It’s always better and beautiful to have a secure website, with HTTPS access. To do this, we will use Let’s Encrypt, and the integration with AKS and Application Gateway.
To do this configuration, I have my DNS that are hosted on Azure DNS. So, I will give DNS Zone Contributor right, on the resource group where my DNS are hosted, to the Service Principal of the AKS. If it’s on another subscription, create a new Service principal, with same rights.
Deploy resources and pods, to your cluster:
|
Now, create a secret, for each subscription where are stored your DNS. In my case, my Azure DNS are stored on 2 different subscriptions, so, I will create 2 secrets, with the password of each service principal:
|
Create a file, certmanager-prd.yaml, and paste the following code. Adapts it:
|
Apply this file:
|
We will now deploy an application, with HTTPS, with the following template:
|
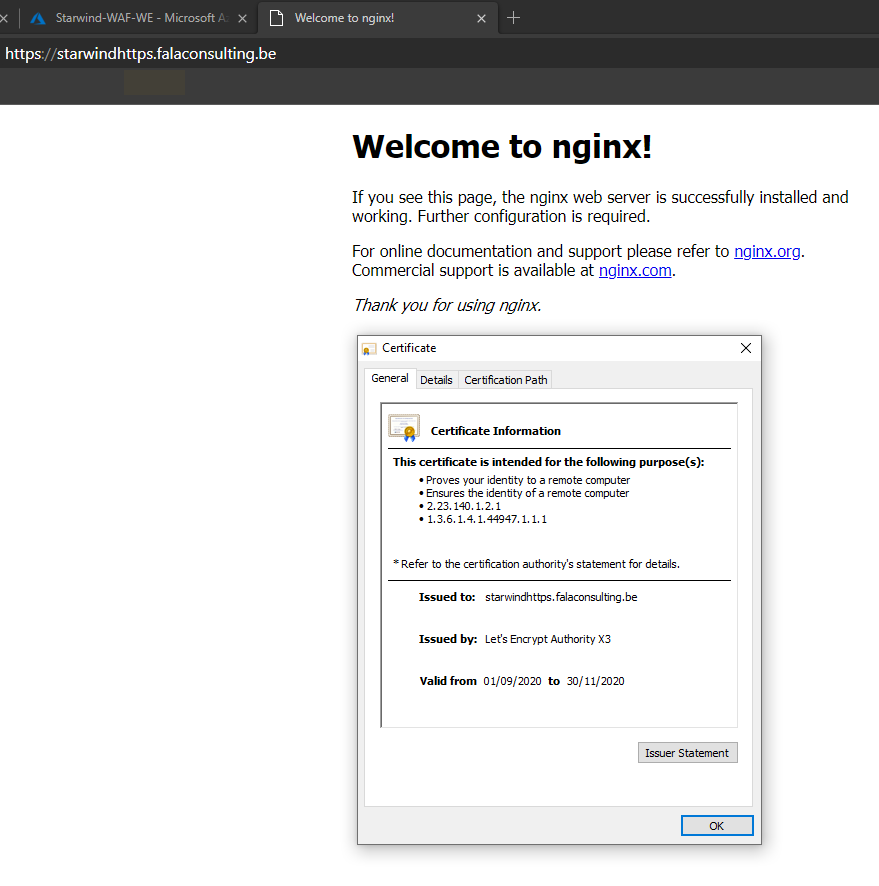
After some seconds, the certificate is requested, and deployed:
In the last part, we will see how to make this app, highly available