There is no question that phishing is an enormous problem for enterprise organizations worldwide. Attackers use phishing attacks to lure unsuspecting end-users into handing over valuable, even privileged access accounts to a threat actor. Many attack vectors exist for phishing attacks, including emails, text messages, and other means.
When users hand over passwords, hackers can simply log in as the account in question without any need to compromise systems. One of the new enhancements found in the Windows 11 22H2 release is an enhanced Microsoft Defender SmartScreen, including phishing protection.
Overview of the new phishing protection in Windows 11 22H2
How has the Microsoft Defender SmartScreen solution been improved in Windows 11 22H2? The new release contains phishing protection baked into the operating system with the new Microsoft Defender SmartScreen. In addition, it provides additional safeguards that help notify end-users when there are imminent dangers to their passwords. It also provides tools and visibility for admins using the Microsoft Defender for Endpoint security portal to manage the organization’s endpoints.
Features and how it works
Microsoft has leveled up its game with the new phishing protection built into Windows 11 22H2 with Windows Defender SmartScreen. It has designed the new SmartScreen with the ability to look at the queues or signals generated from unsafe password usage or entry on Windows devices.
Whether a user is using a local account, Microsoft Account, or a traditional Active Directory account, the new SmartScreen helps protect passwords from phishing attacks in several ways.
- It immediately notifies users when they need to change their password in response to a potential risk of compromising their password.
- It automatically reports the unsafe or potentially compromised password to IT with the Microsoft Defender for Endpoint security portal. In addition, it allows IT to track the incident and follow up with users who may be at risk of a compromised password.
There are several really cool new features related to SmartScreen capabilities that it can notify and alert on:
- It can identify and protect corporate passwords entered on known phishing sites or apps
- Password reuse on apps or sites
- Passwords typed into Notepad, Wordpad, or Microsoft 365 apps will trigger alerts from SmartScreen
For admins who might be worried about the additional “noise” this may generate with end users and the potential helpdesk tickets that may be generated, the solution is configured by default in audit mode. In audit mode, users are not warned. Instead, admins will see the unsafe password usage in MDM and can analyze it from there.
The user experience workflow when phishing activity is detected
What do users see when SmartScreen notifications are enabled, and the solution is no longer in audit mode? SmartScreen will display messaging to end-users and prompt them to change their password if the user has entered a password on a known phishing site. Microsoft makes mention of users entering passwords into any Chromium browser. So, it sounds like the feature is only compatible with the Chromium engine.
When SmartScreen detects an unsafe connection, users will see the below dialog box, stating:
- This app made an unsafe connection that was reported to Microsoft for stealing passwords.
The user can click the button to Change my password, allowing them to immediately initiate a password change to protect their account from being used by an attacker. One of the excellent benefits of the solution is the centralized threat database Microsoft maintains, with the enormous amount of threat signals they detect daily from customers worldwide. In addition, Microsoft aggregates all the phishing sites and information, allowing all other businesses to benefit when new phishing sites and apps are identified.
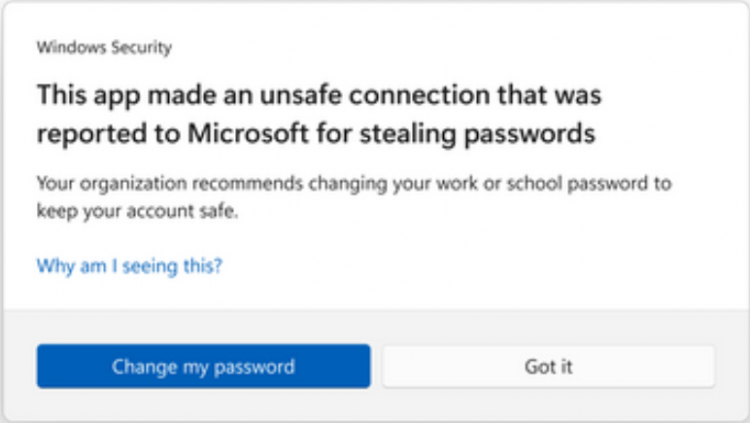 A warning dialog box is displayed to the end user noting an unsafe connection was made to a phishing site
A warning dialog box is displayed to the end user noting an unsafe connection was made to a phishing site
When the user clicks on the Change my password button, they are taken to the Windows password configuration screen, allowing them to change their password from this dialog easily.
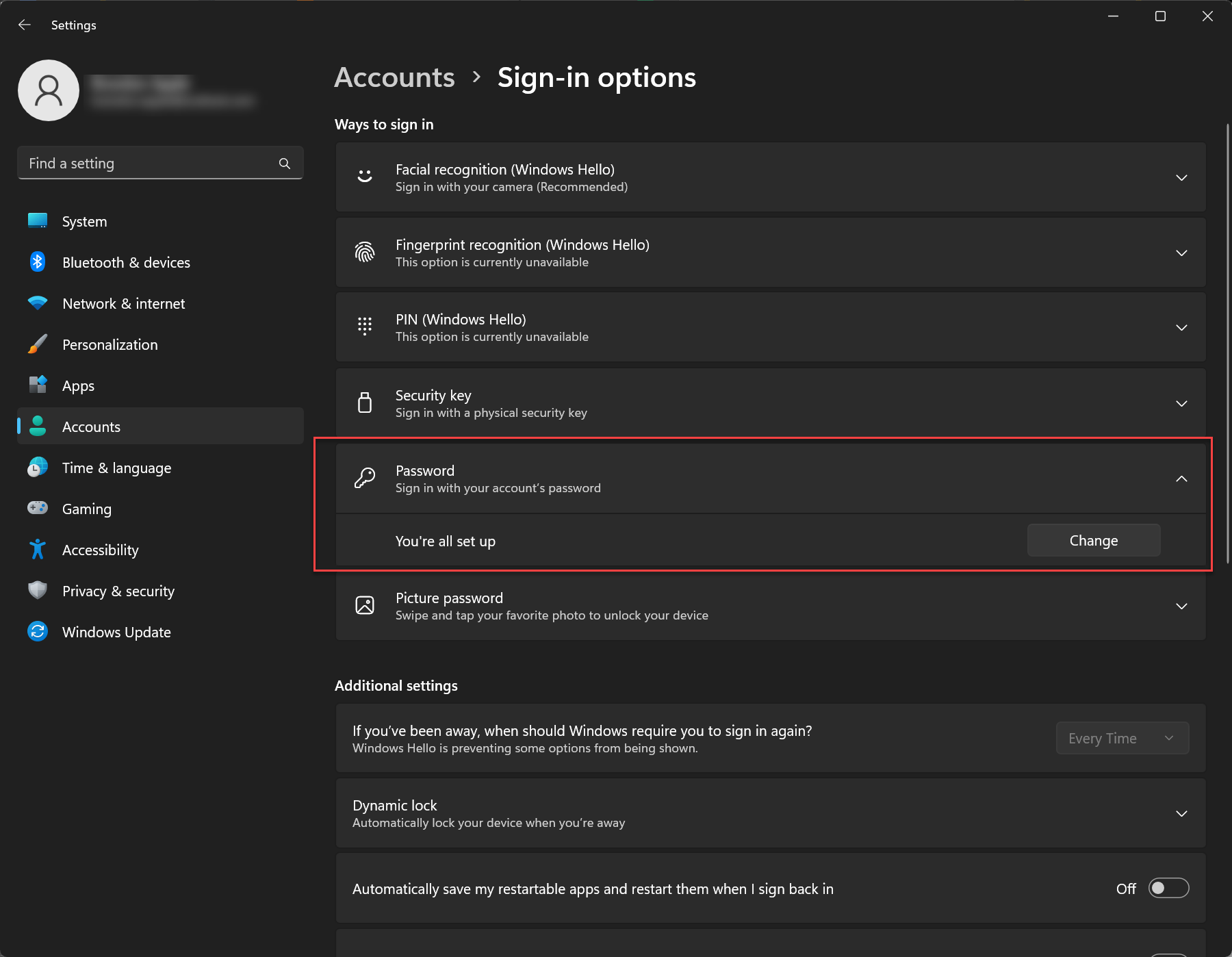 Users are taken to the Accounts screen in Windows Settings to change their password
Users are taken to the Accounts screen in Windows Settings to change their password
Organizations constantly fight the uphill battle to educate end users about phishing and other threats to their security and the overall security of business-critical data. While the new functionality as part of SmartScreen in Windows 11 22H2 release is not a replacement for cybersecurity training, it helps to bolster the visibility and awareness of end-users of a potentially unsafe action involving their password.
It also provides admins with robust tooling in the Windows Defender for Endpoint cloud dashboard to see potential phishing activities across the organization, helping them be proactive regarding remediation activities.
Protecting against password reuse
Another benefit of the new capabilities provided by SmartScreen in Windows 11 22H2 is it promotes better password hygiene and password activities. Password reuse is a common problem among enterprise users and introduces tremendous environmental risks. When passwords are reused, any compromised password essentially compromises the same password in every other environment in which it is used.
SmartScreen proactively alerts users to password reuse activities when it sees behaviors like using the same password on the Windows device used on websites or other applications. In addition, SmartScreen will display a warning that password reuse is a security risk.
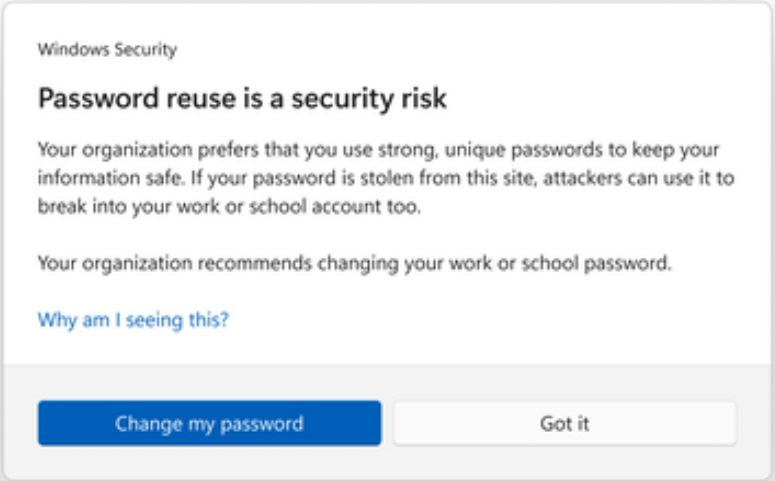 SmartScreen warning about password reuse
SmartScreen warning about password reuse
Saving or storing passwords in clear text documents and files
Another dangerous behavior is storing passwords in clear text in Notepad, Wordpad, Microsoft 365 apps, or any other file. Saving a password in clear text can lead another user or attacker to quickly view the password without having to decrypt it first. Users may not realize the danger of doing this, and having the additional guardrails provided by SmartScreen helps users better understand the risks to their passwords saved in this way.
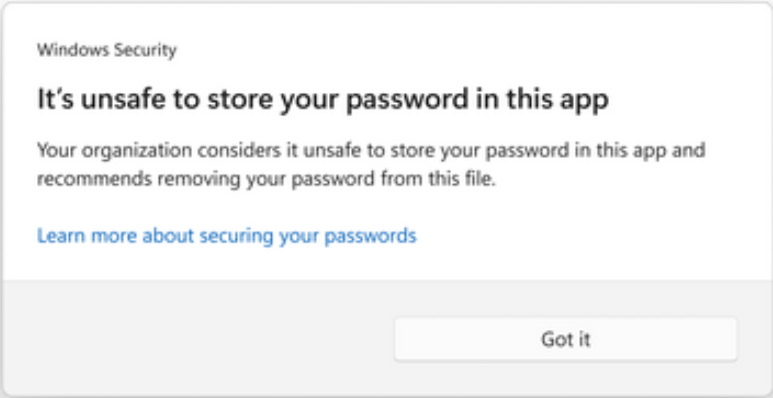 SmartScreen warning about unsafe password storage in clear text files
SmartScreen warning about unsafe password storage in clear text files
Enabling Windows Defender SmartScreen Enhanced Phishing Protection with Group Policy
Enabling Windows Defender SmartScreen Enhanced Phishing Protection with Group Policy is as easy as setting a few policy settings. Navigate to Computer Configuration > Administrative Templates > System > Windows Defender SmartScreen > Enhanced Phishing Protection. Note the following policy settings:
- Notify Malicious
- Notify Password Reuse
- Notify Unsafe App
- Service Enabled
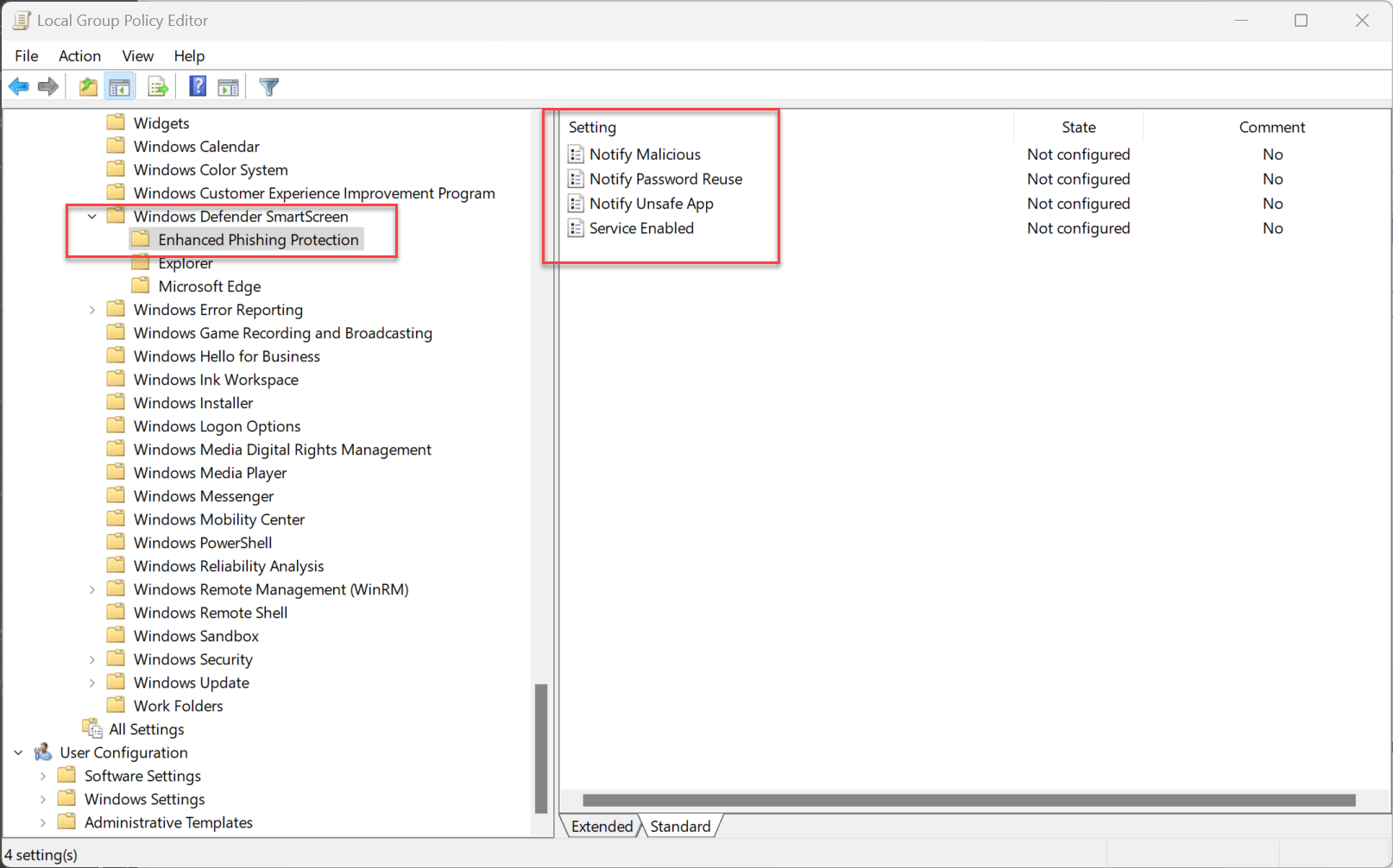 Enabling Enhanced Phishing Protection in Group Policy
Enabling Enhanced Phishing Protection in Group Policy
Microsoft Endpoint Manager Configuration Profile
Administrators can also configure and set the policy settings using Microsoft Endpoint Manager, using a configuration profile.
- Create profile > Windows 10 and later > Settings Catalog > Basics Configuration settings > Add settings
Find the 4 feature settings under SmartScreen. Then, in the dropdown for Enhanced Phishing Protection, select all. It will enable the 4 SmartScreen phishing protections for the configuration profile.
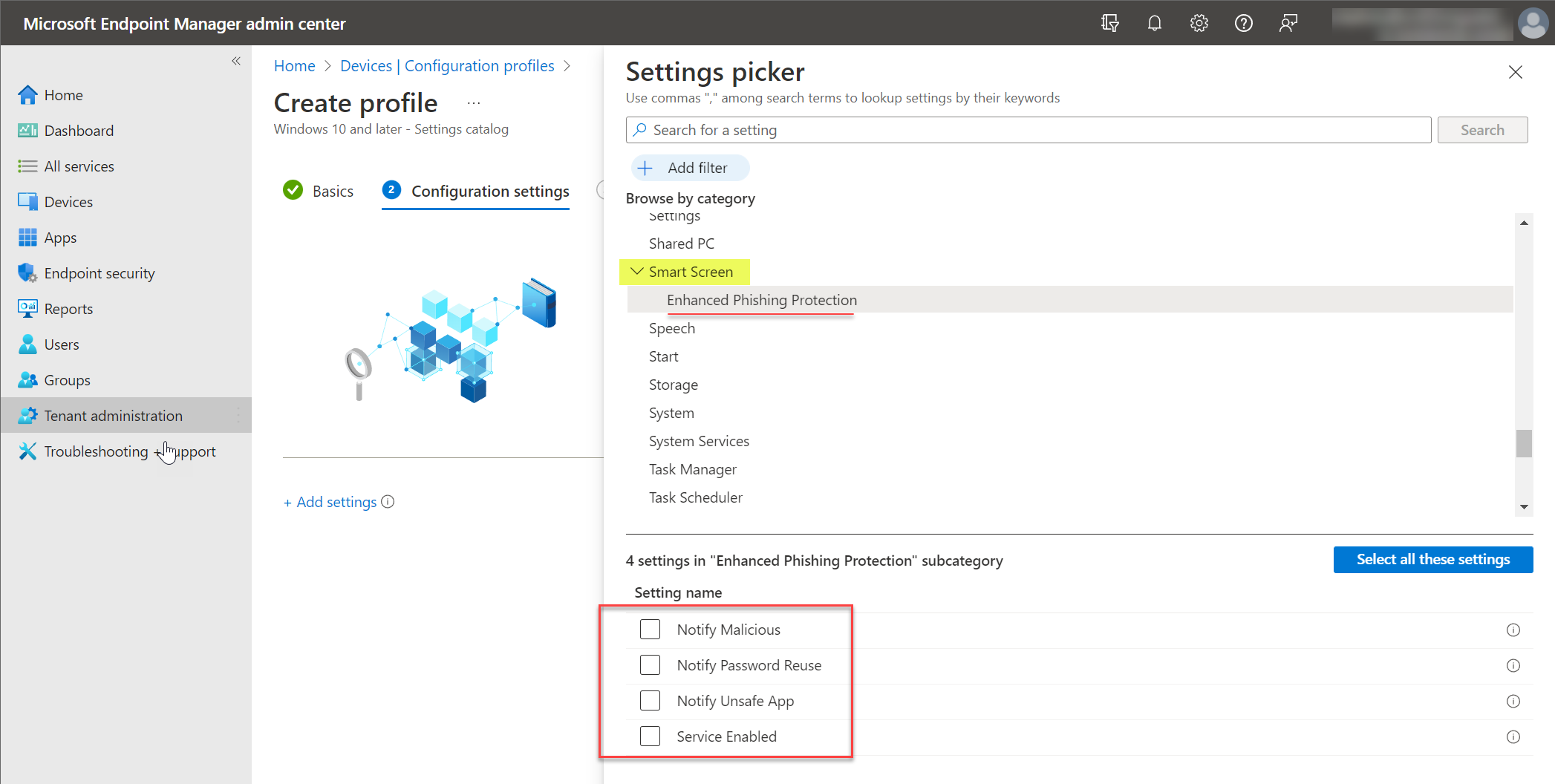 Enabling Enhanced Phishing Protection using a Microsoft Endpoint Manager configuration profile
Enabling Enhanced Phishing Protection using a Microsoft Endpoint Manager configuration profile
Wrapping Up
The new Microsoft Defender SmartScreen Enhanced Phishing Protection is a great new feature in Windows 11 that takes phishing protection in Windows to the next level. It helps organizations bolster their cybersecurity posture by adding proactive phishing protection, helping to alert users in real-time to phishing dangers.
The new feature is baked into Windows 11 and is easily enabled using either Group Policy or a configuration profile in Microsoft Endpoint Manager admin center. You can learn more about the enhanced phishing protection in Windows 11 here: Enhanced Phishing Protection in Microsoft Defender SmartScreen – Windows security | Microsoft Learn


