Nowadays, email and web access are critical for most of the daily operation in any organization, and therefore is considered as the biggest threat surface and a significant source of attacks and incidents. Properly protecting email servers, web browsers and mail clients can reduce drastically security incidents in your organization and improve the security posture of your organization.
In the CIS 20 security controls, there is a specific control dedicated to this topic, covering the basics of browser and email client safety. It mainly consists of limiting scripting in browsers and email clients, but also attachment handling, URL logging, filtering and whitelisting. Your users and your network aren’t secure if your browsers and emails aren’t secure!
Where to start?
Since this domain touches many different IT functions, it’s important to have the right people responsible of the different systems on board when working on this topic. It’s an opportunity to federate multiple IT functions together with a common goal!
Filtering is a good starting point
Successful implementations of such control usually work from two sides: the server and network side and the endpoint configuration and application side. The first thing to do is to limit how attachments are handled and forwarded from the mail server to clients, to filter potential malicious content before it reaches the end users and their inboxes. Usually the networking and email server teams should be involved in such configuration.
Sender Policy Framework (SPF) to limit malicious mail traffic
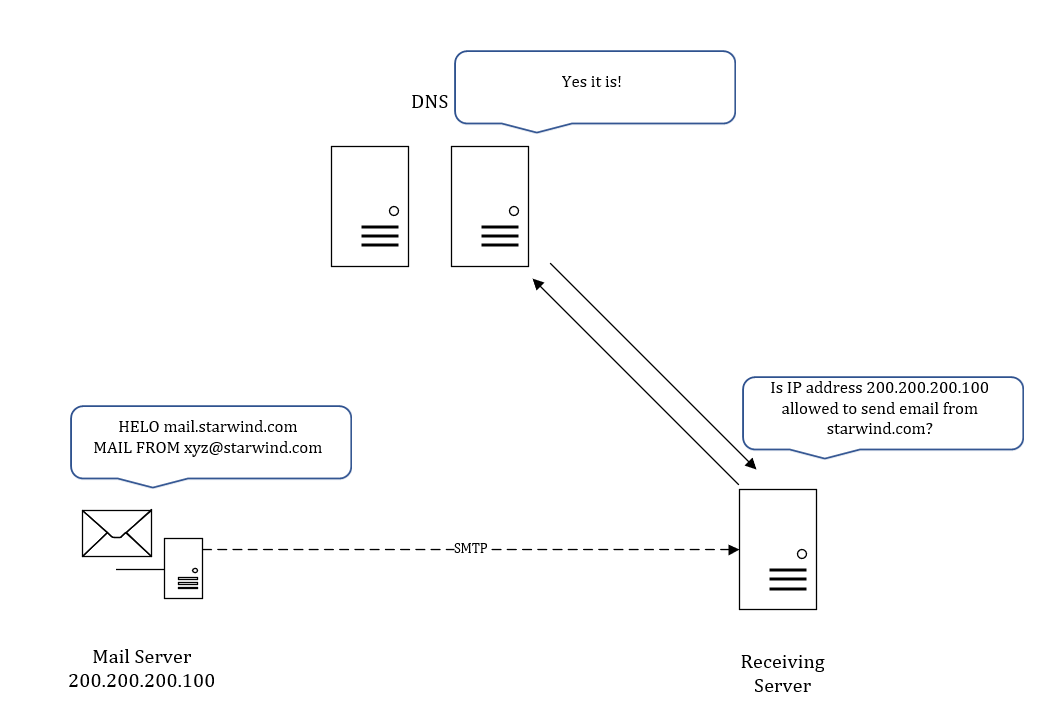
SPF is an email authentication method that specifies the mail servers authorized to send email from your domain. It helps protect your domain from spoofing, and helps ensure that your messages are delivered correctly. It ensures that messages coming from your domain actually are from your domain. It should then cut down the amount of spam and malicious traffic that is coming in to the system. As such, it’s not an anti-spam measure, it’s effective as a control for malicious mail traffic.
Below is very simple high level representation of how SPF works:
On top of SPF, there are a couple of other authentication methods that should be looked into:
- DKMI adds a digital signature to every message. This lets receiving servers verify that messages aren’t forged, and weren’t changed during transit.
- DMARC authenticates messages with SPF and DKIM, and manages suspicious incoming messages
Manage browsers and clients
By far the most difficult part, but basically you should:
- Ensure that only fully supported web browser and email clients are allowed to execute in your organization, ideally only using the latest version of the browsers and email clients provided by the vendor. Update should happen as soon as they become available and a formal written policy should be developed to address user behaviors Doing so will significantly minimize your attack surface.
- Uninstall or disable any unauthorized browser or email client plugins or add-on applications. You can for example scan browsers for extensions on a regular basis.
- Limit use of scripting languages in web browsers and email clients
On top of these controls on clients, you should consider to:
- Enforce network-based URL filters that limit a system’s ability to connect to websites not approved by the organization. This filtering shall be enforced for each of the organization’s systems.
- Subscribe to URL-categorization services to ensure that they are up-to-date with the most recent website category definitions available. By default, uncategorized sites shall be blocked.
- Log all URL requests from each of the organization’s systems, whether on-site or a mobile device, in order to identify potentially malicious activity and assist incident handlers with identifying potentially compromised systems.
- Use Domain Name System (DNS) filtering services to help block access to known malicious domains
- Block all email attachments entering the organization’s email gateway if the file types are unnecessary for the organization’s business.
- Sandbox all email attachments to analyze and block inbound email attachments with malicious behavior
Summary
Properly securing email servers, web browsers, and mail clients can drastically improve the security posture of your organization and limit security misfortunes that continue to make today’s news headlines.
This can simply be summarized as: if your browsers and email are not properly secured, you can guarantee your users and your network aren’t either!