Introduction
Azure Firewall is a new network security feature in Azure. This new feature has been introduced in 2018 as a managed service in order to protect your Azure Virtual Network resources.
Azure Firewall offers the following features as described by Microsoft:
- Built-in high availability: No additional load balancers are required
- Unrestricted cloud scalability: Azure Firewall can scale up as much as you need
- Application FQDN filtering rules: You can limit outbound web traffic
- Network traffic filtering rules: You can allow or deny network filtering rules by source and destination IP address, port, and protocol
- FQDN tags: You can easily use tags to allow or deny traffic
- Outbound SNAT support: Outbound IP addresses are translated to the Azure Firewall public IP
- Inbound DNAT support: Inbound traffic to the firewall public IP address is translated to internal IP addresses.
- Azure Monitor logging: All events are integrated with Azure Monitor
In this article, we will explore the following steps:
-
- Create a Resource Group
- Create a vNet
- Create 3 subnets
- Create 2 Virtual Machines
- Deploy the Firewall
- Configure a default route
- Create an application rule
- Test the Firewall
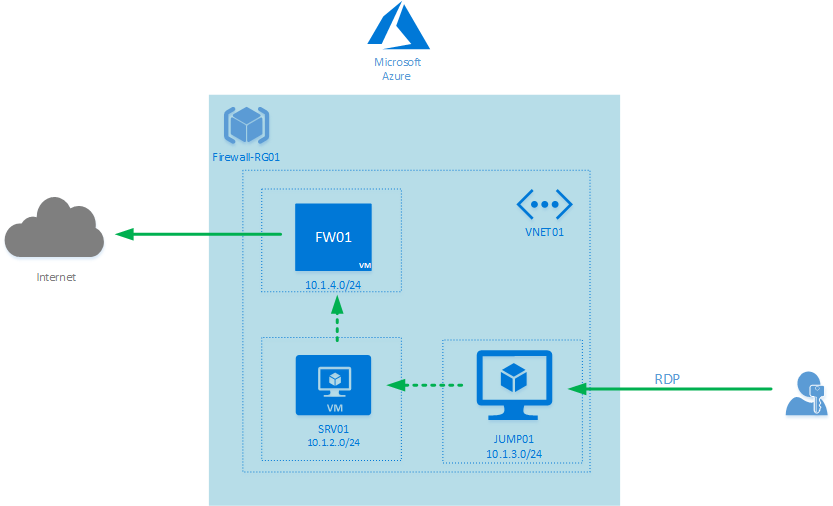
Here is an overview of the architecture:
Create a Resource Group
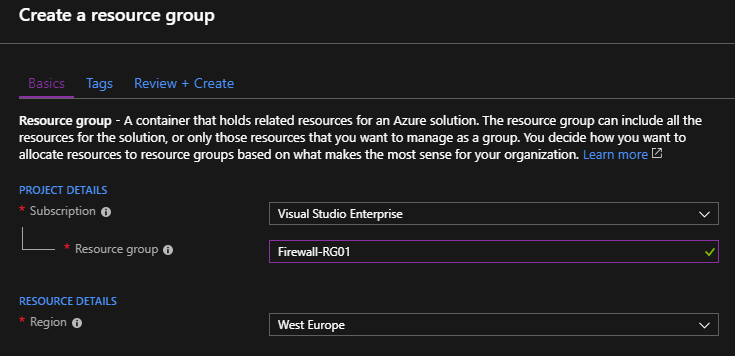
Let’s start this article by creating a new Resource Group. This Resource Group contains all the resources for this guide. Open the Azure portal and click Resource Groups.
-
-
- Subscription: Select your Azure subscription
- Resource group name: Type a friendly name
- Region: Select the location where the resources will be located
-
Validate by clicking Create.
Create a Virtual Network
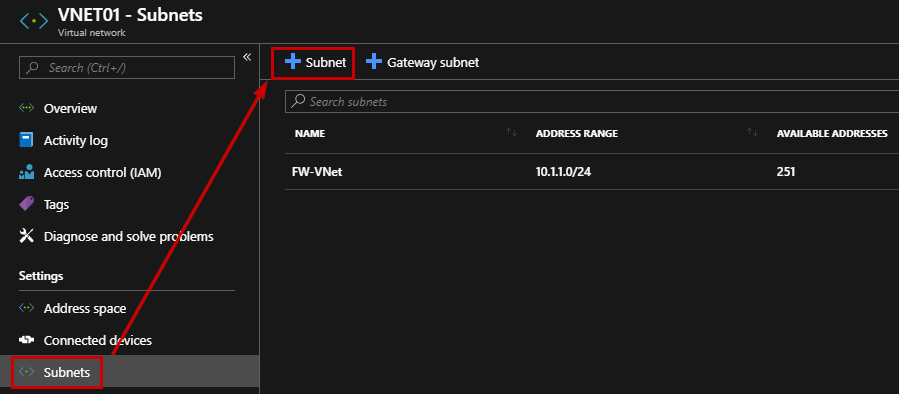
We need to create a single Virtual Network that will contain three subnets. Search for “Virtual Networks”
Enter the following information:
-
-
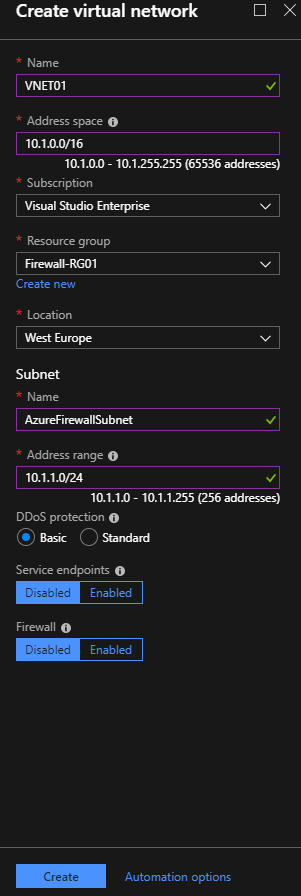
- Name: Type a friendly name for this Virtual Network
- Address space: Enter the address space you want
- Subscription: Select your Azure subscription
- Resource Group: Select the RG that you previously created
- Location: Select the location where the resource will be located
- Subnet: This step is very important because you must use a fixed name called “AzureFirewallSubnet”. (Be careful on my screenshot, the name is wrong)
-
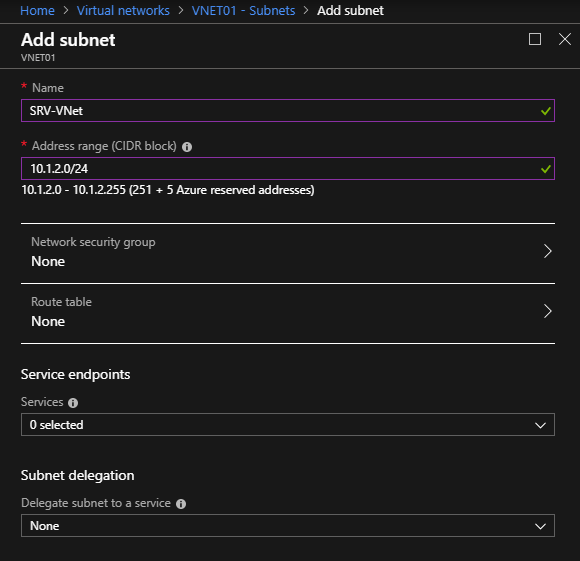
Once the Virtual Network is created, you must create the second subnet:
This subnet will contain a server. In this article, the address range is 10.1.2.0/24.
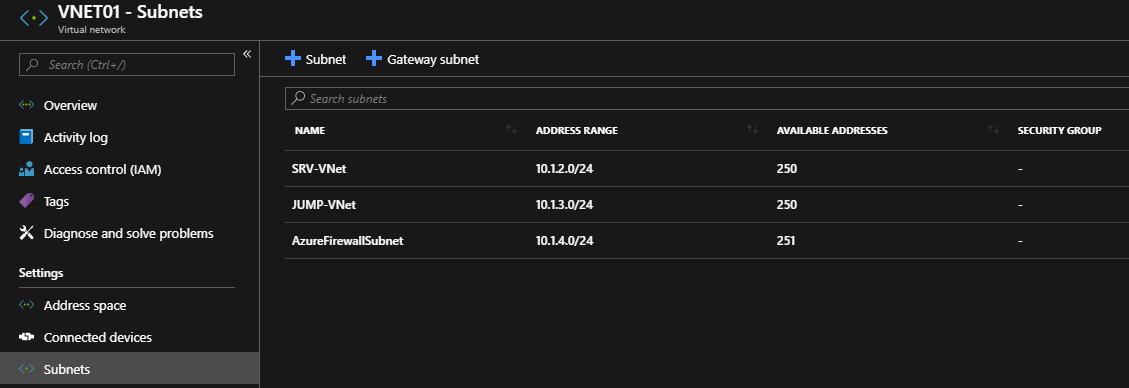
Repeat this step to create the subnet for the Jump server (10.1.3.0/24).
So finally, you will get the following subnets as shown below:
Create Virtual Machine
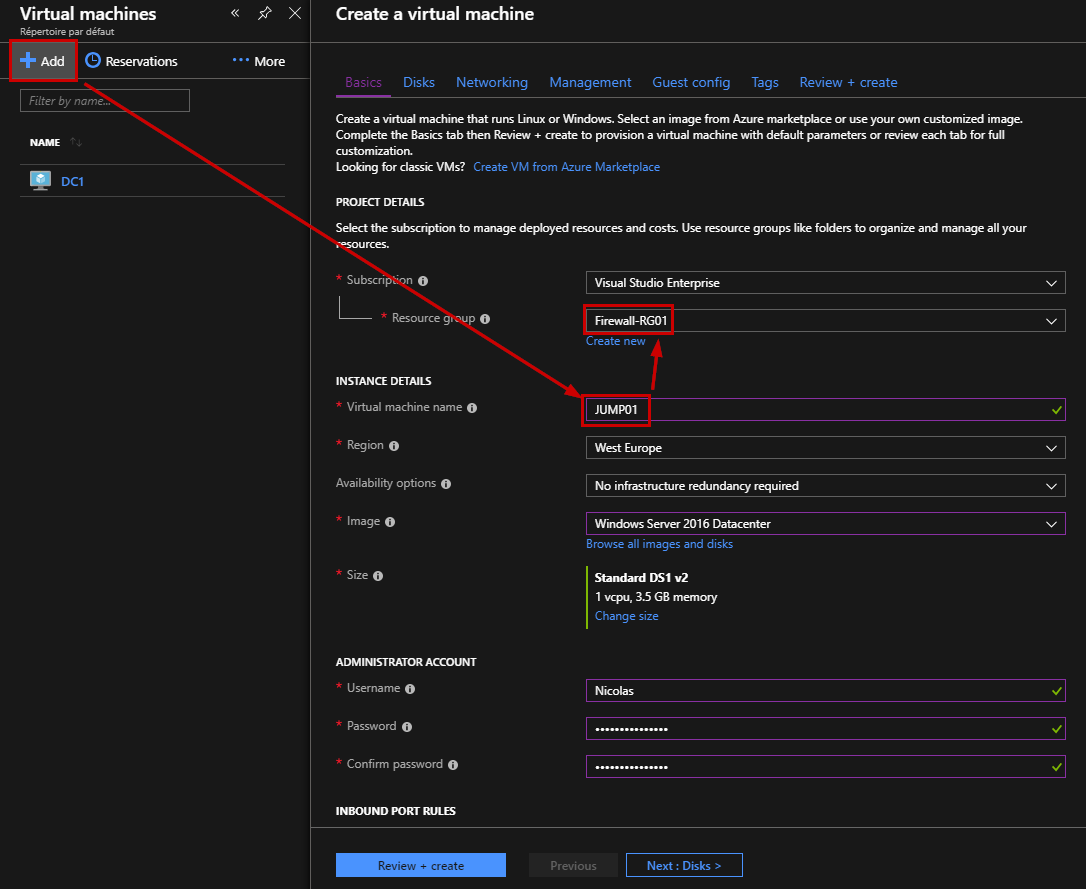
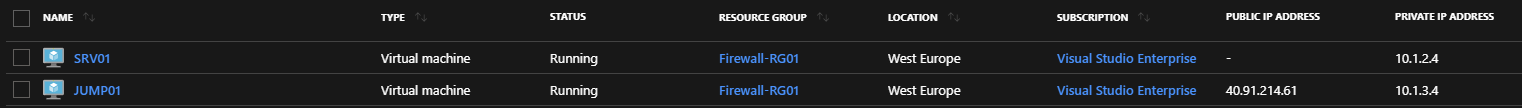
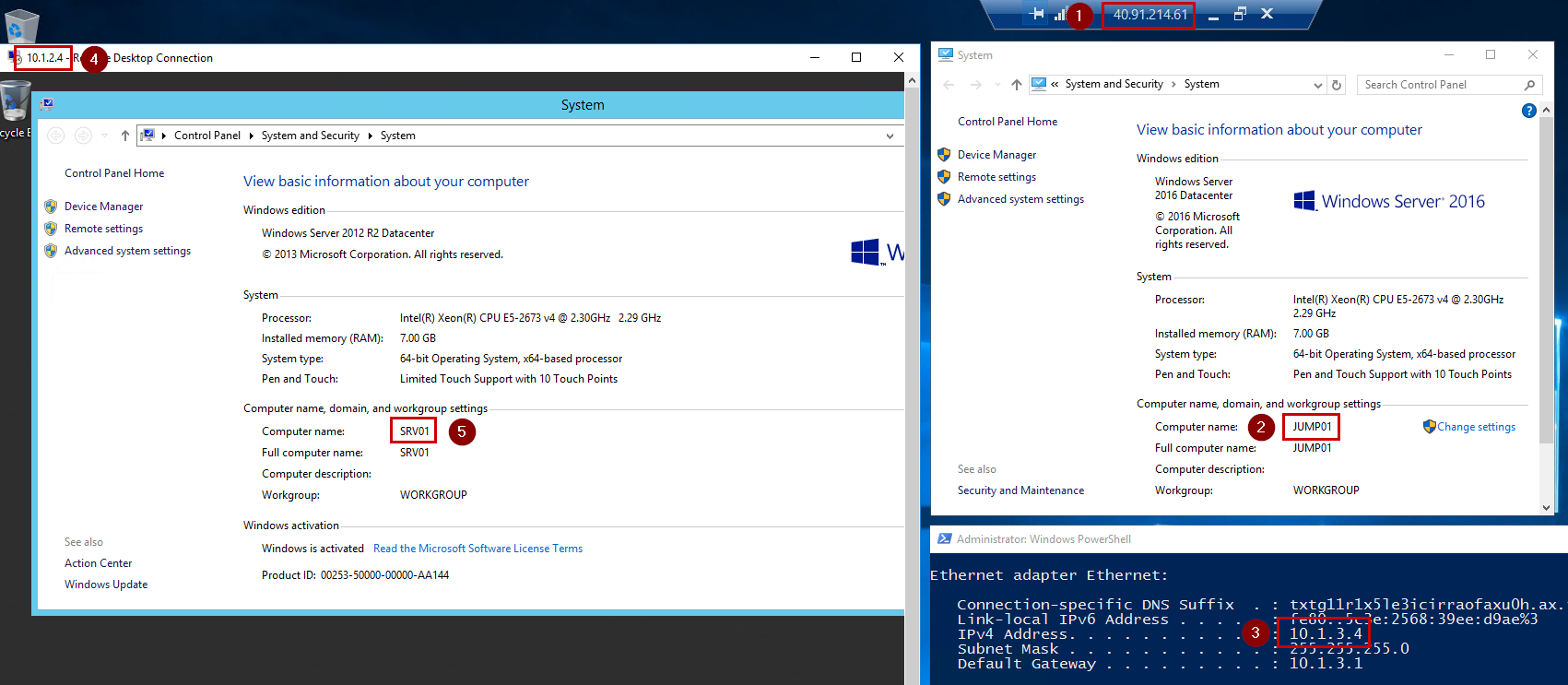
At this step, we created a Resource Group and a Virtual Network including three subnets. Now, we just need to create two Virtual Machines. The first one is the Jump server that will be used to connect to the second Virtual Machine. The Jump machine is called “JUMP01” and the server is called “SRV01”.
Create a new Virtual Machine using the Azure wizard and do not forget to add this Virtual Machine in the Resource Group previously created.
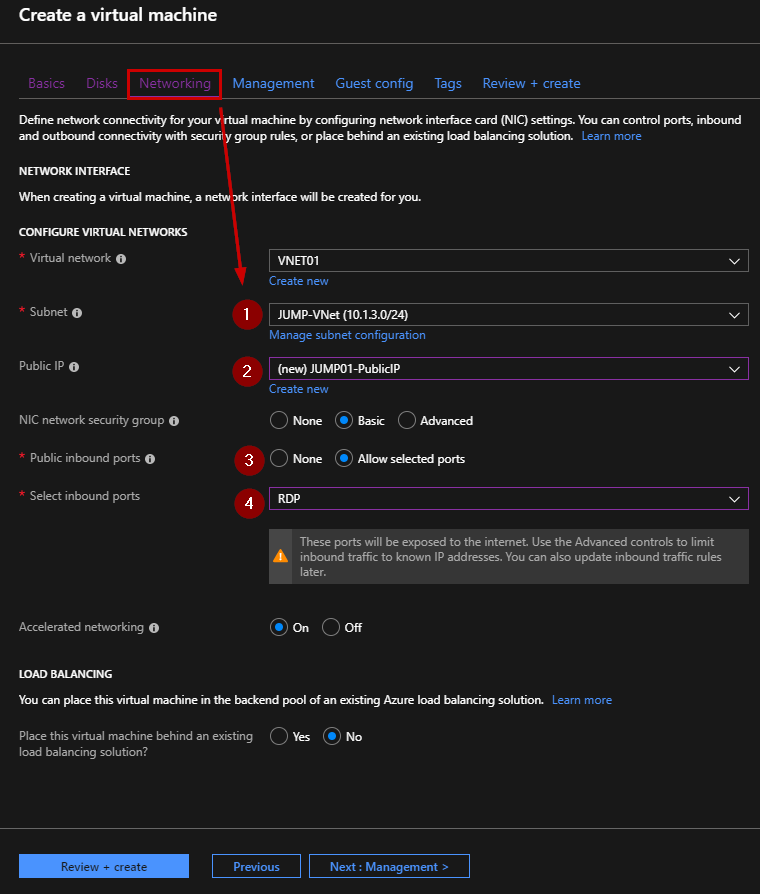
In the Networking area, select the Jump subnet and create a new Public IP Address in order to access to the jump server from the Internet. You just need to allow the RDP Protocol.
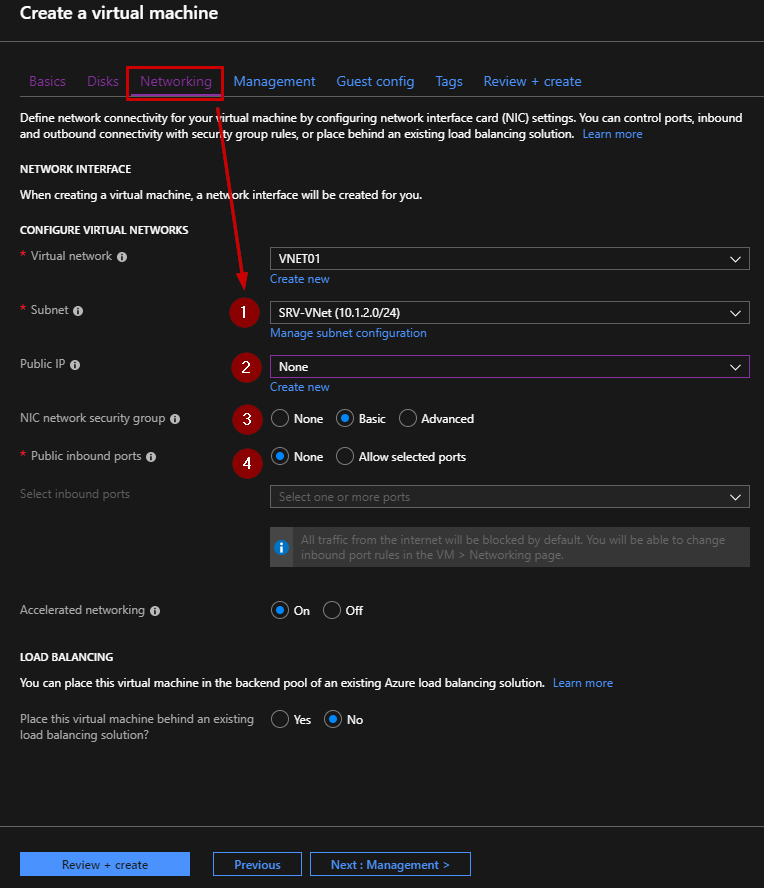
Repeat this step to deploy the SRV01 Virtual Machine.
This Virtual Machine must be located in the “SRV-VNet” subnet and you do not need to open any public inbound ports.
Deploy Azure Firewall
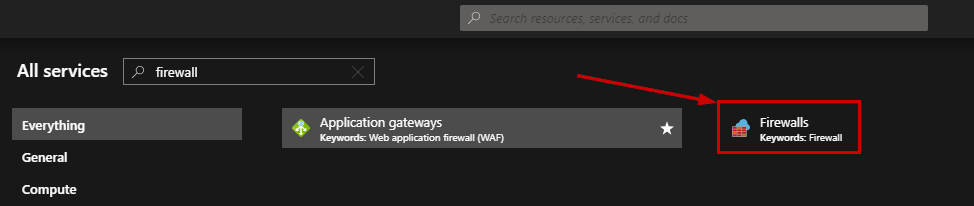
At this step, we need to deploy the Azure Firewall. So, go to the Azure Portal and search for “Firewalls”
Click “Add” to deploy your first Azure Firewall
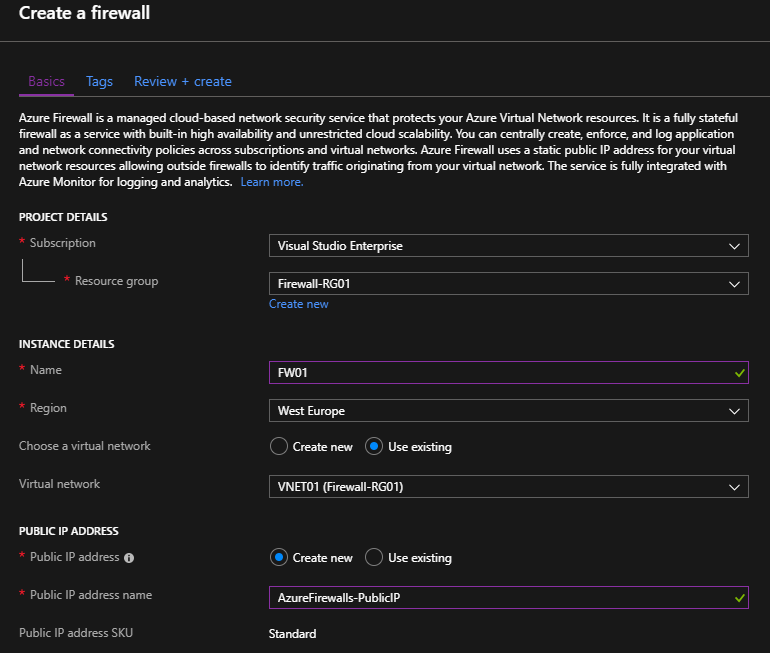
Enter the following information:
-
-
- Select your Azure subscription
- Select the Resource Group previously created
- Enter a friendly name for your Firewall
- Select the Virtual Network previously created
- And do not forget to create a Public IP Address
-
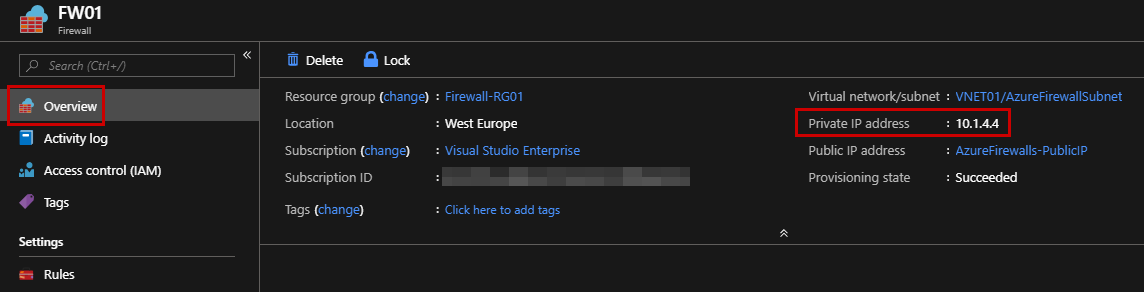
Once the Firewall is created, note the private IP address in the overview section, because you will need it later.
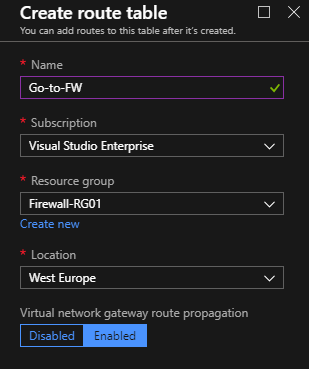
Create The Route Tables
Go to the Azure Portal and search for “Route tables”
Create a new route table called “Go-To-FW”. This route table will contain the default route that your server will choose to route the traffic.
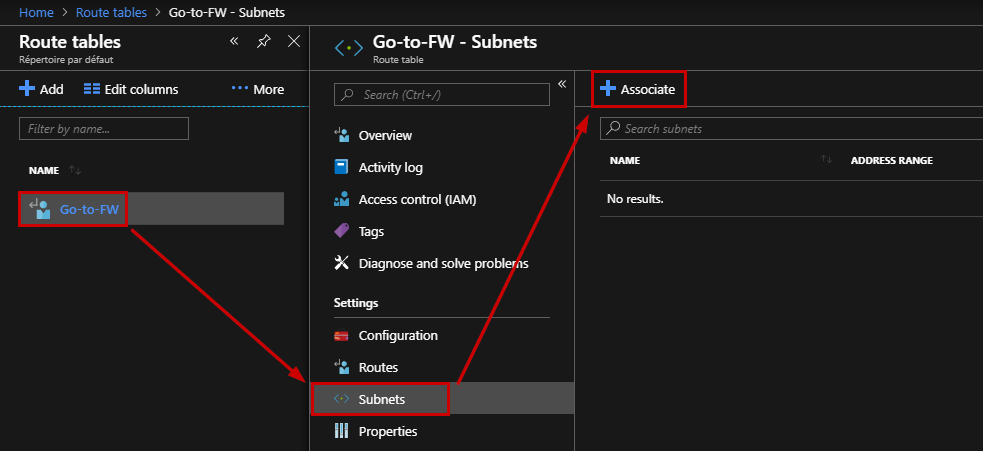
Once the route table is created, you must associate the server subnet to this route table. Go to the “Subnets” section and click “Associate”
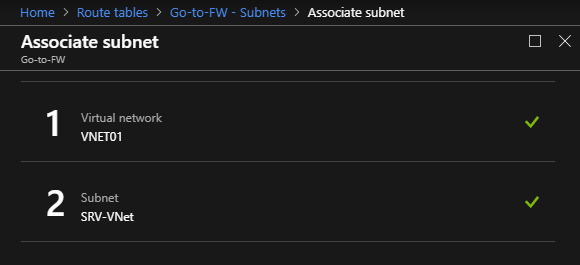
Select the Virtual Network and the Subnet:
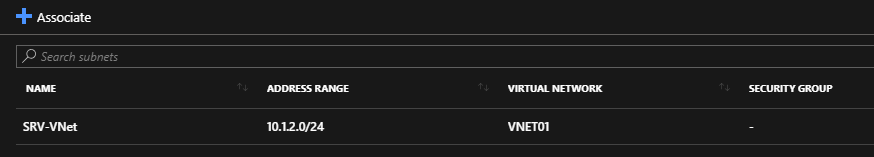
You should see the following output:
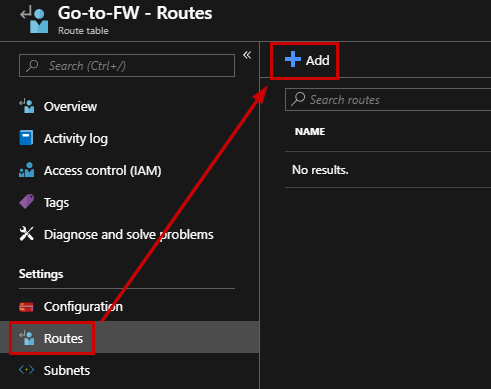
Now, we must add a default route to the Virtual Appliance. Go to the “Routes” section and click “Add”
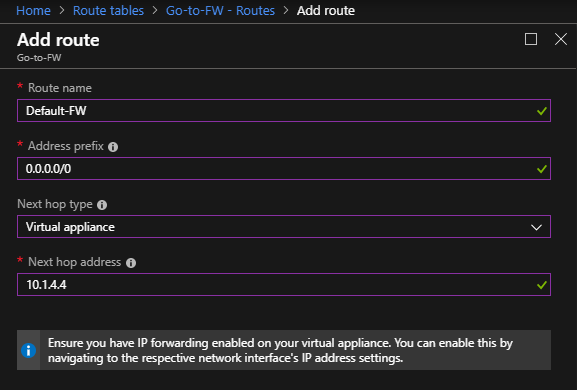
Enter the following information:
-
-
- Route name: it is a friendly name for the default route
- Address prefix: To indicate the default route, you must enter 0.0.0.0/0
- Next hop type: Select “Virtual Appliance”
- Next hop address: Enter the private IP Address that you copied previously
-
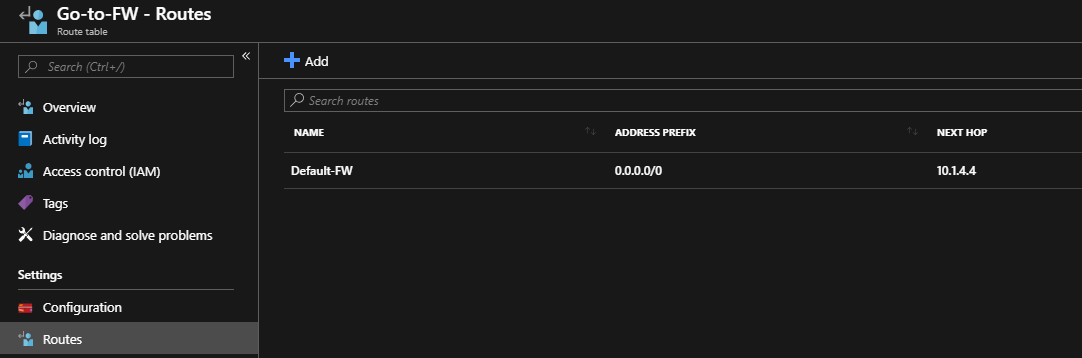
You should see something like that:
Create Application Rule Collection
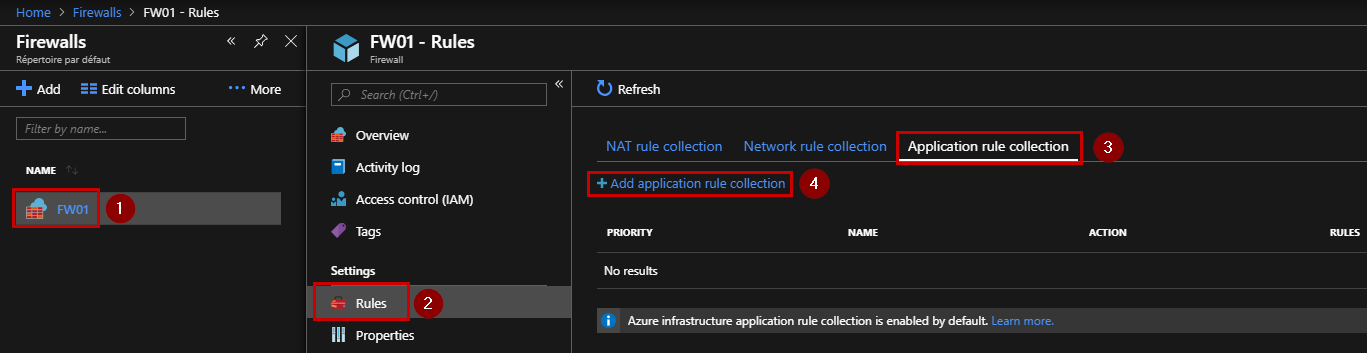
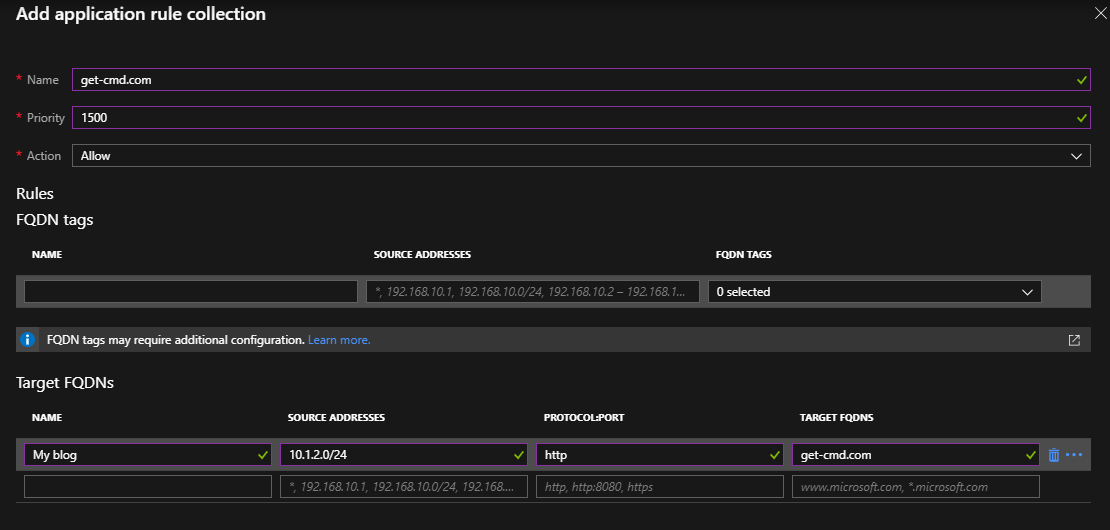
The Firewall is deployed, so we can add an application rule in order to filter the outbound web traffic. Go to the “Rules” section, and click “Add application rule collection“:
Enter a friendly name for this rule, then set a priority and select the action (Allow or Deny). Next, you must indicate the source addresses, the protocol and the target FQDN.
In my case, I want to allow web traffic to my personal blog from the SRV01 Virtual Machine.
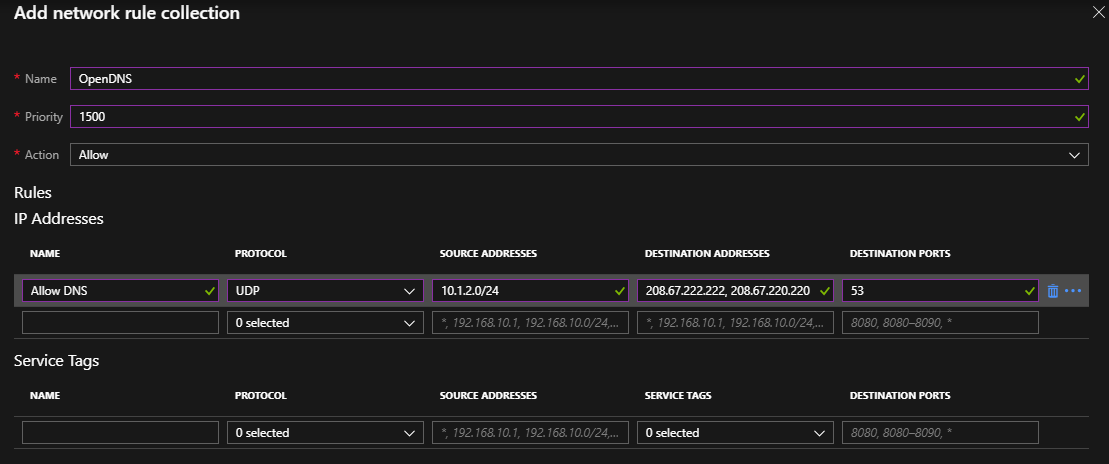
To resolve the FQDN, the machine must be able to contact DNS servers. In this article, I created a network rule to allow the DNS requests from the server subnet to the OpenDNS Servers.
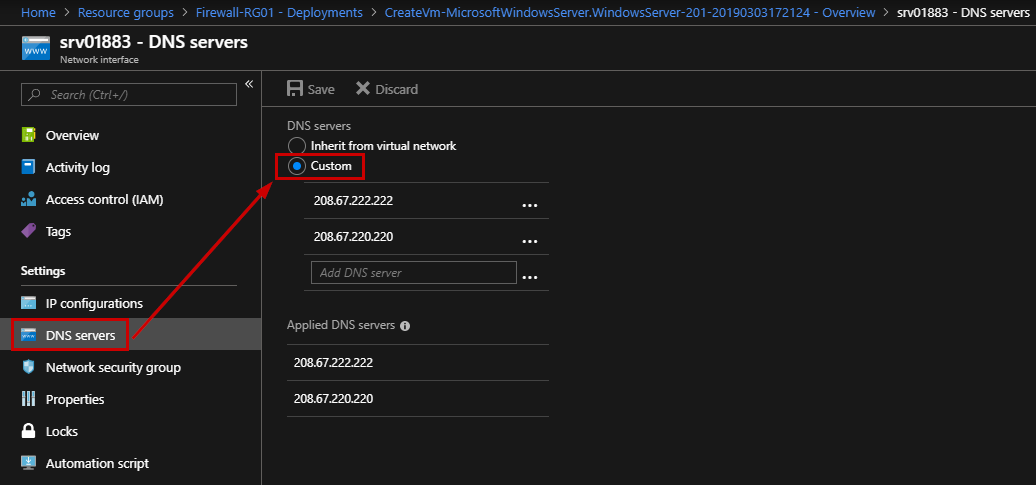
Now, you must be sure that your machine will use this DNS addresses to resolve FQDNS. Go to the network interface, and add custom DNS servers.
Do not forget to reboot the machine in order to take effects.
Test the Firewall
Now, it’s time to test our Firewall rules! First, we need to connect to the Jump Server from the Public IP Address.
Then, I can start a new MSTSC window to connect to the SRV01 machine using the private IP Address.
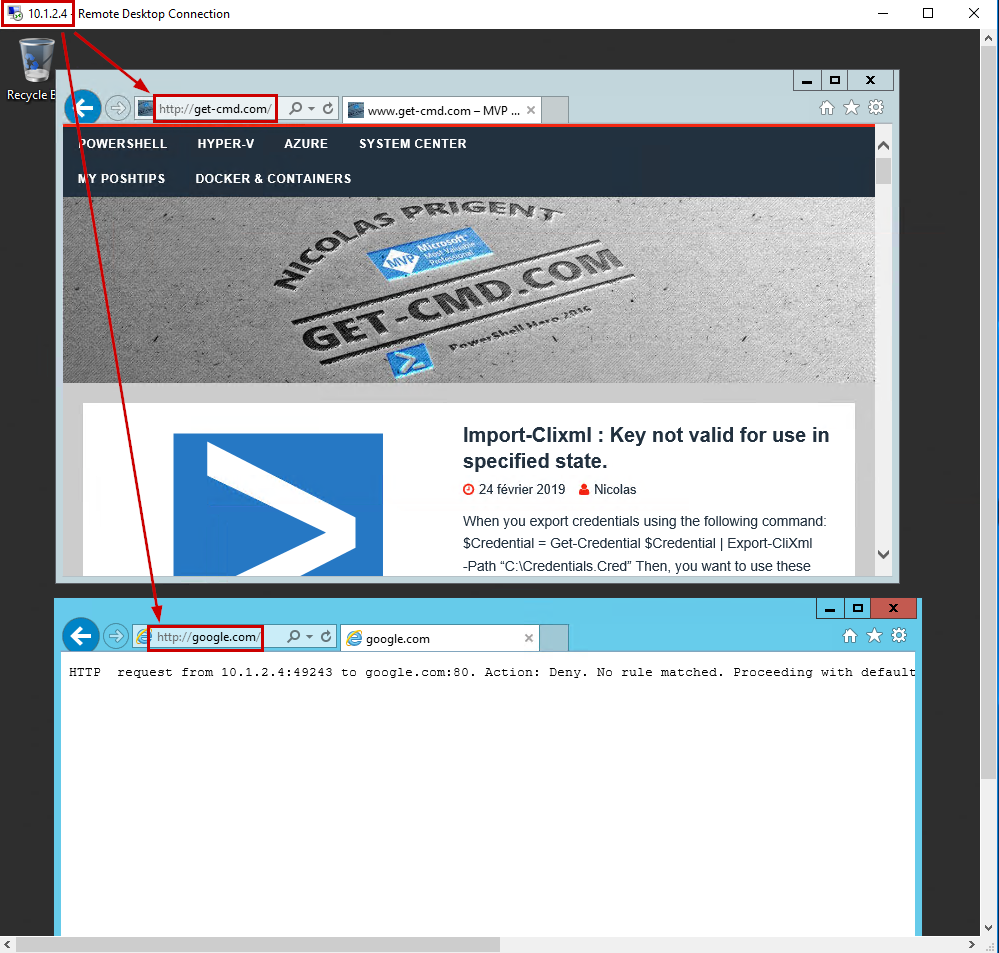
The last step is to check the application rule previously created in the Azure Firewall. I just need to open a web browser and type the website URL.
In my case, I can confirm that my blog is responding but if try to browse Google, an error message appears. I should create an application rule to allow www.google.com.
Conclusion
Thanks to Azure Firewall, you can very easily and quickly protect your Azure Resources. You can also automate tasks using Azure PowerShell.
Azure Firewall allows you to create Application Rules and Network Rules to control the inbound and outbound network traffic.
Thanks for reading!