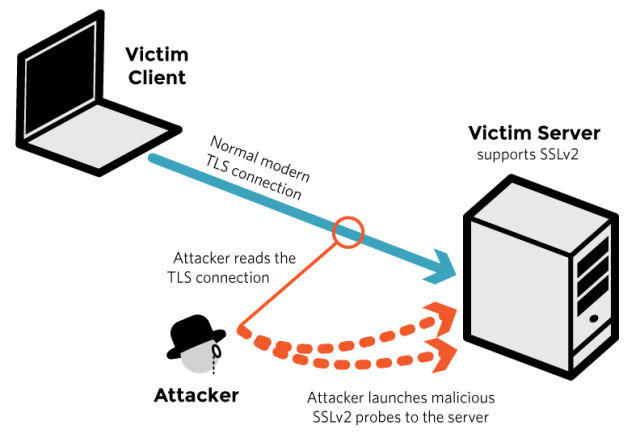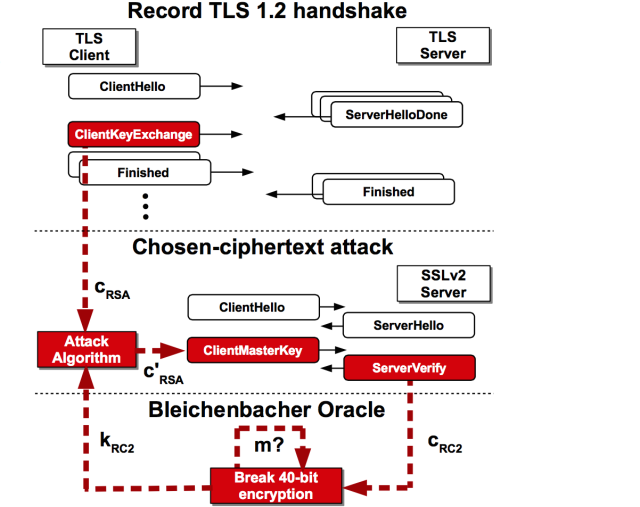
A new low-cost attack that decrypts sensitive communications in neglectable time has been discovered recently. The attack works against TLS-protected communications using RSA cryptosystem which expose the key through SSLv2, which was retired two decades ago due to vulnerabilities, but still may be supported by some service due to legacy compatibility reasons or misconfigured TLS implementations.
According to statistics, over 5.9 million Web-servers directly support SSLv2. Though, even when a server doesn’t allow SSLv2, it may still be susceptible to attack if the underlying RSA key pair is reused on a different server supporting the old protocol.
The researchers dubbed the latest vulnerability DROWN, short for Decrypting RSA with Obsolete and Weakened eNcryption. The most notable example of TLS implementation known so far to be vulnerable to DROWN is OpenSSL cryptolibrary, for which a new security patch was released recently.
This is the review of an article.
Source : arstechnica.com