One year ago, I wrote the following article that explained how to manage multiple Azure tenancies with Azure Lighthouse: https://www.starwindsoftware.com/blog/how-to-manage-multiple-azure-tenancies-with-azure-lighthouse. Azure Lighthouse is Microsoft’s multitenant management solution for use by its managed service provider (MSP) partners, who may be overseeing Azure services for customers. Azure Lighthouse was released in 2019 and became essential for day-to-day tasks. But what about the security?
Today, I write a new article based on Azure Lighthouse and Azure Privileged Identity Management (PIM). Few weeks ago, Microsoft released the preview of this new feature: https://azure.microsoft.com/en-us/blog/privileged-identity-management-with-azure-lighthouse-enables-zero-trust/. The main goals are to add more security and to increase the trust relationship between MSPs and customers.
What is Azure PIM?
Microsoft describes PIM with the following definition:
“Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organization “.
When MSP want to access customer’s resources, they will have to activate RBAC role such as:
- Reader
- Contributor,
- Policy Contributor,
- …
Azure Lighthouse with PIM can also force MSP to enable their MFA before accessing resources.
Prerequisites
This only prerequisite is the EMS E5 or Azure AD Premium P2 license that must be held by the managing tenant.
Getting started
Let’s see how to implement Azure Lighthouse with Azure PIM. In this guide, I will authorize two Azure AD Groups. The first one will have “Reader” role and the second one will have “Contributor” role. In this case, I can add all the engineers as reader so that they can only see the Azure resources. When they need to perform a technical task, such as creating a new Virtual Machine in the customer subscription, they will have to activate the “contributor” role.
Please note two things:
- You can not delegate the owner role.
- If you already deployed Azure Lighthouse, you must use the same MSPOfferName to override the deployment
Go to this link https://github.com/Azure/Azure-Lighthouse-samples/tree/master/templates/delegated-resource-management-eligible-authorizations/subscription and download the following JSON files:
- Subscription.json
- Subscription.Parameters.json
In these files, you must replace the following values:
mspOfferName: it is the friendly visible by your customer in the portal
mspOfferDescription: optional, it is a description
managedByTenantId: it is the tenant ID of the MSP tenant
authorizations
principalId: ID of the AAD group
roleDefinitionId: Role ID that you want to delegate (e.g reader)
principalIdDisplayName: The AAD group name
eligibleAuthorizations (roles that you want to delegate through PIM; e.g contributor)
principalId
roleDefinitionId
principalIdDisplayNameThen, run the following command to start the deployment:
PS > Connect-AzAccount
PS > New-AzDeployment -Name LighthousePIM `
-Location "francecentral" `
-TemplateFile "C:\Temp\subscription.json" `
-TemplateParameterFile "C:\Temp\subscription.Parameters.json" `
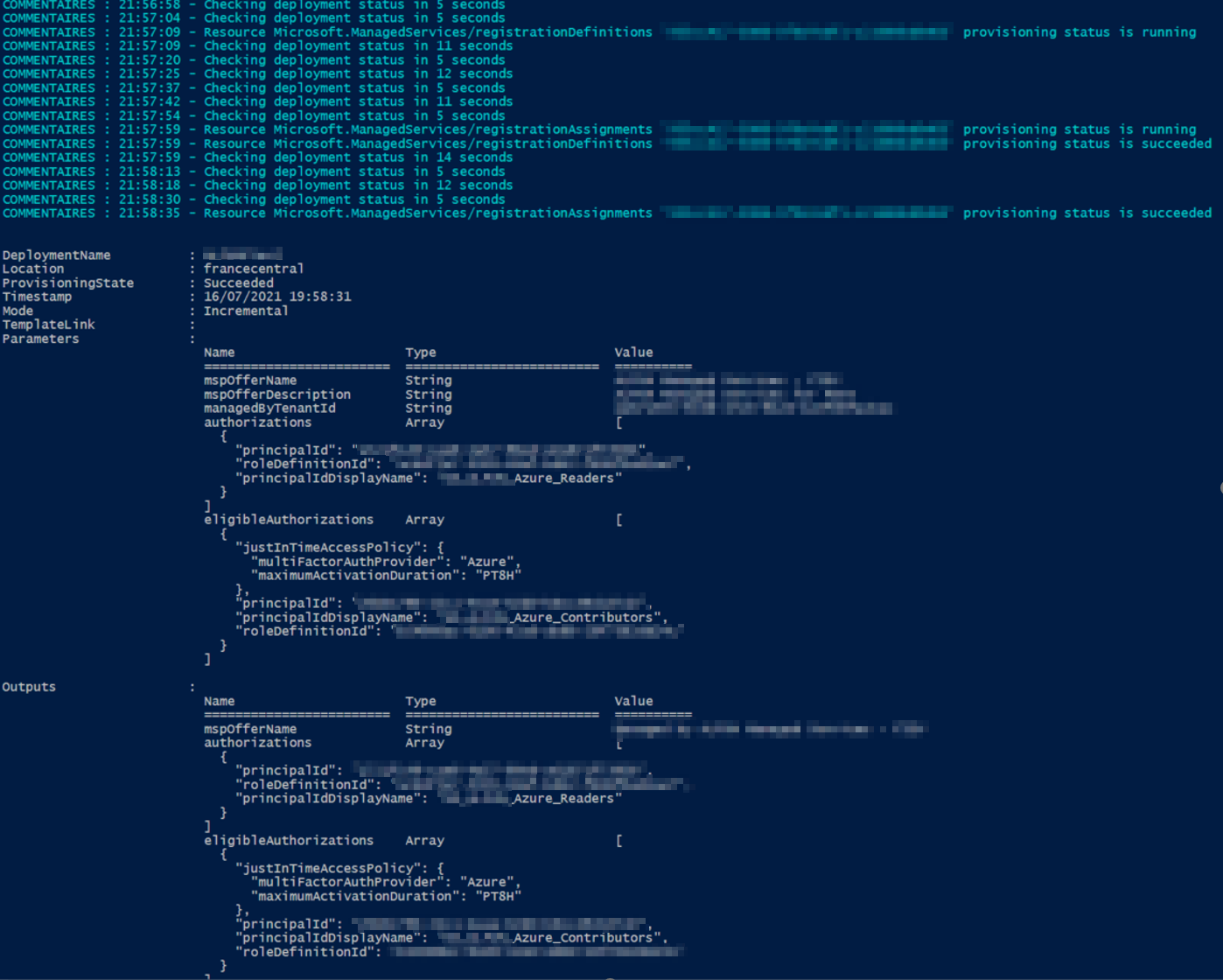
-VerboseIf you want to check the deployment, you can run the following command
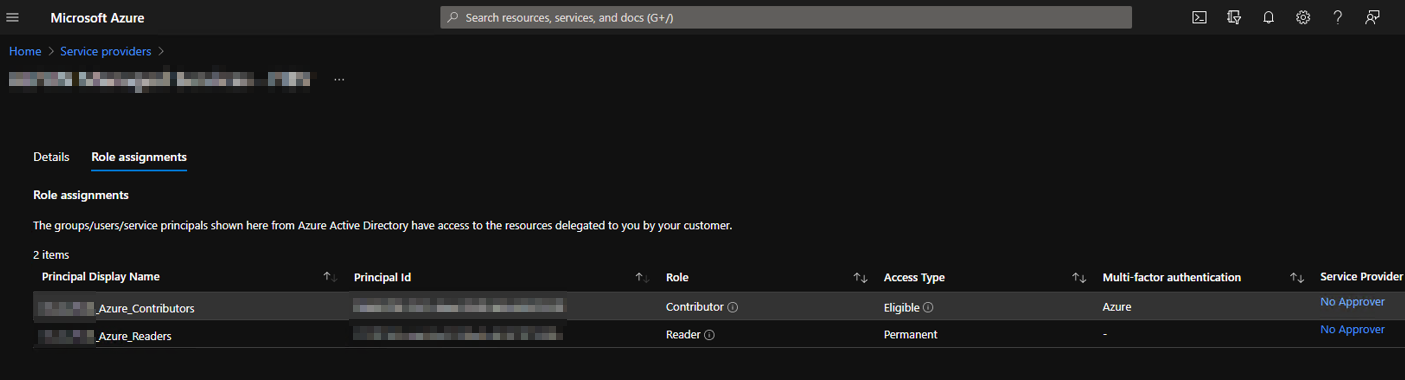
PS > New-AzDeploymentIf you go to the customer portal, you should see the following in the service providers. The first one is the contributor role that must be activated for 8 hours maximum, and the second one is the reader role which is the permanent role.
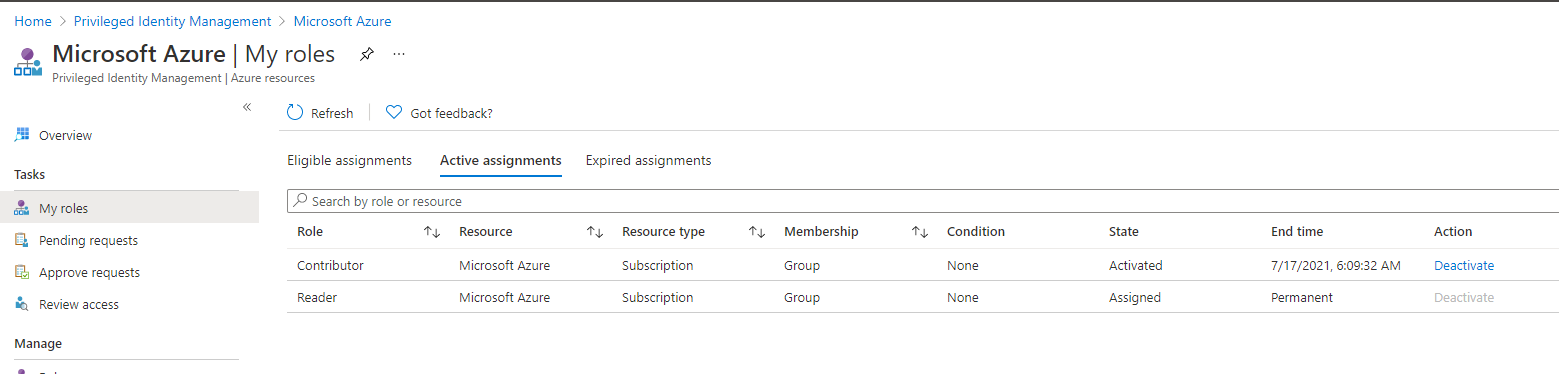
If I switch to the MSP tenant, I can see the eligible roles in the PIM section -> “Azure Resources” -> “My Roles”:
In this example, I activated the contributor role which can be deactivated; however, the reader role can’t be deactivated because the role is permanent.
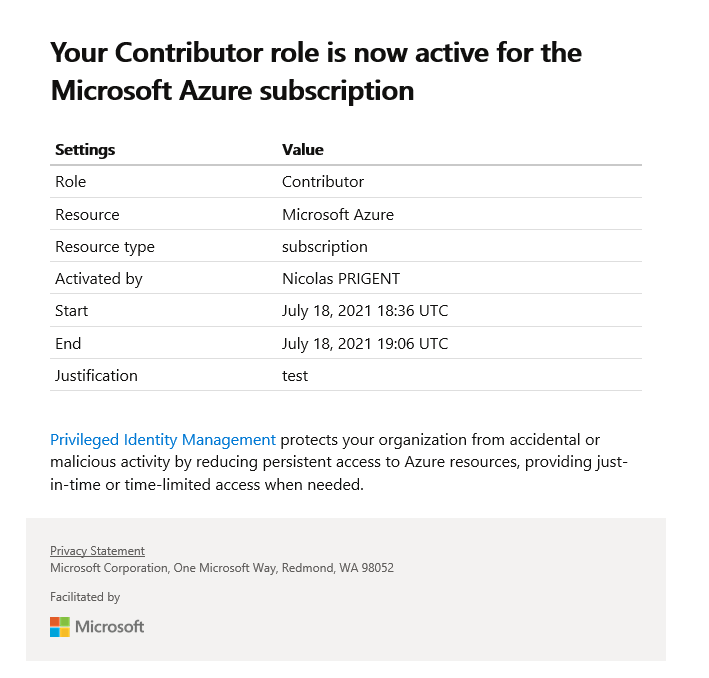
After activating a role, the following notification will be sent