Introduction
Nowadays, every company is doing its best to protect its data, which is pretty much its most valuable asset. As you know, data is vulnerable to unauthorized access and that’s when Microsoft BitLocker saves the day. BitLocker is the encryption technology from Microsoft, which makes possible to encrypt the Logical Volume on the transparent blade-based level (not physical disk). In this article, we will see how to encrypt Cluster Shared Volume (CSV) using Microsoft BitLocker to protect your data against unauthorized access.
Starting from Windows Server 2012, Microsoft has added the BitLocker support for Cluster Shared Volumes to create an additional layer of protection for sensitive, highly available data. It allows adding an extra barrier to security by allowing only certain user accounts access to unlock the BitLocker volume. BitLocker uses the Advanced Encryption Standard (AES) encryption algorithm with either 128-bit or 256-bit keys. As to authentication options…well, there are few to choose from. You can authenticate by specifying a PIN or by storing a key on a flash drive, which you would then need to insert in order to boot the system.
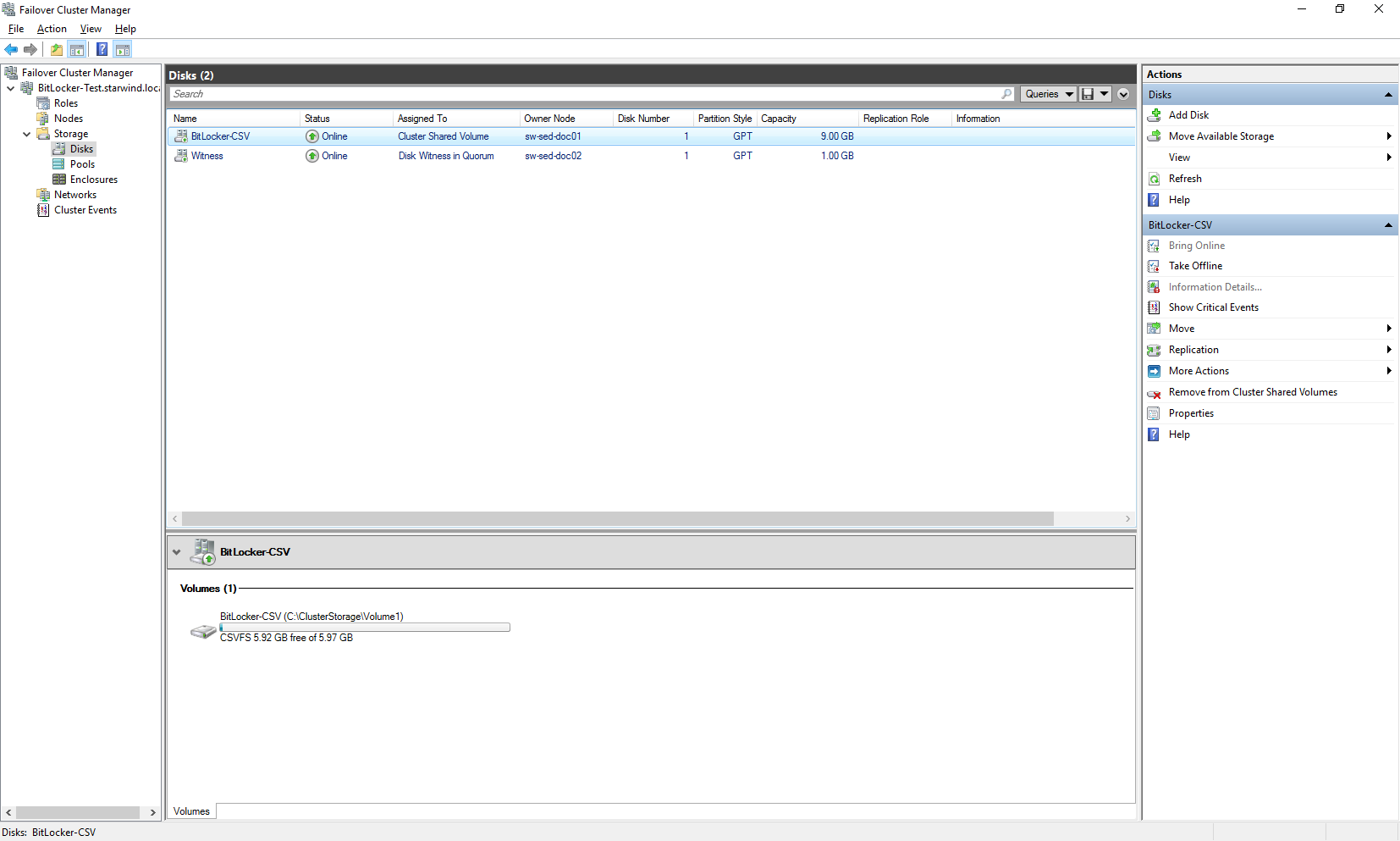
In my case, I have a two-node hyperconverged Hyper-V configuration with 2 StarWind devices (Witness and BitLocker-CSV) which are connected via iSCSI and presented to the Microsoft Failover Cluster.
Below, you can find two different ways to encrypt storage for your Cluster:
1. The first option is to encrypt the host’s underlying storage logical volumes (where StarWind devices are located). This way will improve the volume protection from an unauthorized access to the volume or from decrypting data without a specific password which you can set.
2. The second option is to encrypt a CSV inside a Failover Cluster, based on shared storage which is provided by StarWind VSAN HA devices. This can be implemented as an additional security layer for your already encrypted underlying logical volume or can be used as the single and more granular way of encrypting.
I’ve decided to use StarWind VSAN since it mirrors the storage inside the nodes, allowing to create a shared storage for my Failover Cluster.
Encrypting logical volumes on the underlying (physical) storage
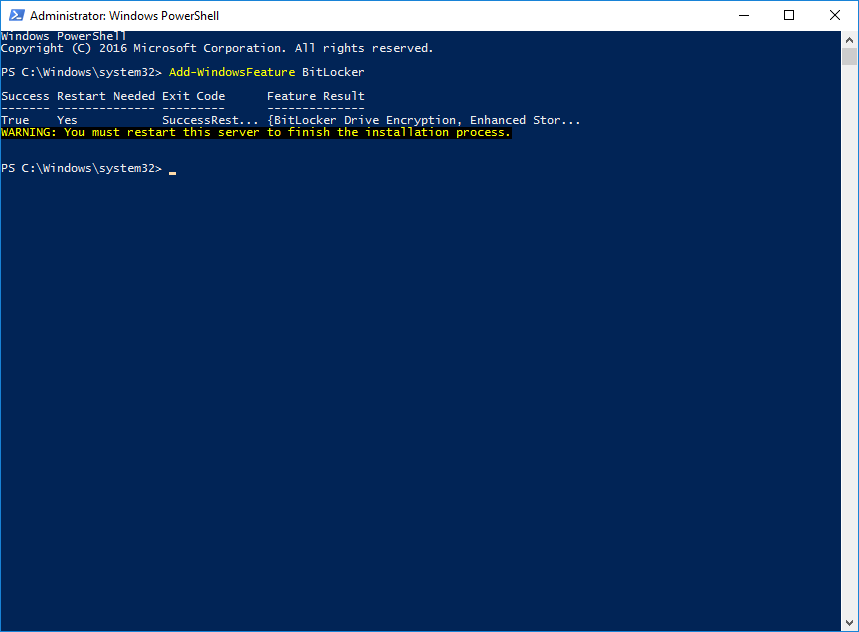
1. First of all, we need to enable the BitLocker Windows Feature on each clustered node.
Note: The installation will require the reboot.
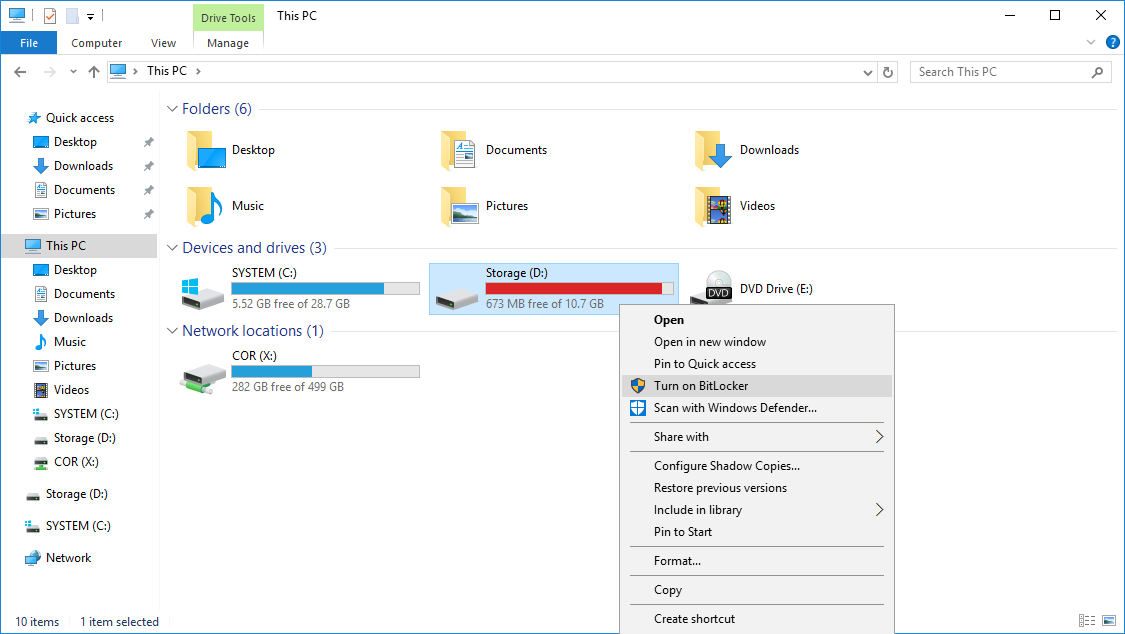
PS>Add-WindowsFeature BitLocker2. The encryption of the local volume can be done through GUI or via PowerShell. To make it via GUI, right-click on the required volume and choose “Turn on BitLocker”.
 3. Select “Use a password to unlock the drive” and specify the password.
3. Select “Use a password to unlock the drive” and specify the password. 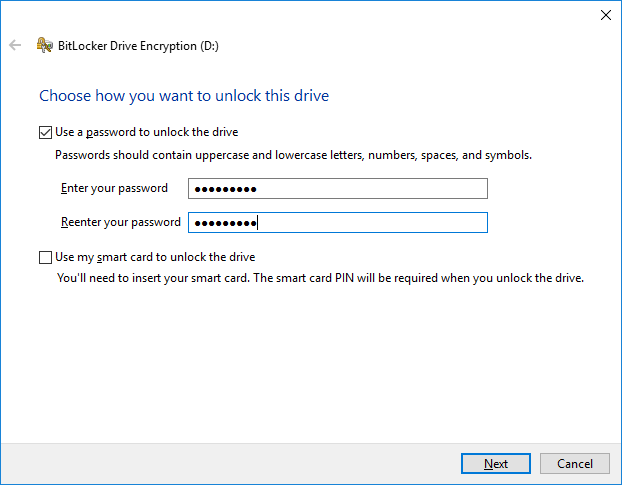
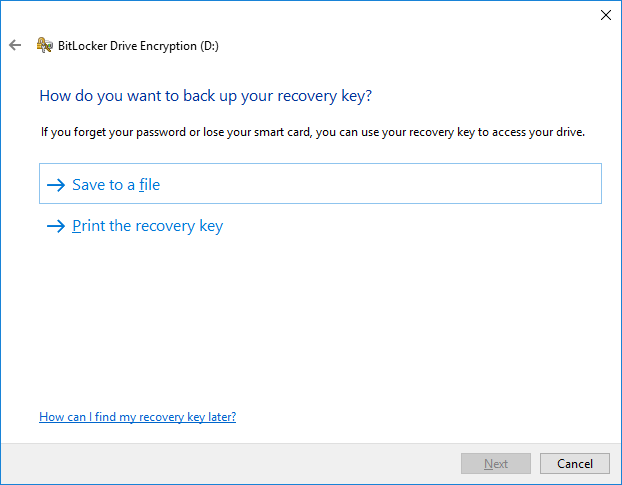
4. Select any option you like. You can use a network share, USB or any other PC in the domain to store the recovery file.
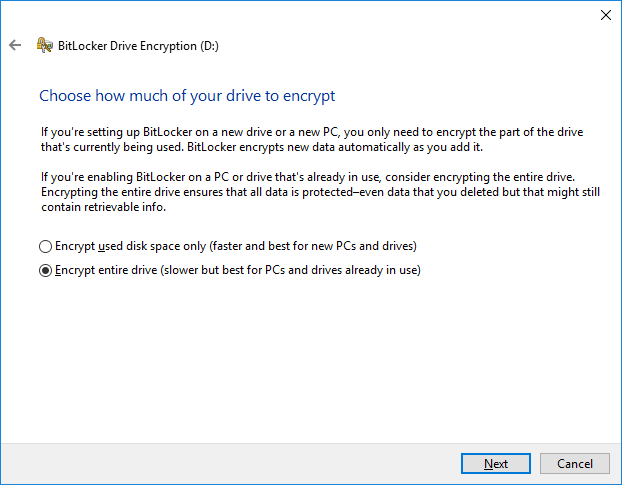
5. Select “Encrypt entire drive” and click “Next”.
6. Use the “Compatible mode” option and click “Next”. 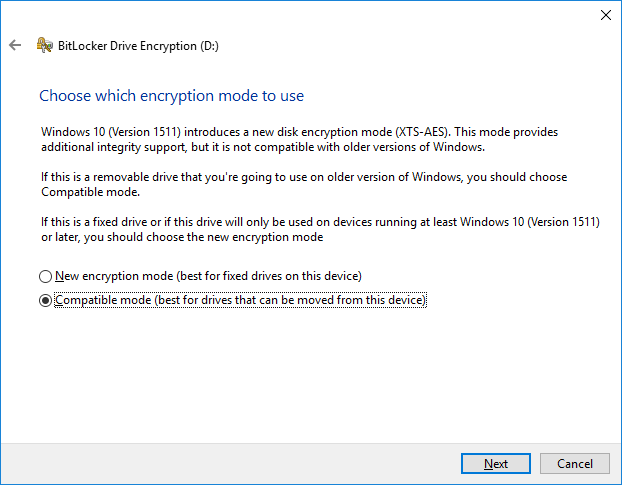
7. Click “Start encrypting” and wait until it ends. 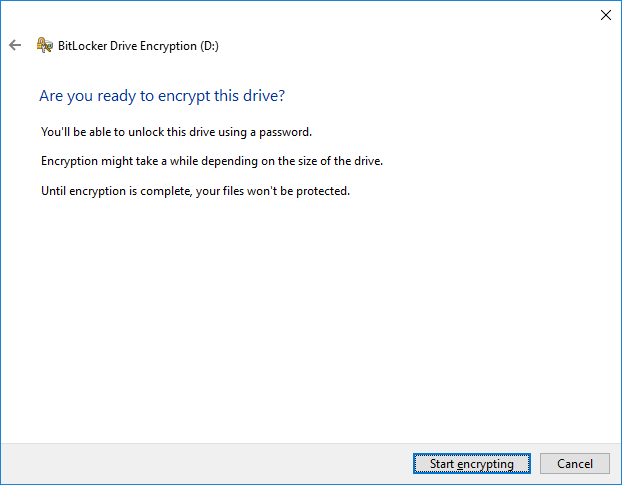
8. Repeat the same steps for each drive which you want to encrypt on the local and the partner nodes. 
Encrypting CSV based on StarWind HA devices
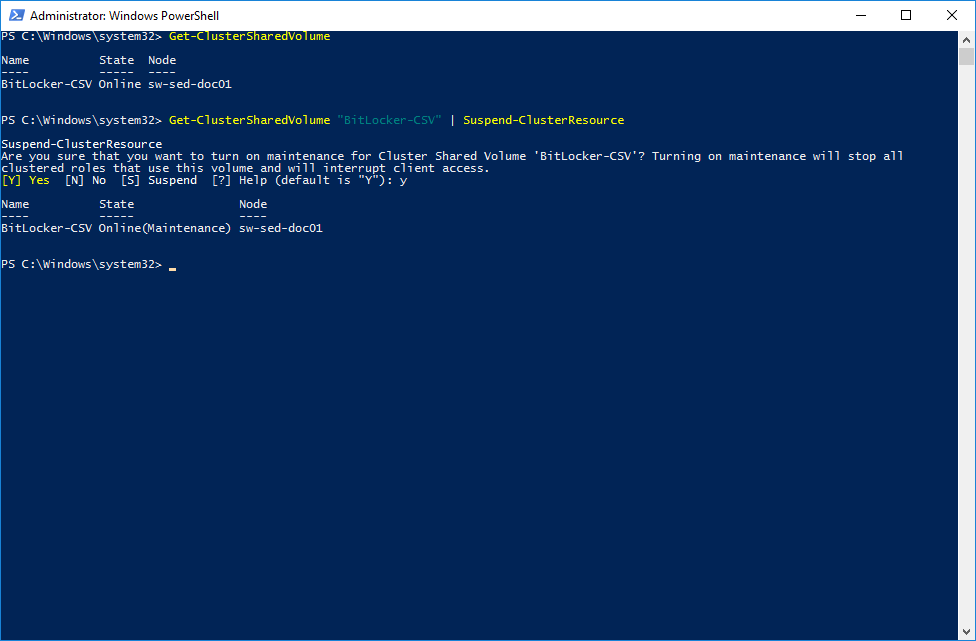
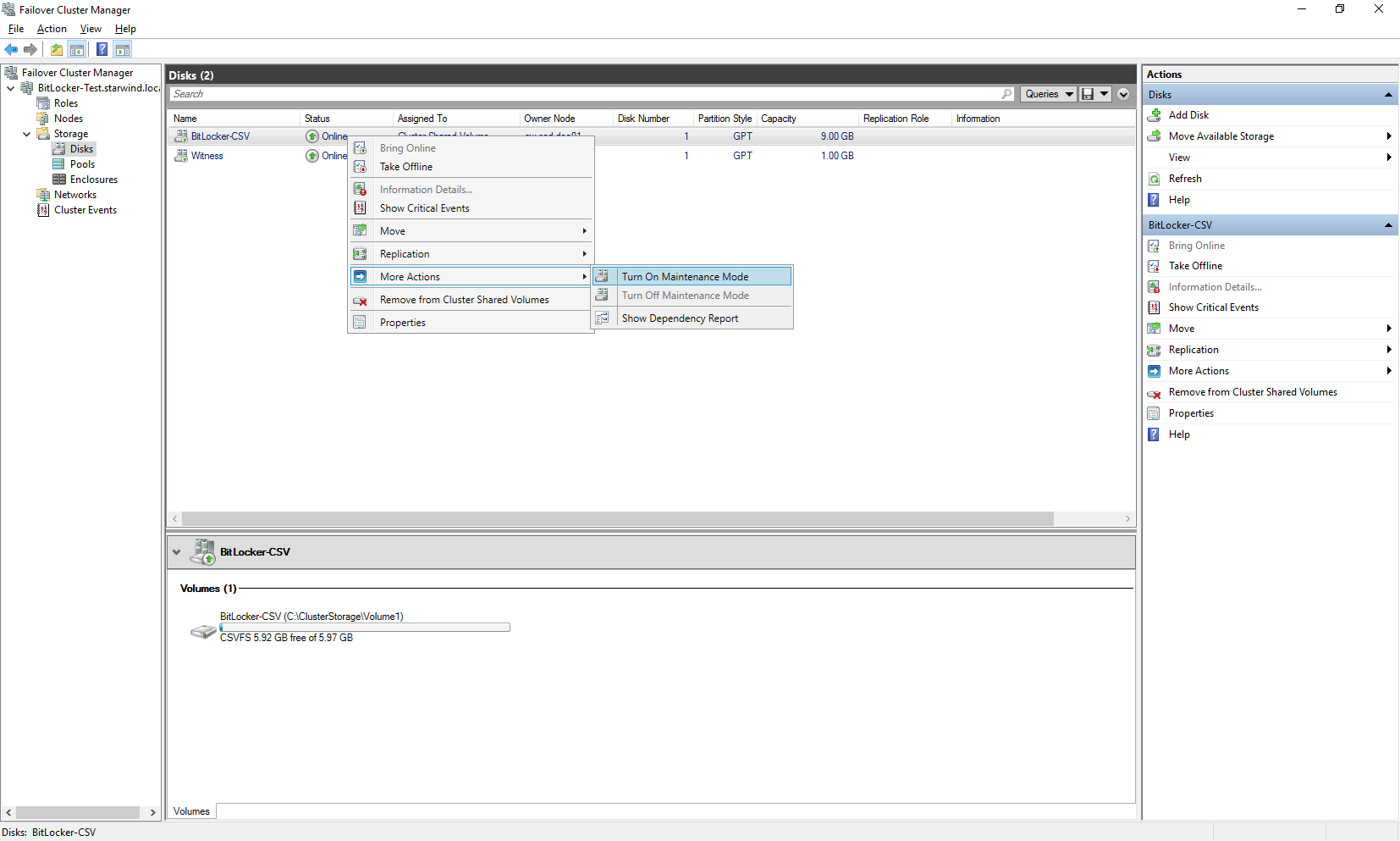
1. Windows can encrypt CSV only when a CSV is in the “Maintenance Mode”. So, to perform this operation you need to turn off all roles on the CSV gracefully. You can do it via Failover Cluster Manager or via PowerShell. Put the CSV to maintenance:
PS>Get-ClusterSharedVolumePS>Get-ClusterSharedVolume “name of CSV” | Suspend-ClusterResource2. Now, we can encrypt the CSV.
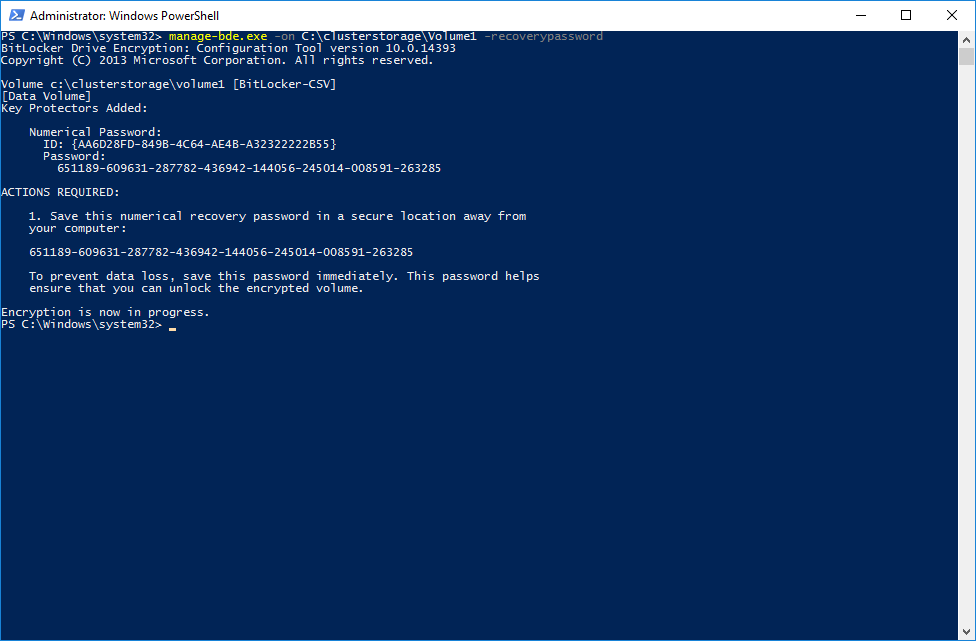
PS>manage-bde.exe –on c:\clusterstorage\volume1 –recoverypasswordNOTE: Please copy and save the recovery key to restore the access if it’s needed. Also, do not return the CSV from the Maintenance Mode until the next step is done.
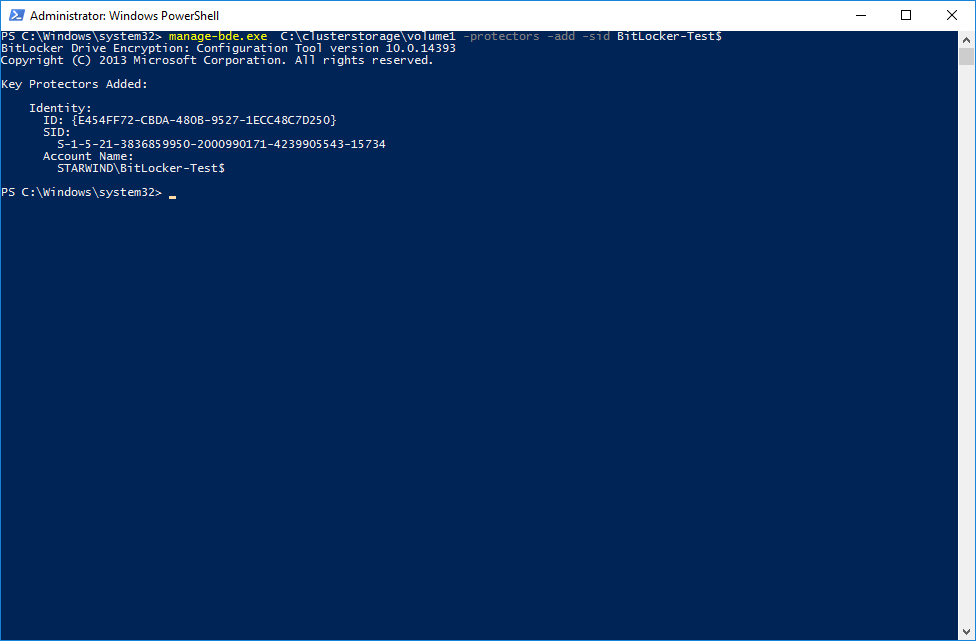
3. As an addition, we need to provide the cluster with the access to our encrypted CSV.
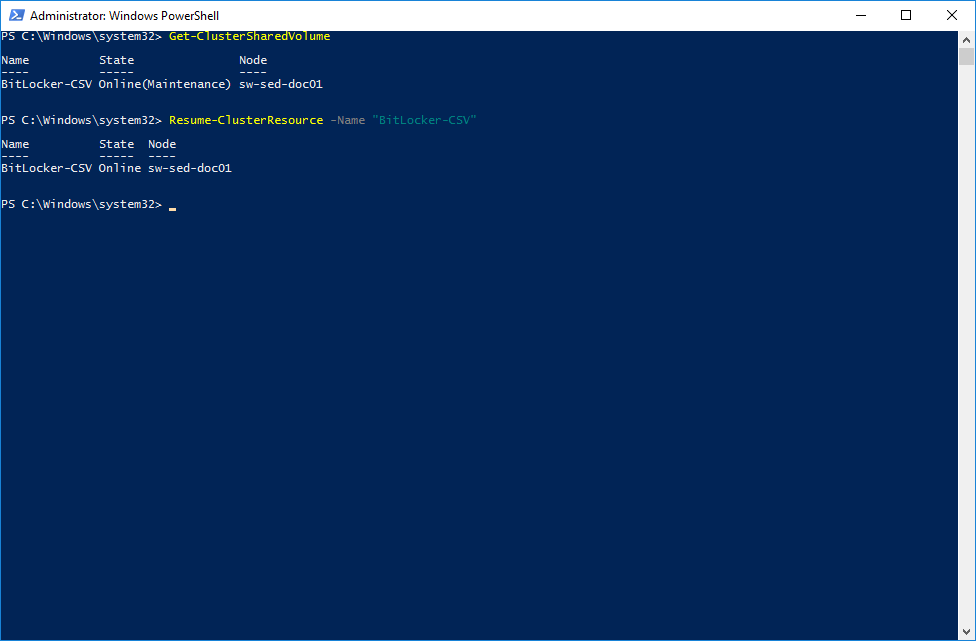
PS>manage-bde.exe C:\clusterstorage\volume1 –protectors –add –sid “cluster name”$4. Now, we can turn off the “Maintenance Mode” for the CSV.
PS>Get-ClusterSharedVolume
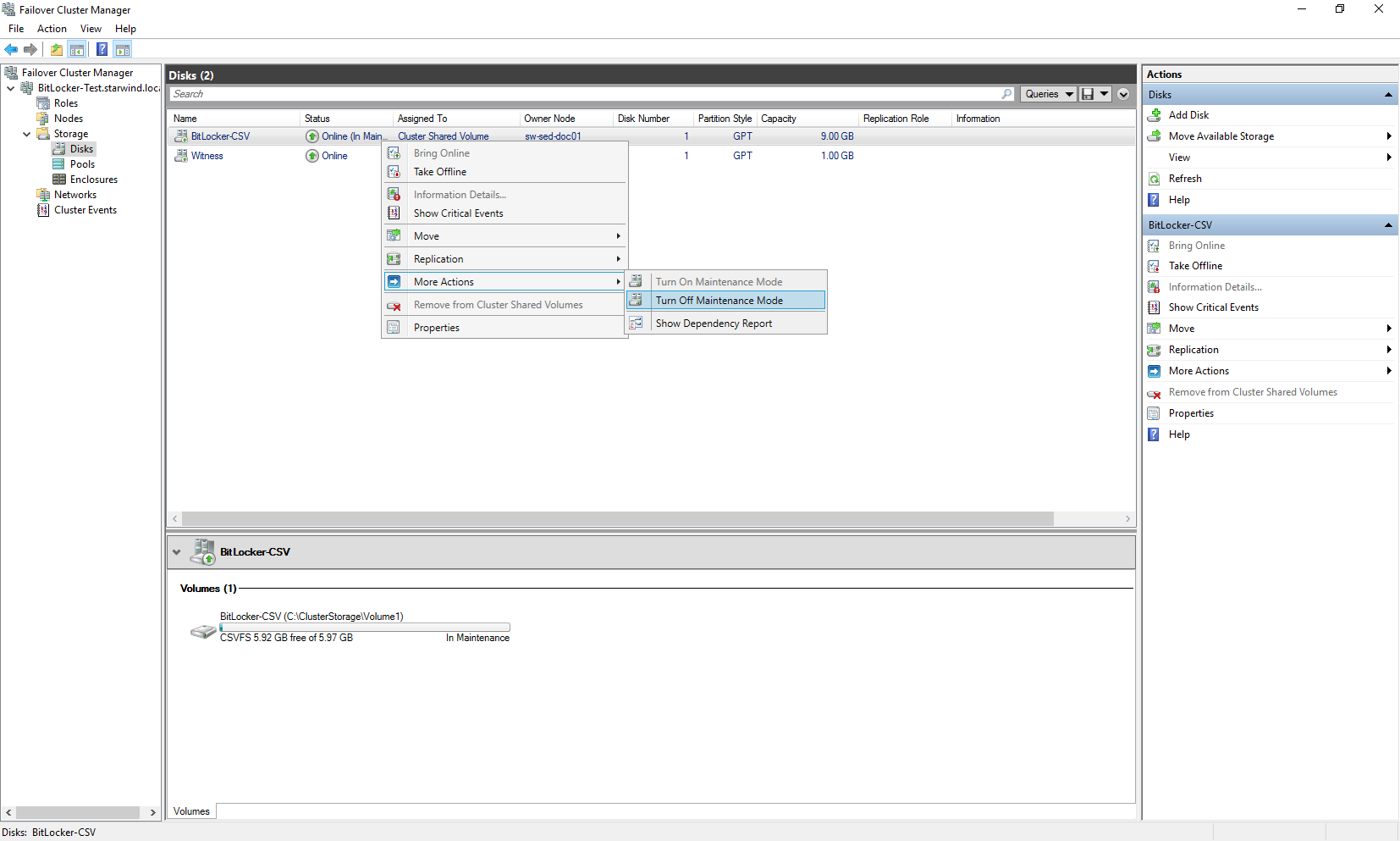
PS>Resume-ClusterResource –Name “CSV name”5. If you will open the Failover Cluster Manager, you will see that the CSV has been successfully encrypted. 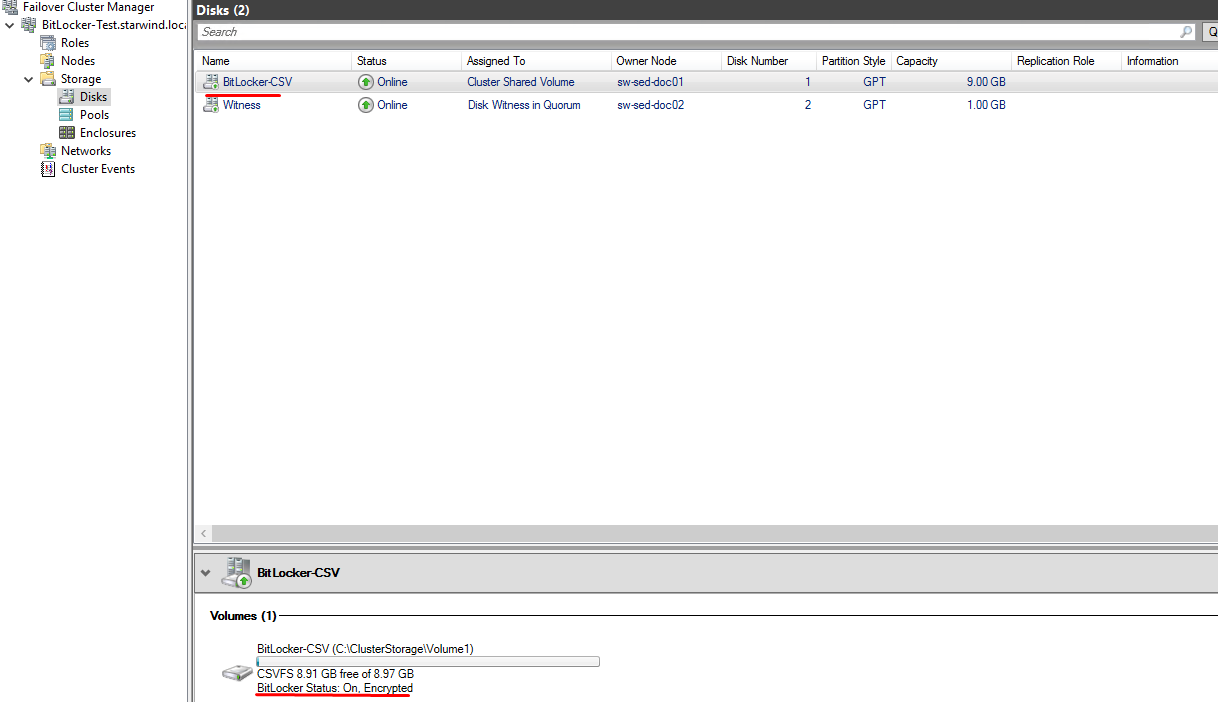
Conclusion
As you can see, we have encrypted the physical (local) logical volume and the CSV inside the Failover Cluster. If you need to encrypt all CSVs in your Failover Cluster, I would recommend encrypting only the local volume. In this way, it will be much easier to manage security keys. However, if you need to encrypt some of the CSVs, you can simply encrypt those without local volume encryption. Ultimately, thanks to BitLocker, we can increase the safety of our data from an unauthorized access to the physical and clustered logical volumes.