When you deploy virtual machines in Microsoft Azure, they come without Bitlocker enabled. That can be a problem regarding your corporate security policy. To encrypt your Windows Azure VM (or Linux with DM-Crypt), we can leverage Azure Disk Encryption (ADE). ADE provides volume encryption of Azure VM through Bitlocker or DM-Crypt.
Because there is no TPM, ADE requires a secret to encrypt data. This secret comes from Azure Key Vault which is a cloud service for securely storing and accessing secrets. To protect this secret, you can generate a key from Azure Key Vault. You can also bring your own key via your own HSM device. In this topic we’ll see how to configure both services to encrypt a Windows Azure VM.
N.B: In this topic you will see that all the configuration is easy. However, I recommend you take your time to configure Azure Key Vault especially the key part. All the security is based on the key, and I heavily recommend you to bring your own key.
Configure Azure Key Vault
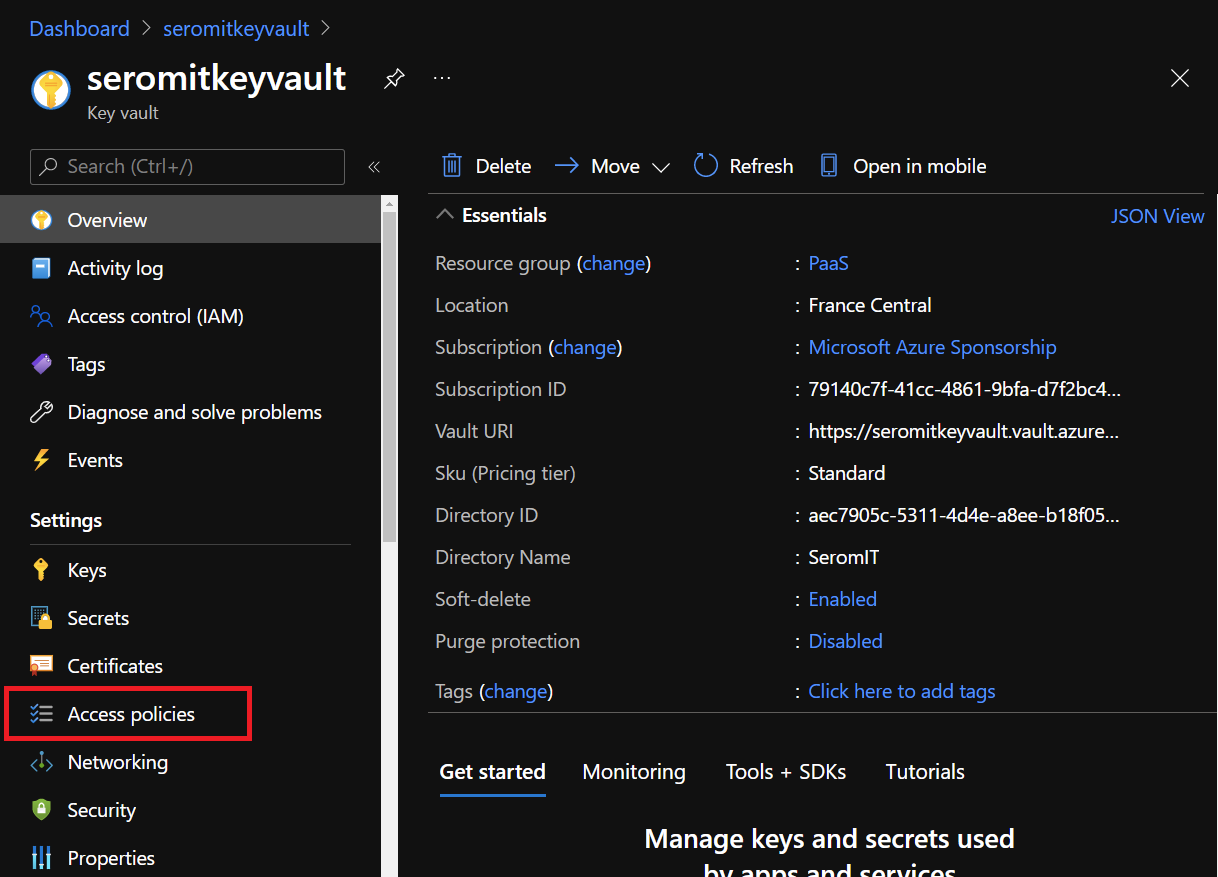
First, we need to set up Azure Key Vault to allow access to Azure Disk Encryption. To do so, navigate to your Azure Key Vault and select Access Policies.
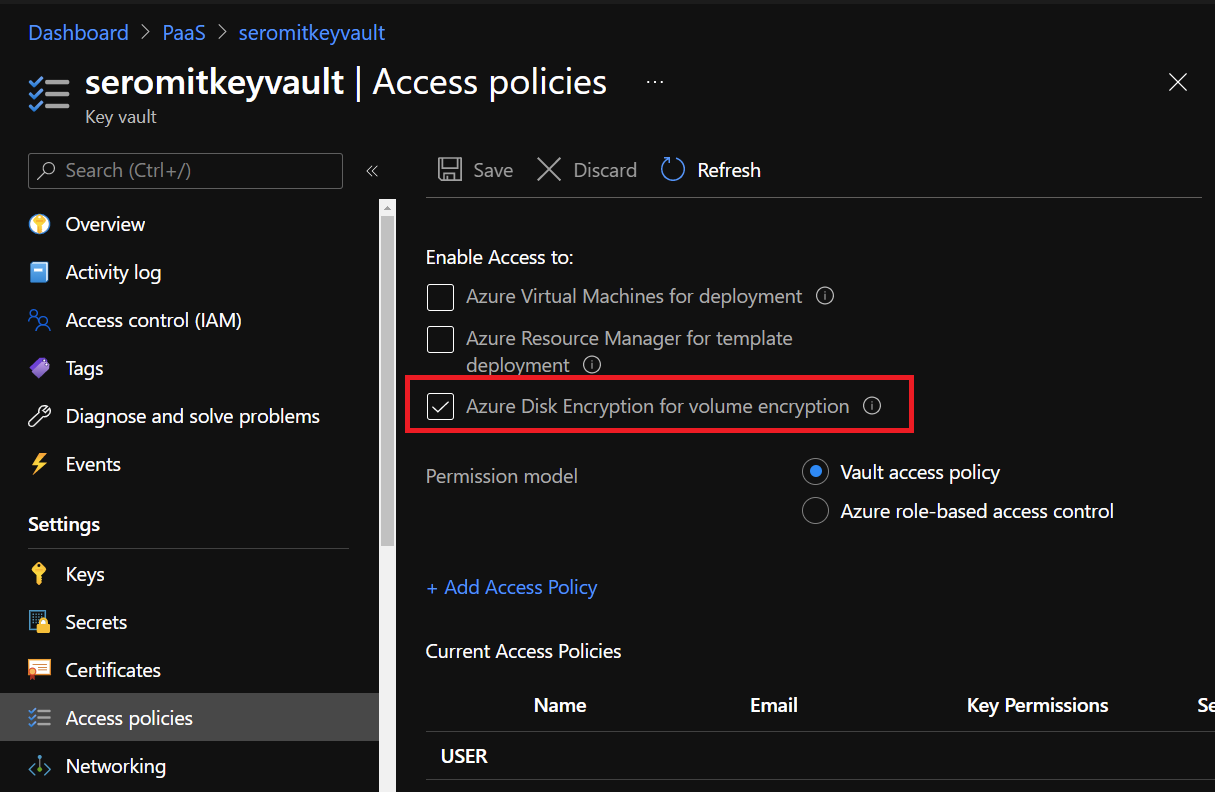
In Access Policies, be sure that Azure Disk Encryption for volume encryption is enabled.
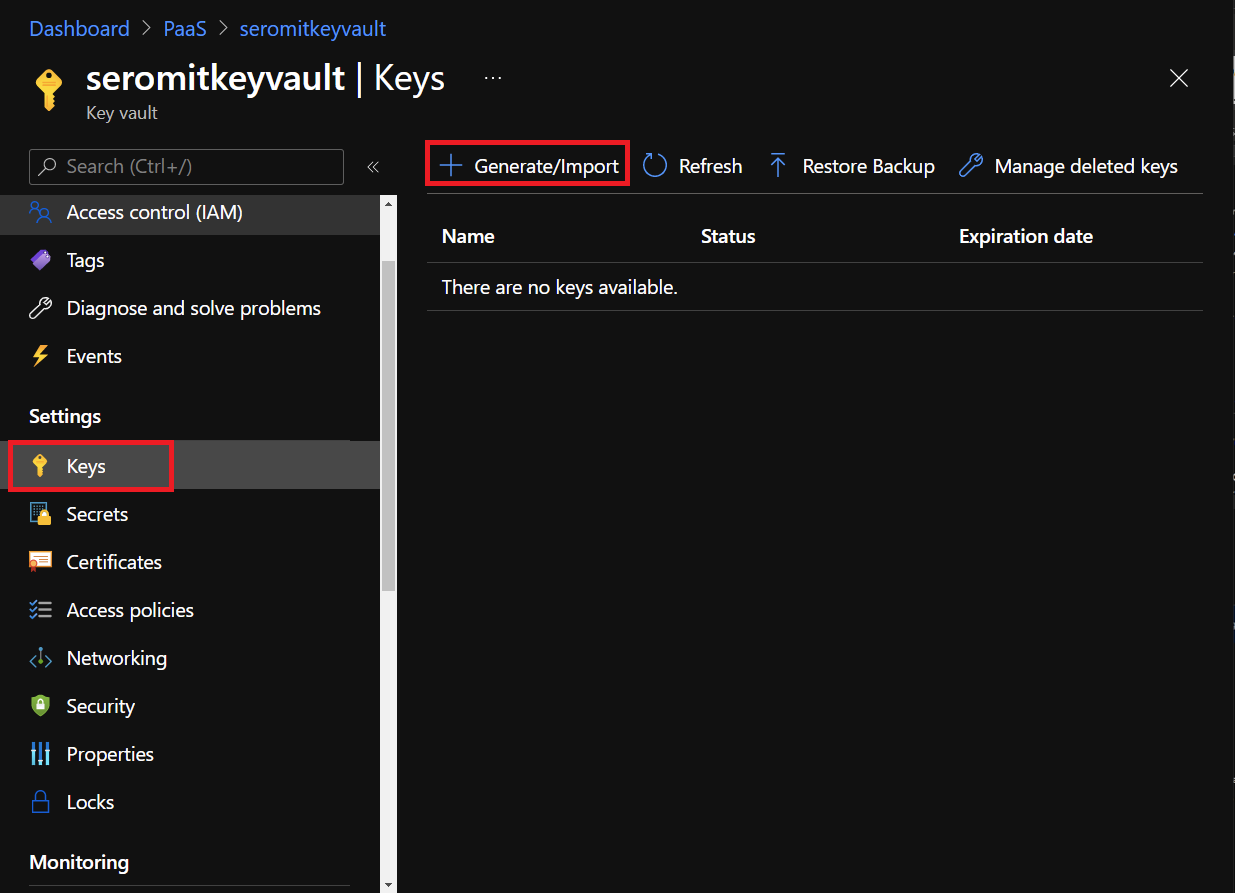
Next, we need a key. For that navigate to Keys in Azure Key Vault. Select Generate / Import.
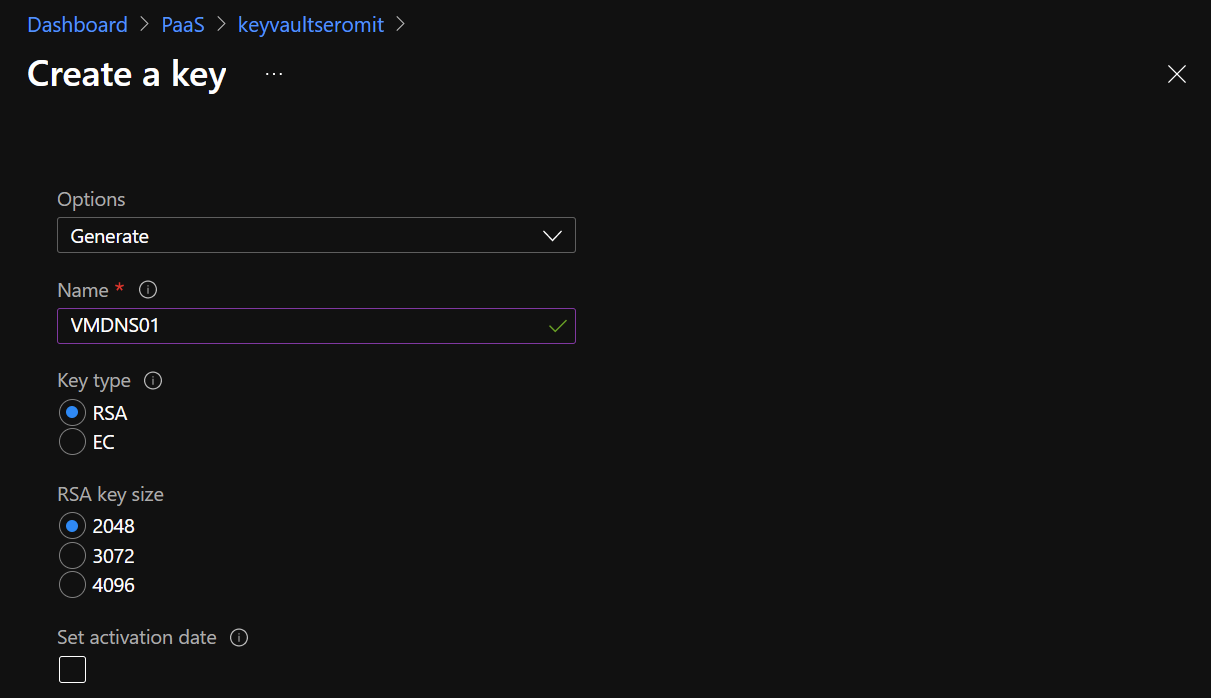
In this menu you have two options: either you generate a key that will be known by Microsoft, or you can import your own key that is known only by your corporation. For sensitive information, I recommend importing your own key.
For this example, I generate a key. In the documentation (Enable Azure Disk Encryption for Windows VMs – Azure Virtual Machines | Microsoft Docs), Microsoft indicates that the key should be RSA 2048 bits.
At this point, Azure Key Vault is configured for ADE.
Enable Azure Disk Encryption
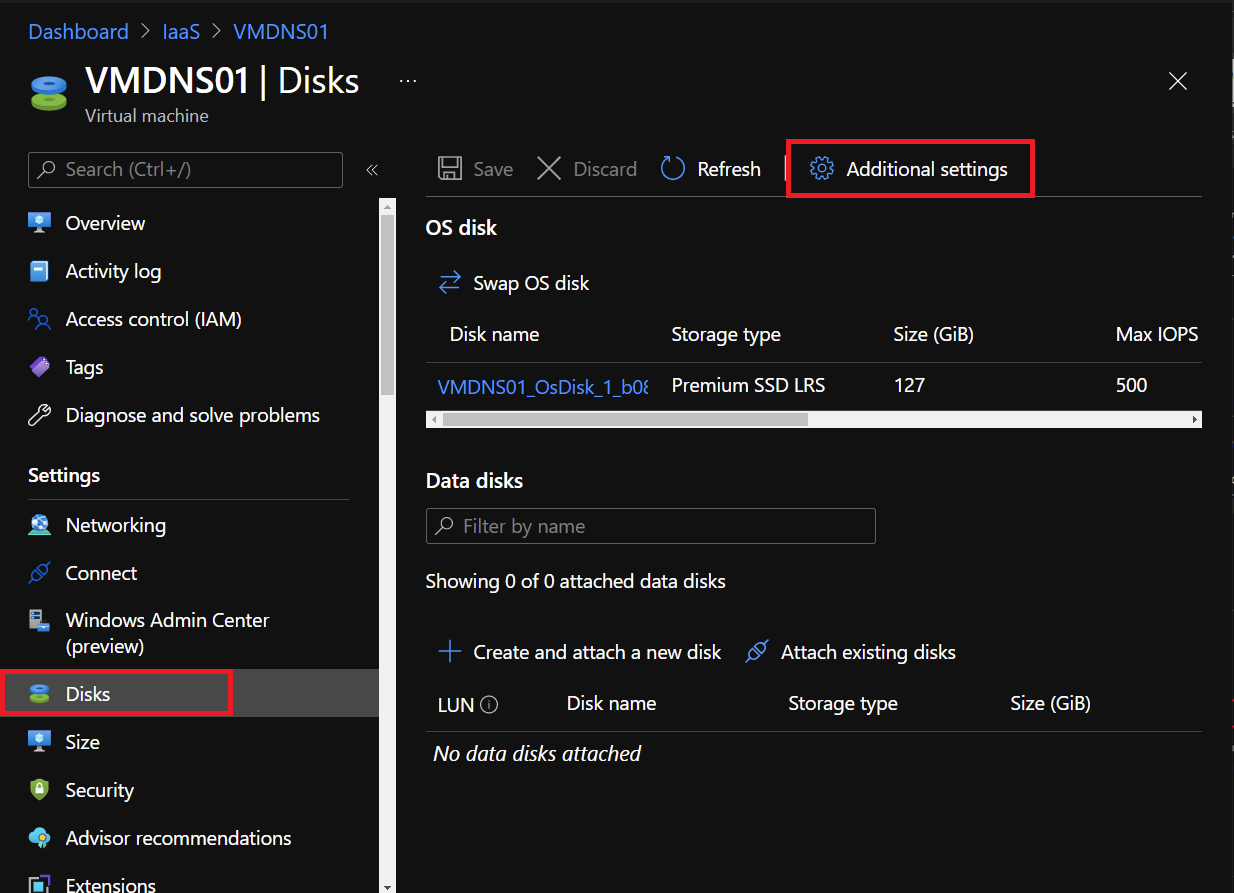
To enable Azure Disk Encryption, your Azure VM must be power on. Navigate to your Azure VM, then select Disks. Next select Additional settings.
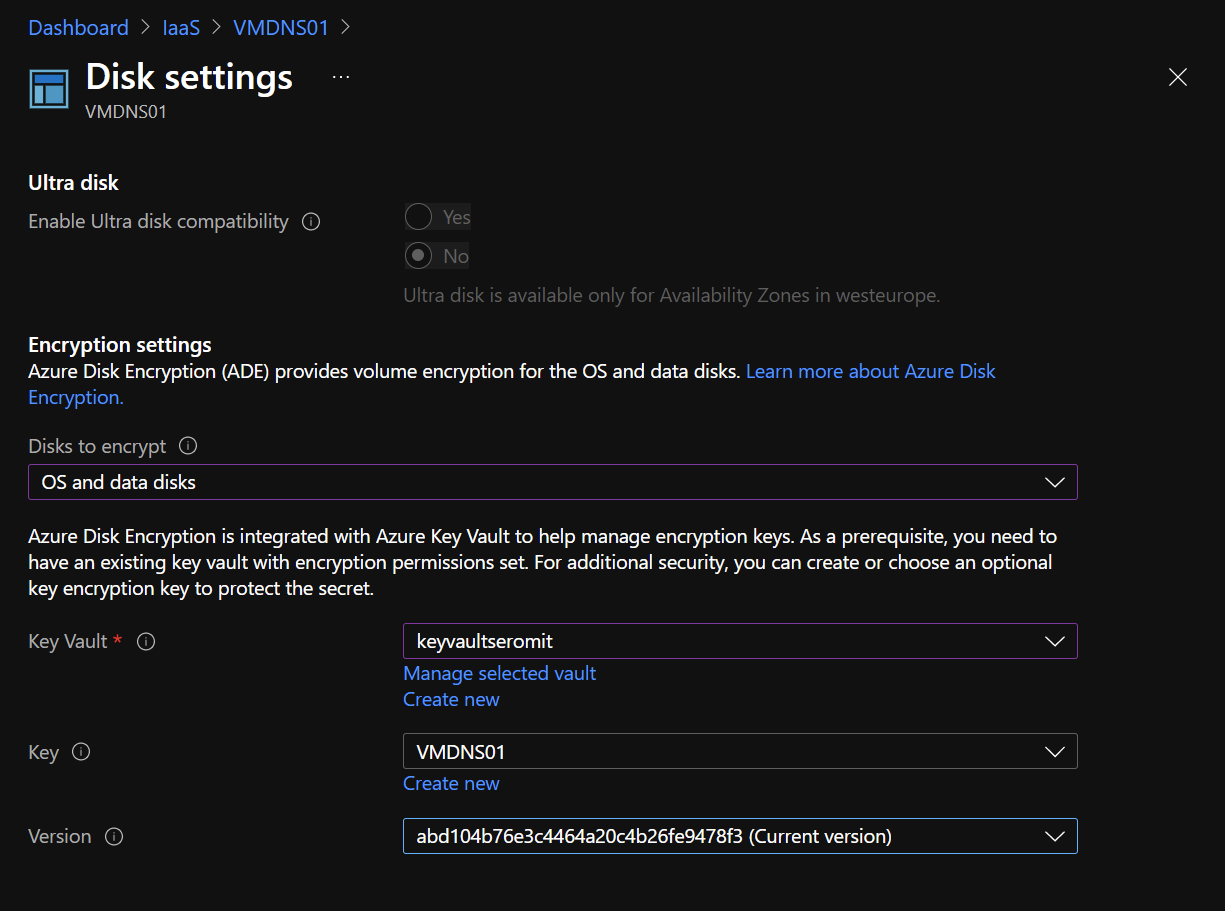
In additional settings, select the disk you want to encrypt and then select the key vault, the key and the version.
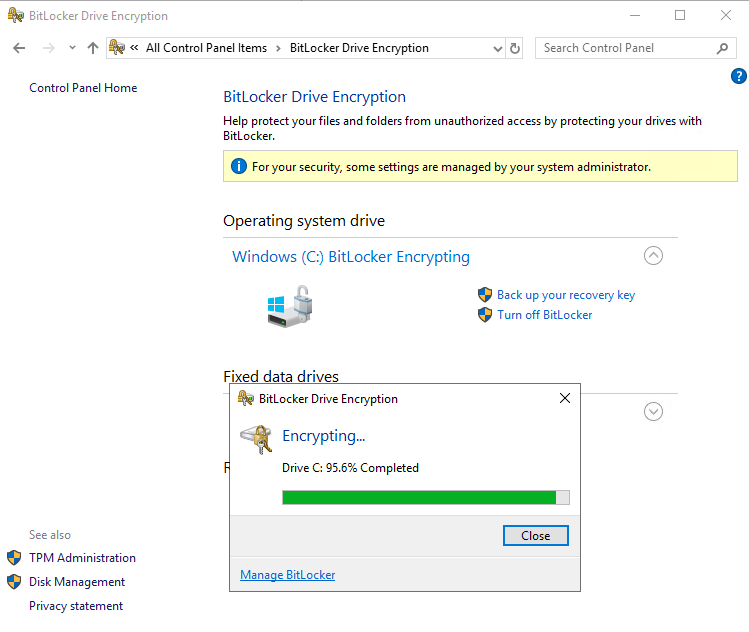
As soon as you click on OK in Azure Disk Encryption settings, Bitlocker is enabled in the Azure VM and the disk is encrypting.