When the AD FS SSL certificate of your Office 365 infrastructure is about to expire, you need to update the AD FS SSL certificate accordingly to avoid services disruption.
During the configuration of the Office 365 environment you need to install an SSL certificate to establish a secure communication between Office 365 components. To easily update the SSL certificate for both AD FS and WAP Servers you can use the Azure AD Connect tool. This procedure works also if the user sign-in method is not AD FS.
The overall procedure can be summarized as follows:
Prerequisites
To successfully update the SSL certificate, you need to meet the following prerequisites:
- AD FS – the AD FS infrastructure should be Windows Server 2012 R2 or later.
- Azure AD Connect tool – the Azure AD Connect version must be 1.1.553.0 or higher.
Update AD FS SSL certificate
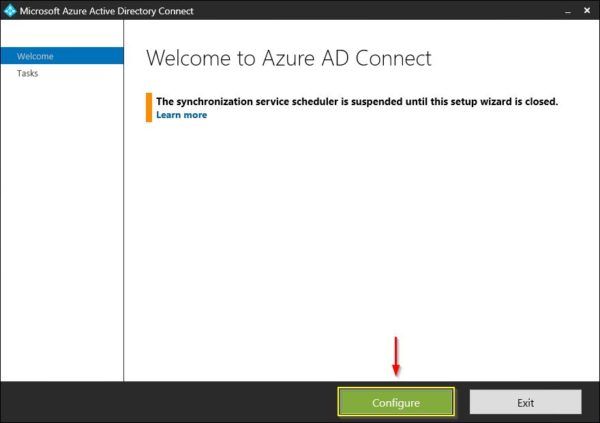
Open the Microsoft Azure Active Directory Connect tool and click Configure. Keep in mind that during this configuration time the synchronization service scheduler will be suspended.
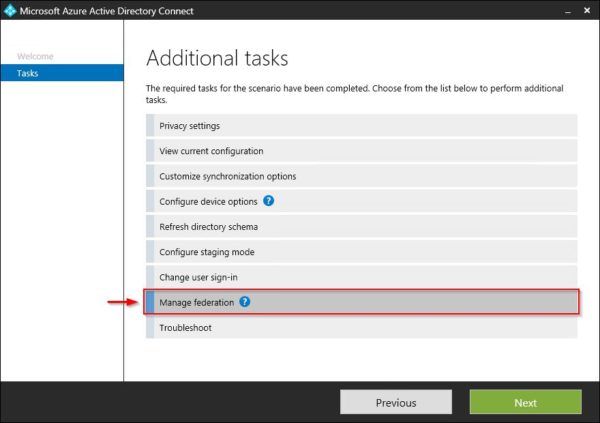
From the Tasks section, select Manage federation then click Next.
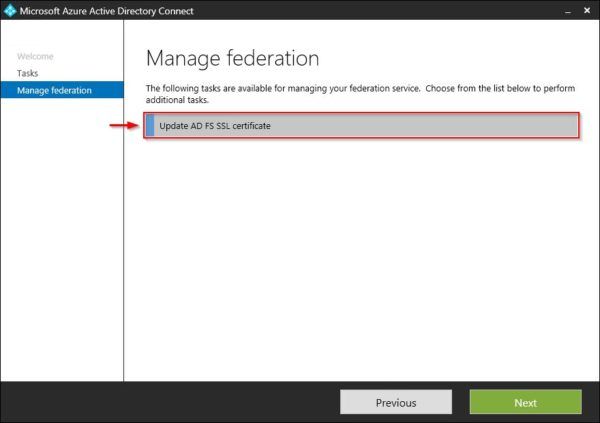
Select Update AD FS SSL certificate option and click Next.
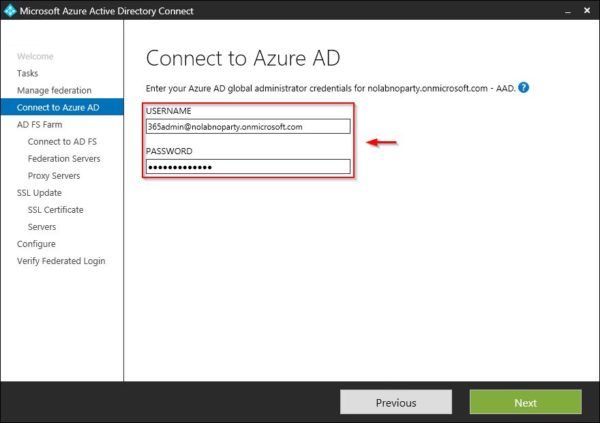
Enter the Office 365 Administrator credentials and click Next.
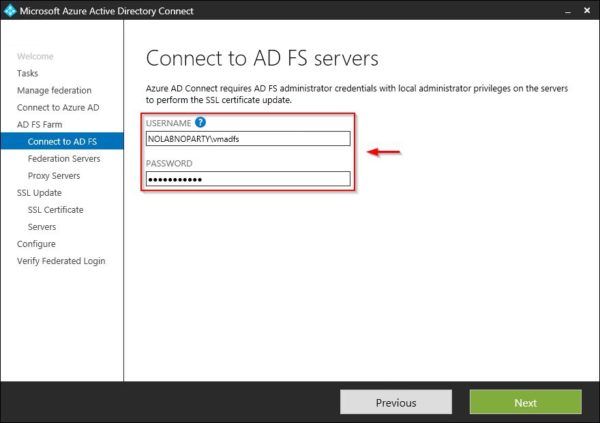
Now enter the credentials of the account with local administrator privileges in the AD FS server and click Next.
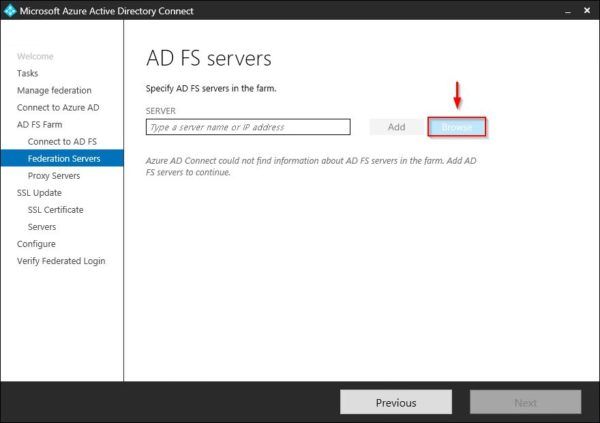
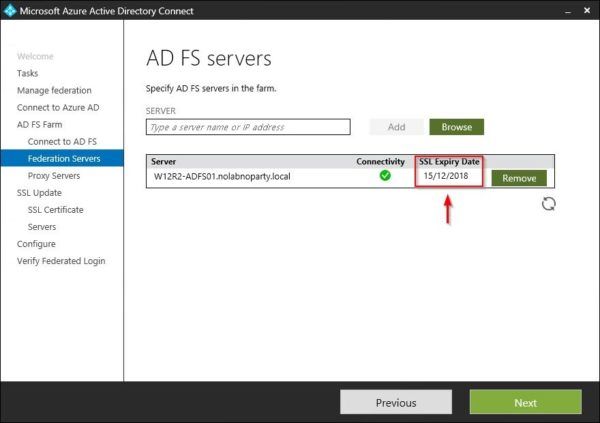
Click Browse to search for AD FS servers in your network.
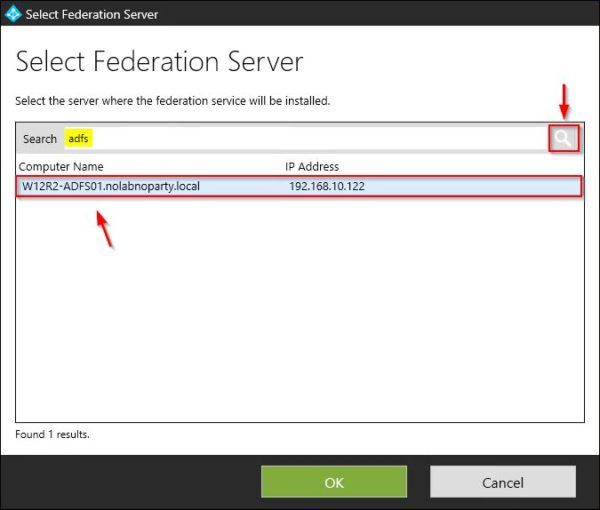
Enter a string to identify the AD FS Servers and click on the Search button. Select the required servers then click OK.
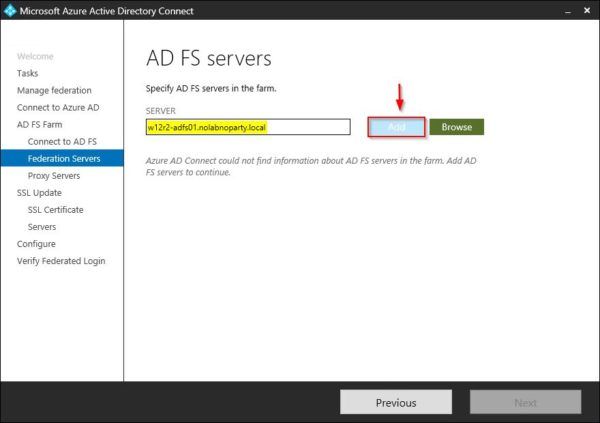
Alternatively you can specify the required AD FS server in the SERVER field and click Add.
To delete servers in the list no longer part of the AD FS infrastructure (they are indicated with a yellow exclamation mark), click on Remove button. Click Next to continue.
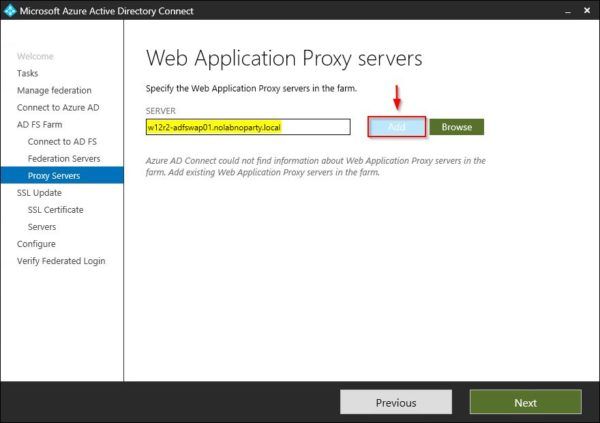
Enter the WAP Server to connect and click Add or click Browse to search for WAP Servers in your network.
Since the WAP Server in the example resides in the DMZ and is not joined to domain, a local account in the WAP Server has to be specified to establish the connection.
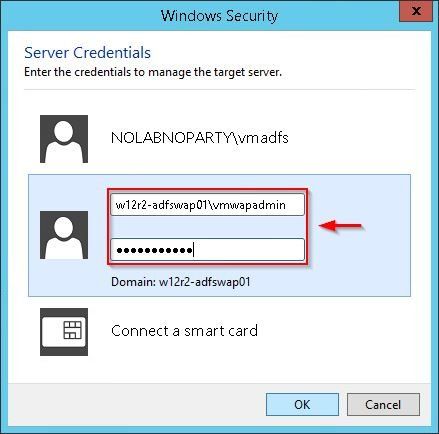
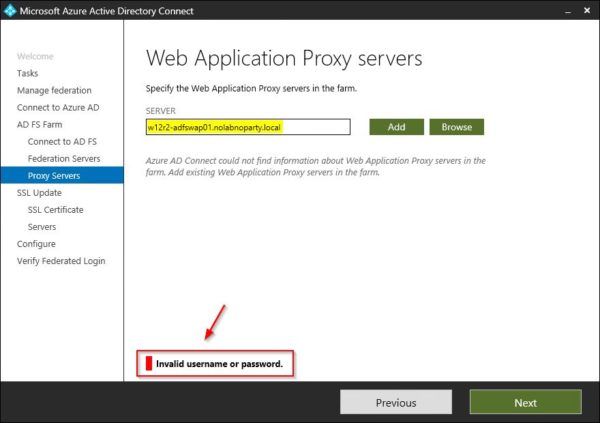
If you are not able to establish a connection with the WAP Server or you receive Invalid username or password error message, you need to do some additional tasks.
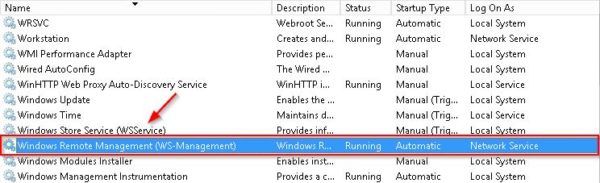
If the WAP Server is not joined to domain, first ensure the service Windows Remote Management (WS-Management) is running in the WAP Server.
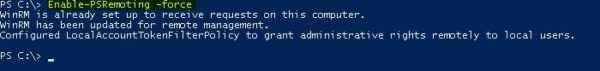
From the WAP Server’s PowerShell command window, run the following command:
PS C:\> Enable-PSRemoting –forceNow access the server where the Azure AD Connect tool is installed and run the following PowerShell command:
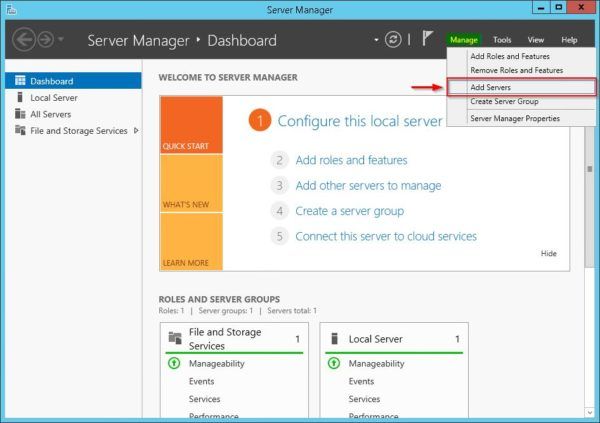
PS C:\> Set-Item WSMan:\localhost\Client\TrustedHosts –value <WAPServerFQDN> -force –concatenateOpen the Server Manager and add DMZ WAP host to machine pool selecting Manage > Add Servers from the menu.
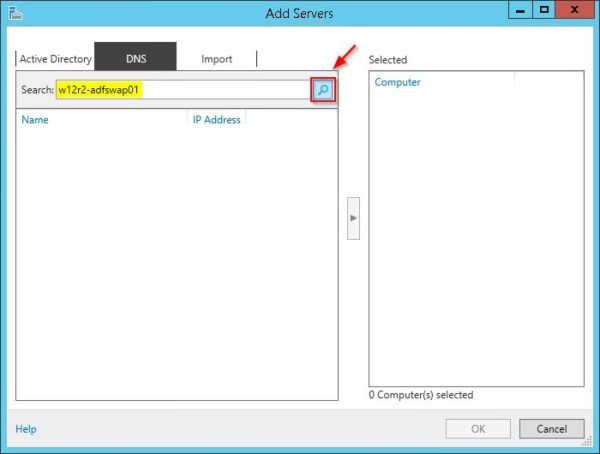
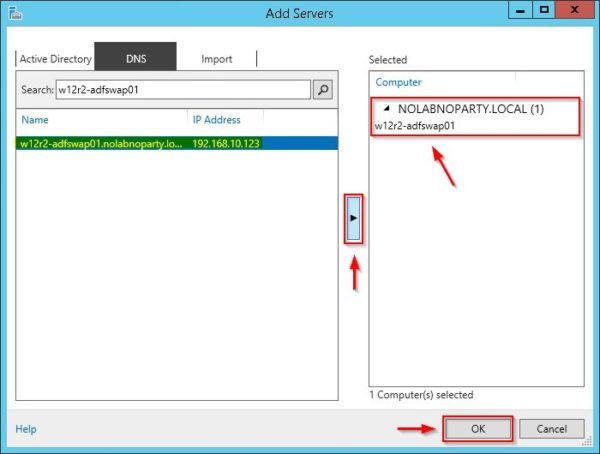
Go to DNS tab and enter the WAP server name or IP address in the Search field then click on Search icon.
Select the required WAP Server and click the Add icon. Click OK to confirm.
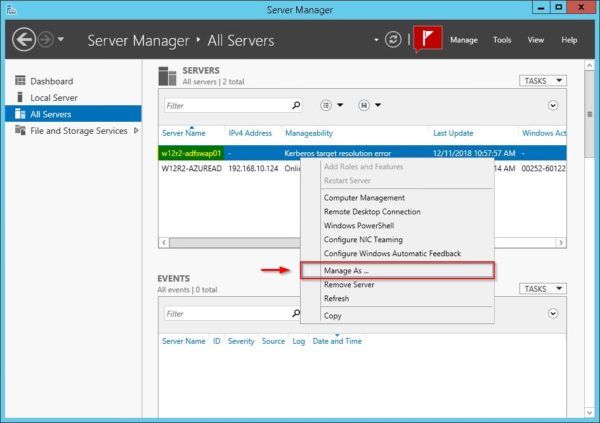
Right click the added WAP Server and select Manage as option.
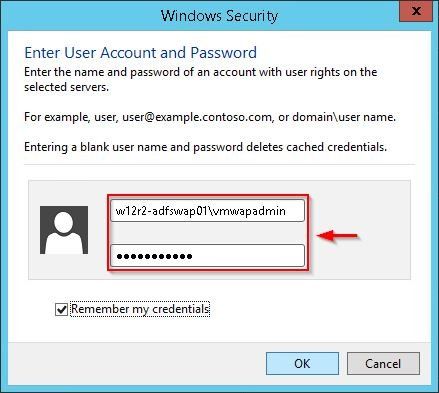
Enter the local credentials of the WAP Server to access the machine.
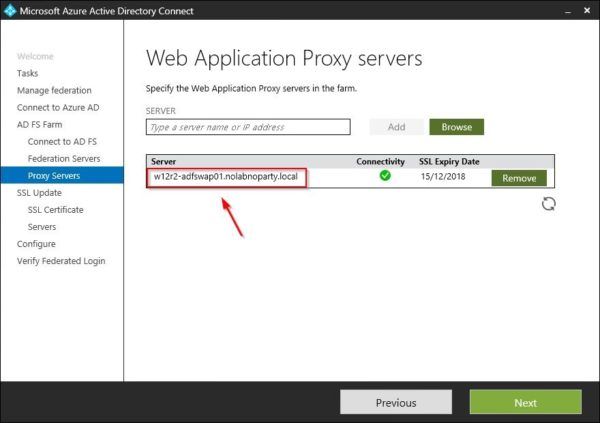
From the Azure AD Connect tool try to add the WAP Server once again. This time the connection is established successfully. Click Next to continue.
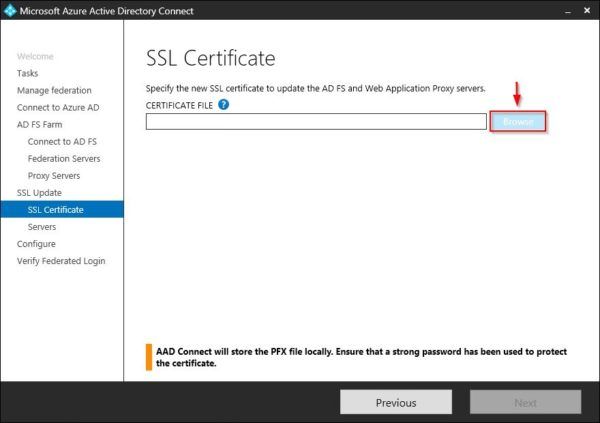
Click on Browse and select the certificate file to use. To avoid problems, the used certificate must meet the following prerequisites:
- the subject name is either the same as the federation service name
- it is valid for more than 30 days
- the trust chain is valid
- it is password protected
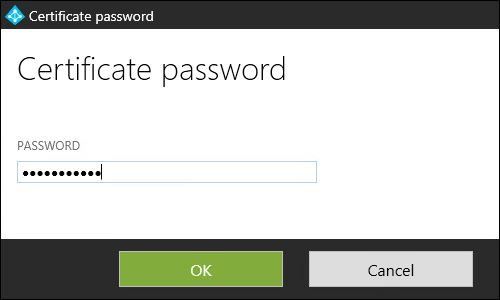
Enter the password used to export the certificate then click OK.
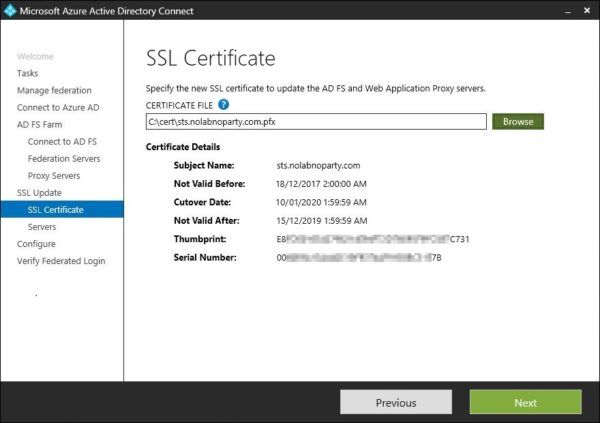
Details of the selected certificate are displayed. Click Next.
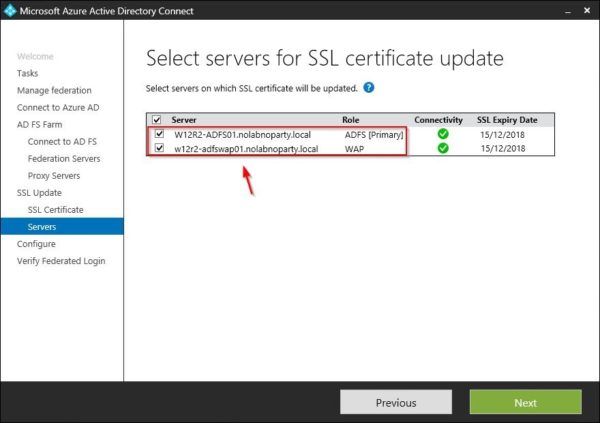
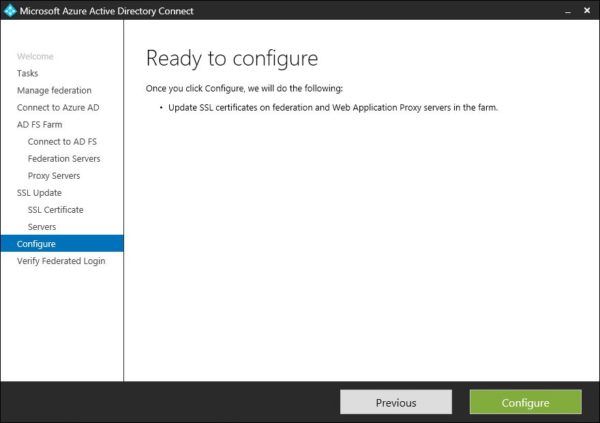
Select servers for SSL certificate update then click Next.
Click Configure to proceed with the configuration.
The SSL certificate is being installed on selected servers.
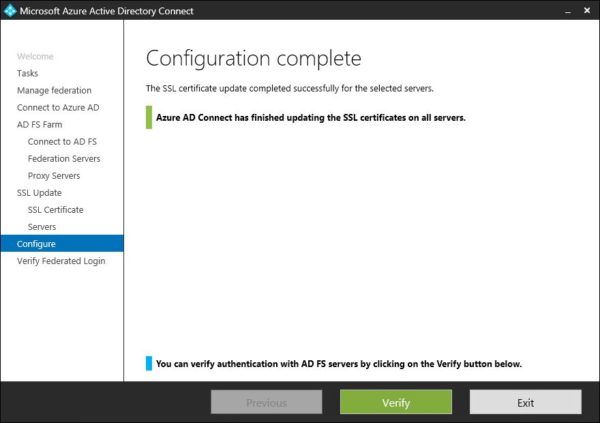
When the configuration has been completed successfully, you can click the Verify button to verify the AD FS sign-in or click Exit to close the wizard.
The SSL certificate used in your Office 365 infrastructure has been updated successfully.