One of the big challenges of the current times is to interconnect offices to a Cloud provider like Azure. I have this need at my home as well: to create and simulate an enterprise network.
My home lab consists of the following:
- One Unifi USG: https://www.ui.com/unifi-routing/usg/
- A Unifi Switch 24p PoE: https://www.ui.com/unifi-switching/unifi-switch-poe/
- 3 Aps Unifi LR: https://www.ui.com/unifi/unifi-ap-ac-lr/
The only problem is that I have a dynamic public IP. So, it’s difficult to maintain the connectivity for this Site-to-Site. Therefore, I used a service, NOIP, to help me. My USG will update this service every time that my public IP changes. It’s easy for me, after that, to host some websites/services at my home too, by creating a CNAME record.
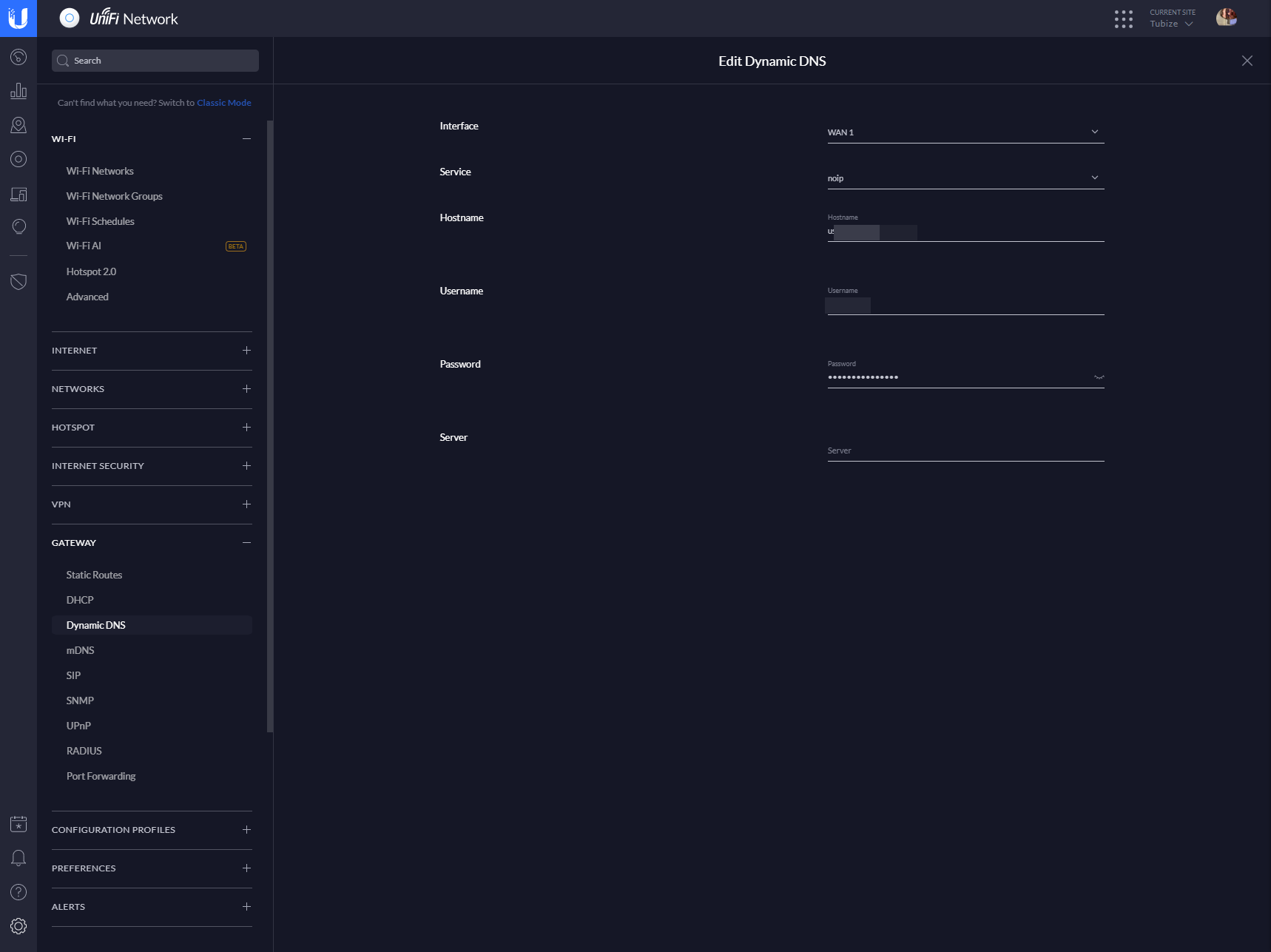
In your USG interface, go to Settings > Gateway > Dynamic DNS and choose on which interface you want to update your Dynamic DNS. WAN 1 for me. Choose the service where you created your dynamic DNS, provide the hostname that you have created on NOIP, and the username/password to authenticate to update the IP directly on your hostname:
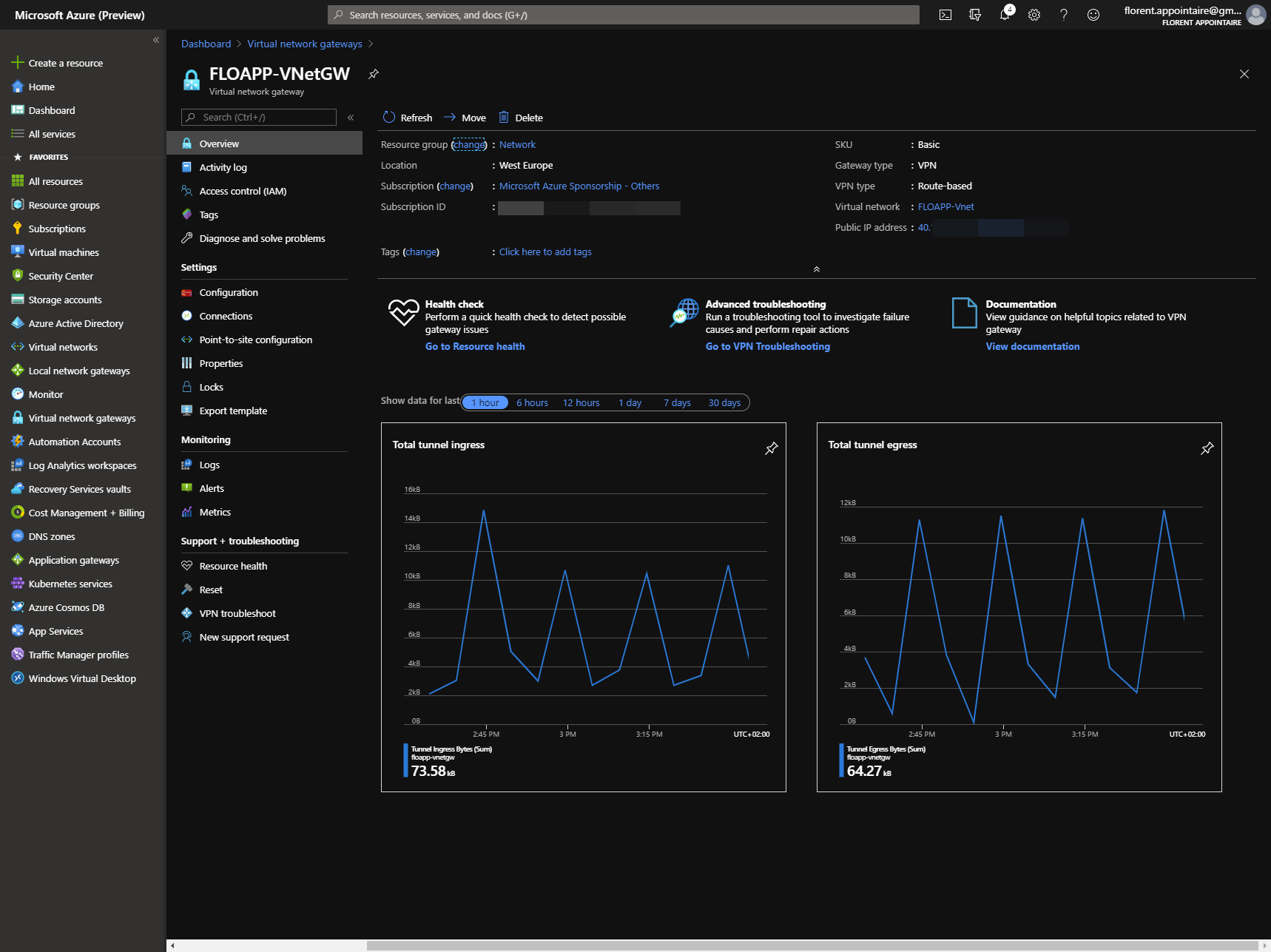
We will go to Azure Portal now, and we will return to this UI interface after. Create a Virtual Network Gateway with a SKU Basic. After 45 minutes, you will have your Virtual Network Gateway with a Public IP that you will need later:
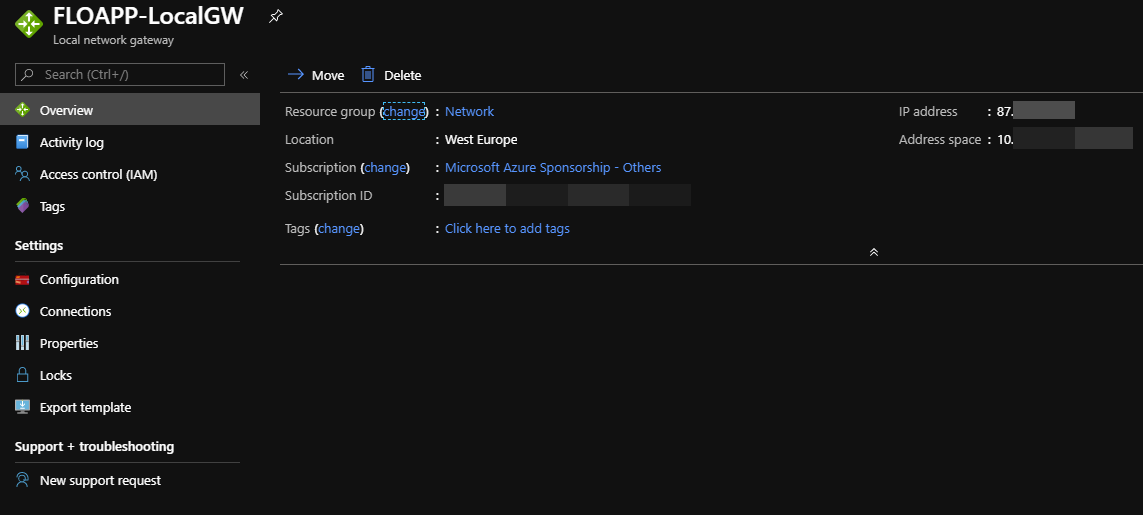
Now, create a local network gateway. It will contain the Public IP of your USG, and each On-Premises address spaces that you want to route on the S2S Tunnel:
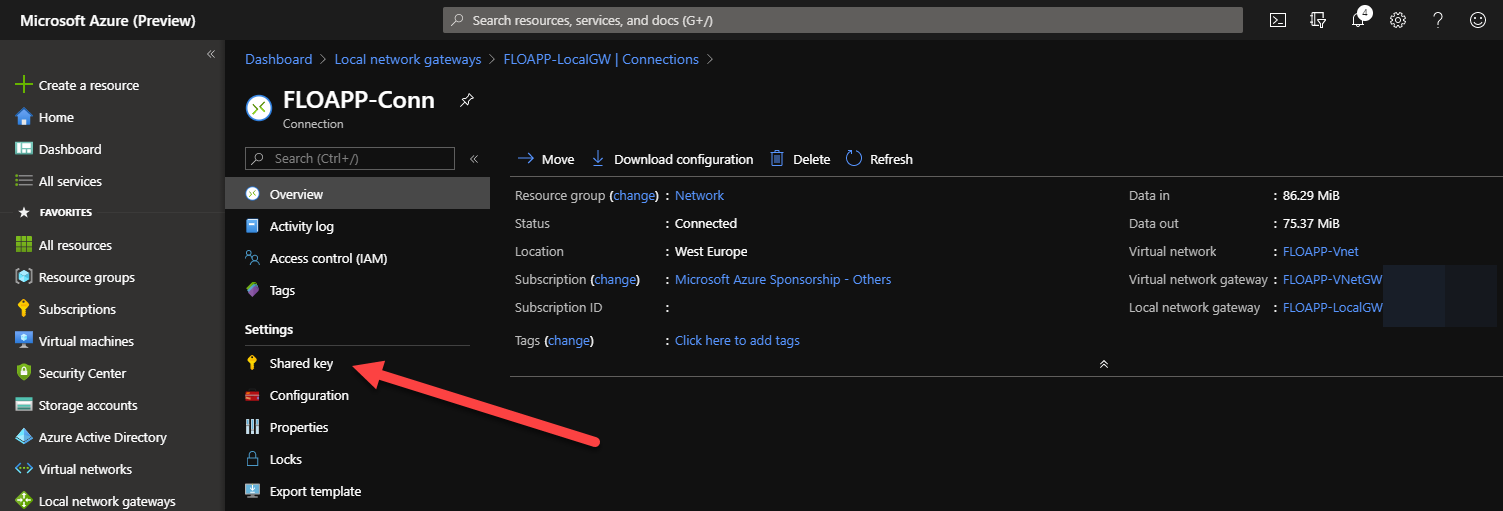
Afterwards, you need to create the connection between your Local Network Gateway and your VPN Gateway in Azure. Create a Shared Key and write it with your public IP on Azure:
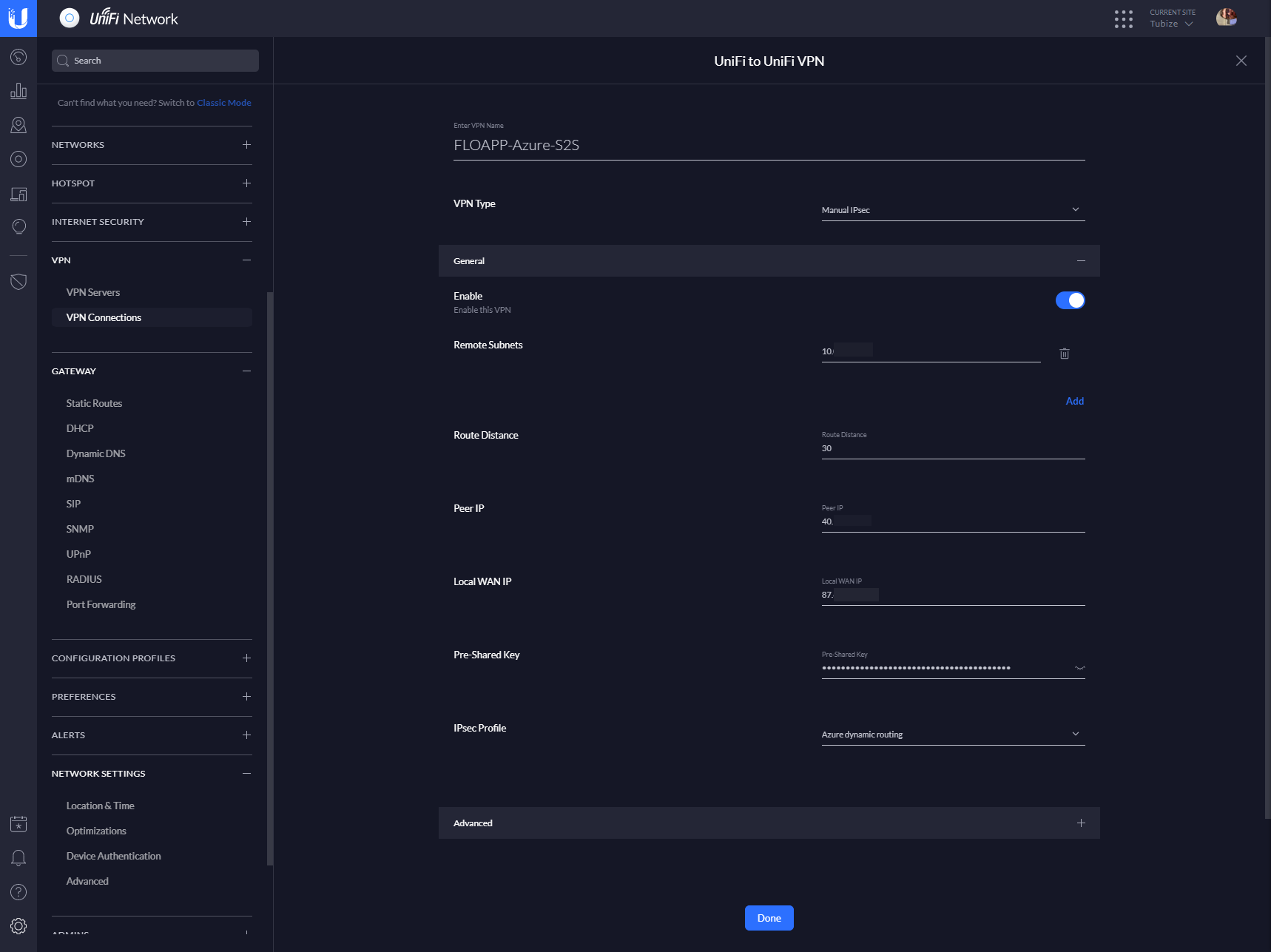
Then, go back to your UI interface. In Settings > VPN > VPN Connections create a new connection to external VPN. Choose the type Manual IPSec and provide the remote subnet where your VPN gateway is connected. Provide the peer IP (this is the IP from Azure), and in Local WAN IP, the IP of your USG WAN interface. At this time, you can’t choose an interface but you need to provide the IP. Provide the shared key that you created in Azure and, in IPSec profile, choose Azure dynamic routing:
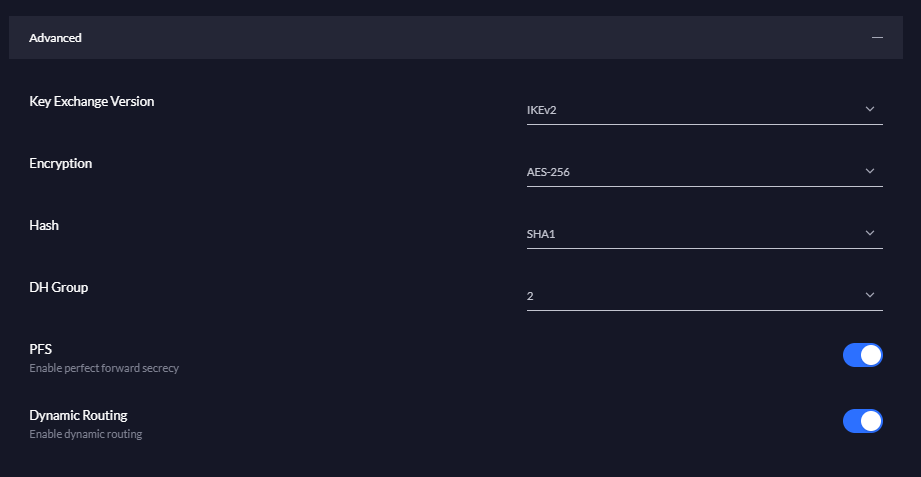
Regarding the encryption, choose the following:
- Key Exchange: IKEv2
- Encryption: AES-256
- Hash: SHA-1
- DH Group: 2
- PFS enable
- Dynamic Routing enable
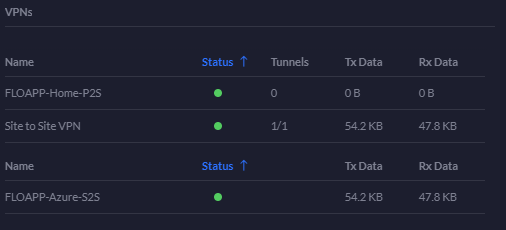
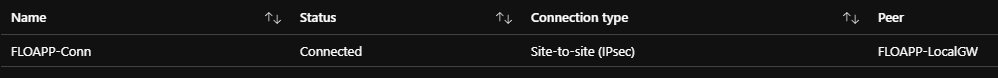
After a few minutes, the tunnel should be up and you should be able to access your VM from your PC to Azure:
I also created a runbook, that will run every 4 hours because of the 500 free Azure Automation minutes. It will check if your IP changed, and if it has changed, it will update your IP automatically with the following script:
|
Only one bug at this time as I already explained, it’s the Local WAN IP part on USG, to be able to select directly an interface.
Feel free to contact me if you have any questions