In previous article (How to start with Azure Virtual Desktop) we deployed a host pool using Active Directory.
In a case where you don’t have Active Directory, but only Azure AD, it is possible to do a domain join for an AVD, to this Azure AD. Some known limitations are present: Deploy Azure AD joined VMs in Azure Virtual Desktop – Azure | Microsoft Docs
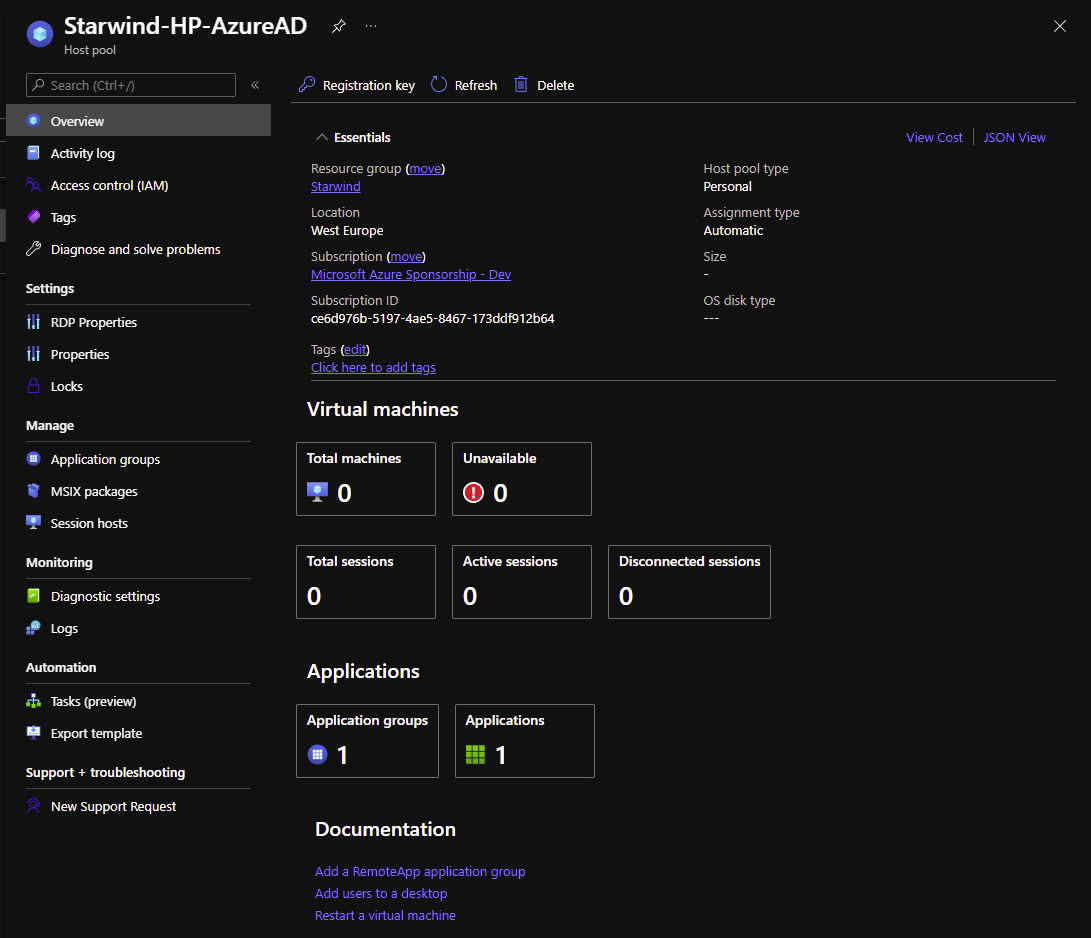
Let’s start by adding a new host pool, dedicated for this tutorial:
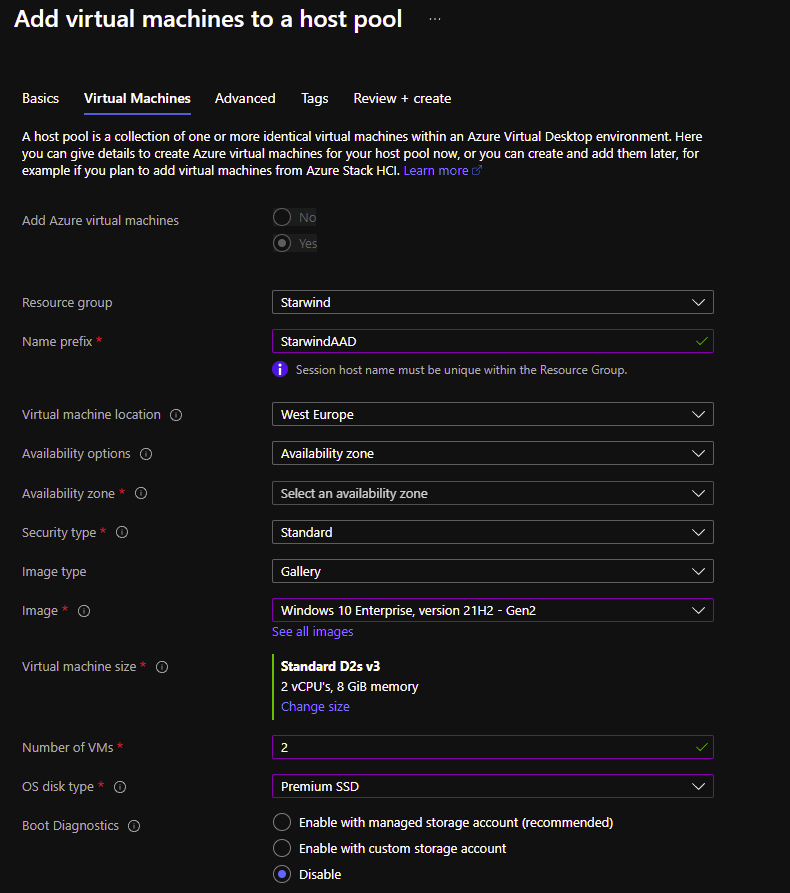
We will now add a new virtual machine to this host pool:
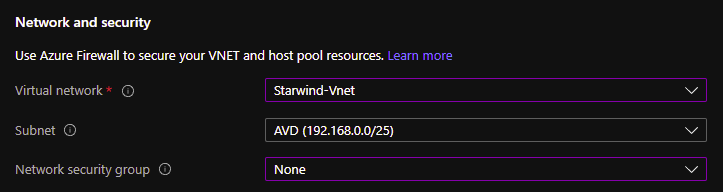
Choose the VNet part:
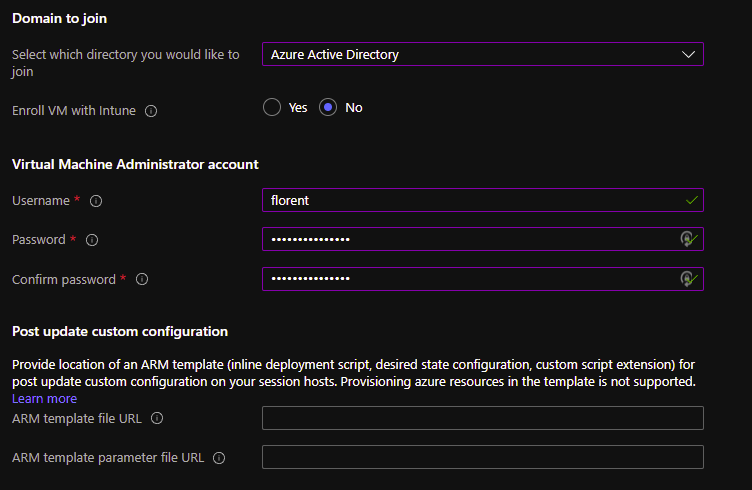
And the most important part, the domain join. Choose Azure AD instead of Active Directory. You can enroll the VM if you need, to manage software, etc. in the VM.
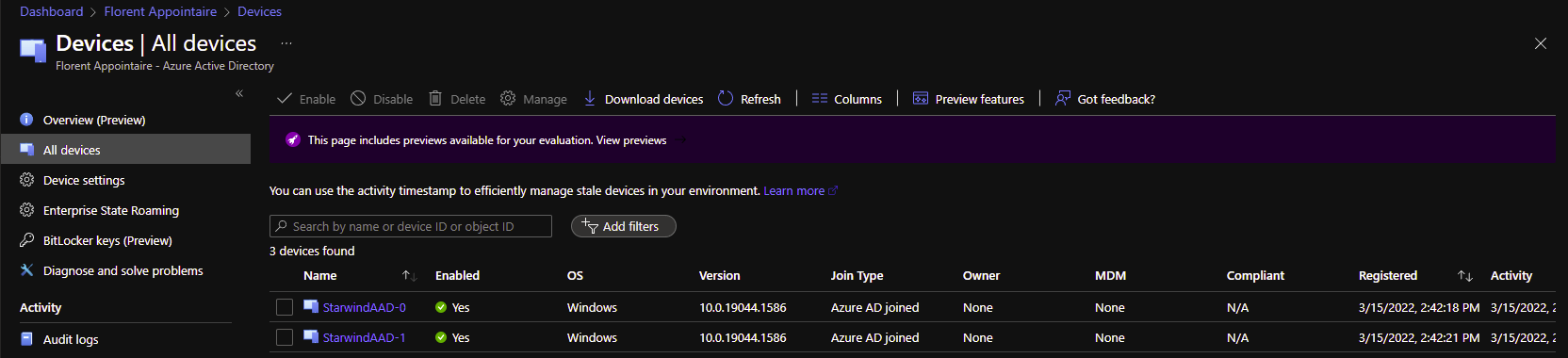
The deployment is finished and VM are Azure AD join:
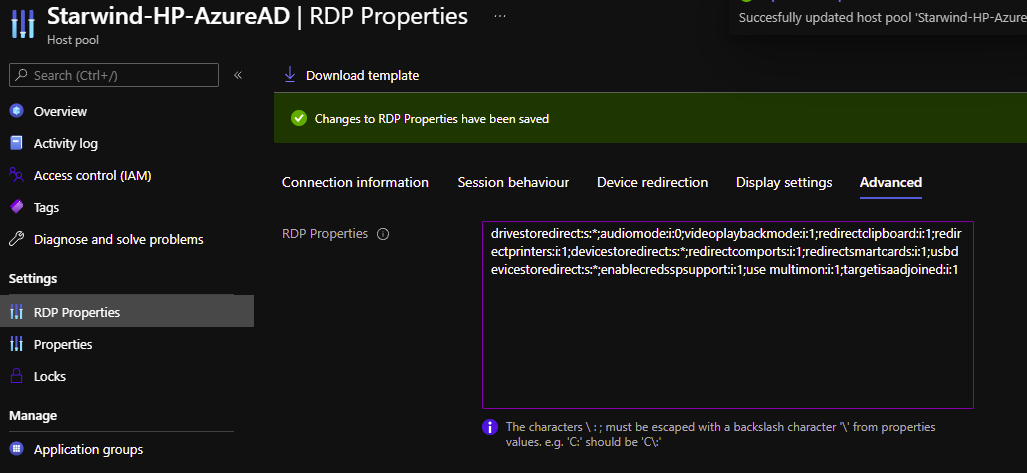
Now, edit the RDP properties of your host pool and, in advanced, add targetisaadjoined:i:1
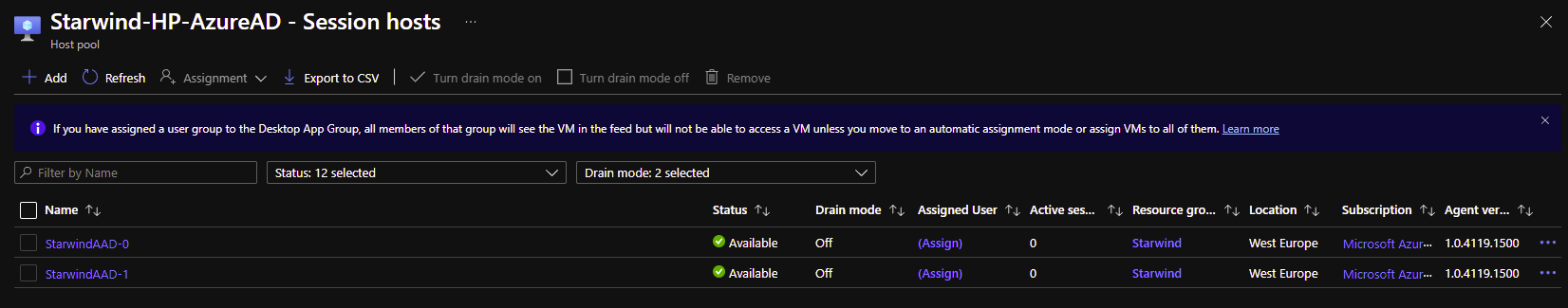
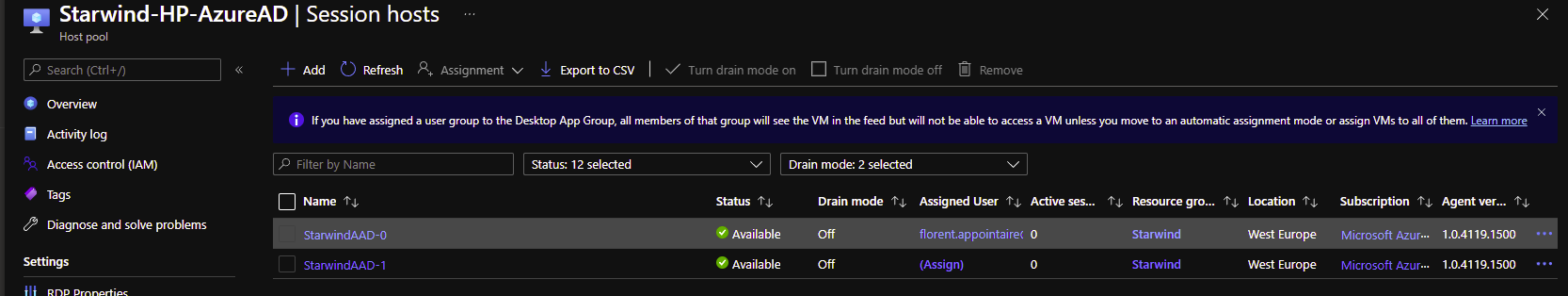
After few minutes, we can now see that the 2 hosts are up:
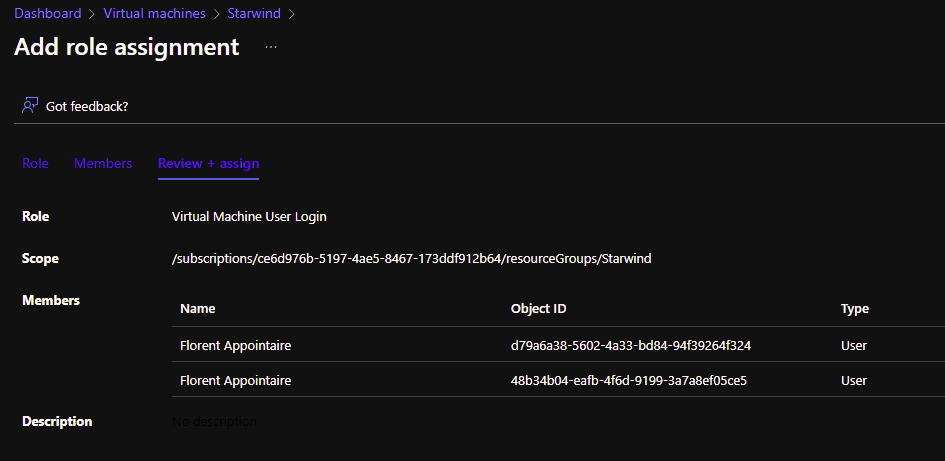
Now that AVD session hosts are up and running, we need to add more permissions before trying to login. On each session host, you need to add accounts/groups that need to connect to this host pool, as Virtual Machine User Login in Azure RBAC. I will add this right at the resource group level:
I will try to connect to https://rdweb.wvd.microsoft.com/arm/webclient
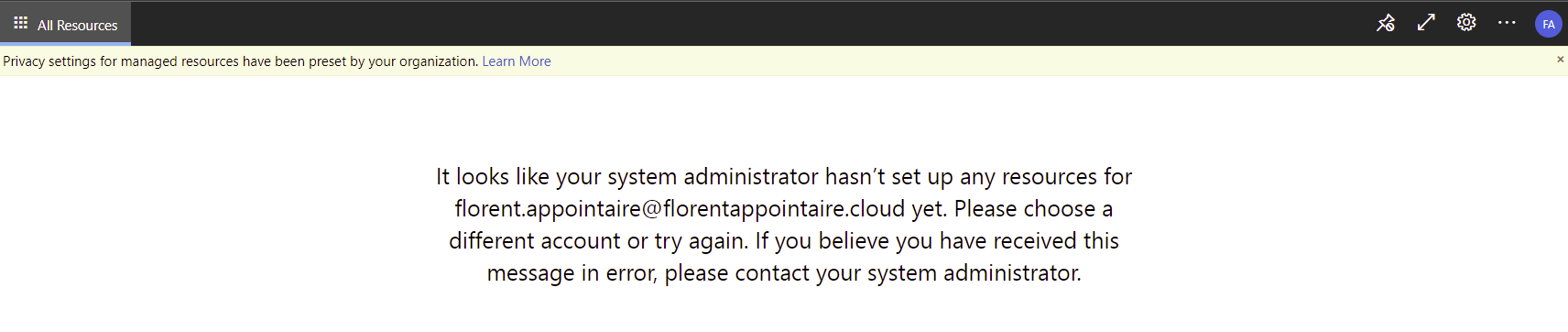
I have the following error:
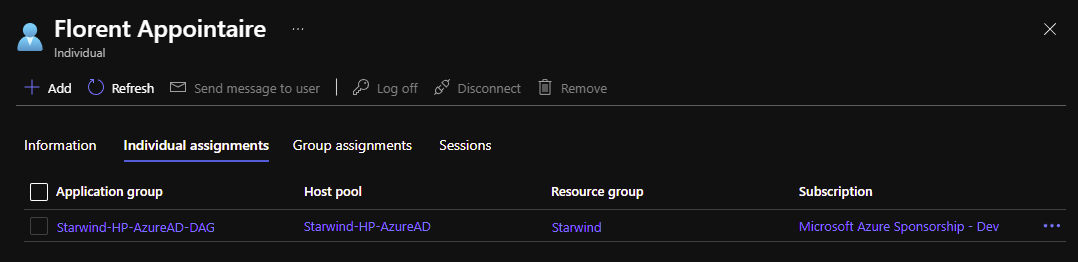
I need to assign a session host to this user:
And after, I can assign this user to a VM:
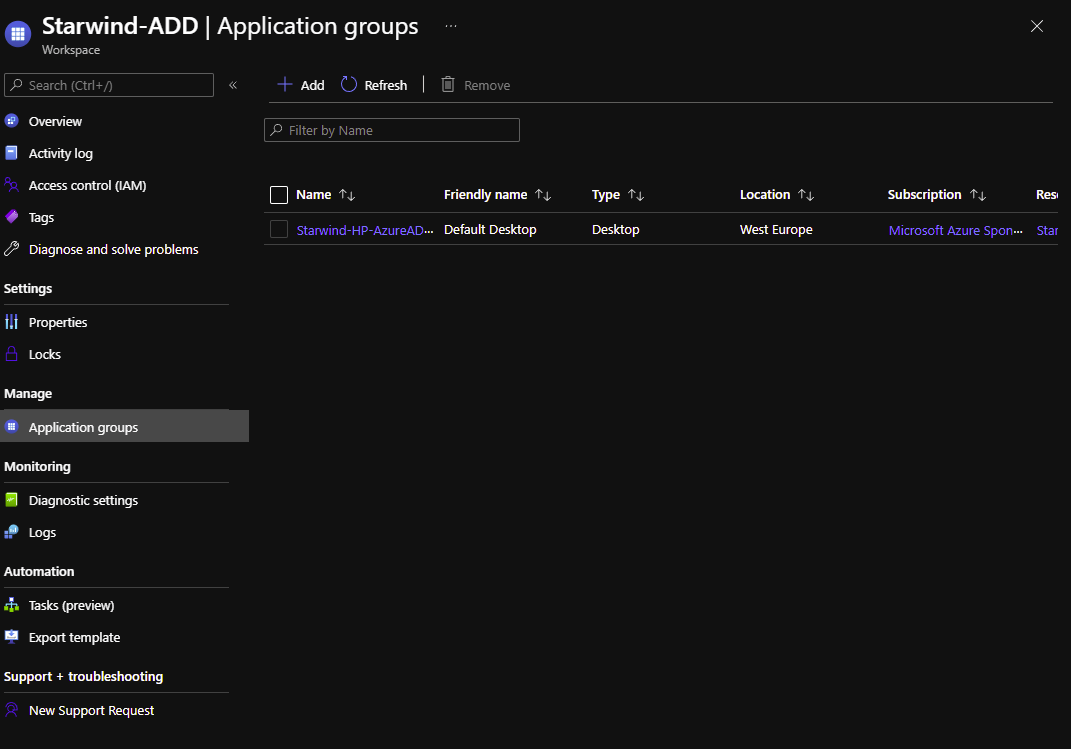
And create a workspace associated to this Application group:
I can now see the application:
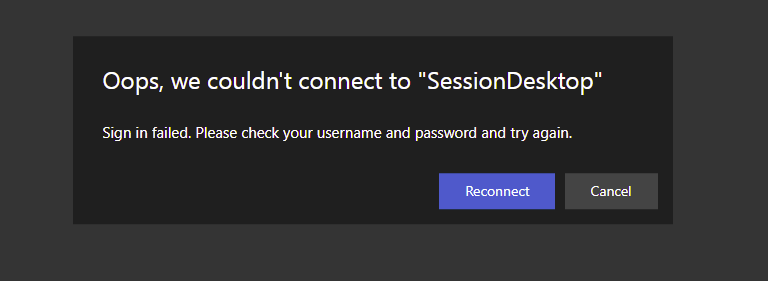
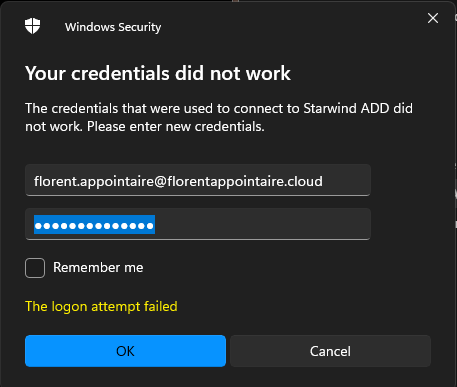
If I try to connect, I have the following error:
Same issue with the fat client:
It is a normal error. I’m using per-assigned MFA. To start, we will create a new conditional policy, based on the following article:
Azure multifactor authentication for Azure Virtual Desktop – Azure | Microsoft Docs
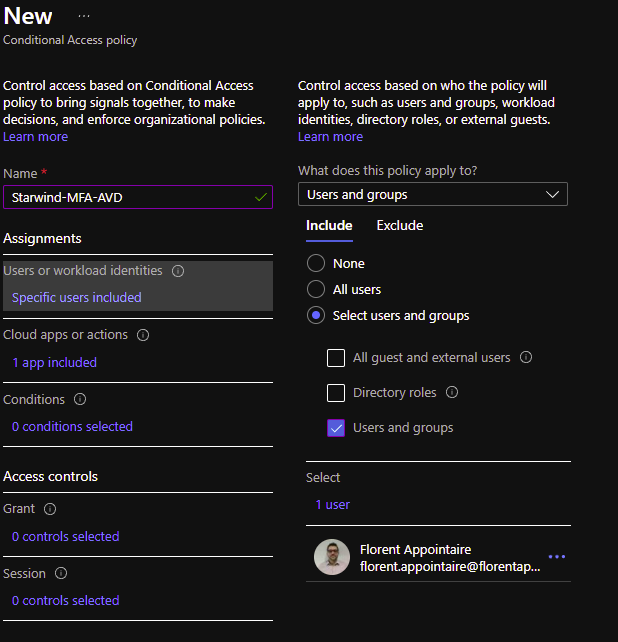
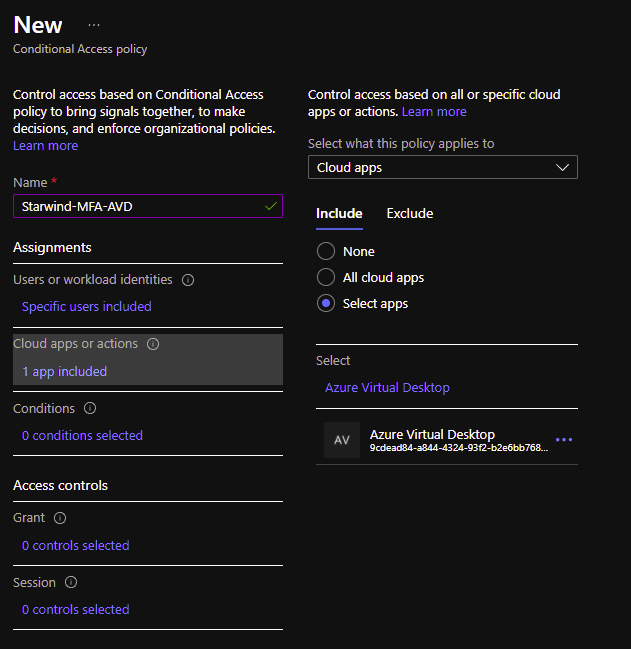
Go to Conditional Access – Microsoft Azure and create a new policy. Assign this policy to a group, a user or all users:
Select an app for which it will be applied, in this case the Azure Virtual Desktop one, with the id 9cdead84-a844-4324-93f2-b2e6bb768d07:
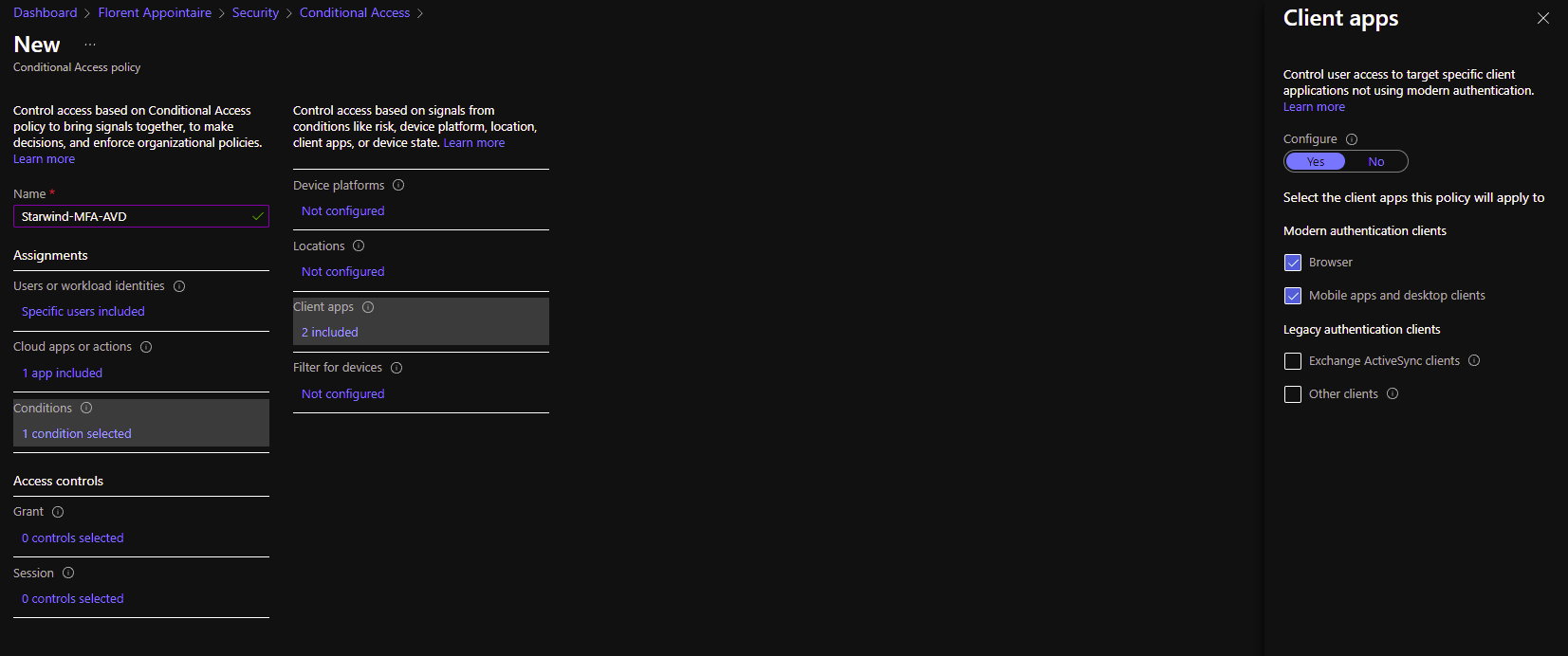
In the Conditions, select to which client app we need to apply this:
For the control, select Grant access and check the box Require multi-factor authentication:
In session, I will tell that we need to reauthenticate with MFA every 15 days:
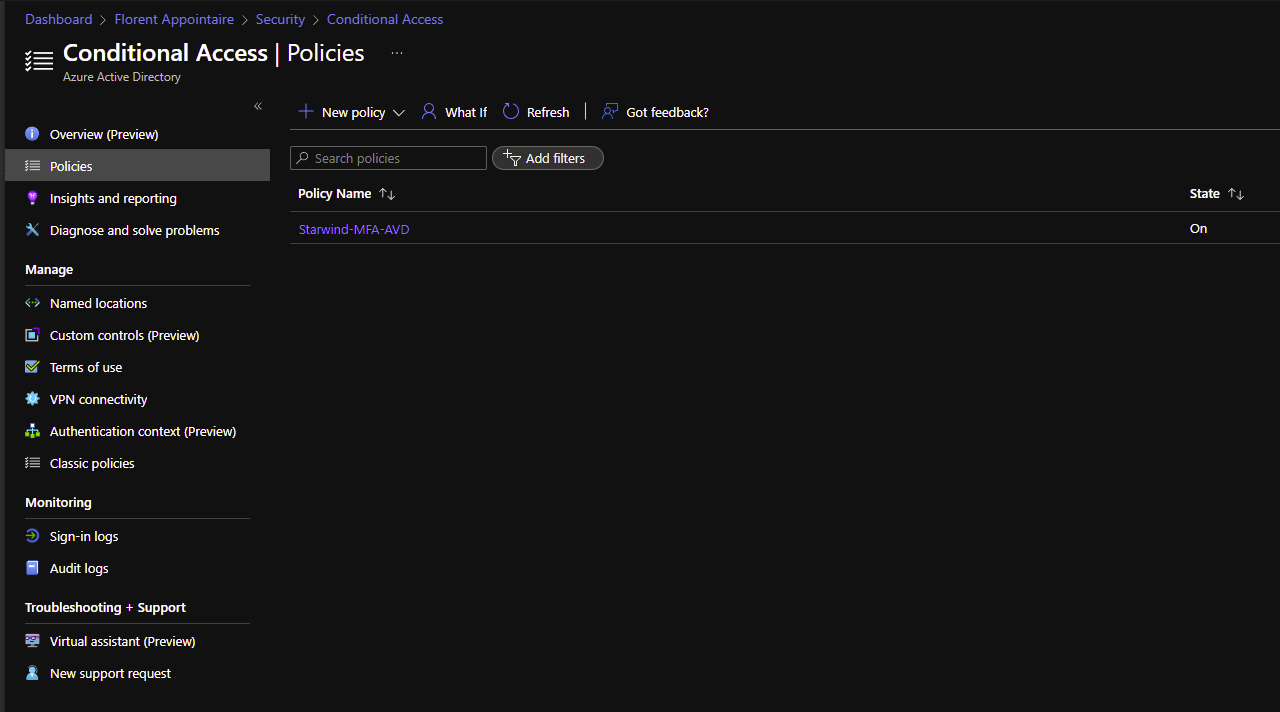
Enable the policy and save it:
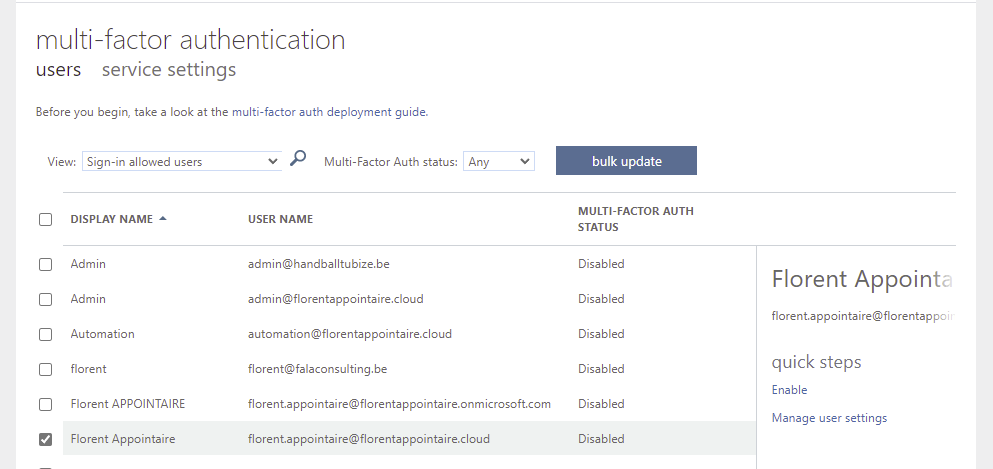
Now, go to your users in Azure AD and click on Per-User MFA. On the new tab, disable the MFA for the users that you want to allow the connection to AVD:
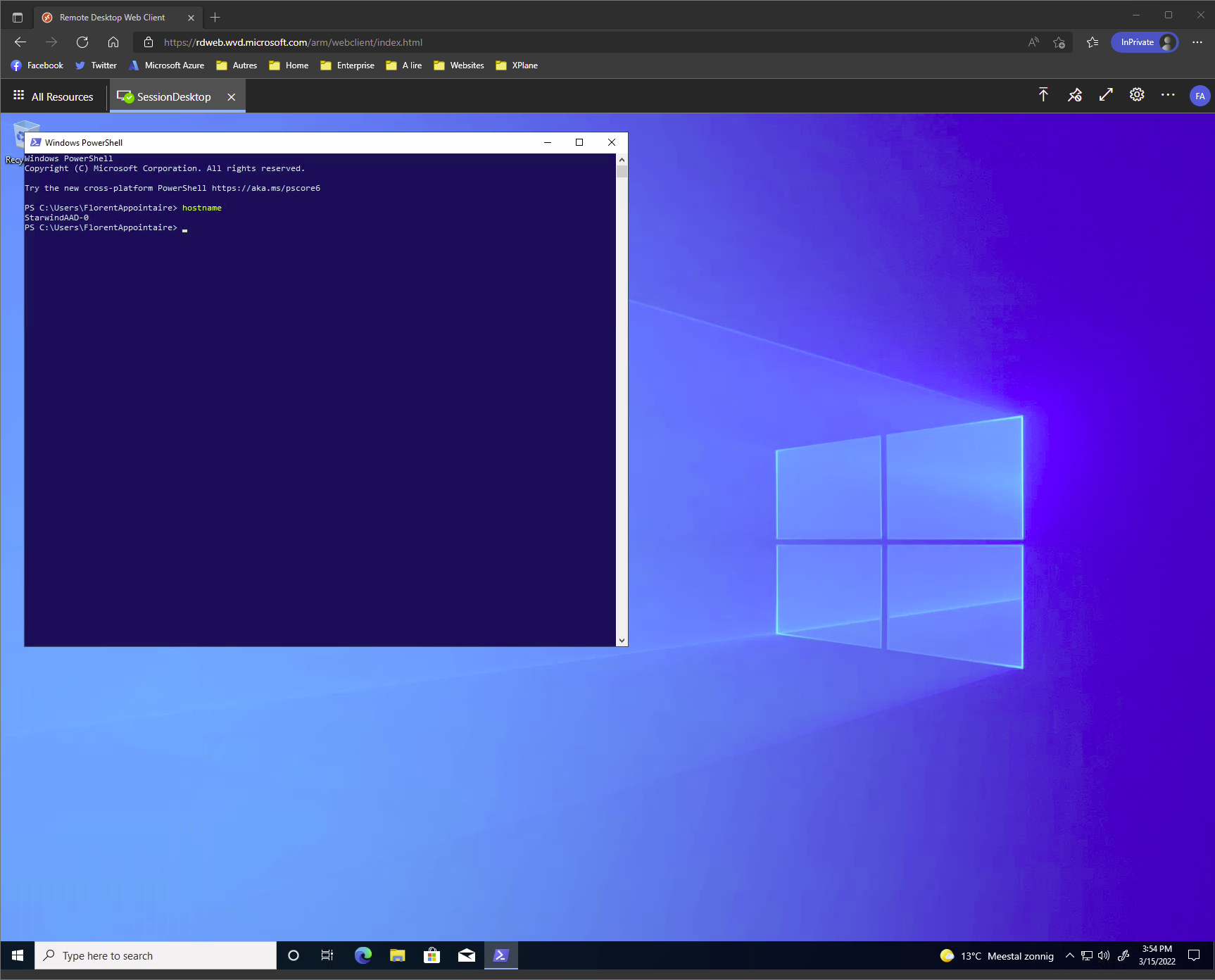
Reconnect to the web interface. You need to login with your account and the MFA. And for the SessionDesktop, it now works:
As you can see, if you have only cloud based directory (Azure AD), you can use Azure Virtual Desktop, in combination with Intune/Conditional Access, to do not deploy an Active Directory only to join a domain and connect with a domain account.