Introduction
Leakage of confidential business information can become a true disaster for any company. Therefore, data security is an issue of prime importance for most of companies. Organizing an IT infrastructure, administrators’ top question is how to warrant a secure storage to keep sensitive business information. In this article, I suggest having a closer look at a relatively recent method of ensuring data security – VMware virtual machines encryption that can become a good remedy against intruders for your organization.
Some theory to consider
VMware VM encryption is quite recent innovation that first emerged in VMware vSphere 6.5. VM encryption is implemented based on the AES-NI algorithm. Key management is organized according to the KMIP 1.1 standard. Encryption of VM objects takes place at the host level. Therefore, guest OS does not have access to encryption keys. Encrypted virtual machines move between ESXi hosts by means of an encrypted vMotion. With VMware VM encryption, encryptable and not-encryptable virtual machine data are as follows:
| Encryptable | Not-encryptable |
|---|---|
| VM files | Log files |
| Virtual disk files | VM configuration files |
| Host core dump files | Virtual disk descriptor files |
How VMware VM encryption works
To start with, let’s break down the three major VMware VM components:
- Key Management Server (KMS) is a server for managing keys. VMware uses KMS to generate and save keys. Later, it sends keys to vCenter. It is possible to use external systems that work following the KMIP standard as KMS. You can find VMware-certified KMS listed in this file.
- Key Encryption Key (KEK) is an encryption key generated and sent over to vCenter by KMS. vCenter, in its turn, sends KEK to ESXi hosts. KEK deploys the AES-256 encryption algorithm.
- Data Encryption Key (DEK) is an encryption key generated by an ESXi host. It is used for encryption/decryption of virtual machines. DEK deploys the XTS-AES-256 encryption algorithm.
The VM encryption follows a scheme like this:
- After a storage policy changes on a virtual machine, vCenter requests KEK from KMS
- After KEK is generated, KMS saves the key on its side and sends it over to vCenter for distribution
- Upon the KEK receipt from KMS, vCenter sends over the key to the ESXi host
- Upon the KEK receipt from vCenter, the ESXi host uses it to encrypt the DEK
- After encryption, the ESXi host saves the encrypted key at its memory cache The ESXi host is responsible for these functions
- Encryption of VM disks
- Sending encrypted guest data to encrypted virtual machines via network
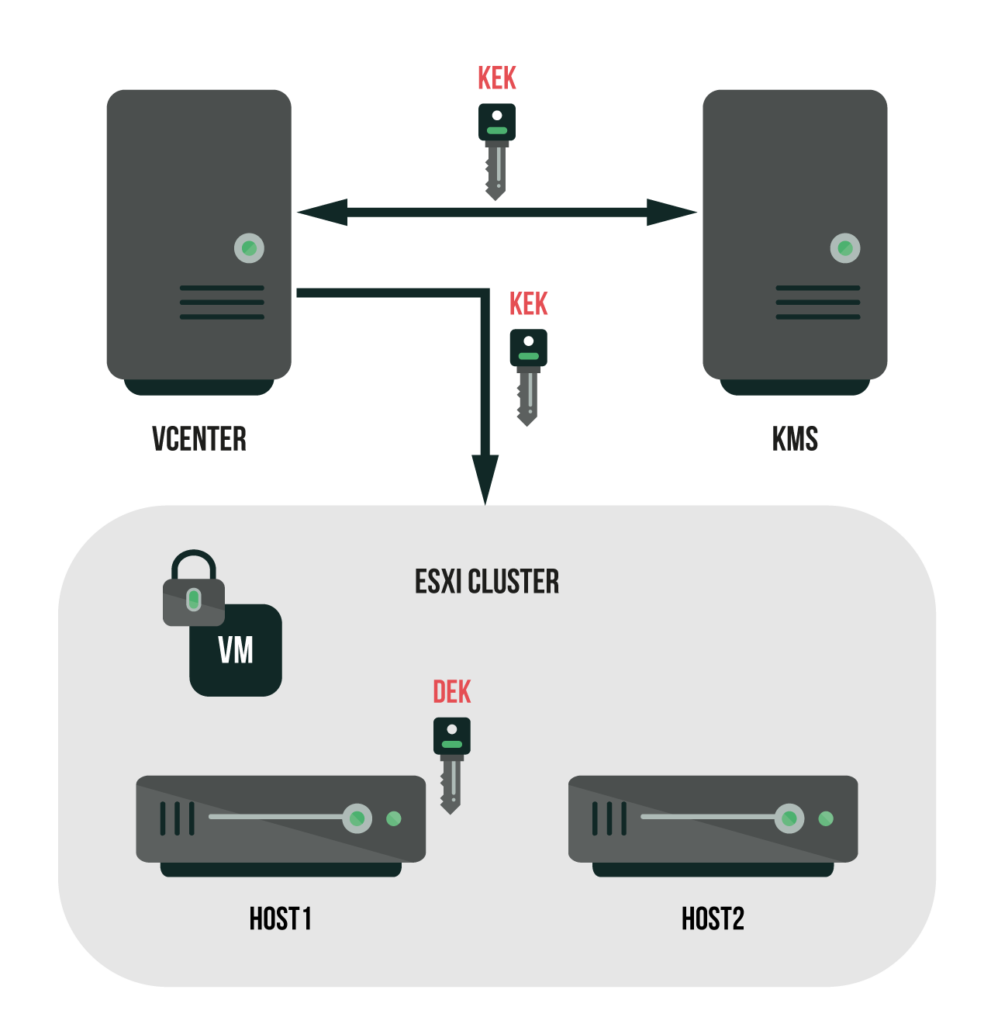 Important note: vCenter does not store and does not save KMS keys, it keeps the list of key identifiers only.
Important note: vCenter does not store and does not save KMS keys, it keeps the list of key identifiers only.
Note 2: It’s also good to know if your processor supports a set of AES-NI instructions, then encryption and decryption operations will be processed faster.
Some risk management
Now that we know how VM encryption works with VMware, let’s take a closer look at some scenarios you should keep in mind if things go wrong.
Scenario 1. What if the host has been rebooted?
The keys that have encrypted the host data will be deleted from the host memory after the reboot. However, the keys will be retrieved from KMS by the identifier and will be transferred to the host via vCenter as soon as the host reconnects to vCenter.
Scenario 2. What if vCenter is unavailable?
Virtual machines and hosts will work as usual because the encryption key is saved to the host memory cache. If vCenter is…“dead”, recover it from a backup. If you don’t have a backup, install a new vCenter and reconnect it to KMS.
Scenario 3. What if KMS server is unavailable?
Recover the KMS from a backup as soon as possible. KMS takes the first place by the accessibility priority after you opt for encryption in your infrastructure. Loss of KMS is a risk with the highest priority. It can result in a total loss of data and perhaps your whole business! More recommendations on what to consider when implementing encryption are available at the official VMware web-site.
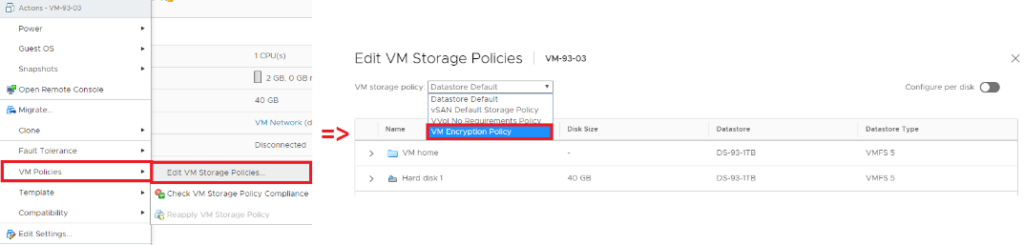
To turn on the VM encryption, change Storage Policy to Encryption Policy in the VM.
To turn off, change Storage Policy from Encryption Policy to any other.
My DOs and DON’Ts advice
| DO | DON’T |
|---|---|
| Do backups of KMS, vCenter and virtual machines. | Don’t encrypt vCenter Server Appliance. |
| Deploy KMS at a separate host. | Don’t edit VMX and VMDK files. These files include an encryption pattern. The changes might make virtual machine recovery impossible. |
| Build a KMS cluster from 2-3 hosts. | |
| Install KMS to a public cloud, e.g. Amazon or Azure, for the sake of disaster resiliency. |
Conclusion
Data has become too valuable as an asset for the business to ever ignore its security. To date, encryption at a virtual level might be the most reliable way to store and manage your important information. Here, I’ve given a deeper insight of what VMware VM encryption is, how it works as well as what to consider to mitigate your risks. Hope, I’ve inspired you to use encryption as a method of data security.