Windows AD (Active Directory) is a service used to manage users on a network. Windows AD makes the life of end-users and system administrators manage their users easy and securely. It provides a centralized management and control over a large number of users. There are many other benefits using Windows Active Directory but integrating it with a Linux Operating system is another challenge. So, in this article we are going to show you how you can integrate your Linux system with your Windows Active Directory domain.
Prerequisites:
The basic requirements for the task that we are going to achieve in this article is to have a Windows server with Active Directory role installed with a domain configured. On the other hand you need to have a Linux system either with RHEL/CentOS or Ubuntu Operating system running on with sudo rights.
Step 1: Installing required packages
In order to install the required packages, login to your system with root user or run the commands with ‘sudo’ on your Linux system.
First, update your system using the below command.
For RHEL/CentOS:
# yum update -yFor Ubuntu:
# apt-get update -yOnce your system is updated with latest packages, run the command below to install the packages required for domain joining.
For Ubuntu:
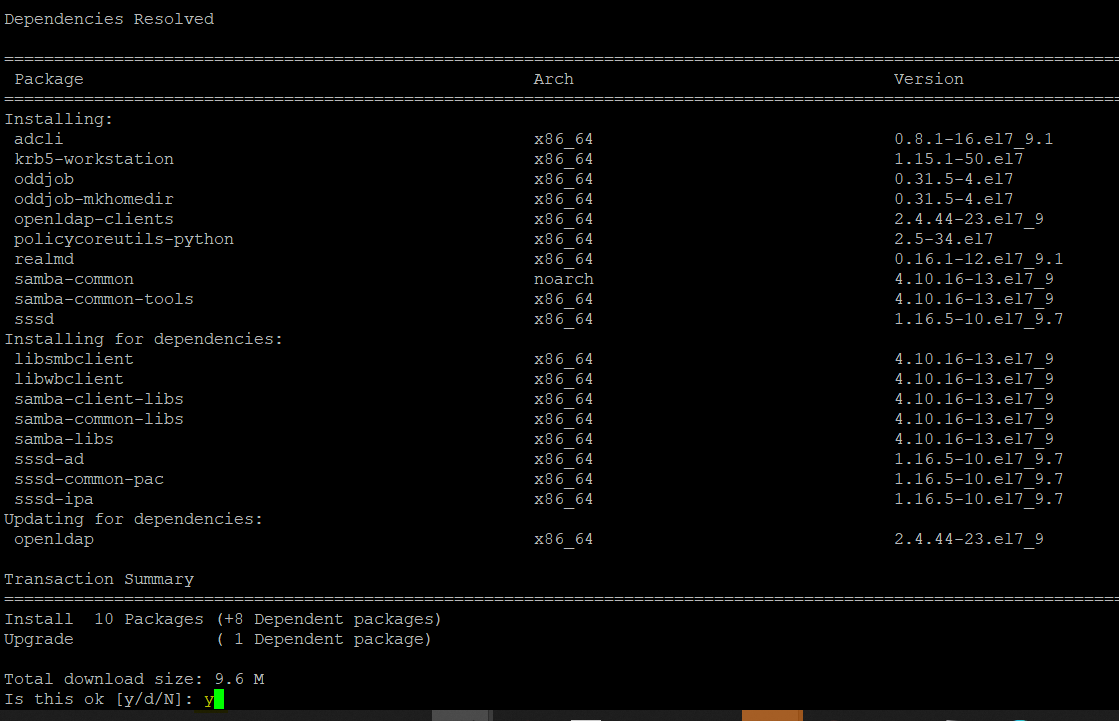
# apt-get install sssd sssd-tools libnss-sss libpam-sss realmd adcli samba-common-bin oddjob oddjob-mkhomedir packagekitFor RHEL/CentOS:
# yum install sssd realmd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation openldap-clients policycoreutils-pythonType ‘y’ and hit enter to continue installing the packages along with their required dependencies.
Step 2: Domain Joining
After the packages are installed, run below the ‘realm’ commands to list and join your Linux system with the domain you want to integrate your system with.
# realm list
# realm join --user=domain_user domain.comYou need to give your own username with sufficient domain admin rights and domain information.
To confirm that your system is joined with the domain, run again the same above command and check the status of ‘sssd’ status, which should be running.
# realm list
# systemctl status sssdStep 3: Domain User Login
As we have our system joined with domain, now lets login using your active directory user account.
Upon successful credentials, your new user’s home directory will be created.
You can check the identity rights of your user using below ‘id’ command.
# id your_user@domain.comIf you want to give your AD users sudo rights on the Linux system, then make sure to allow that in sudoers.
The best convenient way is to create a new group on your AD, make it a member of domain users and add that into sudoers file.
# vim /etc/sudoers
%sudo_group ALL=(ALL) ALLSave and close the file, now every AD user which will be the member of ‘sudo_group’ will be able to gain sudo rights on the system.
Step 4: Domain Configurations Update
Active directory domain user’s behavior can be modified by making changes in its configuration parameters using the ‘sssd.conf’ file.
Open its configuration file using any of your editor to view and update as required.
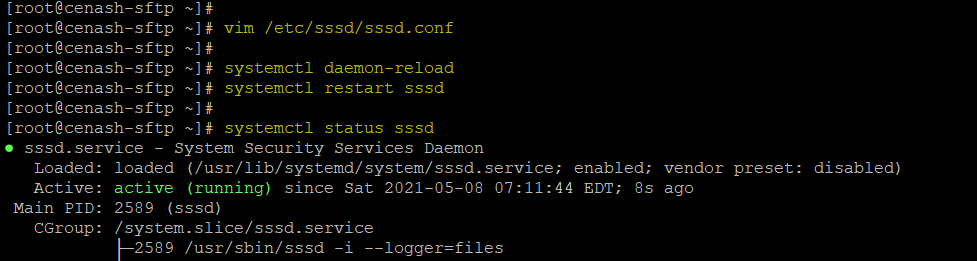
# vim /etc/sssd/sssd.conf
[sssd]
domains = afiniti.com
config_file_version = 2
services = nss, pam
[domain/domain.com]
ad_domain = domain.com
krb5_realm = DOMAIN.COM
realmd_tags = manages-system joined-with-samba
cache_credentials = True
id_provider = ad
krb5_store_password_if_offline = True
default_shell = /bin/bash
ldap_id_mapping = True
use_fully_qualified_names = True
fallback_homedir = /home/%u@%d
access_provider = adAfter making your desired changes in the configuration file, make sure to reload the daemon and the ‘sssd’ service that can be done using below commands.
# systemctl daemon-reload
# systemctl restart sssdConclusion:
In this article we have discussed the steps to join a Linux system with Windows Active Directory. After performing these steps you will be able to login using your AD users, give them sudo rights and even update their domain login parameters as well.