Azure Sentinel becomes a very popular SIEM platform for security IT teams to handle a growing number and complexity of security incidents. The SIEM platform is mandatory to be informed when an incident became true. But what about the incident response? This part is managed by Azure Sentinel as well. Indeed, Azure Sentinel is also a platform for Security Orchestration, Automation, and Response (SOAR).
SOAR is the natural evolution of SOC, driven by the automation of security operations. The SOAR platform is mandatory is you want to reduce the Mean-Time-To-Response. Moreover, you can manage more alerts with less security analyst and of course, you reduce the risk to not see important alerts.
Let us see in this guide how to automate response in Azure Sentinel. First, you must have a Sentinel workspace configured properly. In this guide, I will raise a test alert using Cloud App Security to explain how the incident response works. In Azure Sentinel, enable the data connector “Cloud App Security”
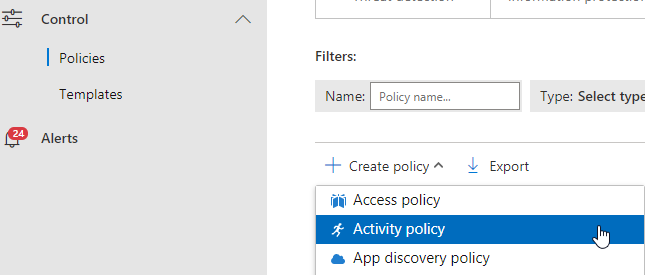
Once it is done, your Sentinel is linked to your Cloud App Security tenant, so you can go to the CAS portal, and create a new policy
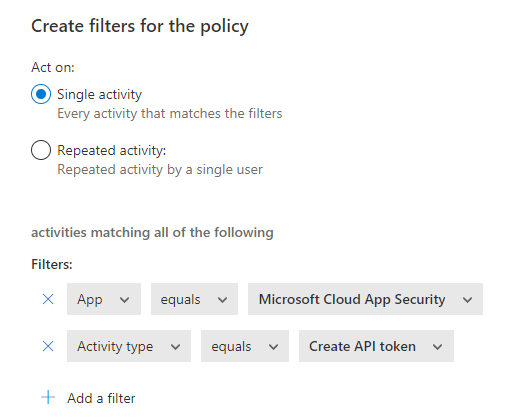
Enter a friendly name for this policy and then, add the following filters
This policy will trigger and alert each time an API token will be generated. Before triggering a false alert, we must configure the incident response in that case.
In this guide, I use a Logic App to automate the response. By using Logic App as an automated response, it is called a playbook. A playbook is a collection of remediation actions that can be run from Azure Sentinel as a routine.
In the Azure Logic Apps section, click Create and edit the Logic App previously created
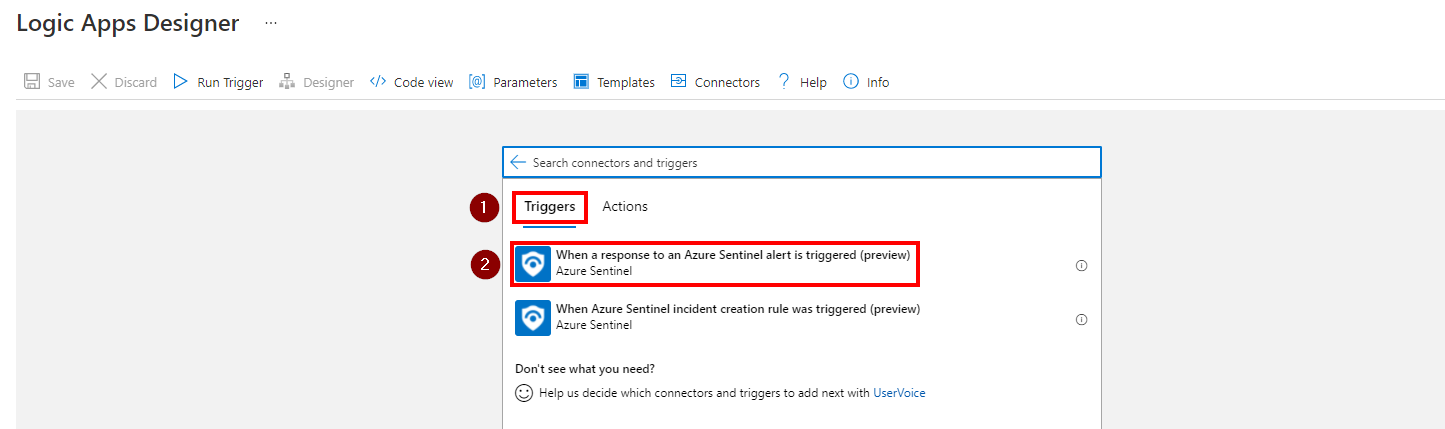
All you need to know about the Logic App pricing is here: https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-pricing. The most important thing to understand when you work with Azure Sentinel and Logic App will be the trigger. Your Logic App must start with the Azure Sentinel trigger.
In this case, the Logic App will start only when a new incident appears in Azure Sentinel. It will be mandatory to automate incident response. You will need to sign in to create a connection to Azure Sentinel. You can use your account (not recommended), a service principal (I would recommend this one) or a managed identity.
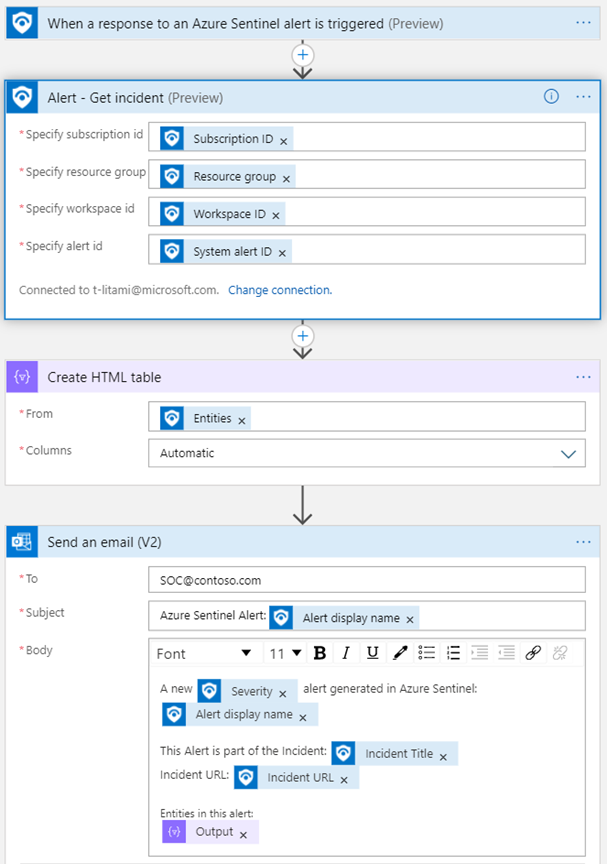
Then you can build your incident response depending on your needs. If you need help or examples, you can refer to this documentation: https://docs.microsoft.com/en-us/connectors/azuresentinel/
The following example from Microsoft can be a good starting point, it will send an email when a new alert is raised:
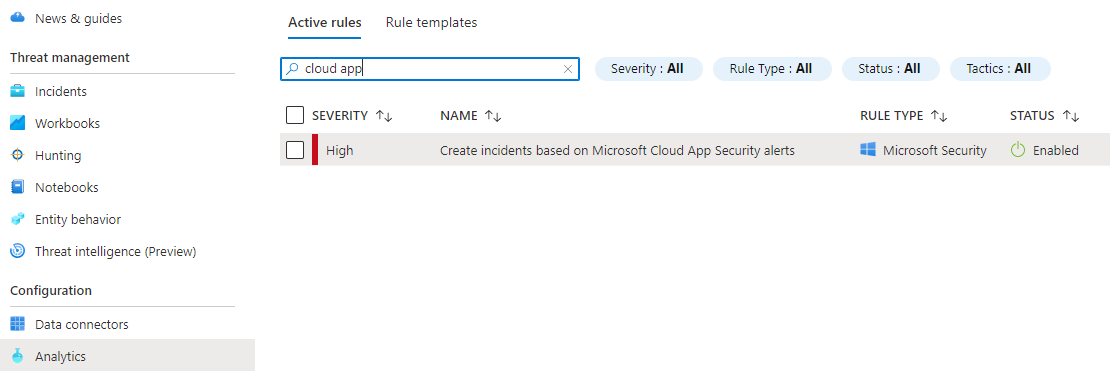
When you are happy with your Logic App, go to the Azure Sentinel workspace, click “Analytics” and search for “Cloud App”. This rule will trigger your Logic App when a new alert appears.
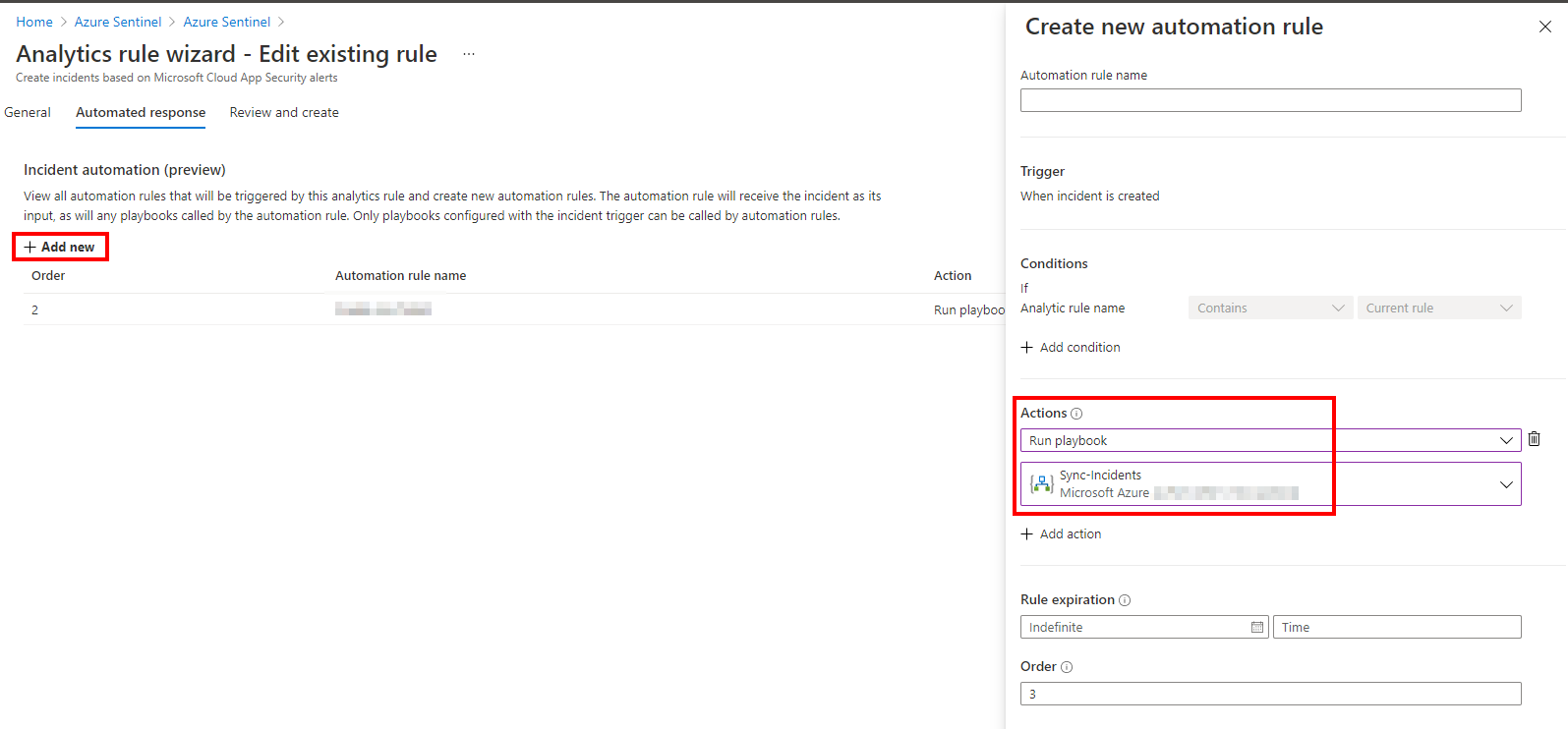
In the automated response tab, click “Add new” and select “Run playbook”. You should see your Logic App. Please note that if your Logic App is not visible or grayed out, it means that the Logic App trigger is not correct. You really need to use the following trigger https://docs.microsoft.com/en-us/connectors/azuresentinel/#when-a-response-to-an-azure-sentinel-alert-is-triggered
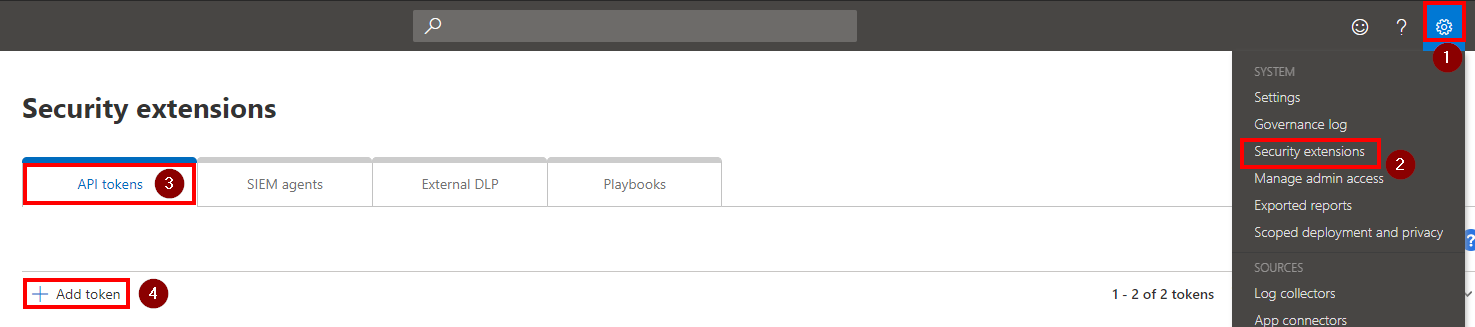
Save the rule. Now we can generate a new token in Cloud App Security to create a false alert. Go to the settings, click “Security Extensions” and “Add token”
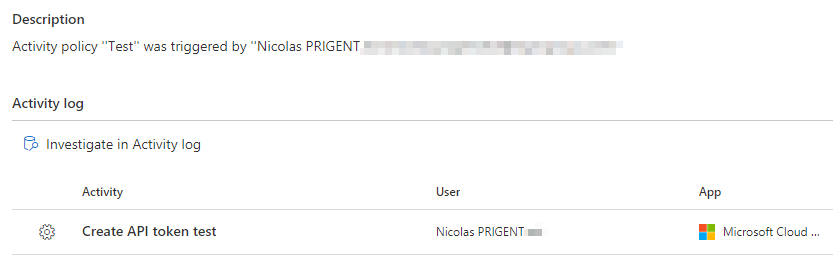
You should see the following alert in the alerts tab (just wait 1 or 2 minutes)
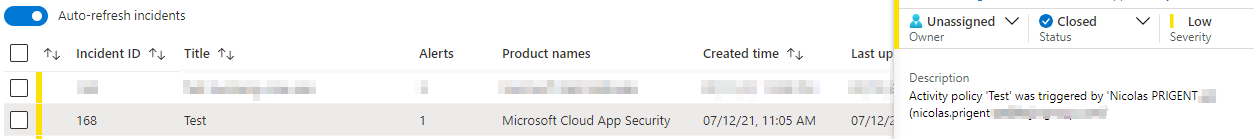
Now, switch to the Azure Portal and go to the Azure Sentinel section to confirm if the alert is visible
And then, confirm that your Logic App has been triggered as excepted.
Go to the following GitHub to see many playbooks examples: https://github.com/Azure/Azure-Sentinel/tree/master/Playbooks