Before starting this article, let me wish you a happy end of the year and wish you all the best for 2023.
One of the big problems for many companies is access to logs. If you have one log analytics for all of your resources in Azure, this article is for you
In this article, I will send all logs to one log analytics workspace. I have logs for different types, like Azure Application Gateway, Azure Virtual Desktop, App Service Plan, App Service, Storages, etc.
Before starting, we will create 4 Custom RBAC roles, to give these permissions:
- AVD Log Reader
- Storage Log Reader
- App Service Log Reader
- Application Gateway Log Reader
AVD Log Reader:
{
"properties": {
"roleName": "AVD Log Reader",
"description": "",
"assignableScopes": [
"/subscriptions/your_subscription_id"
],
"permissions": [
{
"actions": [
"Microsoft.OperationalInsights/workspaces/query/WVDAgentHealthStatus/read",
"Microsoft.OperationalInsights/workspaces/query/WVDCheckpoints/read",
"Microsoft.OperationalInsights/workspaces/query/WVDConnections/read",
"Microsoft.OperationalInsights/workspaces/query/WVDErrors/read",
"Microsoft.OperationalInsights/workspaces/query/WVDFeeds/read",
"Microsoft.OperationalInsights/workspaces/query/WVDHostRegistrations/read",
"Microsoft.OperationalInsights/workspaces/query/WVDManagement/read",
"Microsoft.OperationalInsights/workspaces/read",
"Microsoft.OperationalInsights/workspaces/query/WVDConnectionGraphicsDataPreview/read",
"Microsoft.OperationalInsights/workspaces/query/WVDConnectionNetworkData/read",
"Microsoft.OperationalInsights/workspaces/query/WVDSessionHostManagement/read",
"Microsoft.OperationalInsights/workspaces/query/read",
"Microsoft.OperationalInsights/workspaces/query/Tables.Custom/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}Storage Log Reader:
{
"properties": {
"roleName": "Storage Log Reader",
"description": "",
"assignableScopes": [
"/subscriptions/your_subscription_id"
],
"permissions": [
{
"actions": [
"Microsoft.OperationalInsights/workspaces/read",
"Microsoft.OperationalInsights/workspaces/query/read",
"Microsoft.OperationalInsights/workspaces/query/Tables.Custom/read",
"Microsoft.OperationalInsights/workspaces/query/StorageBlobLogs/read",
"Microsoft.OperationalInsights/workspaces/query/StorageTableLogs/read",
"Microsoft.OperationalInsights/workspaces/query/StorageQueueLogs/read",
"Microsoft.OperationalInsights/workspaces/query/StorageFileLogs/read",
"Microsoft.OperationalInsights/workspaces/query/StorageCacheWarningEvents/read",
"Microsoft.OperationalInsights/workspaces/query/StorageCacheUpgradeEvents/read",
"Microsoft.OperationalInsights/workspaces/query/StorageCacheOperationEvents/read",
"Microsoft.OperationalInsights/workspaces/query/StorageBlobLogs/read",
"Microsoft.OperationalInsights/workspaces/query/StorageAntimalwareScanResults/read" ],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}App Service Log Reader:
{
"properties": {
"roleName": "App Service Log Reader",
"description": "",
"assignableScopes": [
"/subscriptions/your_subscription_id"
],
"permissions": [
{
"actions": [
"Microsoft.OperationalInsights/workspaces/read",
"Microsoft.OperationalInsights/workspaces/query/Tables.Custom/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceAntivirusScanAuditLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceAppLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceAuditLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceConsoleLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceEnvironmentPlatformLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceFileAuditLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceHTTPLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceIPSecAuditLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServicePlatformLogs/read",
"Microsoft.OperationalInsights/workspaces/query/AppServiceServerlessSecurityPluginData/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}Application Gateway Log Reader:
{
"properties": {
"roleName": "App Service Log Reader",
"description": "",
"assignableScopes": [
"/subscriptions/your_subscription_id"
],
"permissions": [
{
"actions": [
"Microsoft.OperationalInsights/workspaces/query/AzureDiagnostics/read",
"Microsoft.OperationalInsights/workspaces/read",
"Microsoft.OperationalInsights/workspaces/query/Tables.Custom/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
After that, you can apply permissions at resource level or at the subscription level, depending of your needs.
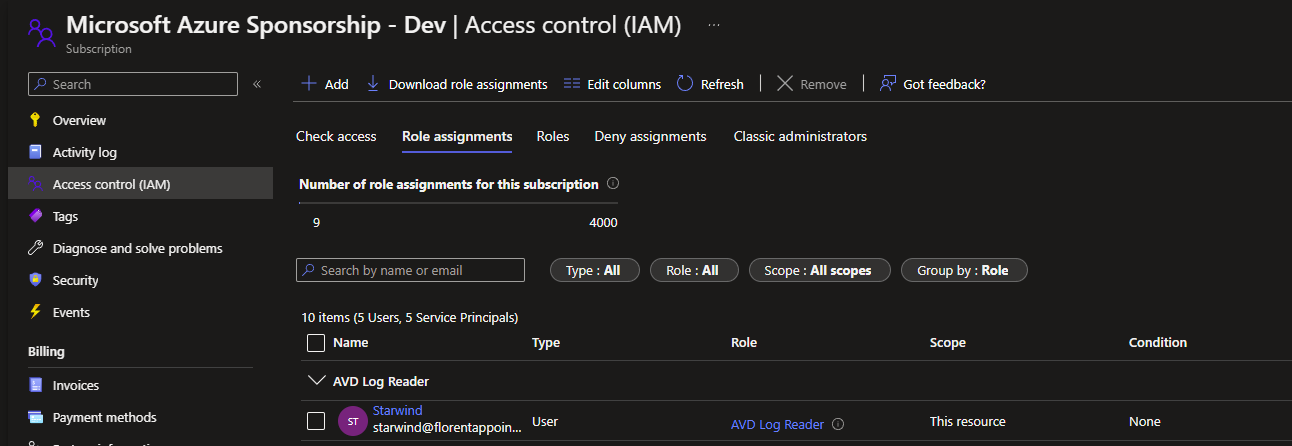
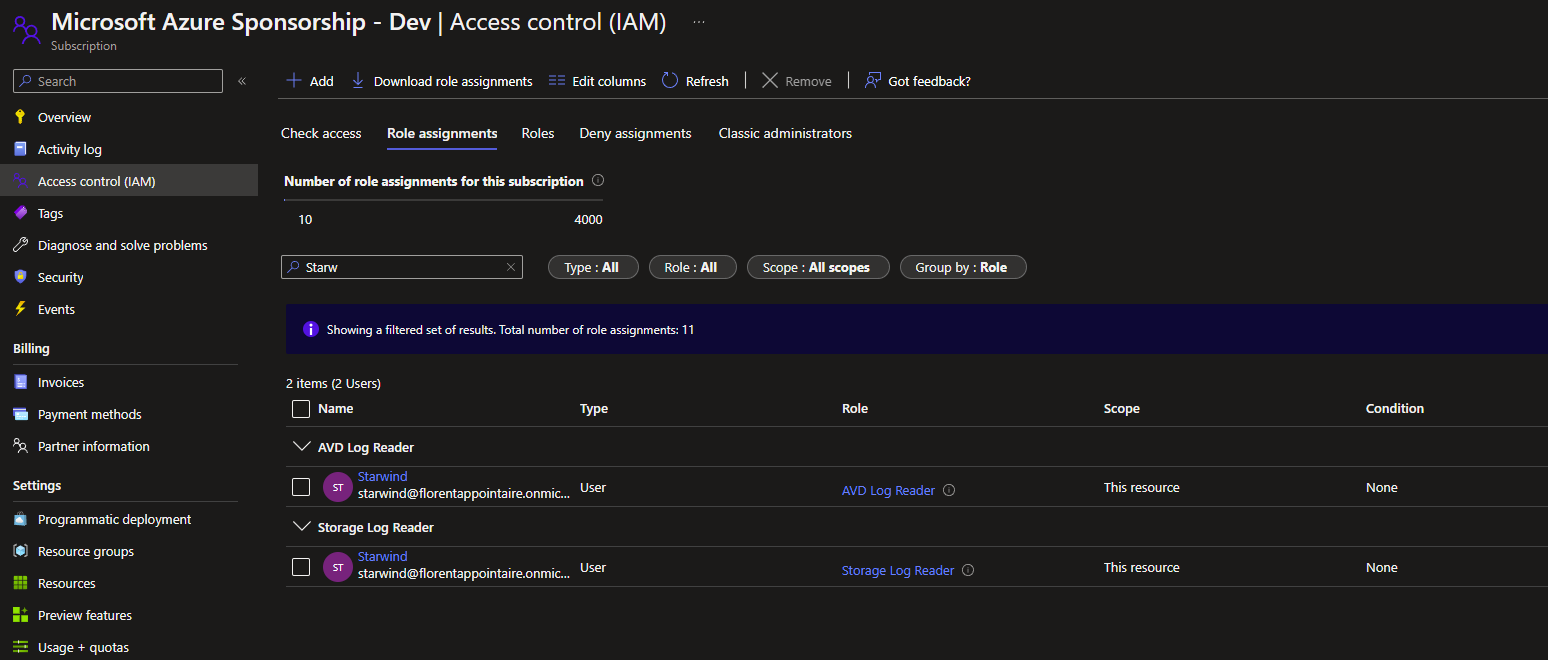
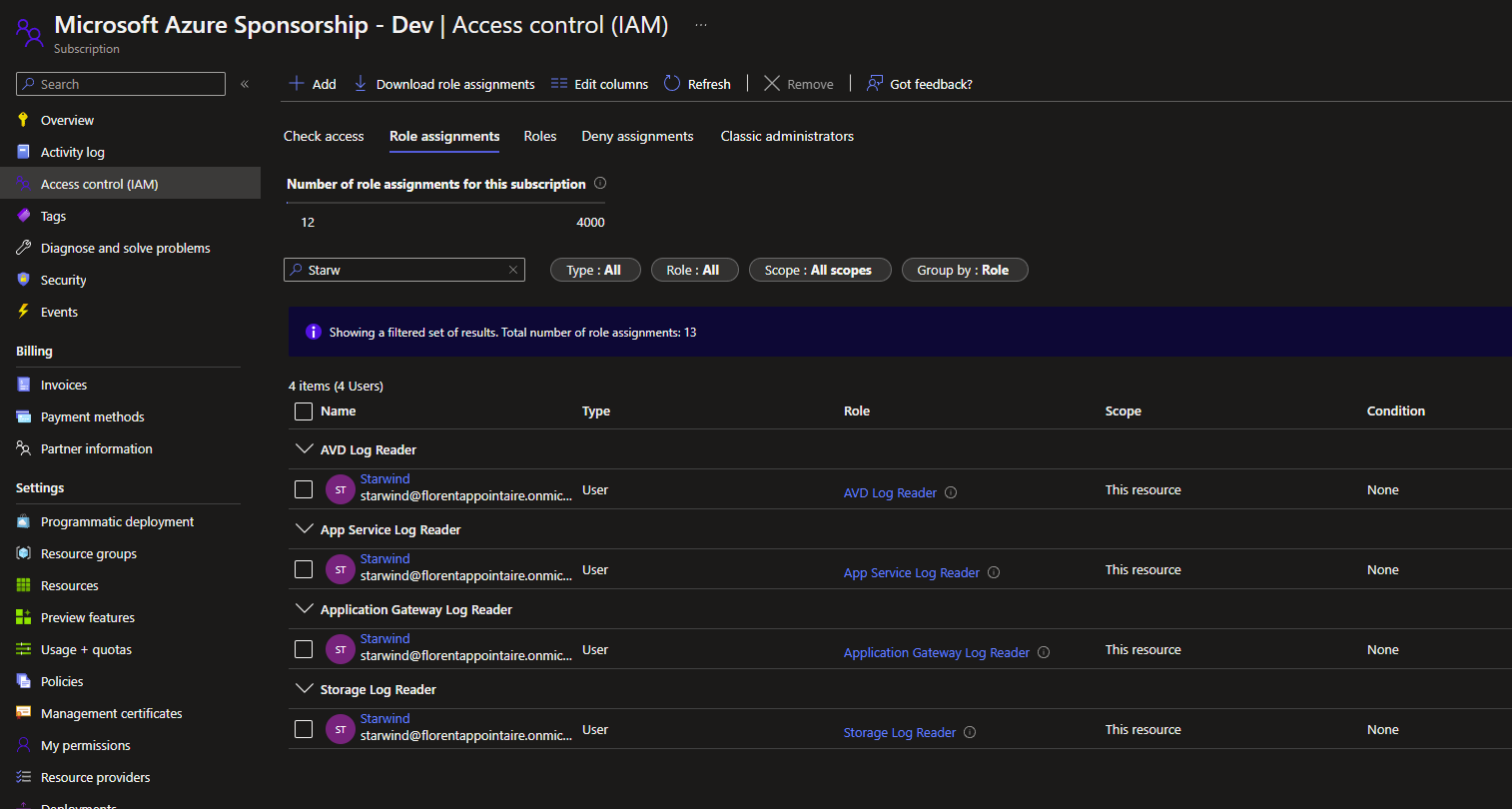
For example, for the AVD Log Reader, I applied it at the subscription level:
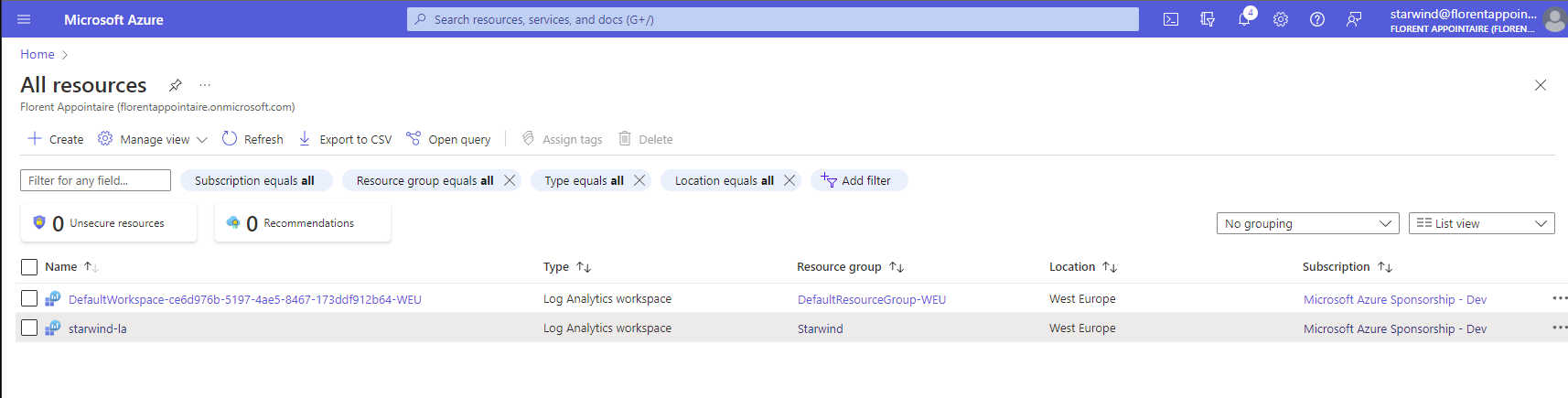
If I logged in with this user, I can only see the log analytics resource:
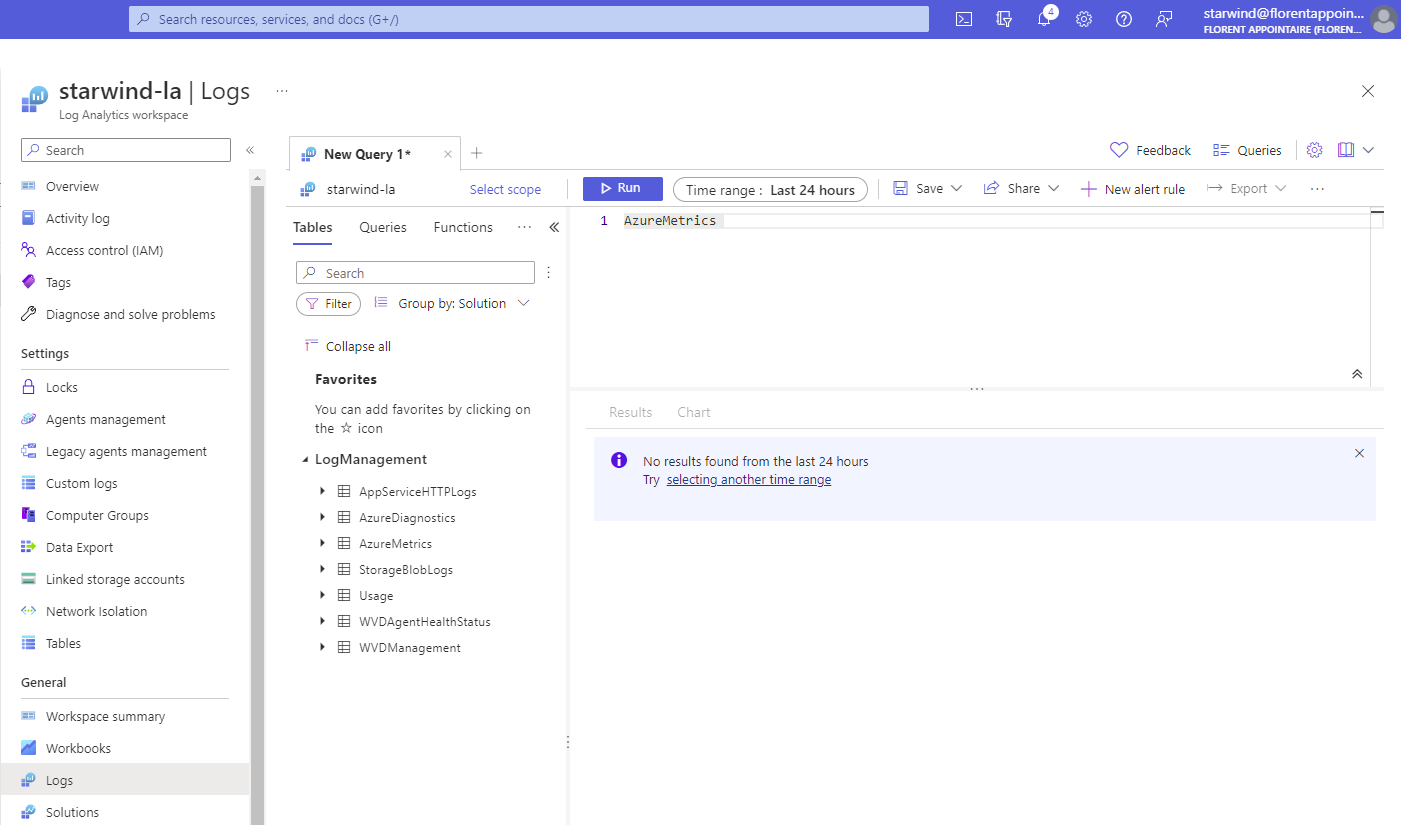
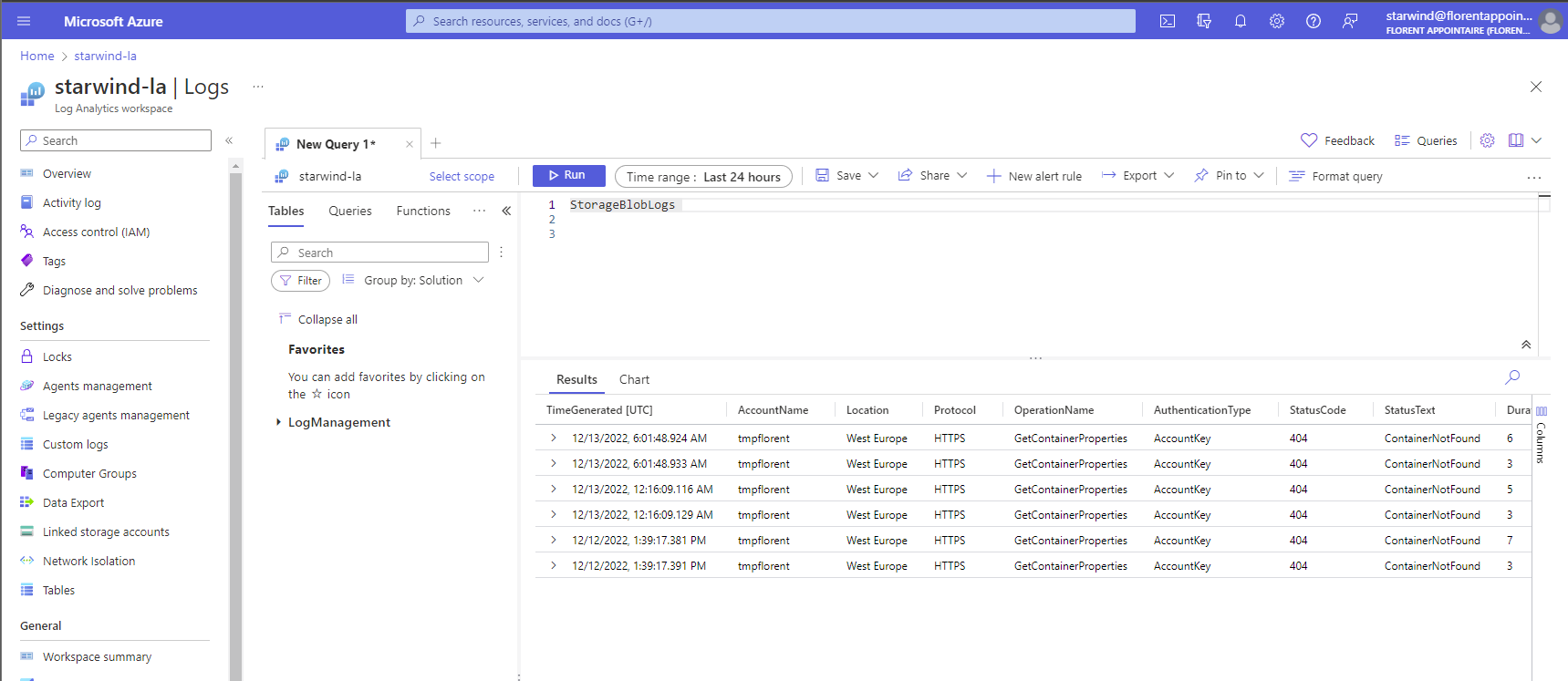
If I try to browse logs I should not have access, I have no results:
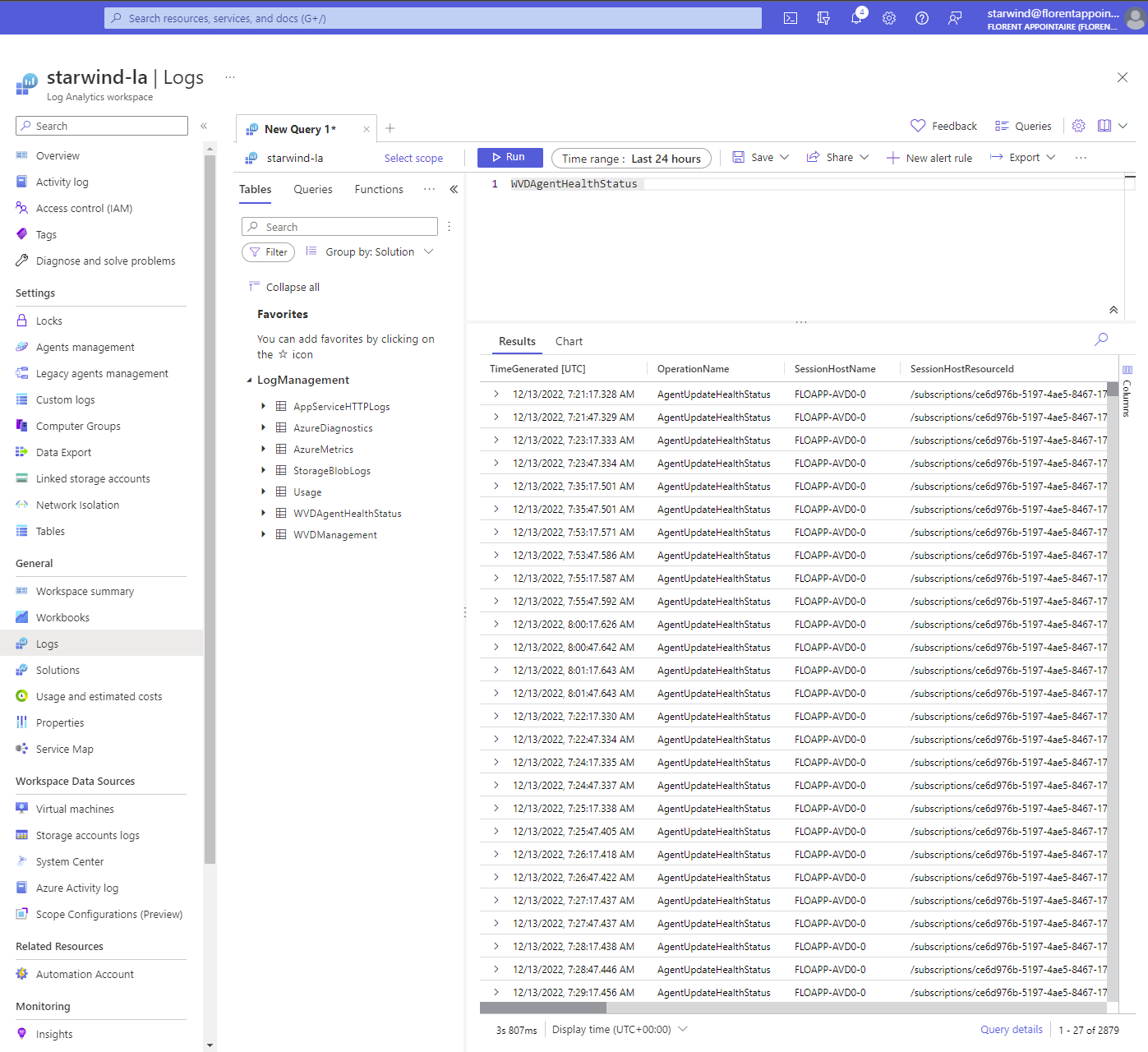
But for logs of AVD, I can access them, because I have the rights:
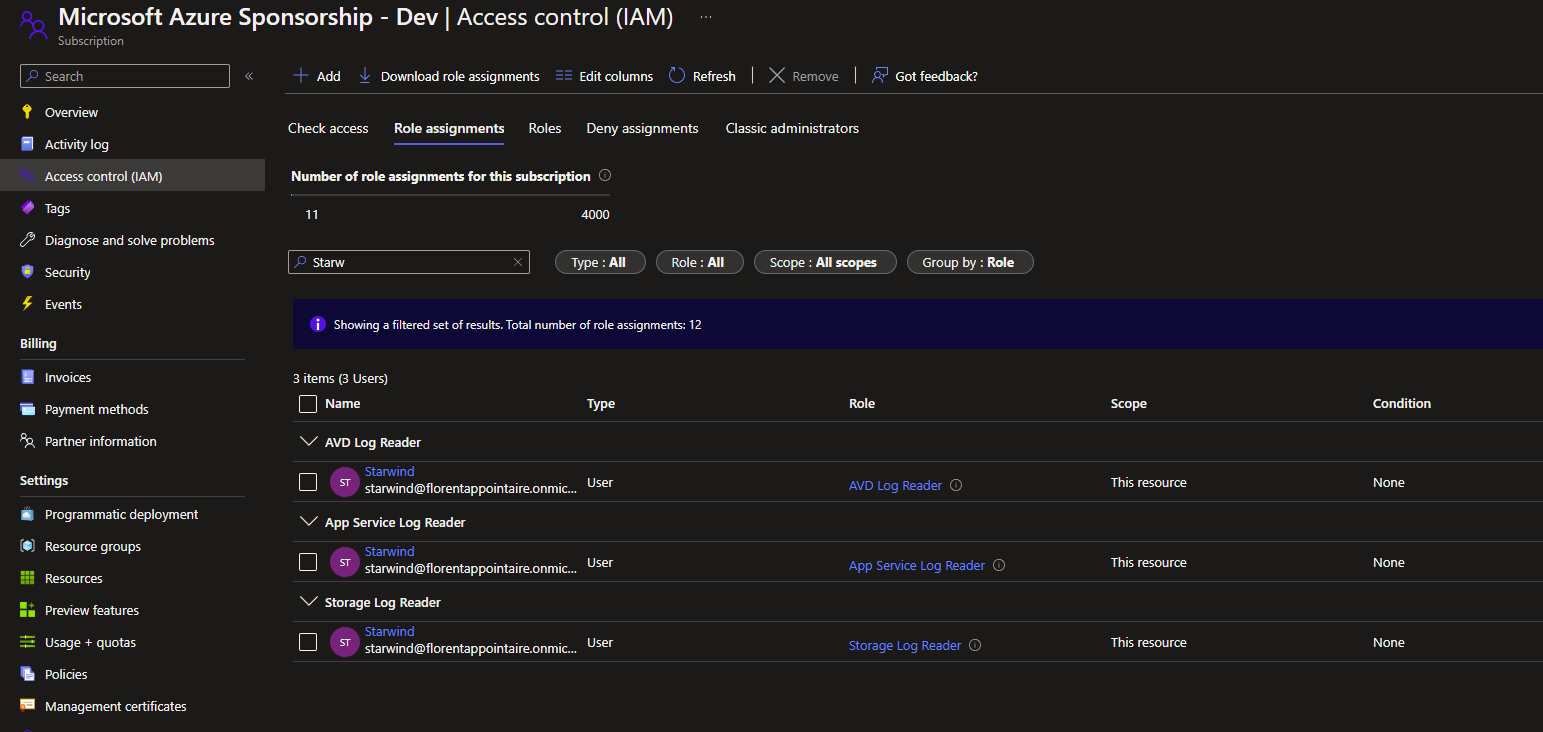
After adding the permissions for the Storage logs, I can now access them:
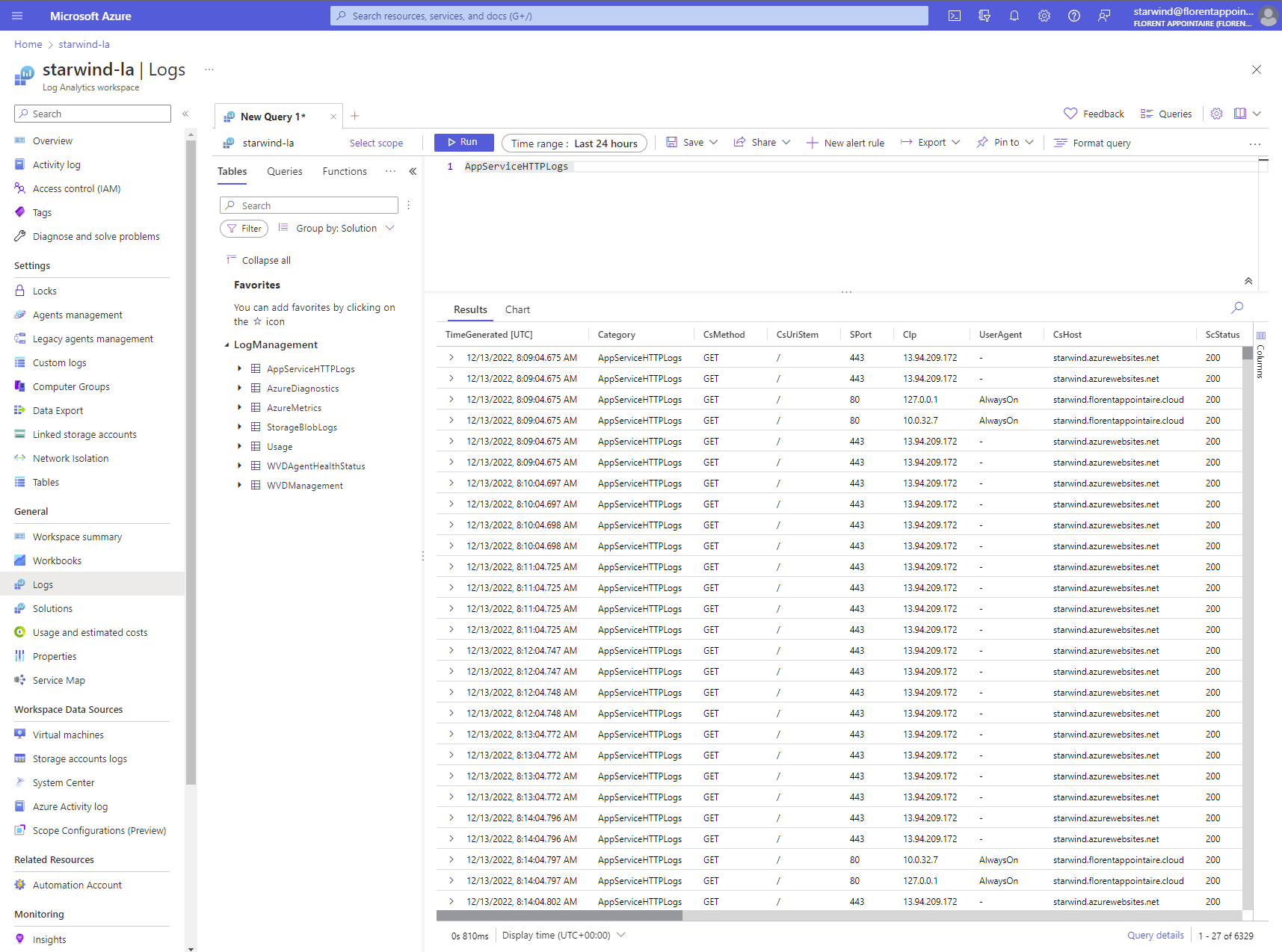
And for App service plan:
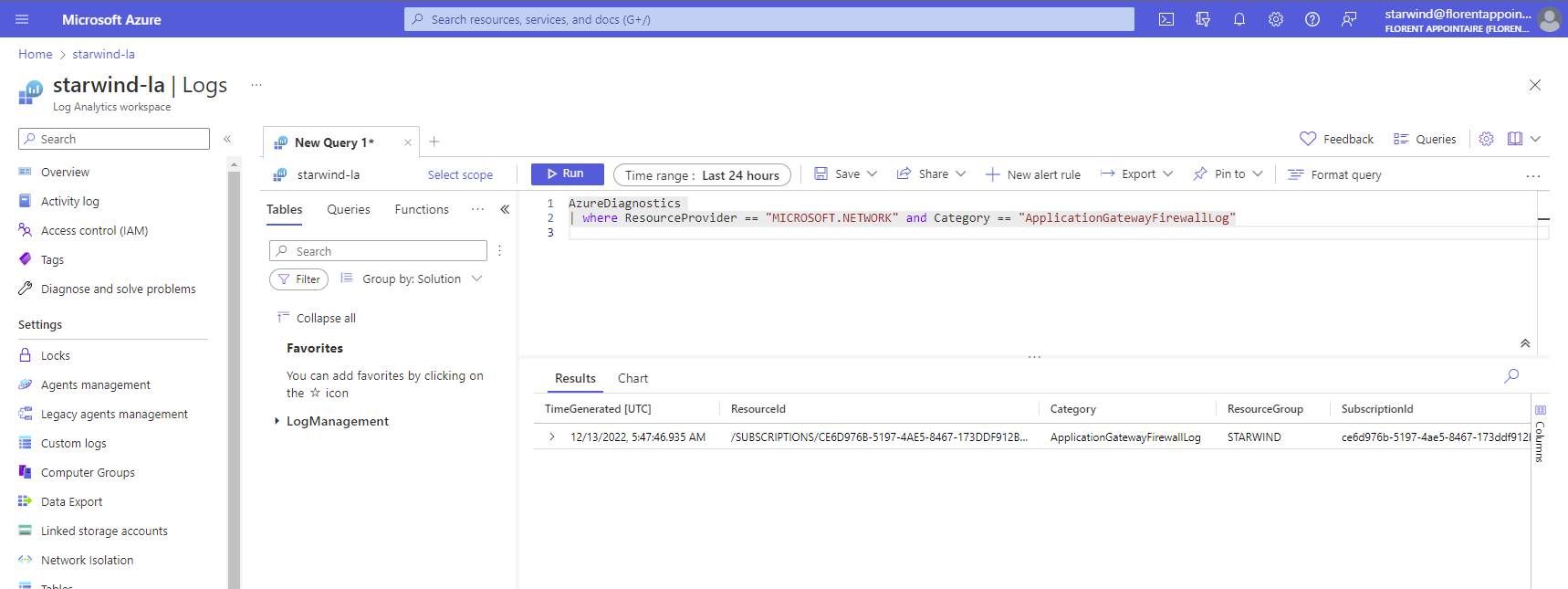
Finally, for Application Gateway logs:
It is very interesting to put this in your administration, to have a centralized Log Analytics workspace, with all logs, but with the right permissions for each team.
One problem that I can see, is for example the network part. Logs are common for all disagnostics components, you can’t at this time, give access to a team to a specific part in Azure for a specific team in diagnostics.
I gave you 4 examples of custom RBAC roles, but of course, you can do this with all logs in your Log Analytics workspace.