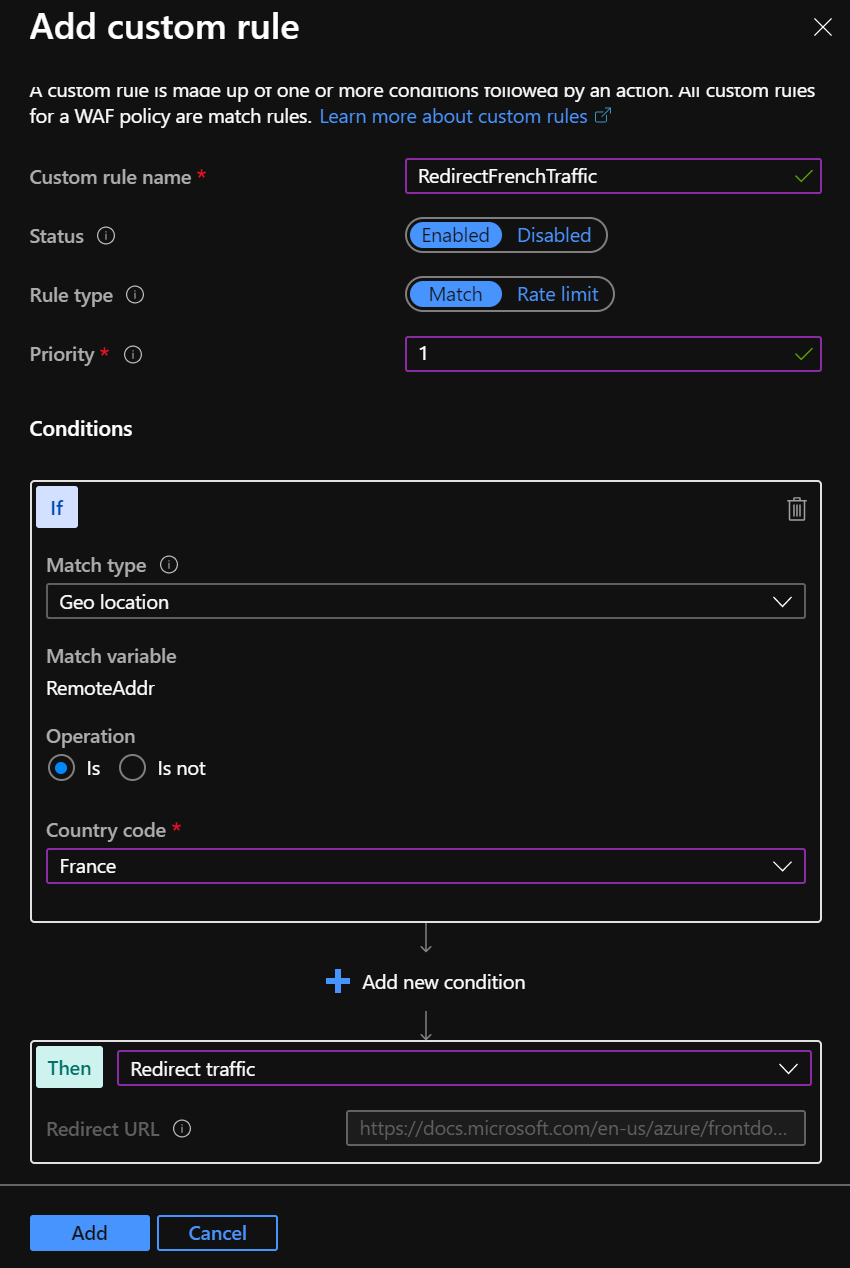
Wait a few seconds after applying the rule and Azure Front Door will redirect the traffic. Below is the “before/after” screenshot for French traffic
Conclusion
Thanks to Azure Front Door, you can easily manage and secure your web application traffic. Azure Front Door pricing can be found on the following page: https://azure.microsoft.com/en-us/pricing/details/frontdoor/