A couple month ago, Ubiquiti has released a new all-in-one hardware called Unifi Dream Machine Pro (UDM-Pro). UDM-Pro is great because it handles several features such as router, firewall, switch, SDN or camera management. When I bought UDM-PRO I removed 3 VMs and two equipments.
UDM-PRO embeds a Unifi Controller which is a piece of software that enables to manage several Ubiquiti hardware. It’s an SDN. From Unifi Controller you can handle your whole Ubiquiti network such as switches, firewall and obviously VPN. When I bought UDM-PRO, I wanted to establish a Site-to-Site VPN with Azure for my lab. Thanks to that, I can try hybrid scenarios between On-Premises and Azure. In this topic, we will see how I have established this VPN.
Requirements
To follow this topic, you need an Azure subscription with the following resources deployed:
- A virtual network
- A local network gateway
- A virtual network Gateway
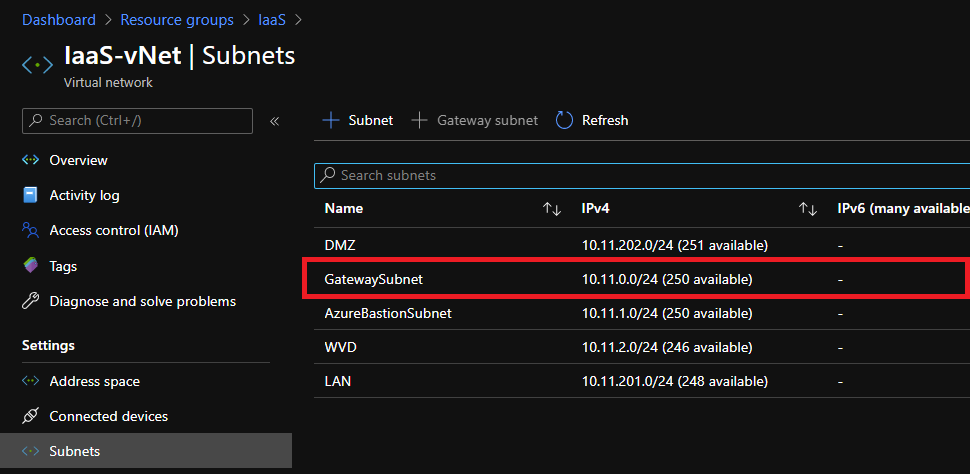
Make sure that a gateway subnet is created in your virtual network:
Configure the local network gateway
The local network gateway is used to define the On-Premises network configuration. You need your Public IP and the subnet you want to route in Azure:
In address space field, I specify each subnet I want to route to Azure. Some network such as management doesn’t need to be routed to Azure.
Configure the virtual network gateway
The virtual network gateway is a software gateway deployed in your Azure tenant. Your On-Premises gateway will establish a VPN with the virtual network gateway. When you create your virtual network gateway you just have to choose the SKU. Microsoft gives detail about difference between SKU here.
For the purpose of my lab, I chose the VpnGw1 SKU. You can also configure BGP to spread route automatically between On-Premises and Azure.
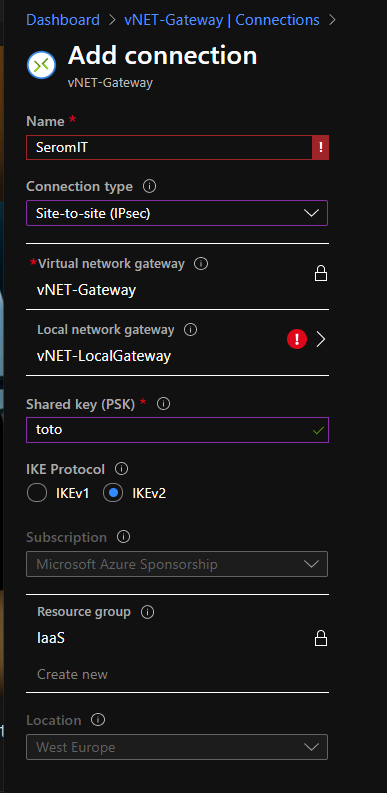
Once the virtual network gateway is ready, you need to create a Connections. To create a connection, just navigate to Connections and click on Add.
You need to specify a name and shared key to create a connection. Moreover, select the right local network gateway to establish the Site-to-Site VPN between your On-Premises and Azure.
Configure the UDM-PRO
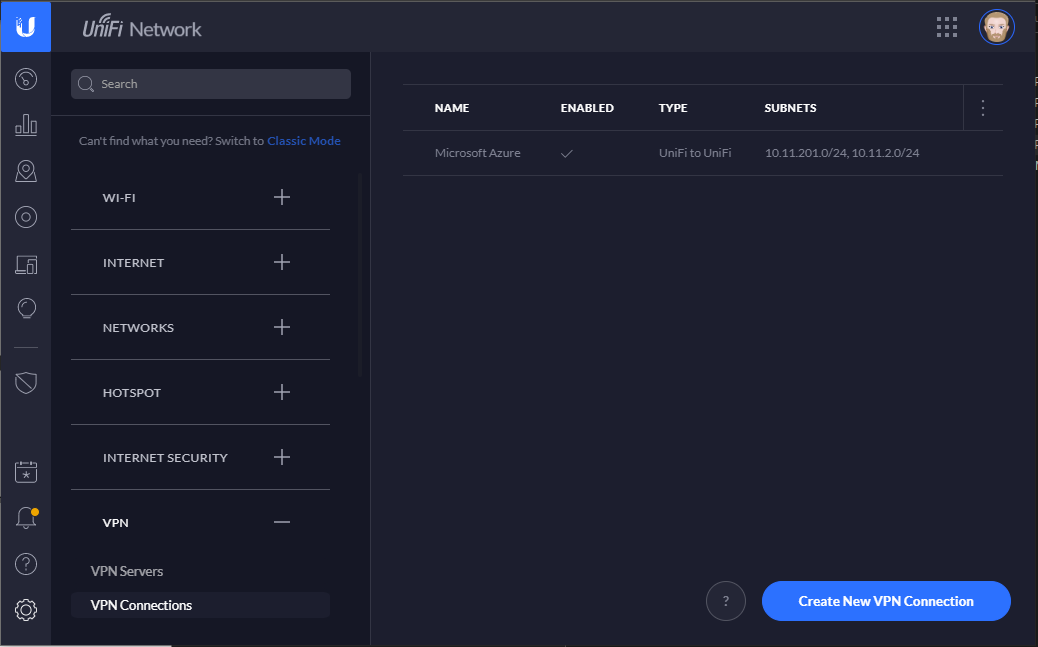
Connect to the Unifi Controller. It should be your UDM-PRO IP or name. Open the settings and navigate to VPN connections. Click on Create New VPN Connection.
Even if it’s not a Unifi to Unifi VPN, select Create Unifi to Unifi VPN. It’s a UI glitch:
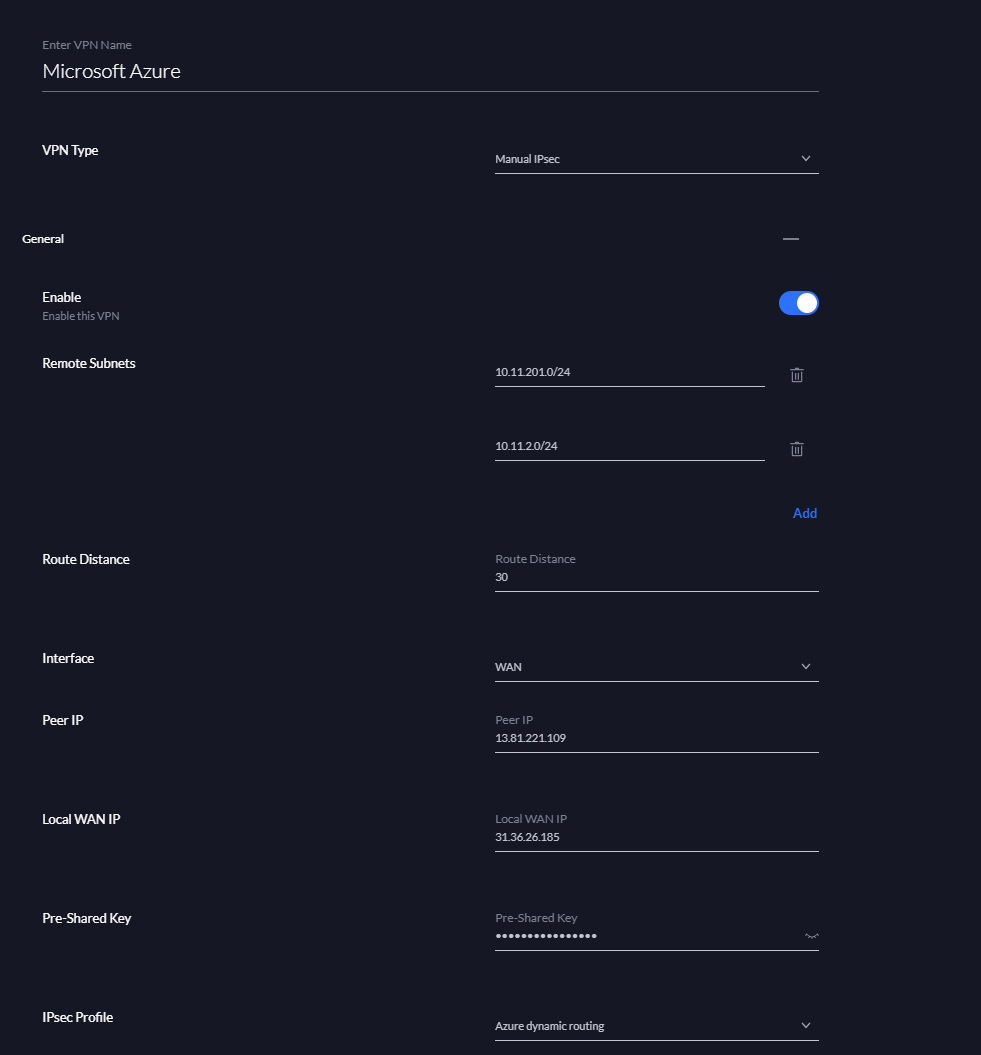
Then select Manual IPSec and specify the following configuration:
- Remote Subnet: Azure subnet that will be routed On-Premises
- Route Distance: number of hops allowed
- Interface: specify the WAN interface
- Peer IP: Public IP address of the virtual network gateway (Azure)
- Local WAN IP: Your public IP address (On-Premises)
- Pre-Shared Key: Copy past the one you have specified in the Connections creation wizard (Azure)
- IPsec Profile: Azure Dynamic routing
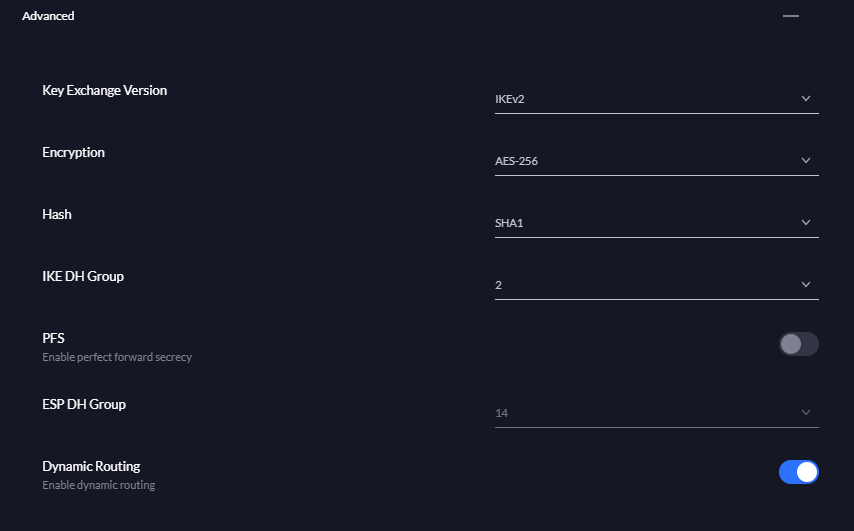
By selecting Azure Dynamic routing, the advanced settings should be set automatically as below:
Test of the VPN connection
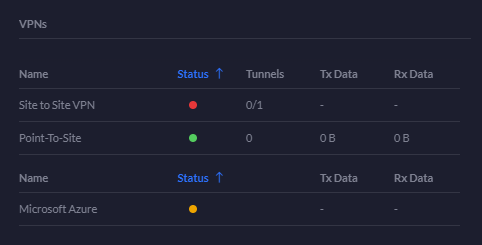
Do not look at the Unifi Controller to check if the VPN is established. In my lab it’s working but the Unifi Controller dashboard indicates the Site-to-Site VPN down:
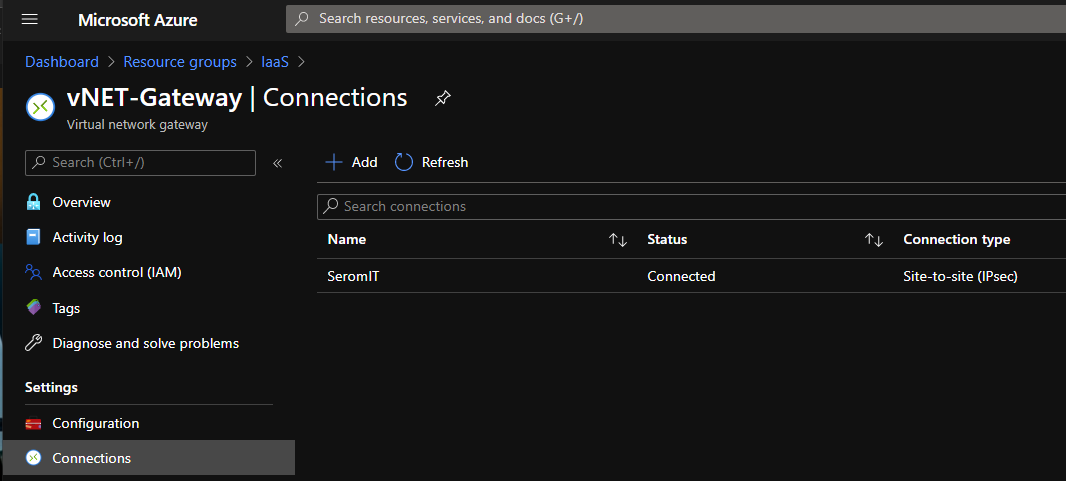
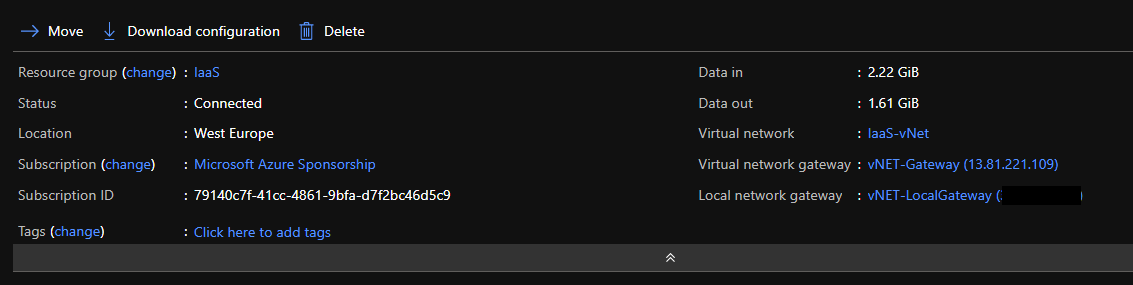
To check if the VPN is established, open the Azure portal, and look at the Connections:
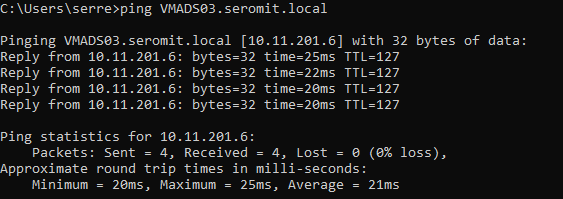
You can also make a ping from an On-Premises server to an Azure service: