In this series of posts, we’ll discuss the best option to secure and implement Virtualization at small scale within a small company running 2-3 ESXi hosts managed by vCenter server. This article also might be useful for Hyper-V admins willing to migrate to VMware ESXi platform as Microsoft shall phase out Hyper-V. The latest version of Hyper-V Server 2019 will still be supported under its lifecycle policy until January 2029. After that, the transition to Azure Stack HCI with monthly payments will become mandatory.
IT admins managing small infrastructures are most of the time people that are not in the IT at first, but got responsibilities of an “IT guy” because their main job wasn’t an IT. As a result, within their small company, they are responsible for their IT outside their day-to-day tasks as an accountant, or administrator.
The size of a small business company (SMB) differs in different parts of the world. If you say SMB within US, it does not say the same as you say SMB in Europe. In fact, SMB in US is already quite big, but still within 2-3 ESXi hosts managed by vCenter server which we need to secure.
VMware vCenter server security
VMware vCenter server appliance (VCSA) is the main management piece of your vSphere infrastructure. You can manage all your ESXi hosts and VMs from a single console. It’s important to keep it as secure as possible.
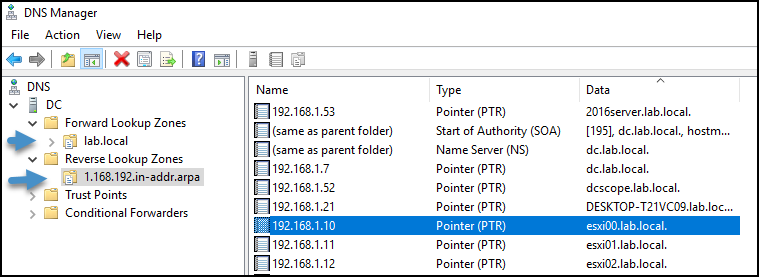
Static IP and DNS resolution – your vCenter server appliance should have a static IP assigned and properly resolved via your internal DNS server. Usually, a DNS server within small organizations is a service installed on Windows Server host, which usually has other roles, such as Microsoft Active Directory (AD). As such, it’s easy to create forward and reverse DNS records for your vCenter server appliance and your ESXi hosts.
Forward and reverse DNS records for my lab ESXi hosts and VCSA
The detailed installation and configuration of VCSA is outside of the scope of this article and VMware has done a great job improving the assistant which walks you through. You’re good to accept the defaults and create “vsphere.local”, the default Single Sign-on (SSO) domain.
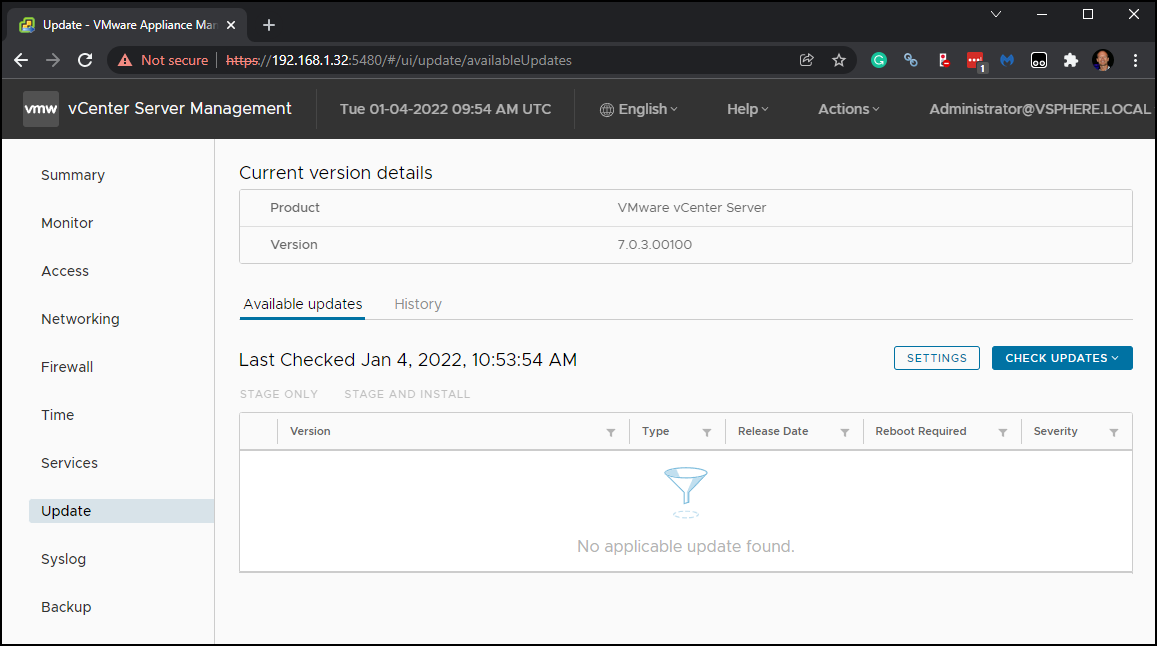
Security patches and updates – As VCSA runs on Linux distribution called PhotonOS, the maintenance of upgrades and patches is simple. The connection to the “maintenance” UI called VAMI (web-based management interface) is accessible through https://ip_of_vcsa:5480 and there you have an update TAB allowing you to check for the latest patches and updates.
Check for latest updates on your VCSA
Note that ESXi Shell and SSH interfaces are disabled by default. Keep these interfaces disabled unless you are performing troubleshooting or support activities.
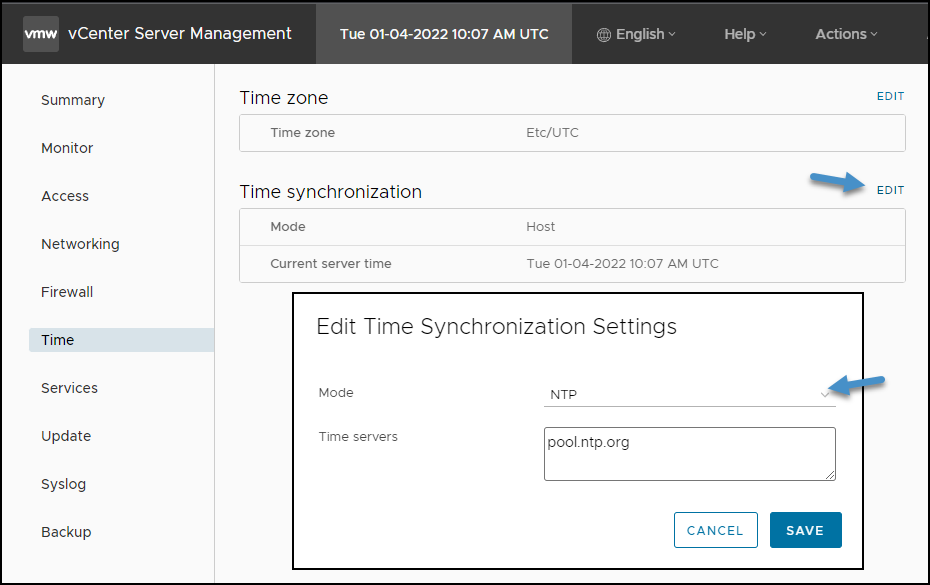
Time synchronization – VMware recommends using a NTP server or pool to keep your VCSA in sync. To set up the vCenter Server to use NTP-based time synchronization, you must add the NTP servers to the vCenter Server configuration. You can do that while you’re within the VAMI UI by clicking the Time menu.
Example of VMware VCSA NTP settings
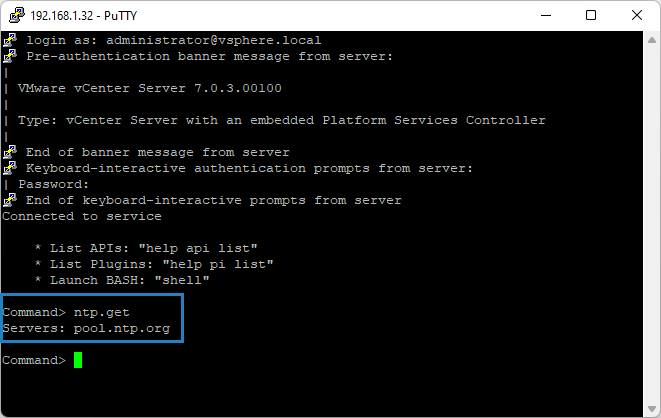
You can verify your current settings while logged in within the appliance shell. You can use this command:
ntp.getThat returns a space separated list of servers for the NTP synchronization.
Note: You’ll only need to go and connect via SSH or console if anything goes wrong. Within normal situation you can see and access the status within the VAMI User interface.
NTP verification example
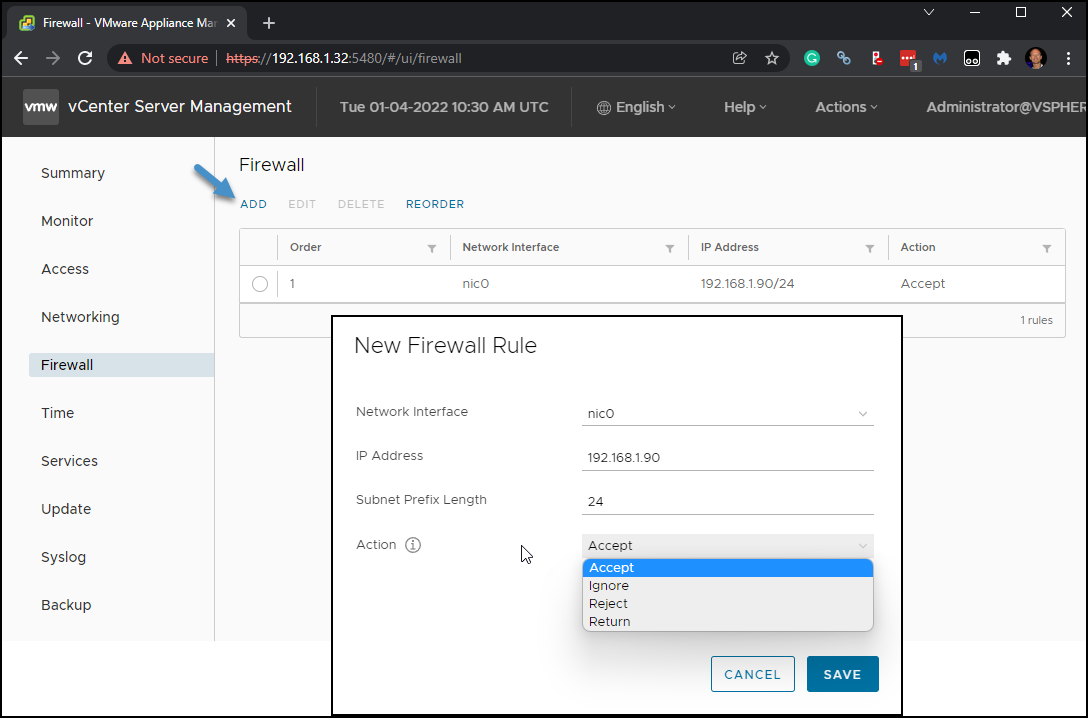
Firewall configuration – VCSA and its built-in firewall is able to restrict access to the appliance. VMware recommends a best practice access to VCSA should be allowed only from trusted hosts or VMs and blocked for the rest of the devices.
Note: If you have backup software, it is important to note that while blocking access to the VCSA, you should definitely leave access for other products like backup products or vROPs, SRM, etc.
Firewall settings of VCSA
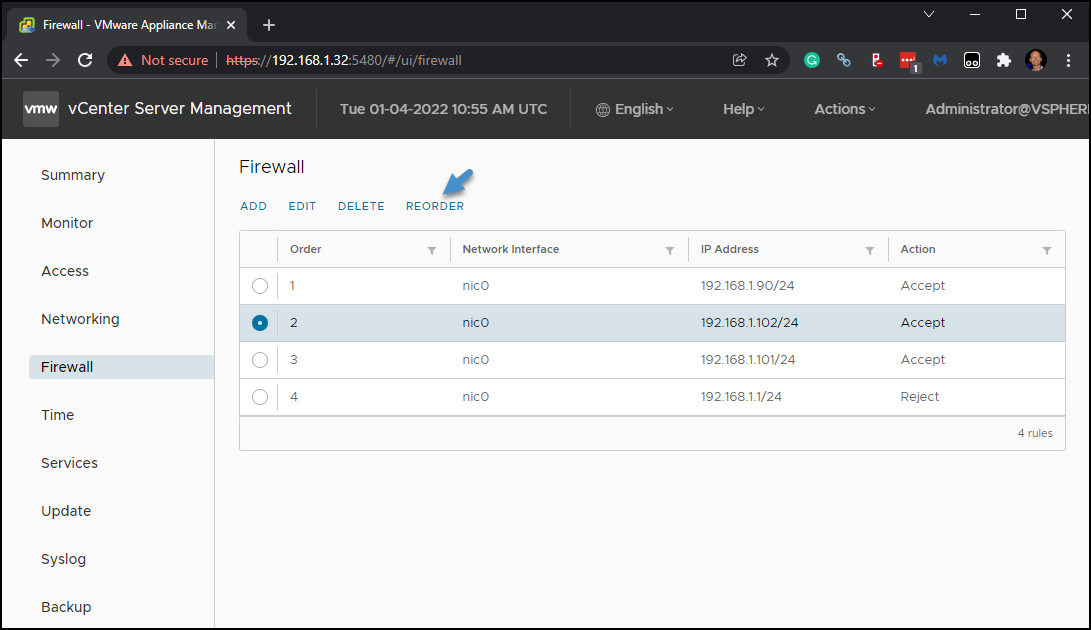
As such, you can restrict (or allow) systems to access your VCSA. The vCenter Server firewall processes and matches rules from the top down. So, if you want to allow traffic and have some blocking rules, first, the top of the list shall have allowed rules. In my example I have some allow rules at the top and one block rule at the bottom.
Note: Within this basic firewall you cannot block individual ports
You can reorder your firewall rules
IN general, firewalls shall be present at entry points. You can install other firewalls on other systems within your network depending of the security risk within your network configuration. You can check the required ports for vSphere 7 at this page at VMware.
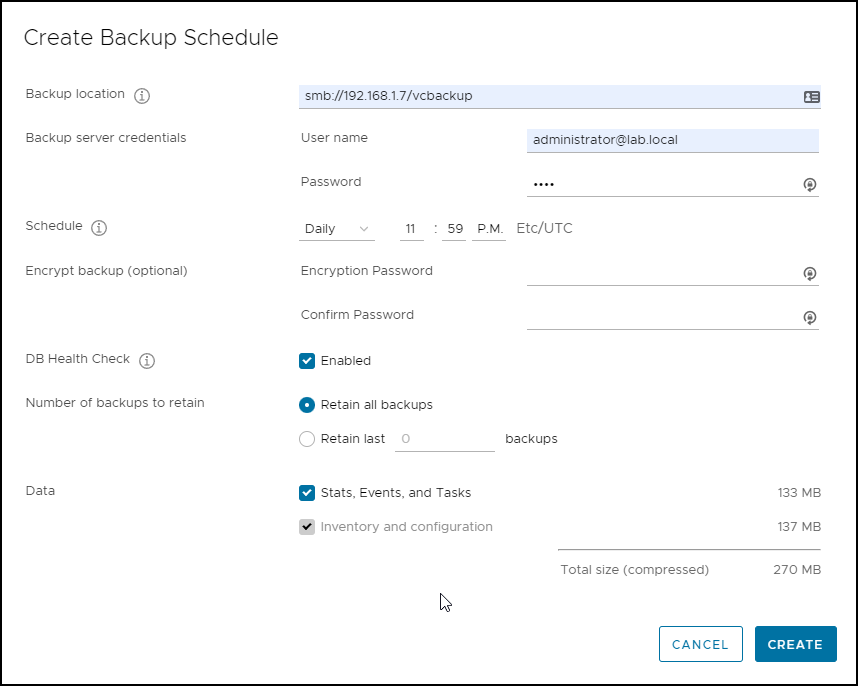
File-Level backup of VCSA – VMware best practice is to configure file-level backup for your VCSA. It allows you, in case you have problem, to restore the configuration of your environment. I found out that it can be an additional help when your other DR and backup plans fails. Before any patching of VCSA is highly recommended to create a snapshot. Other backup plans would be to have a full backup via your backup software and also, as mentioned, snapshot creation.
Create file-level backup of your VCSA
Thoughts
There is a lot of to think of and be prepare for disaster recovery of your environment by securing as much as possible your virtual (and physical) infrastructure. Have three different kinds of backups on different medias and locations while at least one backup shall be highly secured and immutable, which means “undeletable”. In one of the upcoming posts, I’ll show you how to setup a backup storage repository on secured Linux server which will hold your backups that are not possible to delete. Stay tuned for more.