Windows Server 2019 should be available in barely two months. So, first migration will start shortly after. From experience, I know that the first feature customers ask for migrating is Active Directory. Therefore, I wanted to try In-Place Upgrade, which has been improved in Windows Server 2019. To try this feature, I upgraded a forest that is handled by two domain controllers running on Windows Server 2016. It was not a “click and fun” process, but Microsoft has really improved In-Place Upgrade. Let’s take a look at how to migrate Windows Server 2016 DC to 2019.
Pre-Migration Steps
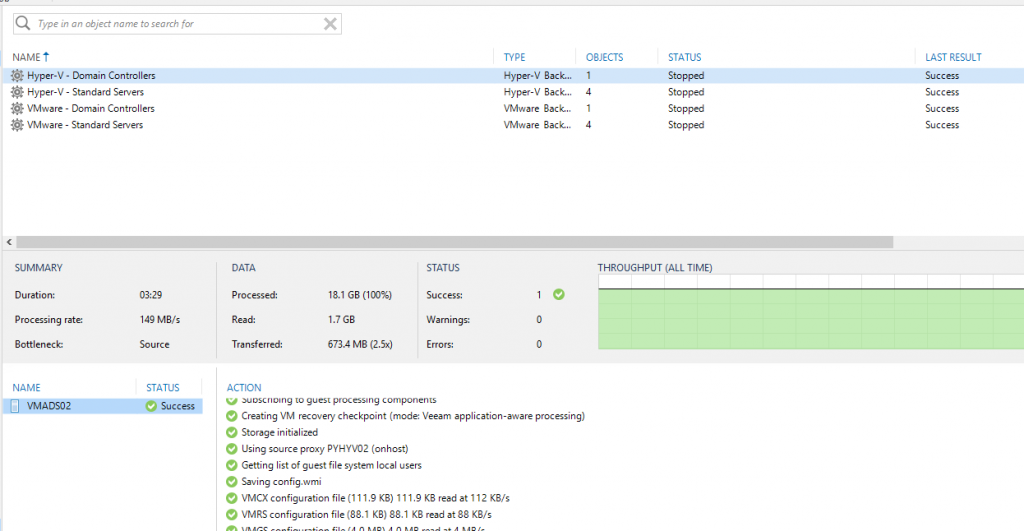
Firstly, check the backup of your domain controller before migrating it. A consistent backup enables you to rollback quickly. This step is often forgotten but it is really important. The following screenshot is a backup of a domain controller by using Veeam.
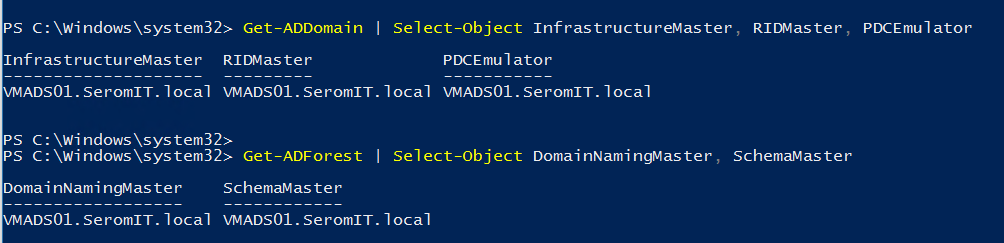
Then, run the following cmdlet to check where FSMO roles are located. I don’t want to upgrade a DC that owns FSMO roles. The schema master role owner should be noted because later we will run some adprep cmdlet against this server.
Get-ADDomain | Select-Object InfrastructureMaster, RIDMaster, PDCEmulator
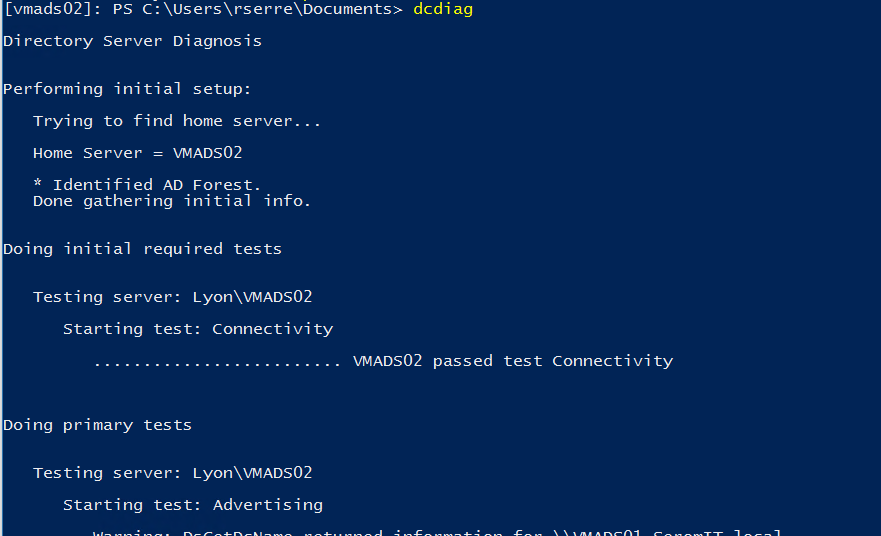
Get-ADForest | Select-Object DomainNamingMaster, SchemaMasterThen, double check the health of your domain controllers. Check that replication is working fine, DCs are healthy and so on. You can use the respective commands, such as dcdiag, repadmin or the event viewer.
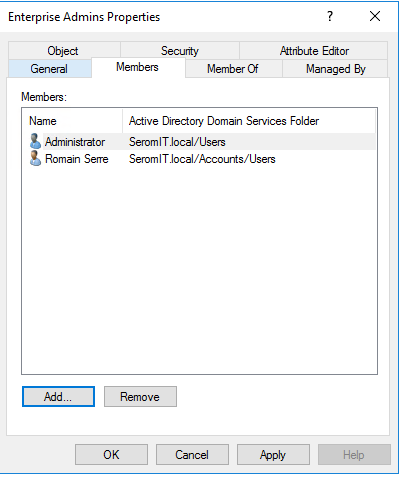
For the migration (and only during the migration), add your Active Directory account to Enterprise Admins and Schema Admins groups. It is required by the adprep cmdlet. When the migration is finished, remove your account from these groups.
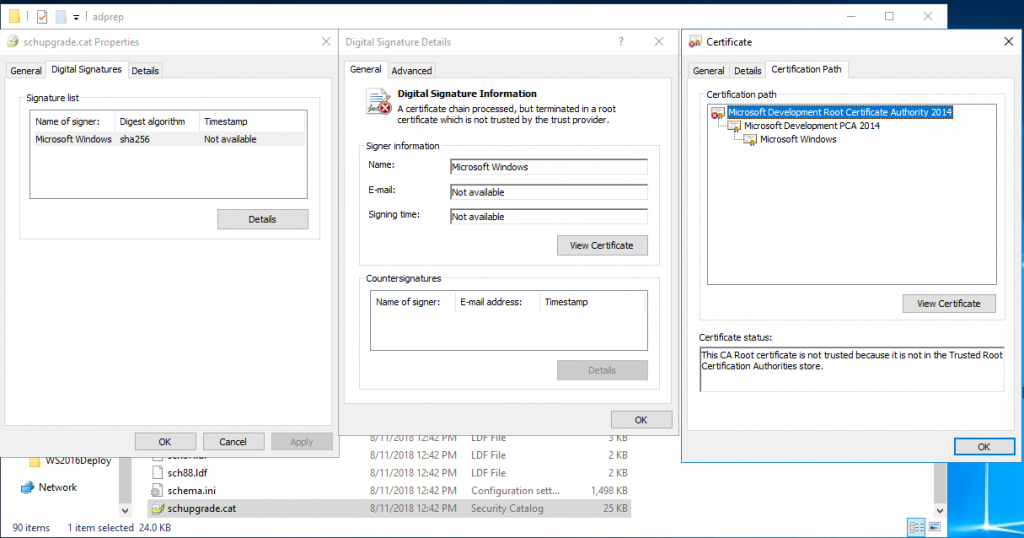
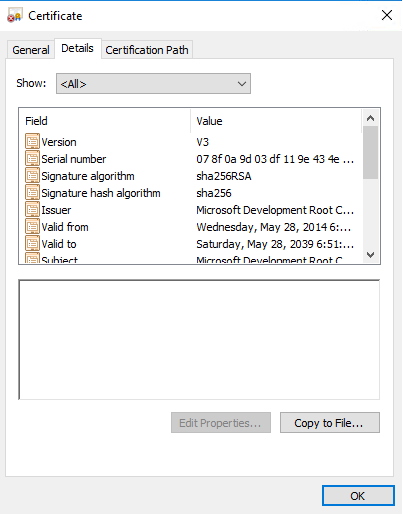
And now for the fun part. Currently there is a bug in the adprep command from Windows Server 2019 17338 build. A certificate must be installed on all servers in order for adprep to run. Mount the Windows Server 2019 ISO on a machine with a GUI. Navigate to <ISO Drive>:\Support\adprep. Right click on schupgrade.cat and select properties. Then open Digital Signatures tab and click on Details. Next, click on view certificate. Click on Certification Path and select the Root CA certificate (the top one). Click on View Certificate.
In the Details tab, click on Copy to file. Save the certificate in a location of your choice.
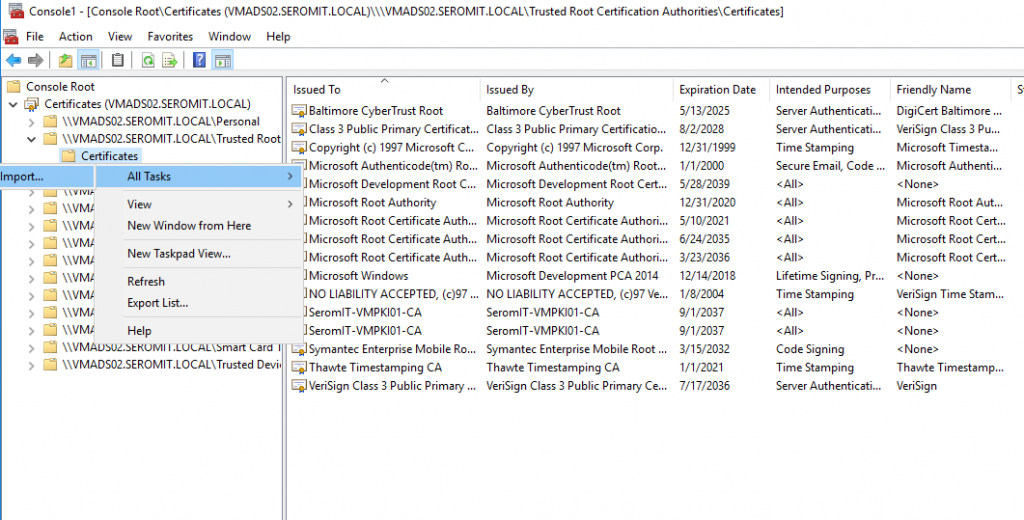
Then, add the certificate to trust root certification authorities store of each domain controller. I used the MMC because my domain controllers are installed in Core edition. You can also use Windows Admin Center or PowerShell.
Don’t forget: this part should be applied for Windows Server 2019 preview and should be resolved with the final release.
Prepare the Forest and the Domain
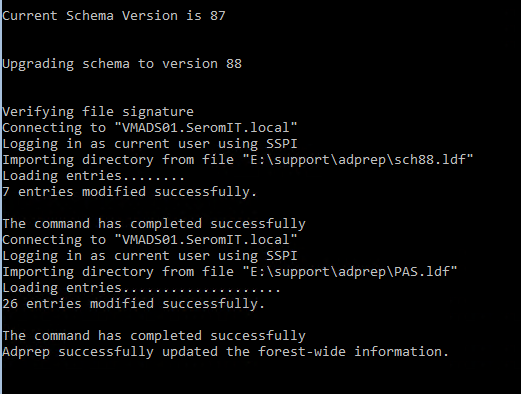
Mount the ISO of Windows Server 2019 on the Schema Master owner. Then, navigate to <ISO letter>:\support\adprep. Run the following command:
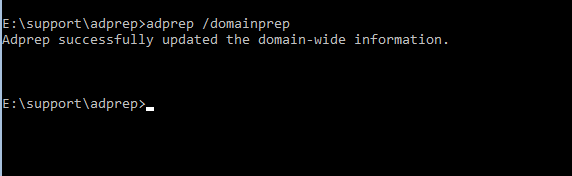
Adprep /forestprepOnce the schema is upgraded, run the following command (this command should be run on all domain controllers):
Adprep /domainprepMigrate First Domain Controllers
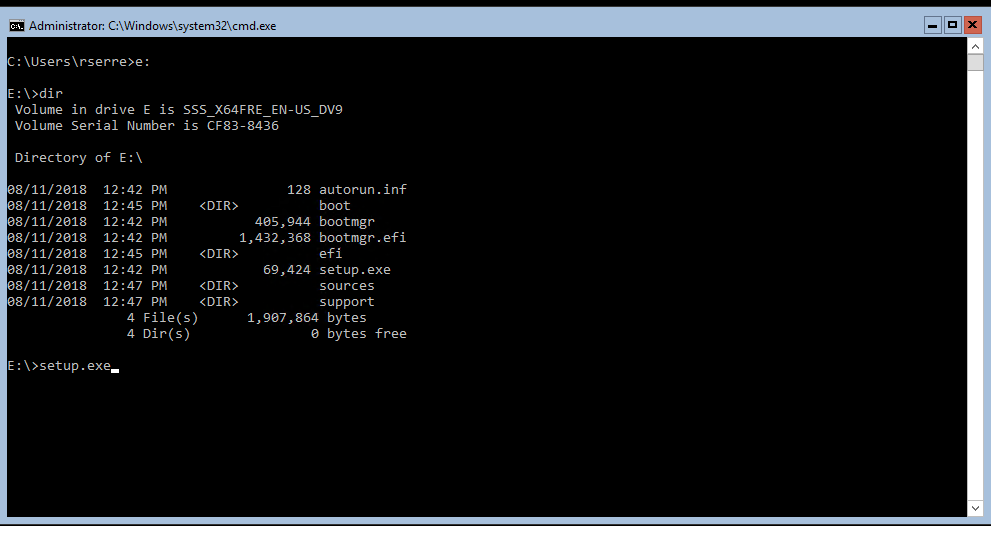
Connect to a domain controller that doesn’t own any FSMO roles. Then, mount the ISO and run setup.exe.
Next, choose whether download updates right now or not.
Then, enter the product key.
Select the Windows Server 2019 edition you want (Core edition or not).
Accept the license agreement and click on Next.
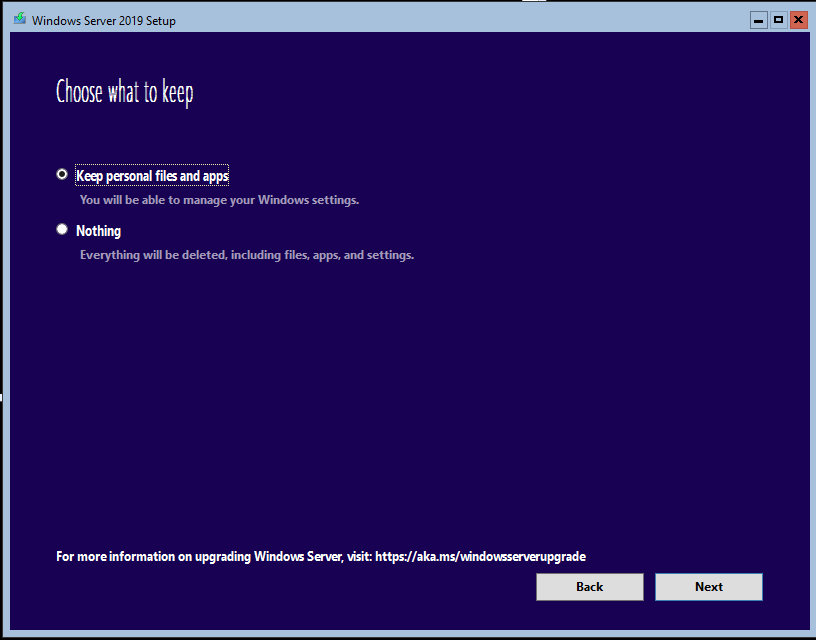
Next, keep personal files and apps to run an In-Place upgrade.
When the wizard has checked prerequisites, it should allow you to update your operating system.
To upgrade the first DC, the process took almost 30min.
Migrate Second Domain Controllers
Now that the first DC is upgraded, I’m going to transfer the FSMO role to this last one. To transfer the role, I run the following script from a DC:
$Server = Get-ADDomainController -Identity "VMADS02"
Move-ADDirectoryServerOperationMasterRole -Identity $Server -OperationMasterRole SchemaMaster,DomainNamingMaster,PDCEmulator,RIDMaster,InfrastructureMasterThen, mount the ISO on the DC and run setup.exe. Follow the same procedure applied to the first domain controller.
Once the migration is finished, you can transfer again the FSMO role to the original owner:
$Server = Get-ADDomainController -Identity "VMADS01"
Move-ADDirectoryServerOperationMasterRole -Identity $Server -OperationMasterRole SchemaMaster,DomainNamingMaster,PDCEmulator,RIDMaster,InfrastructureMasterDon’t forget to remove your account from Enterprise Admins and Schema Admins groups.
Functional Level
Currently, there is no Windows Server 2019 functional level. At present, I don’t know if Microsoft has anything planned for a Windows Server 2019 functional level.
Flight Signing Issue
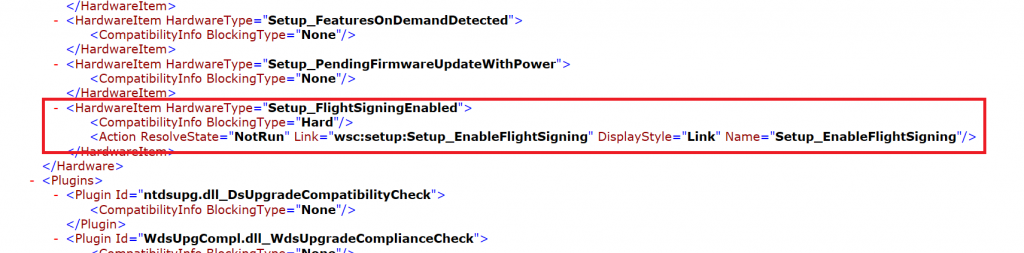
I had an issue that prevented to migrate the second domain controller. If something prevents the in-place upgrade, you can open the folder c:\$Windows~BT\Sources\Panther. In this folder, there is a file called ScanResult.xml. When I opened this file, I saw the following:
Microsoft PM told me how to resolve this issue. To resolve this issue, run the following commands:
bcdedit.exe /set flightsigning on
bcdedit /set {bootmgr} flightsigning onThen, start the setup.exe again.