A Temporary Access Pass (TAP) is a time-limited passcode issued by an admin that satisfies strong authentication requirements (Microsoft definition). TAP can be used in two different contexts:
- When onboarding a user to register another authentication method (such as Microsoft Authenticator or FIDO2)
- When a user recovers a lost or a forgotten of their strong authentication method (for example a user lost FIDO2 key)
TAP is a passwordless authentication methods like a FIDO2 or a Passwordless phone sign-in through Microsoft authenticator. So TAP helps to register a passwordless authentication methods without users specify a personal E-mail address or a mobile phone at the first registration.
From my point of view, it is a good method to onboard new user in a company. We can provide a TAP password to this user for his first log in. Then he can register a passwordless authentication method. TAP helps to embrace a full passwordless world.
In this topic, we’ll see how to enable TAP and how to create a TAP for a user.
Enable Temporary Access Pass
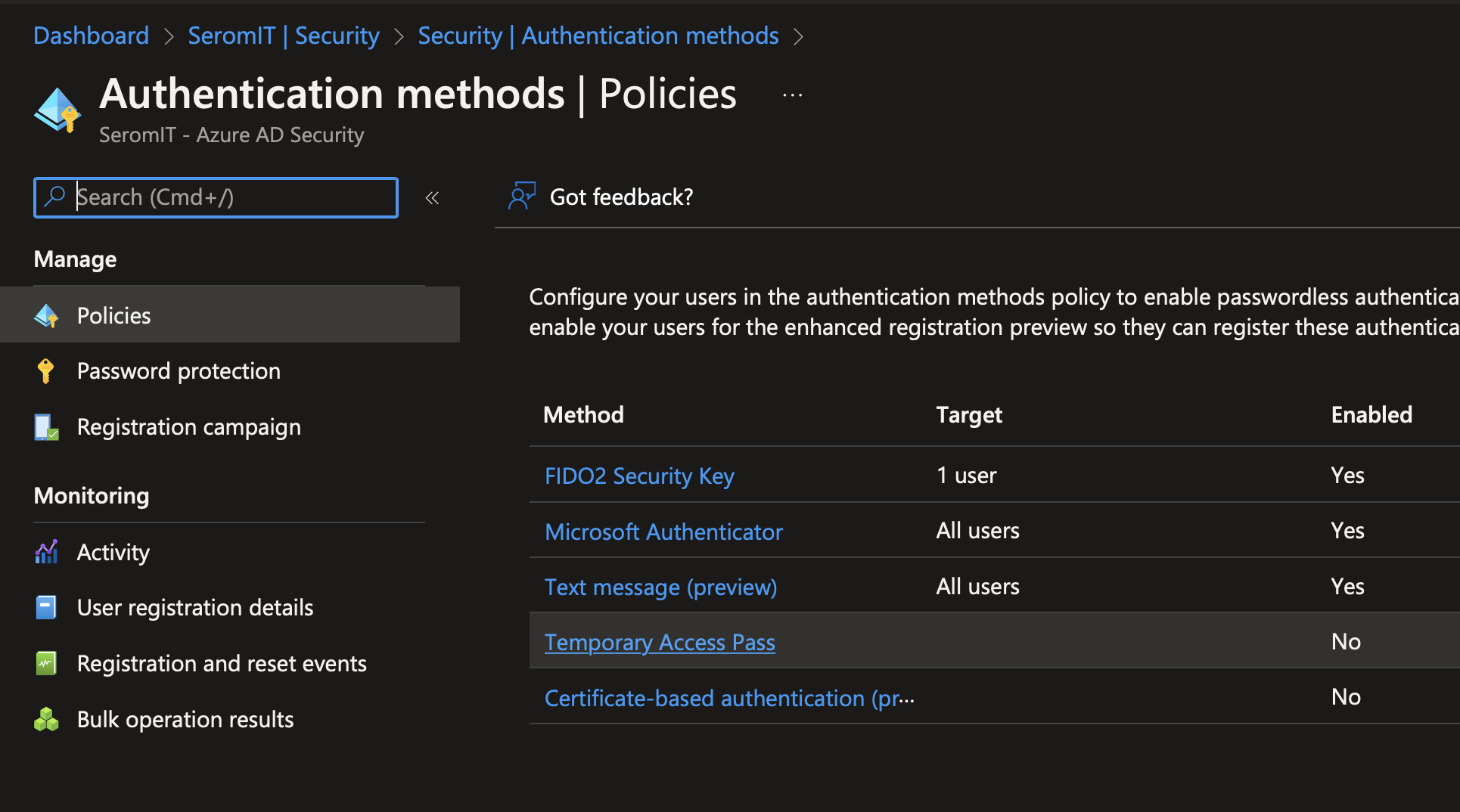
First open your Azure AD and navigate to Security > Authentication Methods. Then in Policies, select Temporary Access Pass.
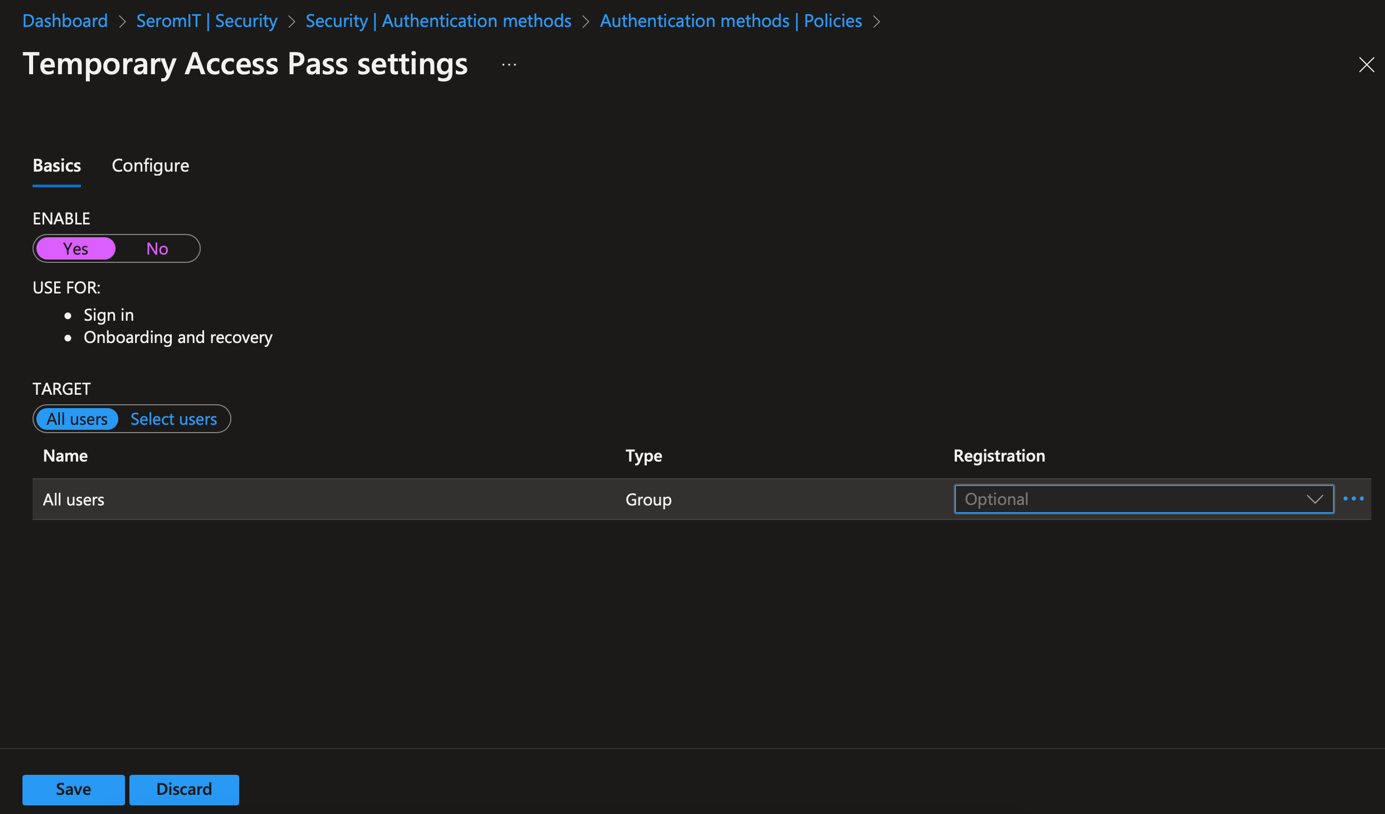
Enable Temporary Access Pass and choose a target.
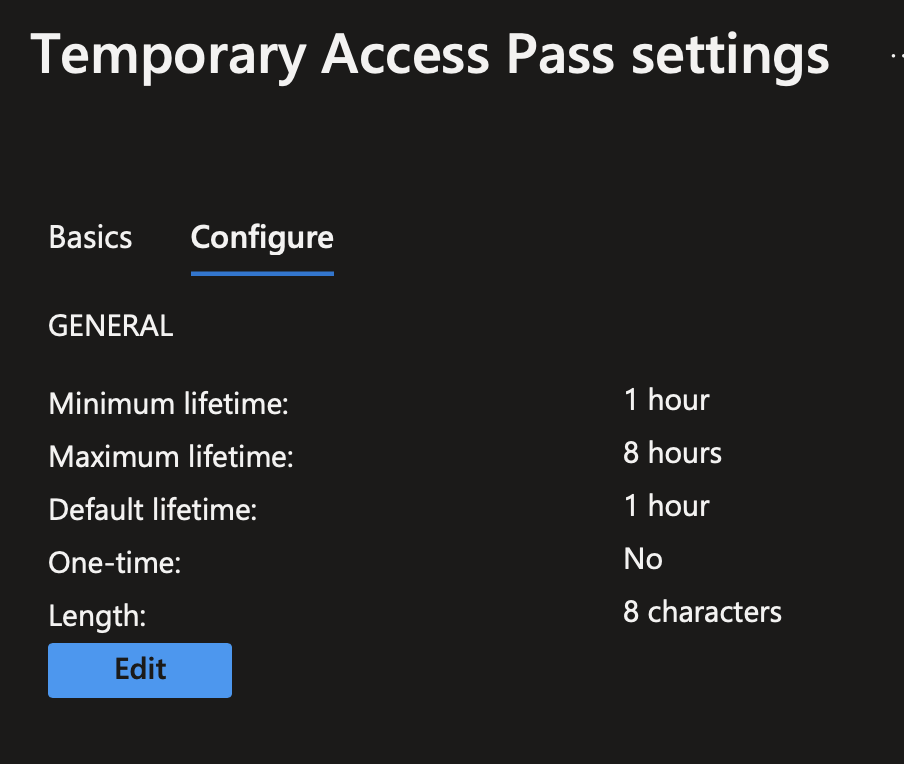
In Configure, you can change the lifetime and the length of the TAP. You can also set TAP to be used one time or several time.
Enable a TAP for a user
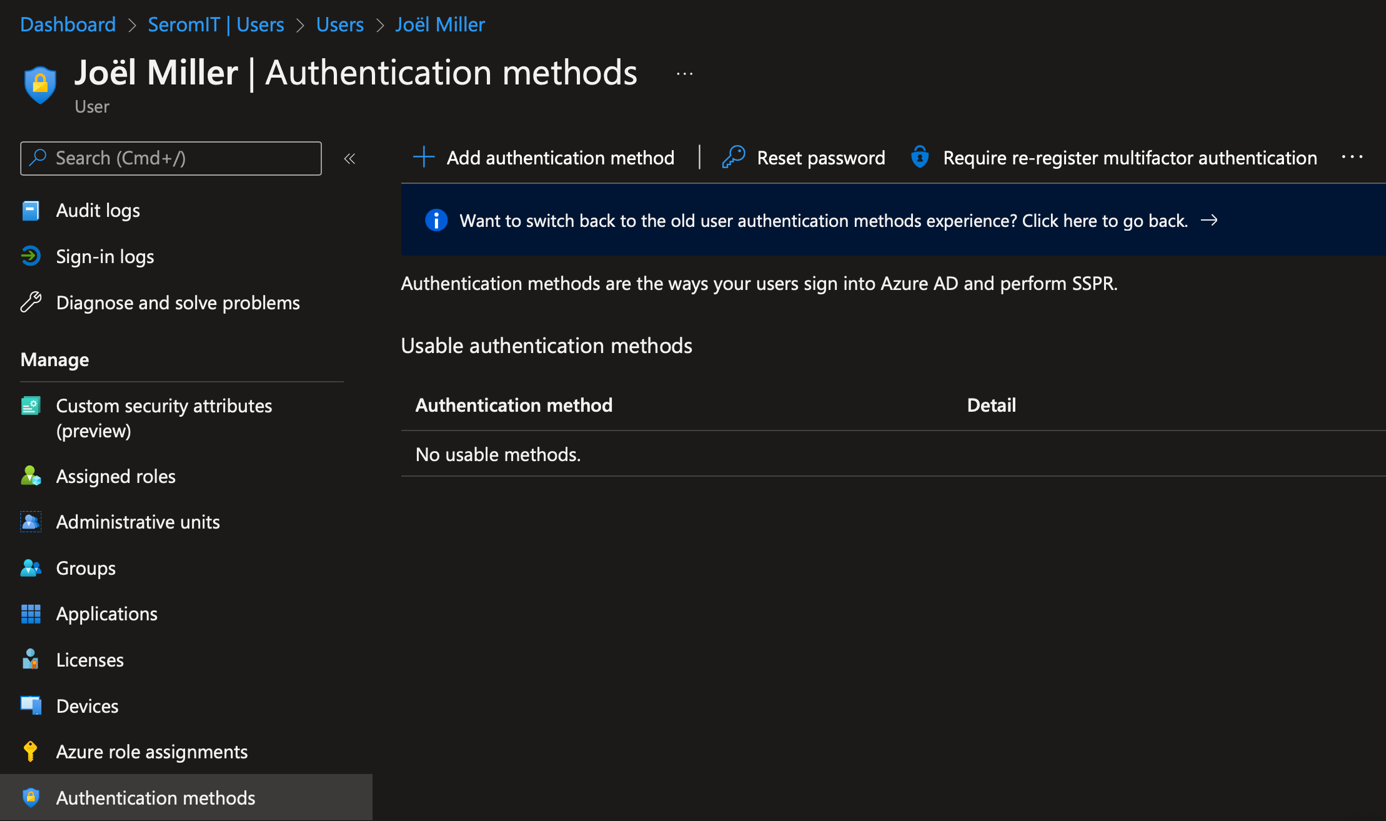
In Azure AD navigate to users, a select a user. In Authentication methods, click on Add authentication method.
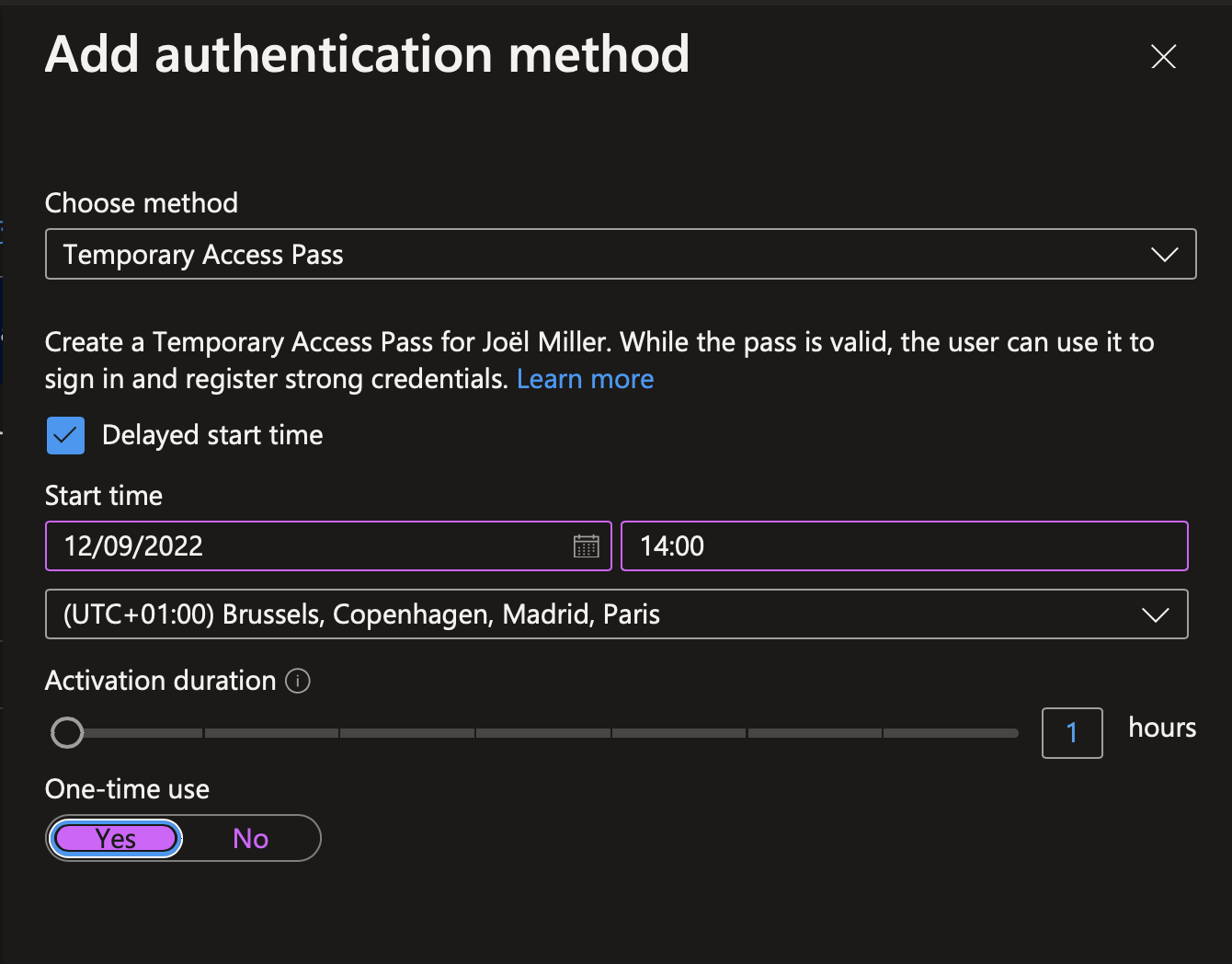
In the next screen, you can delay start time of the TAP. For example, you know that a new employee is coming next Monday, you can delay the TAP for the next Monday. You can also choose the TAP activation duration and if the TAP is useable one time or several time.
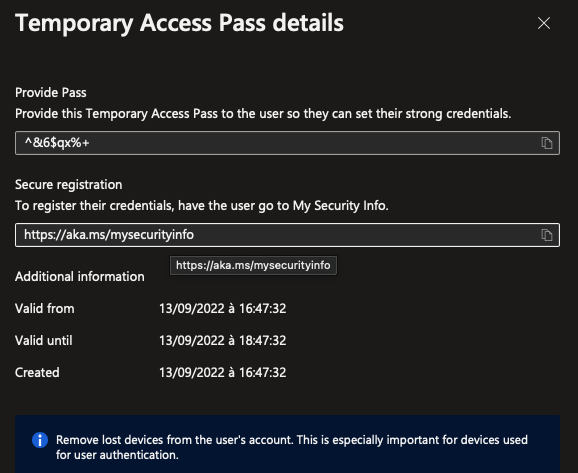
A pass is generated and Microsoft provide a link to go to security info in Azure AD profile.
Use Temporary Access Pass
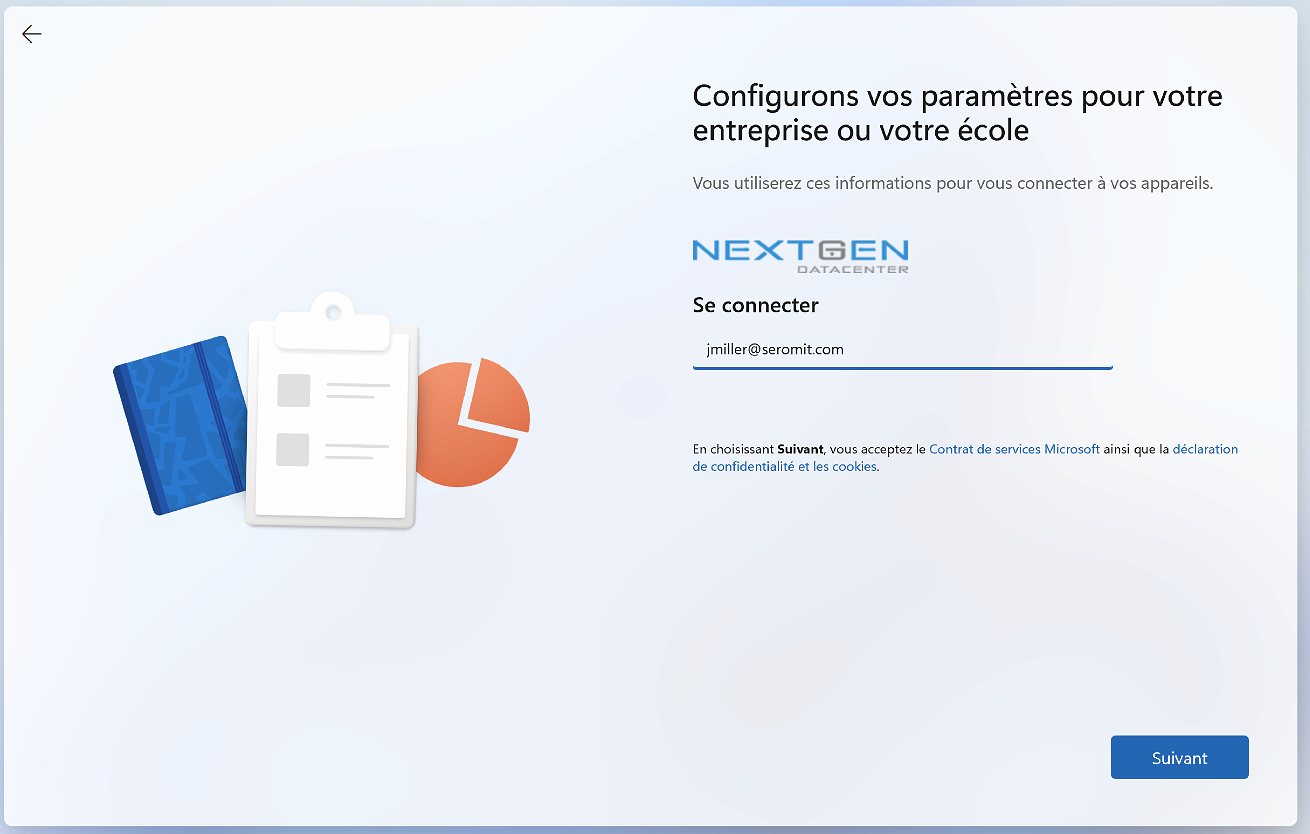
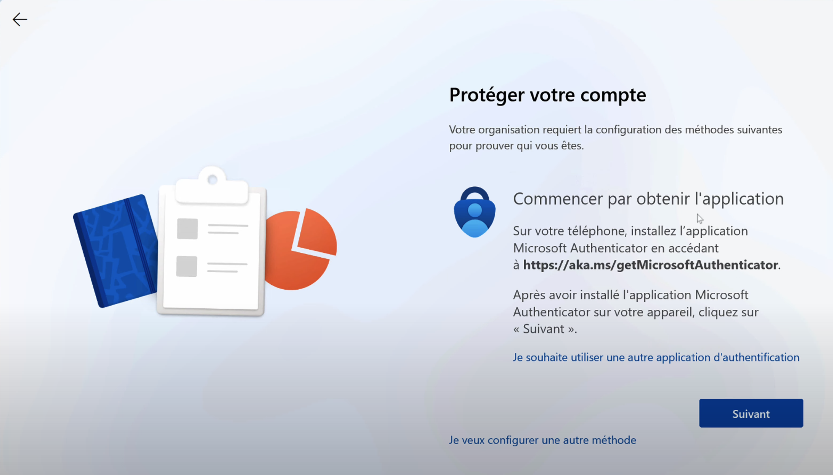
In the following screenshot (sorry for French screenshot), I use TAP in Autopilot process. So the user specify his E-mail address.
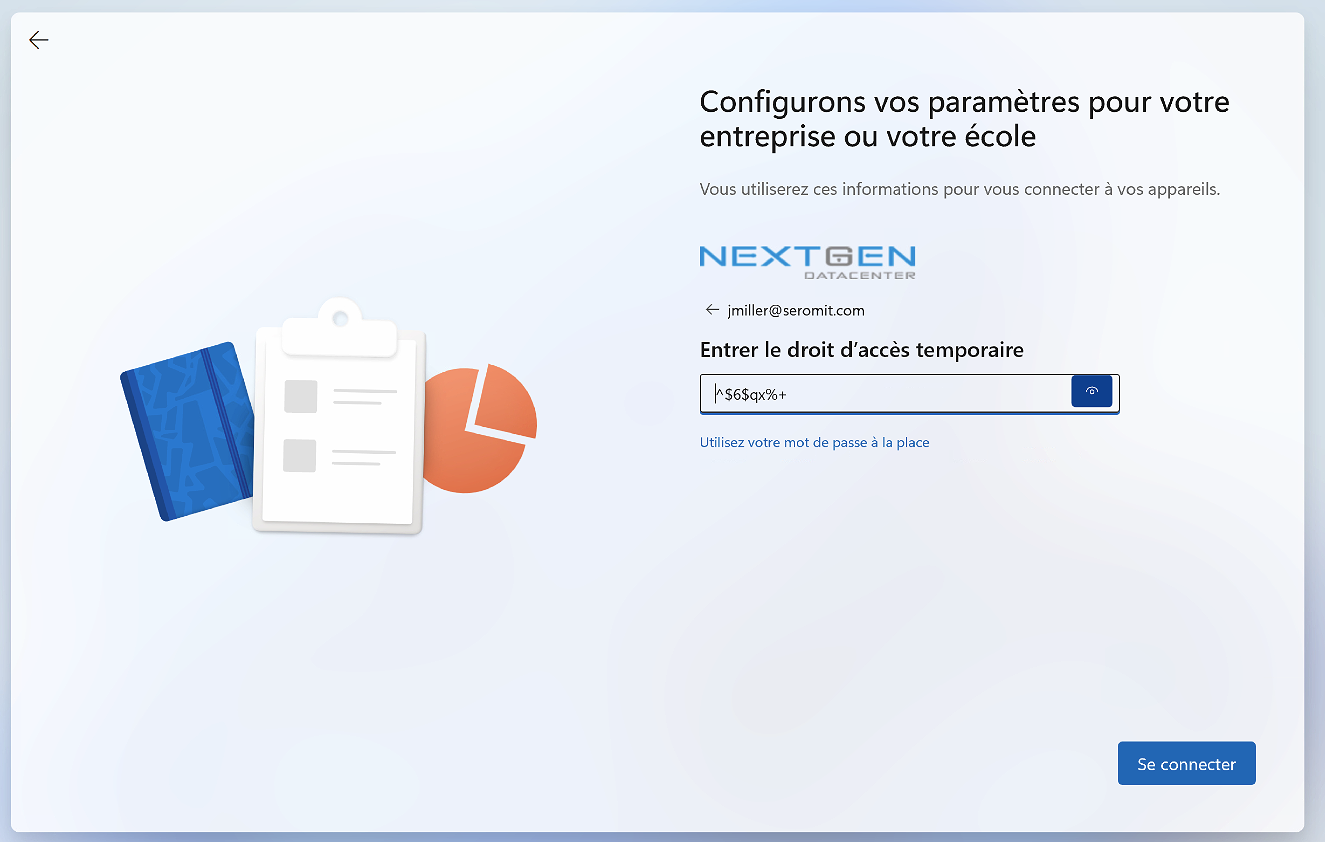
Then the user can type their Temporary Access Pass.
After that the user is asked to register Microsoft Authenticator or a FIDO2 key. If you use Microsoft Authenticator, I recommend heavily to configure Microsoft Authenticator from the smartphone to get passwordless authentication.