Some web services don’t include an authentication feature such as a form or SSO. When these web applications are accessible from the Internet through Kemp, it’s a huge security issue. To solve that, Kemp provides ESP (Edge Security Pack).
Thanks to ESP, an authentication form is presented to clients before accessing the web applications.
The Kemp ESP provides the following features (copied from Kemp documentation):
- End point authentication for pre-authentication
- Persistent logging and reporting for user logging
- Single Sign-On (SSO) across Virtual Services
- LDAP Authentication from the LoadMaster to the Active Directory
- Basic authentication communication from a client to the LoadMaster
- Dual-factor authentication
In this topic, we’ll see how to configure ESP on a virtual service and how to allow only users that belong to an Active Directory Group.
Active Directory configuration
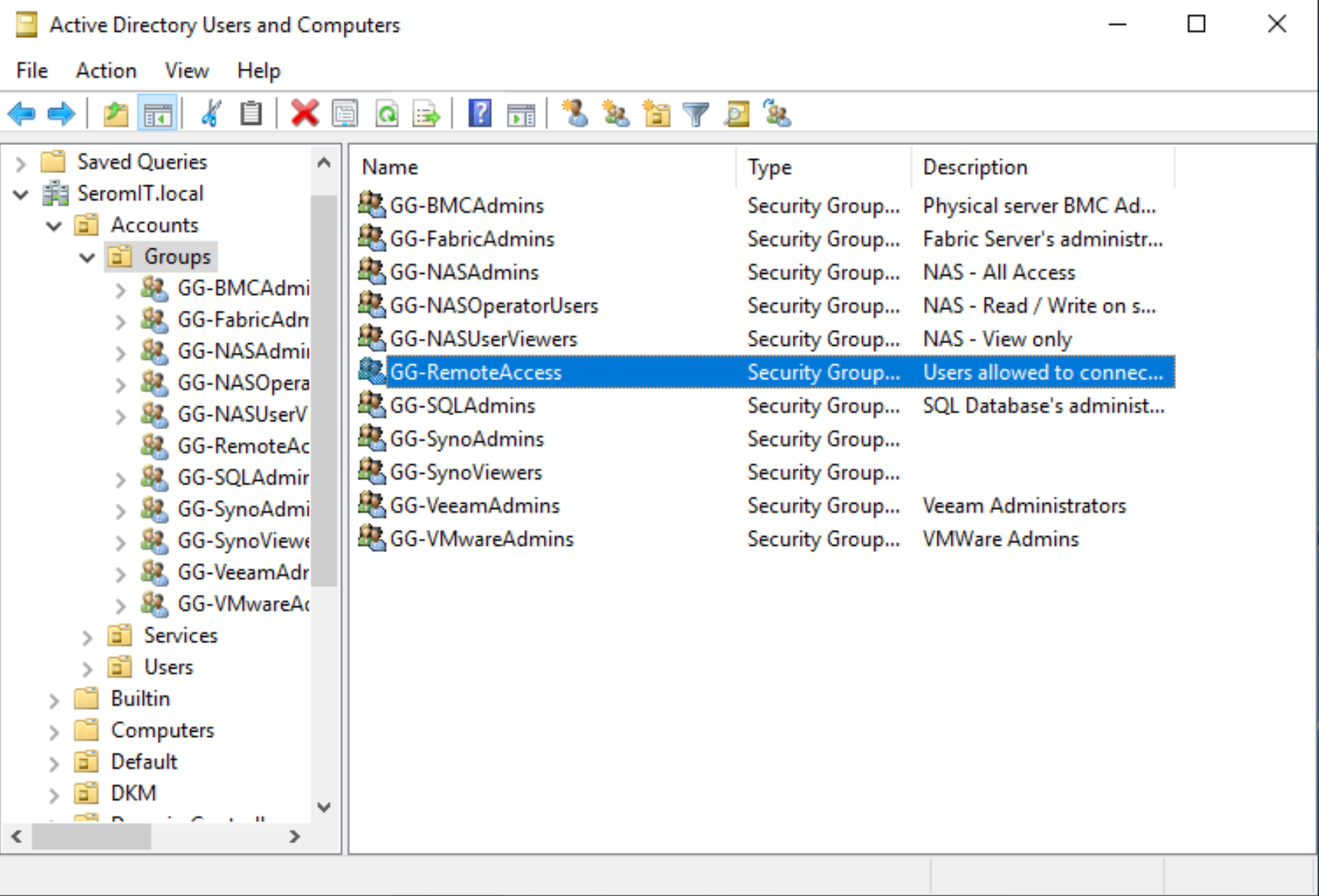
In my domain SeromIT.local, I’ve created a group called GG-RemoteAccess. It’s a usual global security group. You can create a specific group for each Kemp virtual services to manage applications access from Active Directory.
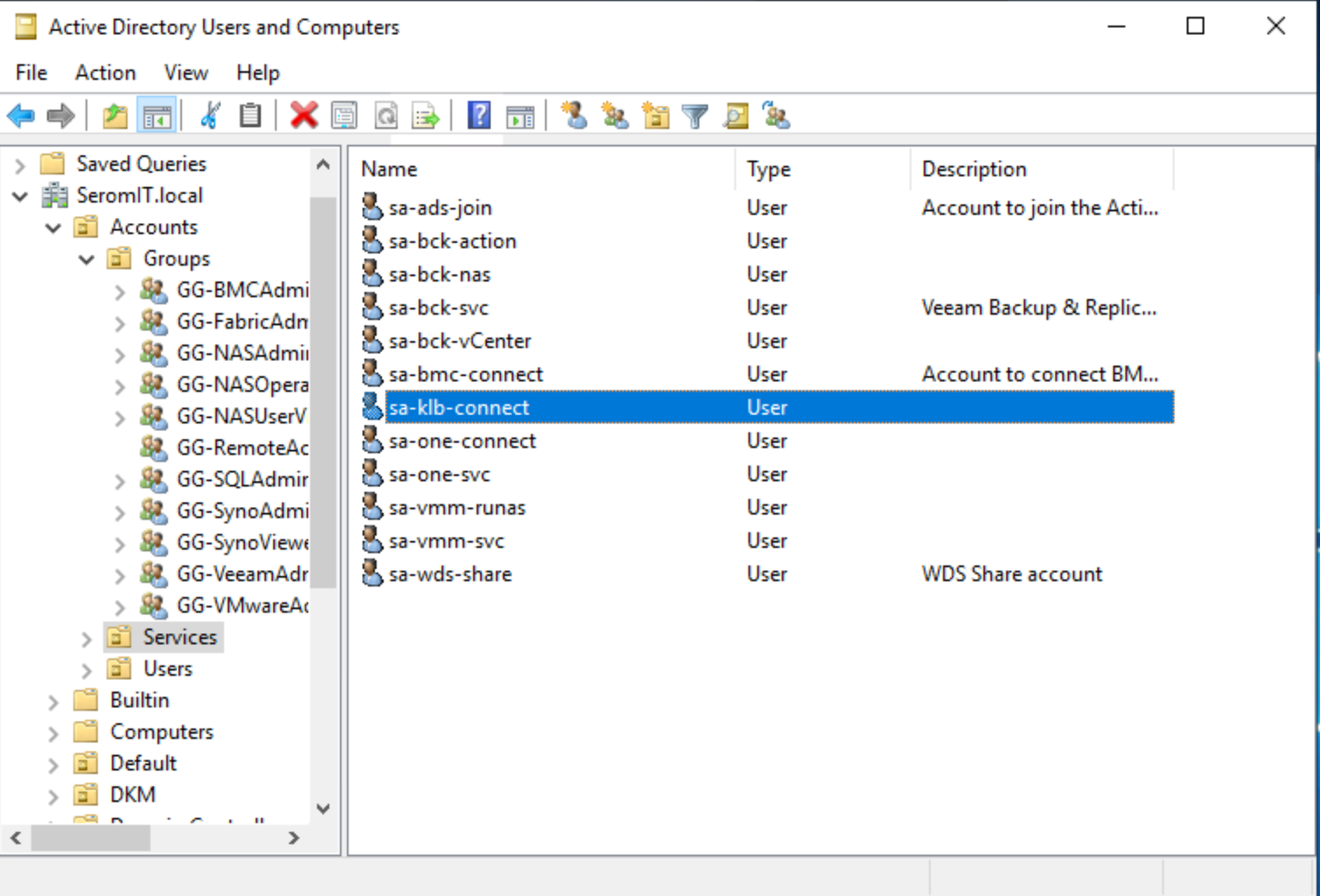
Create also a user account with classic user permissions to allow Kemp to parse the Active Directory. I called my account sa-klb-connect.
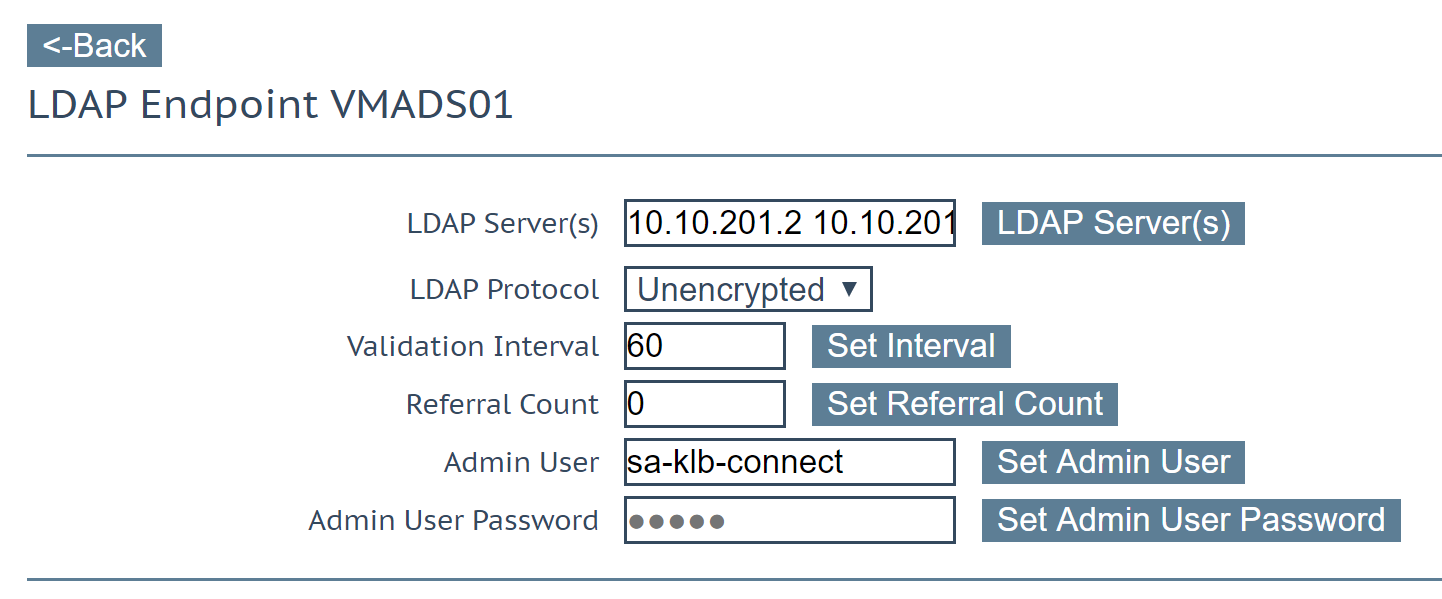
Configure Kemp LDAP endpoint
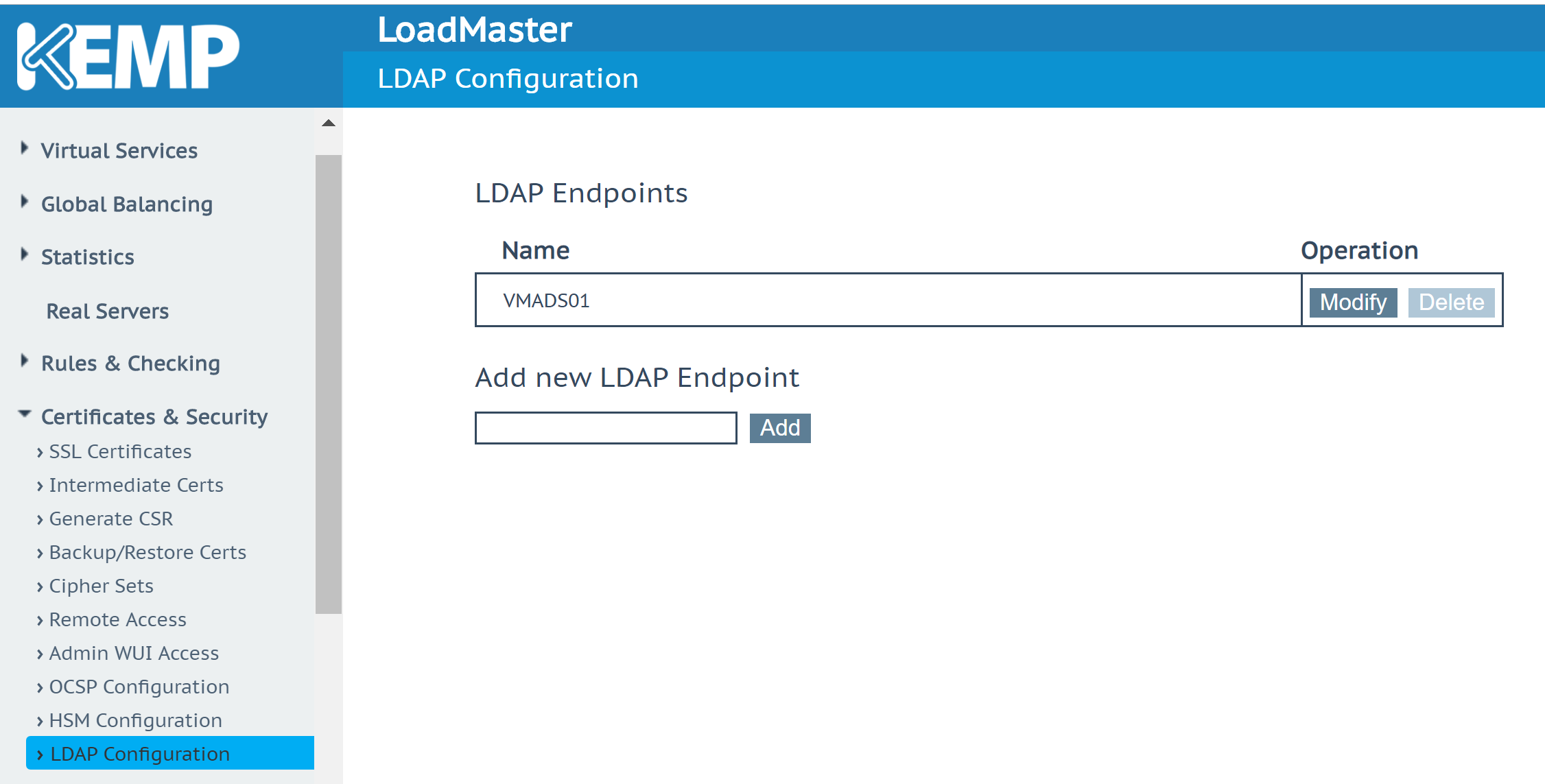
Connect to Kemp LoadMaster GUI and navigate to Certificates & Security | LDAP Configuration. In Add new LDAP Endpoint field, provide a name and click on Add.
In LDAP Server(s) field, provide Domain Controller IP addresses separated by space. If you want to connect to Active Directory through SSL, configure LDAP protocol. Then specify the AD account that you have previously connected to parse the Active Directory.
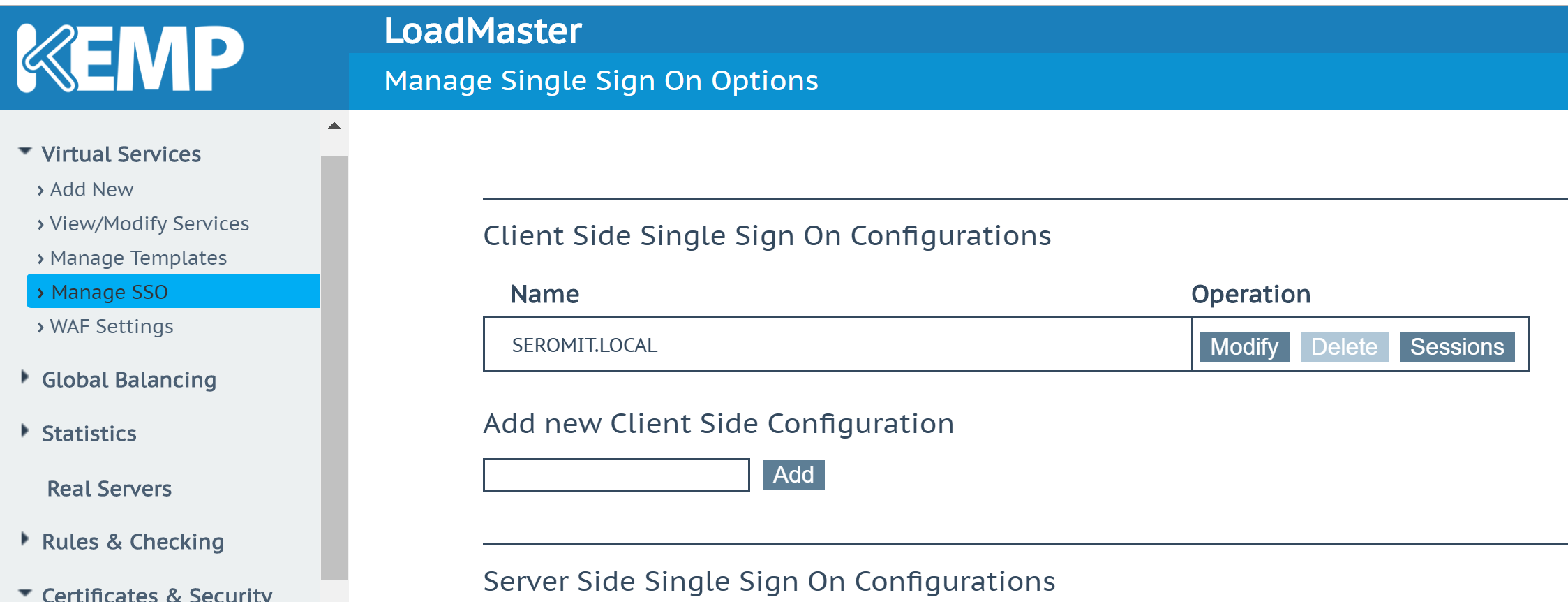
Configure Kemp SSO Domain
In Kemp LoadMaster GUI, navigate to Virtual Services | Manage SSO. In Add new Client Side Configuration field, specify a name and click on Add. I called mine SeromIT.local.
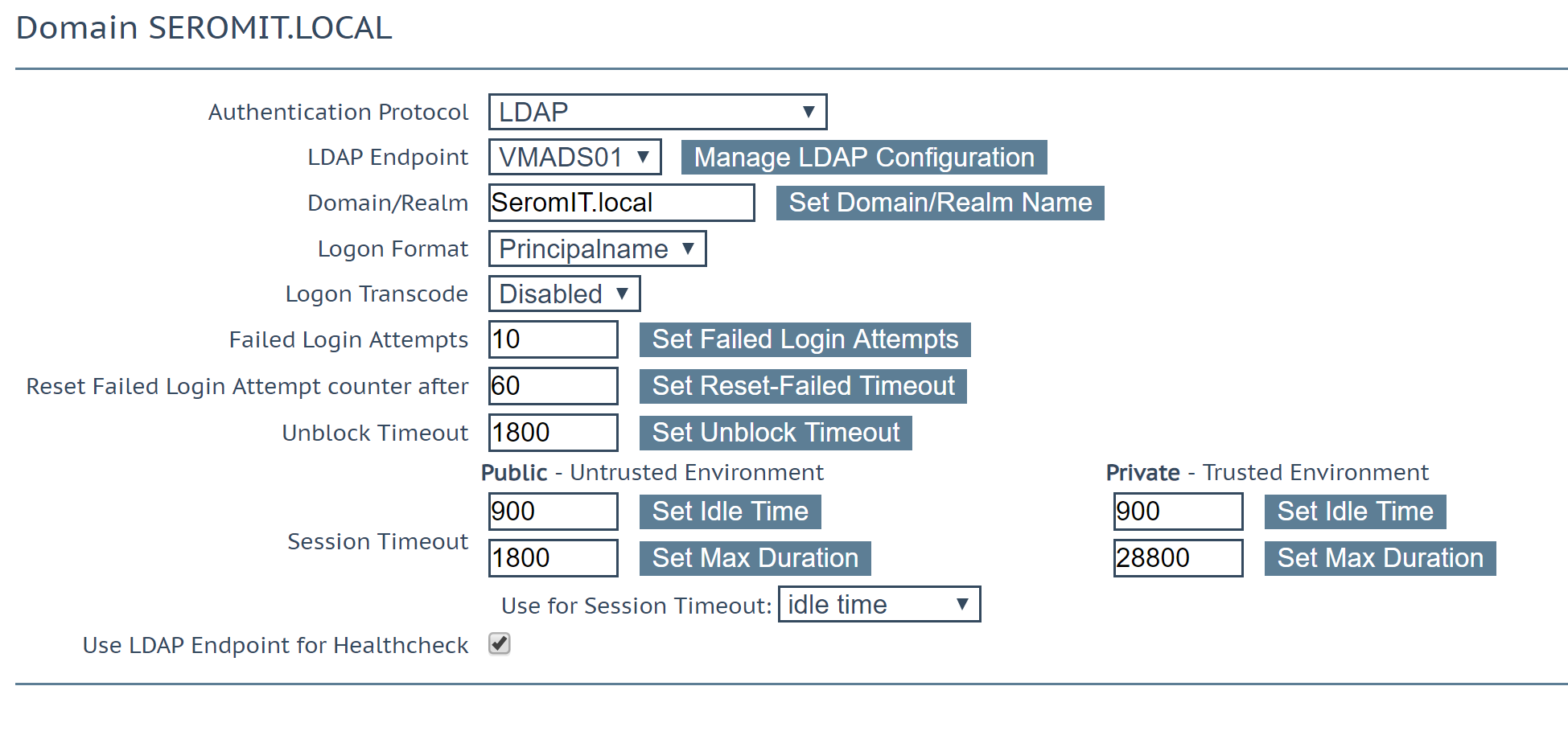
Configure the fields as the following:
- Authentication Protocol: LDAP
- LDAP Endpoint: the LDAP endpoint you previously created
- Domain/Realm: the domain name
- Login Format: Principalname
Leave other fields to default and enable Use LDAP endpoint for Healthcheck.
Configure virtual service
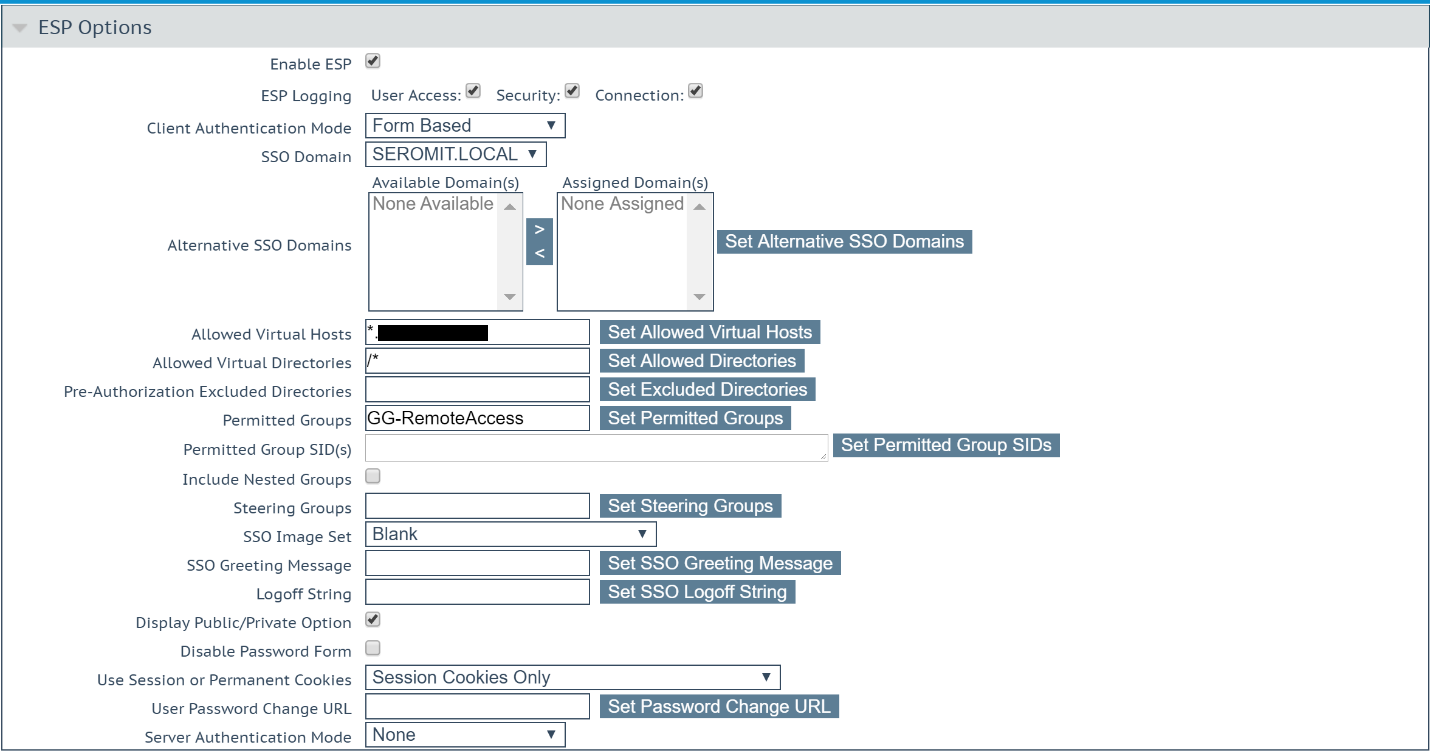
Now open the settings of the virtual service you want to configure. Navigate to ESP options. Enable ESP and configure as the following:
- Client authentication mode: Form Based
- SSO Domain : the domain you previously created
- Allowed Virtual Hosts: *.mydomain.com
- Allowed Virtual Directories: /*
- Permitted Groups: the group you created in Active Directory
You can get further information about each field in the following documentation:
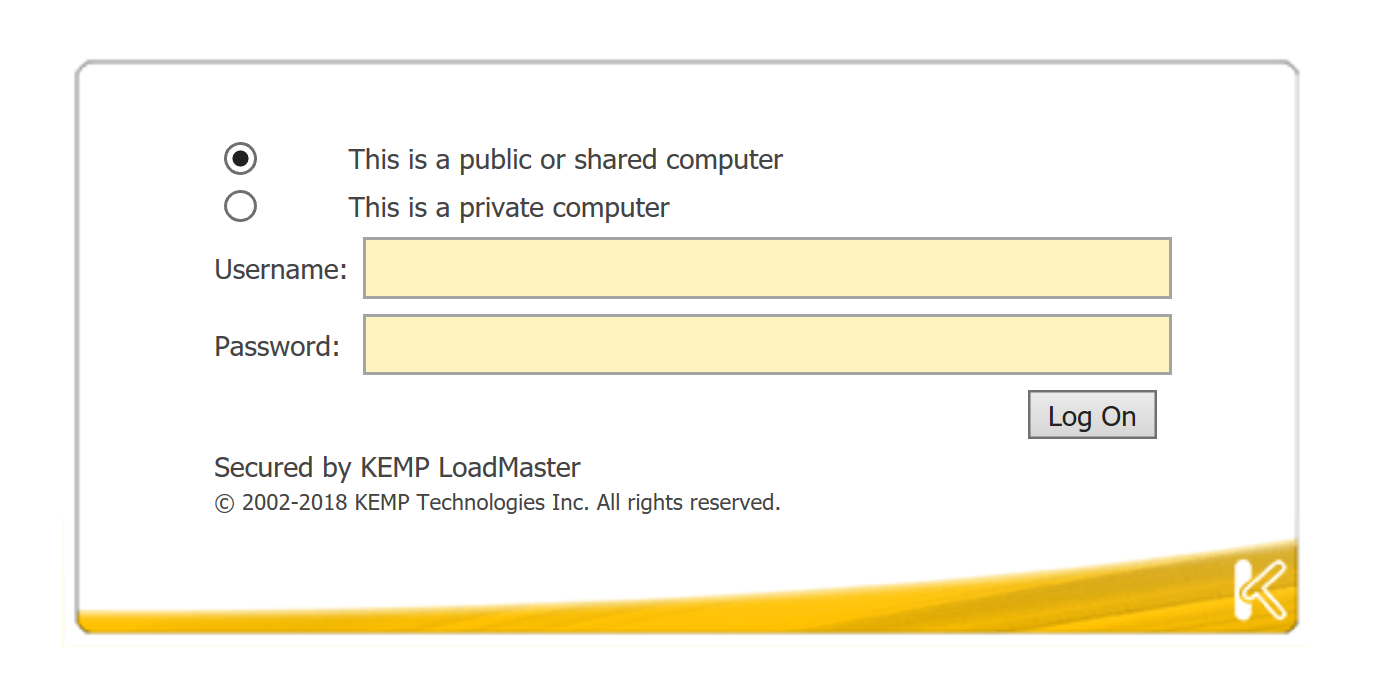
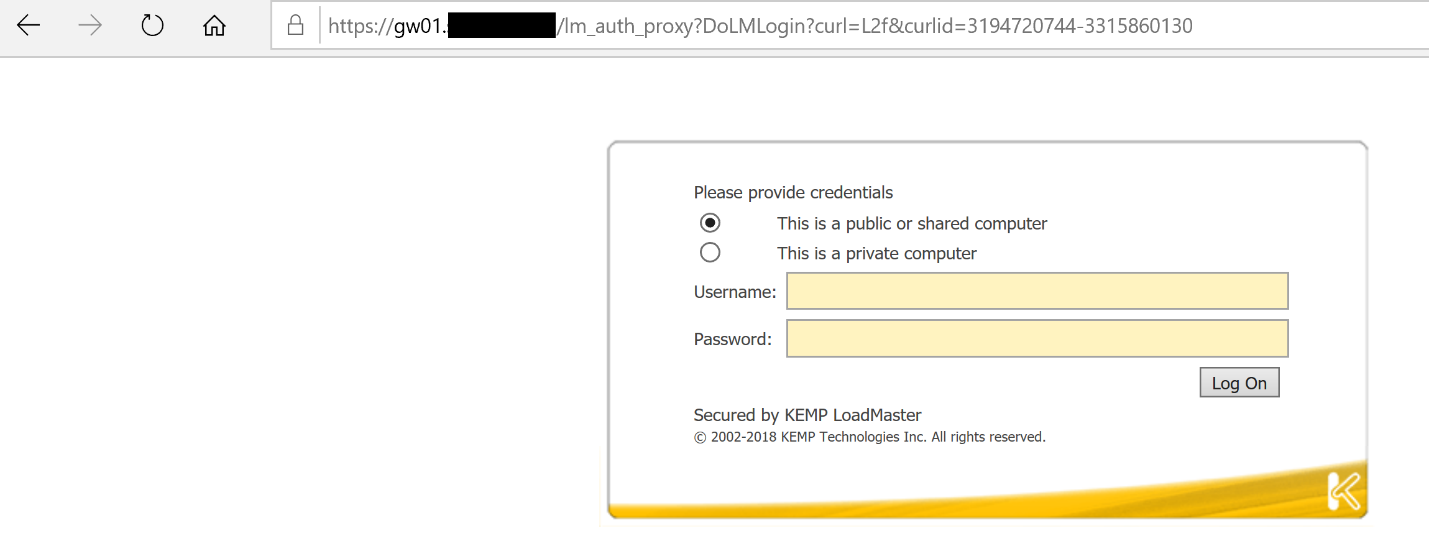
Now when I try to access to this virtual service, I have the following authentication form:
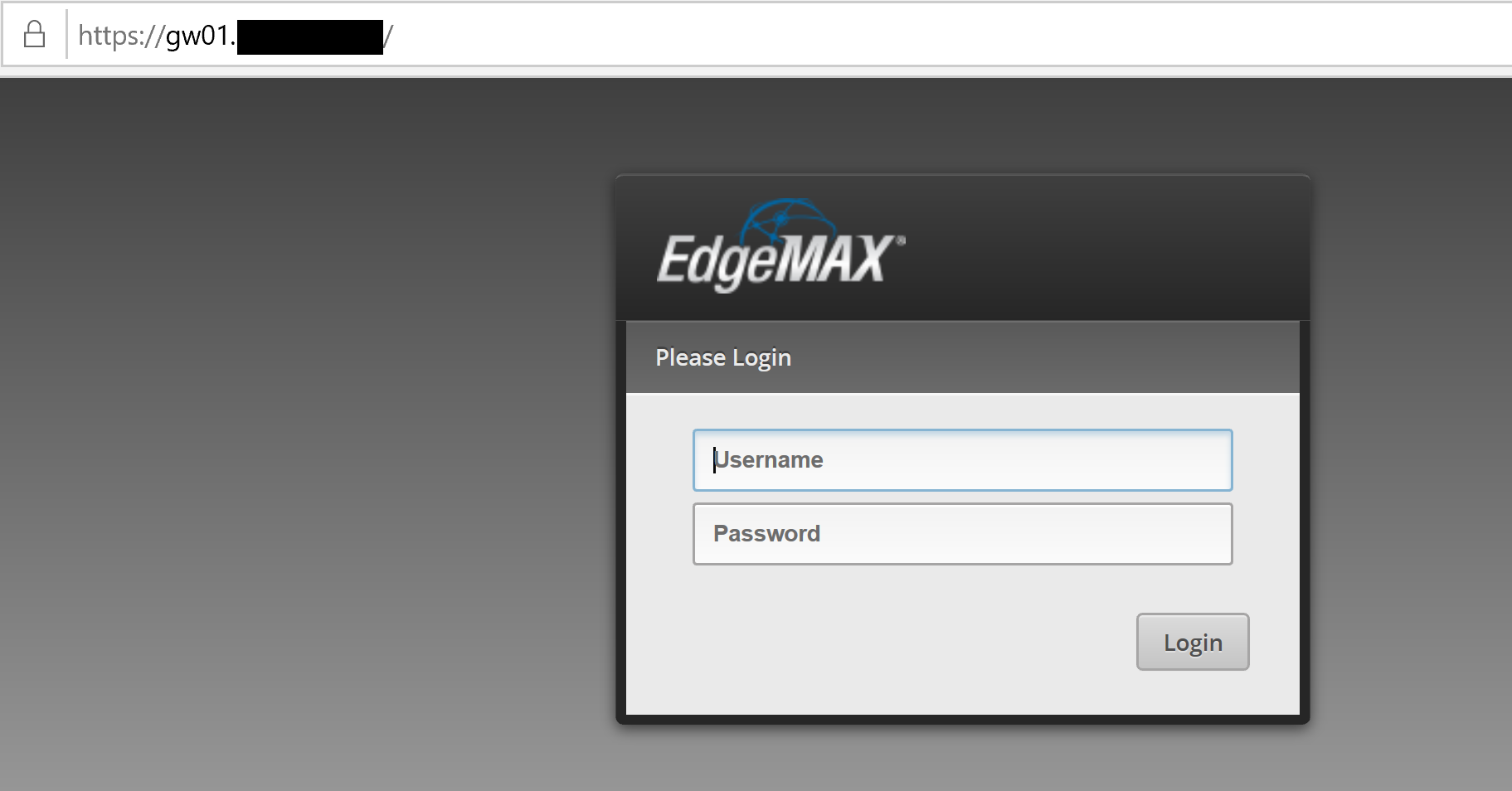
When I’ve specified credentials, I access to my service:
Conclusion
Kemp ESP can enhance the security level of your web applications by moving the auth provider from the web app to Kemp. Instead of authenticate on your web application, Kemp ESP enables to authenticate on your load balancer before accessing to the web service.