Passwords are arguably the weakest link in an organization’s cybersecurity posture. As a result, attackers continue to compromise business-critical networks using weak and otherwise compromised passwords. Passwordless authentication has been touted as a solution to these challenges for years. However, setting up passwordless authentication infrastructure has historically been complex and challenging.
Microsoft has been chipping away at this problem with various solutions and services introduced in Azure to support passwordless authentication. At Ignite, Microsoft announced Windows Hello for Business Hybrid Cloud Kerberos Trust to help with the complexity of passwordless authentication.
Why are passwords no longer good enough?
Passwords have been around for decades and are often the weakest link in the overall cybersecurity of most organizations. Why is that? Due to human nature, the passwords we choose are often weak, easily guessed, reused, and may even currently exist on a breached password list.
Generally speaking, most end users want to choose passwords they can remember, making it easier to access systems without needing password managers, copying and pasting passwords from other locations, and ease of access. However, attackers know this, and compromising account passwords are often the first step they take to breach business-critical networks.
In the IBM Cost of a Data Breach 2022 report, compromised credentials remain the most common cause of a data breach. Stolen or compromised credentials accounted for 19% of all data breaches in 2022. In addition, breaches caused by stolen or compromised credentials had an average cost of USD 4.50 million.
One of the other alarming characteristics of compromised credentials is they are often difficult to detect. As a result, breaches resulting from compromised credentials had the most extended breach lifecycle at 243 days to identify and another 84 days to contain the breach.
How does Windows Hello for Business help?
Windows Hello for Business provides a modern multi-factor authentication mechanism that is more secure than using passwords. It is also an authentication mechanism natively part of current Windows versions since Windows 10. In addition, it is exponentially more secure as it uses key-based authentication built on top of certificates.
How is Windows Hello for Business a multi-factor authentication mechanism? It combines something the end-user knows (PIN) or something the end-user is, their biometric information, with something they have, physical access to the device.
Using Windows Hello for Business is convenient. This aspect is something that many multi-factor authentication methods fail to deliver. In addition, complex end-user login processes and inconveniences often thwart multi-factor authentication adoption. Windows Hello for Business helps solve this problem and provides a seamless login experience.
Introduction of Kerberos authentication in Azure Active Directory (Azure AD)
In a previous blog post, which you can find here, we discussed the introduction of Kerberos authentication into Azure Active Directory (Azure AD) earlier this year. This new authentication capability is a major new feature of Azure Active Directory that opens up new and exciting scenarios.
Microsoft initially introduced Kerberos in Azure AD to access Azure File Shares configured for Azure AD authentication to allow certain use cases, such as allowing FSLogic interfaction with Azure File Shares. At that point, we knew Microsoft would undoubtedly use the new capabilities of Kerberos authentication in Azure AD for even more extended functionality.
As stated then, we knew Windows Hello functionality would be on the horizon:
“With the introduction of Kerberos in Azure AD, organizations can now have the best of both worlds with the extremely easy security solutions integrated with Azure AD, such as conditional access, Windows Hello, and other technologies. In addition, advanced security features that are complex and difficult to implement with on-premises AD DS are relatively easy to do in Azure AD, often amounting to a few checkboxes.”
It has now materialized with the introduction of Windows Hello for Business Hybrid Cloud Kerberos Trust.
What is Windows Hello for Business Hybrid Cloud Kerberos Trust
Microsoft has built upon the Kerberos authentication in Azure Active Directory (Azure AD) functionality and extended Windows Hello for Business to hybrid deployments, significantly reducing the complexity of deploying Windows Hello for Business.
It is now much easier to deploy than the previous key and certificate trust deployment models. In addition, it removes the need for the often complicated public key infrastructure (PKI) and Azure AD Connect synchronization requirements. Instead, Windows Hello for Business Hybrid Cloud Kerberos Trust uses an infrastructure already introduced in Azure to support hybrid Azure AD-joined devices with on-premises resources.
It provides the following benefits:
- No PKI requirements
- No Azure AD Connect synchronization dependency – This was previously required for writing back the public keys to Active Directory
- No device write-back requirement. This requirement is only applicable to certificate trust deployments
- No Active Directory Federation Services (AD FS) deployment requirement. Again, this requirement is only applicable to certificate trust deployments
As you may have noted above, it does not require Active Directory Certificate Services (ADCS). Active Directory Certificate Services has typically been a daunting, poorly understood, and difficult-to-implement solution for businesses who may not have the skillsets in-house to do so. Instead, with Windows Hello for Business Hybrid Cloud Kerberos Trust, businesses only need to ensure they are running Windows Server 2016 or higher domain controllers at each site and they are running hybrid, or Azure AD joined devices.
Note the following high-level look at the logon process architecture:
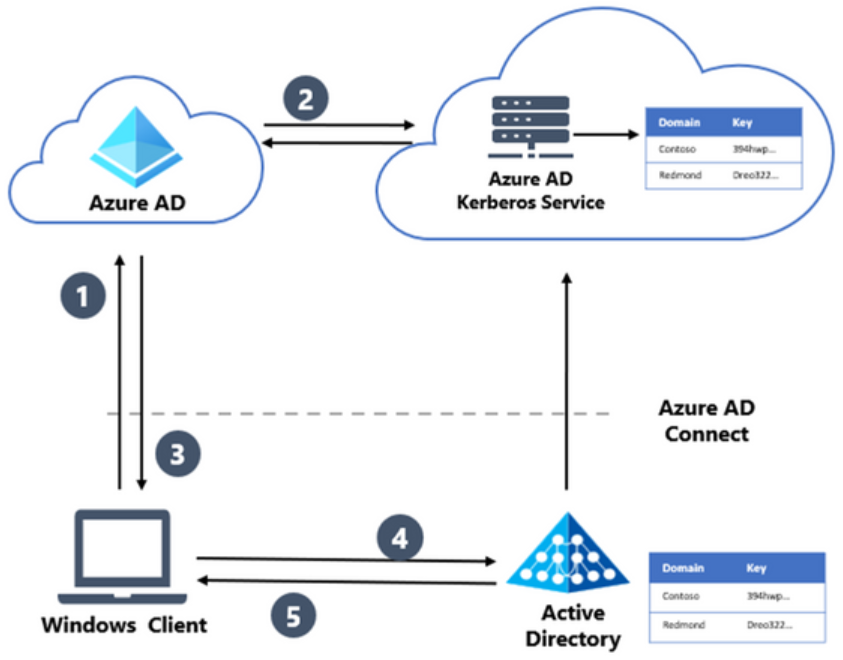 Hybrid cloud Kerberos trust using Azure AD Kerberos for key trust deployment
Hybrid cloud Kerberos trust using Azure AD Kerberos for key trust deployment
Let’s look at an overview of the logon process from an end-user perspective:
- The user signs into Windows with Windows Hello for Business by authenticating with Azure AD
- When the user signs into Azure AD, it checks for a Kerberos server key and matches the on-premises AD domain, generating a partial Kerberos ticket-granting ticket (TGT) for the on-premises domain. The partial TGT contains only the user security identifier (SID) and no authorization data. An example of this would be their group memberships.
- The partial TGT returns to the client with an Azure AD Primary Refresh Token (PRT)
- The client contacts an on-premises Active Directory Domain Services (ADDS) domain controller and exchanges the partial TGT for a full TGT. This protocol flow is the same flow used today for a Read Only Domain Controller login process
- The client now has the Azure AD PRT and a full Active Directory TGT completing the login process with the new Windows Hello for Business Hybrid Cloud Kerberos Trust model
Prerequisites
Multi-factor Authentication – You can use Azure AD multi-factor authentication, multi-factor authentication provided through AD FS, or a comparable solution.
Patched Windows 10, version 21H2, or patched Windows 11 and later – Windows 10 21H2 needs KB5010415 installed. If you’re using Windows 11 21H2, KB5010414 must be installed. There’s no Windows version support difference between Azure AD-joined and Hybrid Azure AD-joined devices.
Fully patched Windows Server 2016 or later Domain Controllers – Domain controllers should be fully patched to support updates needed for Azure AD Kerberos. If you’re using Windows Server 2016, KB3534307 must be installed. If you’re using Server 2019, KB4534321 must be installed
Azure AD Kerberos PowerShell module – This module is used for enabling and managing Azure AD Kerberos, and it’s available through the PowerShell Gallery
Device management – Windows Hello for Business cloud Kerberos trust can be managed with group policy or through mobile device management (MDM) policy, and it is disabled by default/must be enabled using policy.
Scenarios that are unsupported
- You can’t use it with on-premises-only deployments
- RDP or VDI scenarios using supplied credentials – RDP or VDI can be used with Remote Credential Guard or if a certificate is enrolled into the Windows Hello for Business container
- You can’t use the solution if you require a certificate for authentication
- This authentication method can’t be used for “Run as” operations with cloud Kerberos trust
- Signing in with cloud Kerberos trust on a Hybrid Azure AD joined device without previously signing in with DC connectivity
Wrapping Up
The new Windows Hello for Business Hybrid Cloud Kerberos Trust will be a giant leap forward for organizations looking to introduce strong multi-factor authentication for users. It helps businesses forego the complexities of standing up on-premises certificate services infrastructure for certificate-based authentication.
Windows Hello for Business Hybrid Cloud Kerberos Trust allows businesses to use Windows Hello, which requires something the user knows or is (PIN or biometrics) with something they have (physical access to the machine). You can learn more about the Hybrid Cloud Kerberos Trust Deployment steps here:


