As requirements for some company, when an employee leaves the company, it is to remove data and accesses.
The problem with Kubernetes, is that you have credentials, in your kube file. So, if you leave the company, get the file with you, and copy it to your personal computer, you will be able to connect to the AKS cluster, except if you implemented network restriction for example, by authorizing only the public IP of you company.
So, one way to remove these accesses, is to renew the CA of your AKS cluster. But, all other employees must renew their credentials, after this CA rotation certificate. And to renew these credentials, you need… an Azure CLI access, with your company credentials 
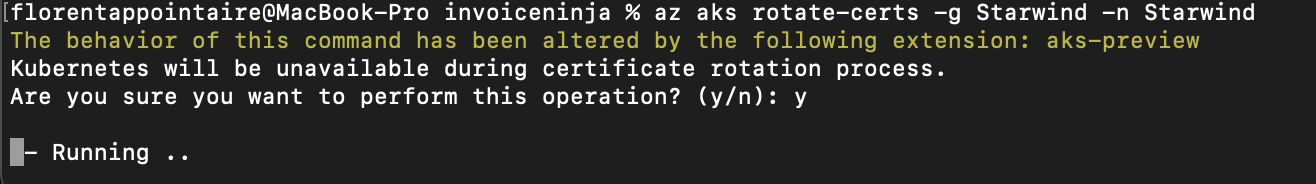
You need to be careful when you do this CA rotation, because your cluster will be down for some minutes (maximum 30 minutes). Why? Because all of your pods will be redeployed with this new CA
So, to start, execute the following command:
|
When it’s done, if you try to get pods for example, you will have the following error:
|
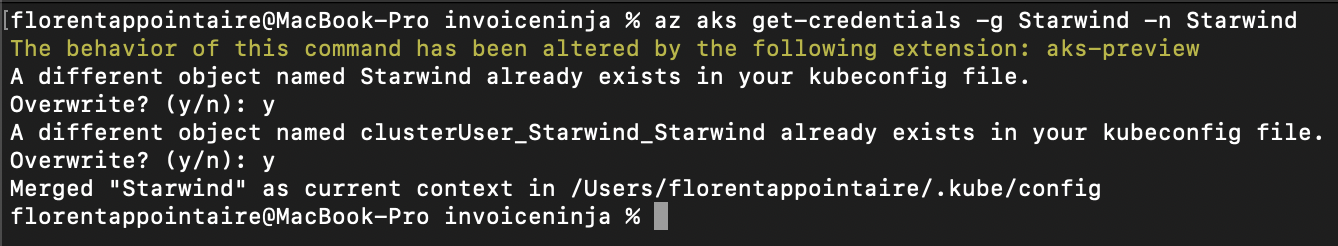
So, you need to login, with az login, and get credentials again:
|
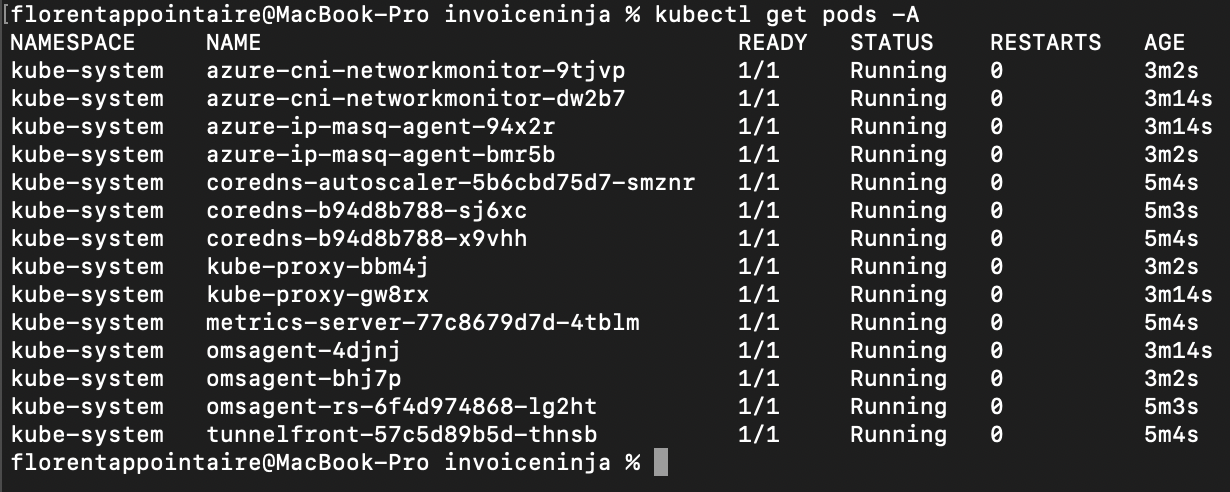
Now, you will be able to get your pods again:
And, as you can see, the age of pods are pretty new, because they have been redeployed with the new CA.
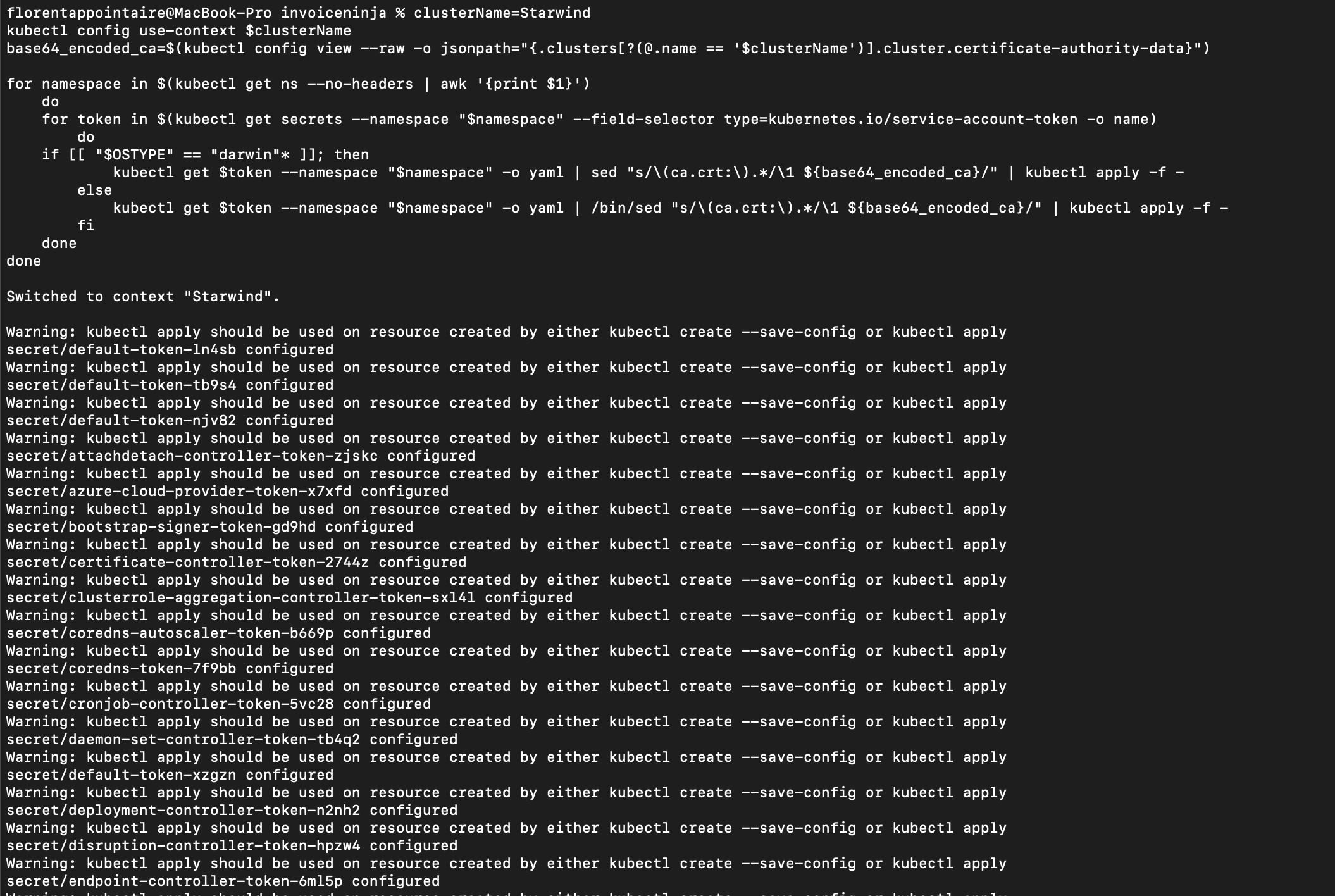
If you use the ca.crt in your secret, for example, you will need to update them, with the following script:
|
What it will do here? It will get you ca.crt that you just get, and update each secret with this new one: