This is our second post where we try to teach some really basic security options and security habits that every IT admin shall adopt for local vSphere environments. In the first post we have secured our vCenter server and adopted some DR strategies allowing us to restore if something happens to vCenter Server.
Today we’ll try to have a look at different security settings we have to secure the VMware ESXi hypervisor. We’ll try to make sure that our ESXi hosts are secure.
VMware ESXi is quite secure even when you do an out-of-the-box installation. You can further enhance its security settings by either managing ESXi via vCenter Server or implementing those security settings at the ESXi level (standalone ESXi).
Security at the ESXi host is the first layer of defense. You can restrain access to your ESXi host by enabling a lockdown mode as you’ll see later down in this post. This has the advantage that nobody can go to the console of your server and enter as root.
VMware Secure boot and TPM 2.0 (trusted platform module)
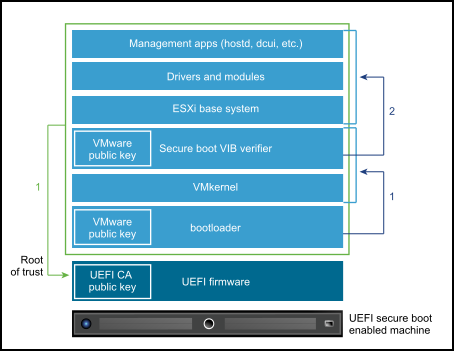
One of the first things which come to mind is to have your servers equipped with hardware TPM 2.0 dongle devices (you can find them on Amazon) and correctly configure your BIOS. UEFI Secure Boot is a prerequisite for TPM 2.0 support. UEFI Secure Boot protects the ESXi Boot Loader against tampering and ensures only signed software is installed.
When you boot an ESXi host with an installed TPM 2.0 chip, vCenter Server monitors the host’s attestation status. The vSphere Client shows the hardware trust status in the vCenter Server’s Summary tab under Security and you can see two different alarms there:
- Green – Normal status, indicating full trust.
- Red – Attestation failed.
You should read the documentation for your server and also VMware documentation about TPM before willing to configure the solution.
Quote about TPM:
TPM is a standard for a secure cryptoprocessor. The dedicated microprocessor is designed to secure hardware by integrating cryptographic keys into devices. The Trusted Computing Group (TCG) is responsible for TPM technical specifications. TPM hardware stores measurements in Platform Configuration Registers (PCRs). These measurements can be used to detect changes for anything that can be loaded into memory.
Intel TXT is computer hardware technology that uses a TPM and cryptographic techniques to provide measurements of software and platform components so that the system software and management applications may use those measurements to make trust decisions. It protects users from software-based attacks which attempt to steal sensitive information by corrupting system and/or BIOS code, or modifying the platform’s configuration.
You can use TPM 2.0 since vSphere 6.7 and higher.
Server BIOS settings
You should validate and configure the TPM 2.0 devices in the BIOS of each ESXi host otherwise it won’t work correctly. Each BIOS on different manufacturers is different so things to watch:
- TPM shall be set to use SHA-256 hashing
- Use FIFO (first-in, first-out) instead of CRB (which stands for Command response buffer)
- TXT shall be disabled (for now, TXT isn’t implemented on ESXi with TPM 2.0).
UEFI secure boot
VMware ESXi Shell
Disabling the ESXi shell is another way of protecting your ESXi hosts. The ESXi Shell is disabled by default on ESXi hosts. The only reason you should enable it is for troubleshooting. You should always keep as less ports open as possible in order to reduce surface attack. Another option would be to activate Lockdown mode.
What is lockdown mode?
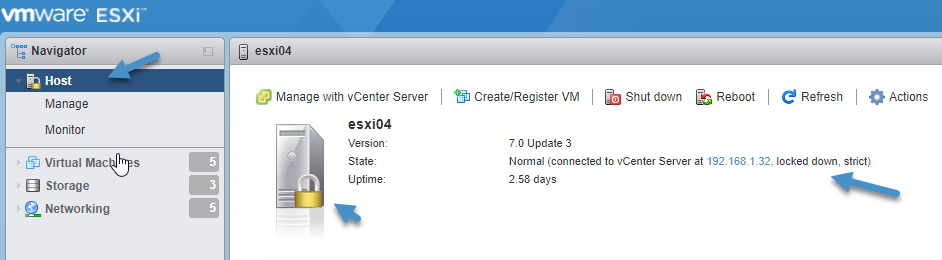
The lockdown mode is usually used to add another security layer to your installation. If you enable lockdown mode, the ESXi can only be accessed via vCenter Server.
ESXi lockdown mode enabled
In order to reduce the risk of unauthorized access, enable the ESXi Shell for troubleshooting only. The ESXi Shell is something different than lockdown mode. You should know, however, that even if the host is running in lockdown mode, you can still log in to the ESXi Shell if it is enabled.
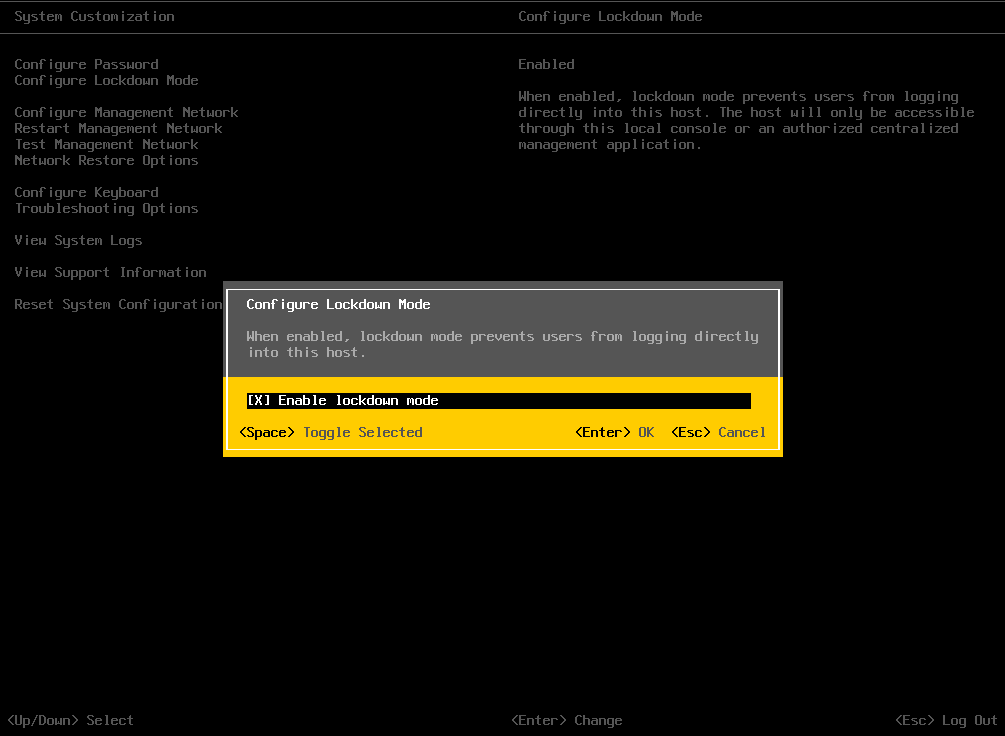
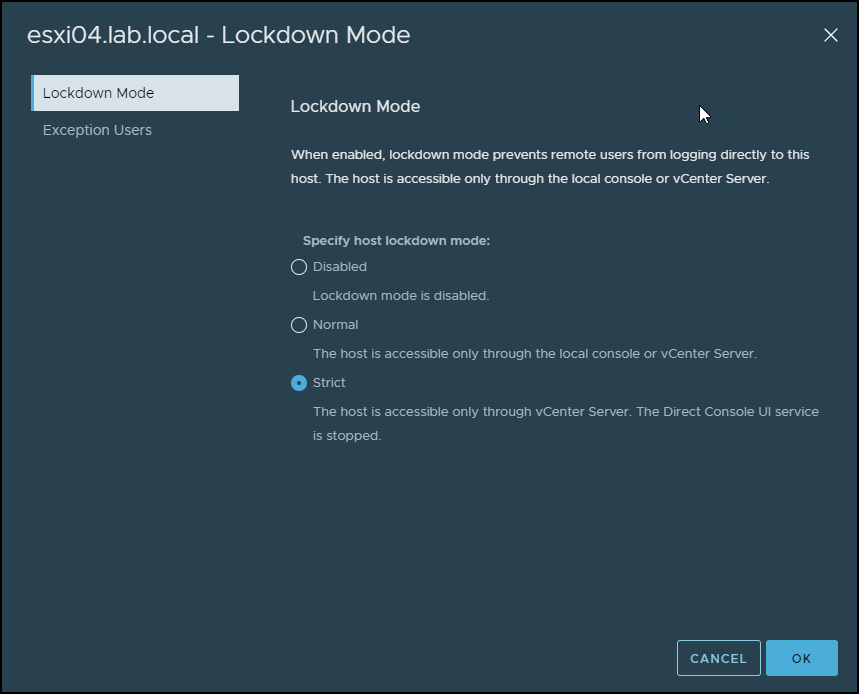
There are Normal or Strict lockdown modes. When ESXi is in Normal lockdown mode, the DCUI (direct control User Interface) is not stopped. You can activate the normal lockdown mode via DCUI or via vCenter.
Lockdown mode activation or deactivation
If you happen to lose the connection to the vCenter Server and ESXi host client is not working, you can still log on via a privileged account through the direct console (via Normal lockdown mode) and exit the lockdown mode there.
If not, and have a Strict lockdown mode activated, hopefully, the Exception Users are defined. The exception users have to be defined in the DCUI.Access advanced option for the host. You can do it via GUI through the vSphere client when connected to vCenter Server. Only users who are on the Exception Users list and have administrator privileges can log in to the Direct Console User Interface.
Attention here. If you cannot restore the connection to your vCenter Server and you have not defined Exception users and SSH and Shell are disabled, you have to reinstall the host.
The strict lockdown mode looks like this:
Host in strict lockdown mode
Exception users are host local users or Active Directory users with privileges defined locally for the ESXi host. They are not members of an Active Directory group and are not vCenter Server users. They are usually used as accounts for services such as backup software. Exception users do not lose their privileges when the host enters lockdown mode.
When the host is in lockdown mode, if a user in the “Exception User” list has an administrator role on the host, they can access the host from the ESXi Shell and via SSH or via host client. This access is possible even in strict lock mode.
How to set up Exception users on a host?
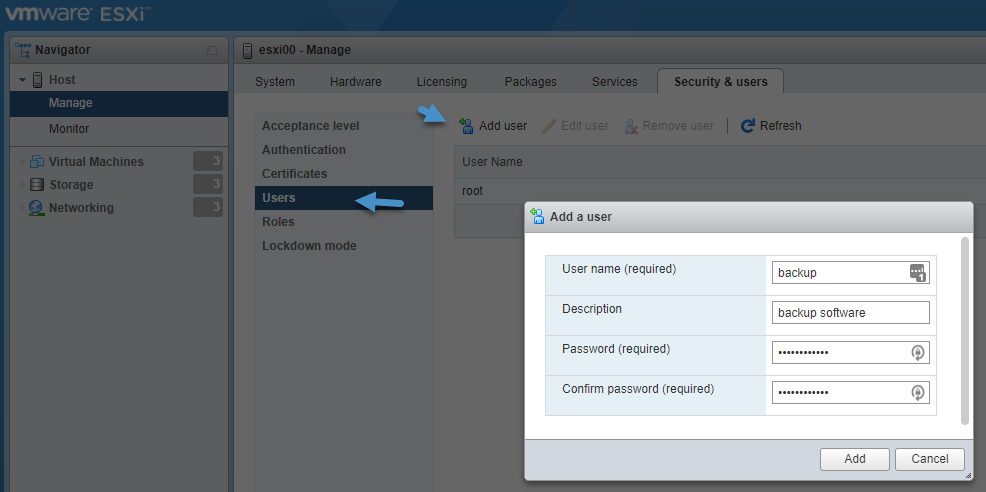
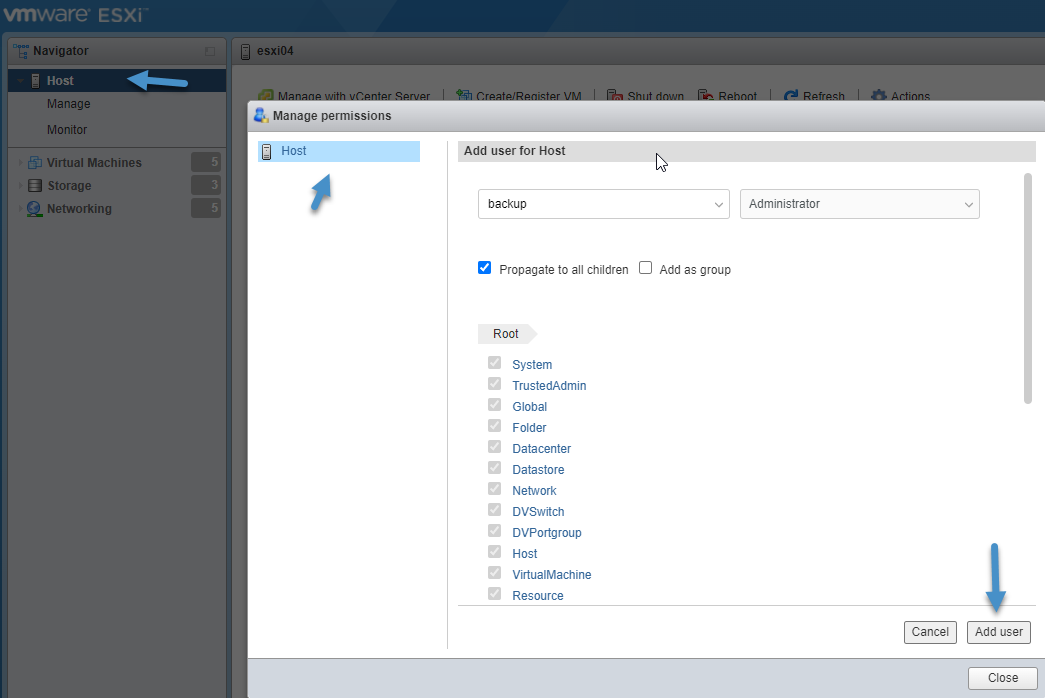
You have to set up exception users the following way. First, go to your ESXi host and create a service account. In our case “backup” user. You have to assign some privileges so the account (if you wish) can log in to the DCUI.
Add service account to ESXi
And also set permissions. You just right-click the host when within the host client > Permissions. Then assign permissions > Add User > Close.
Assign Permission to your backup user
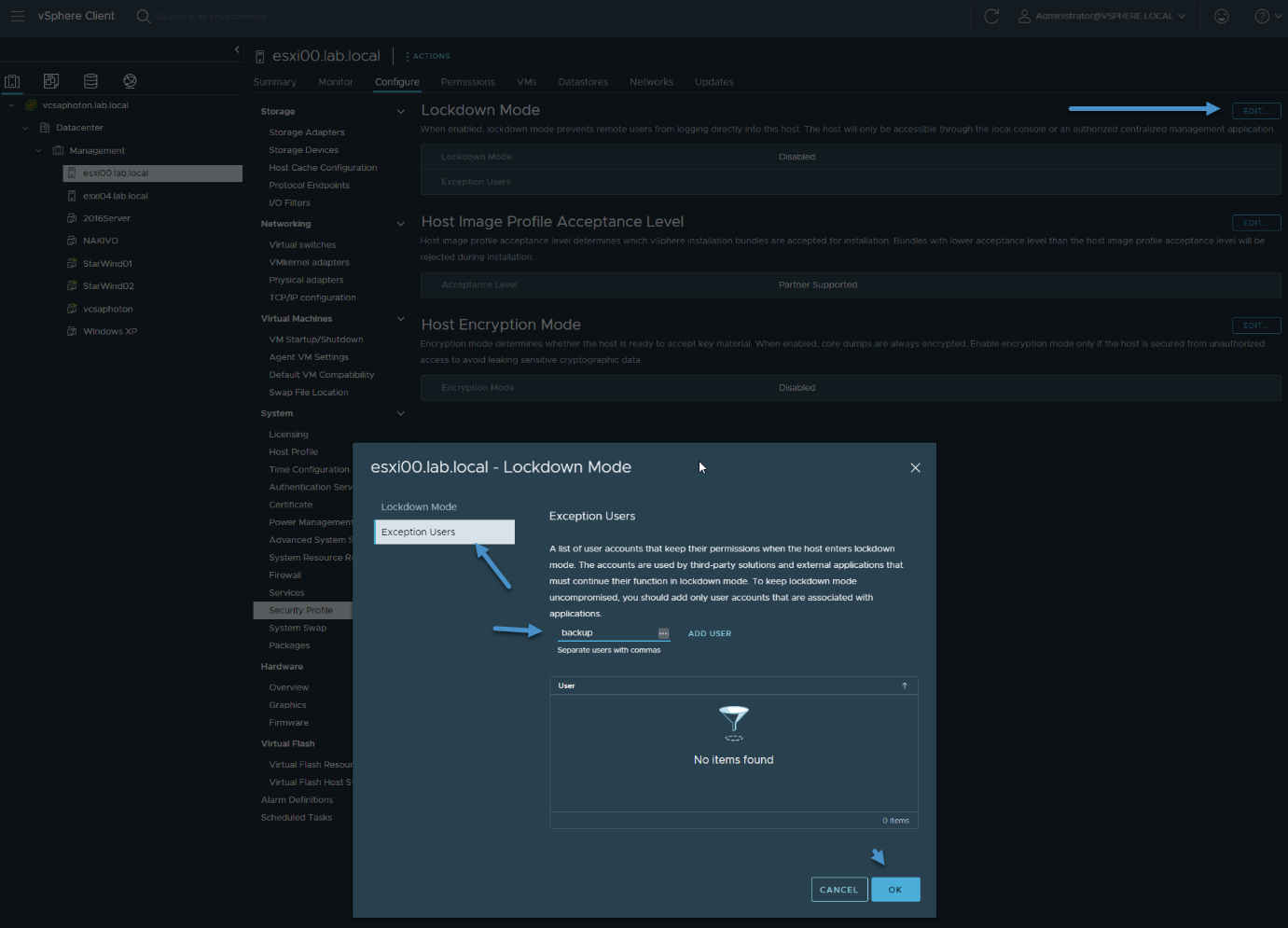
Then go to your vCenter server and add this user to the exception users via Configure > Security Profile > Lockdown mode > Edit > Exception users > Add
Assign Permission to your backup user
You’re done.
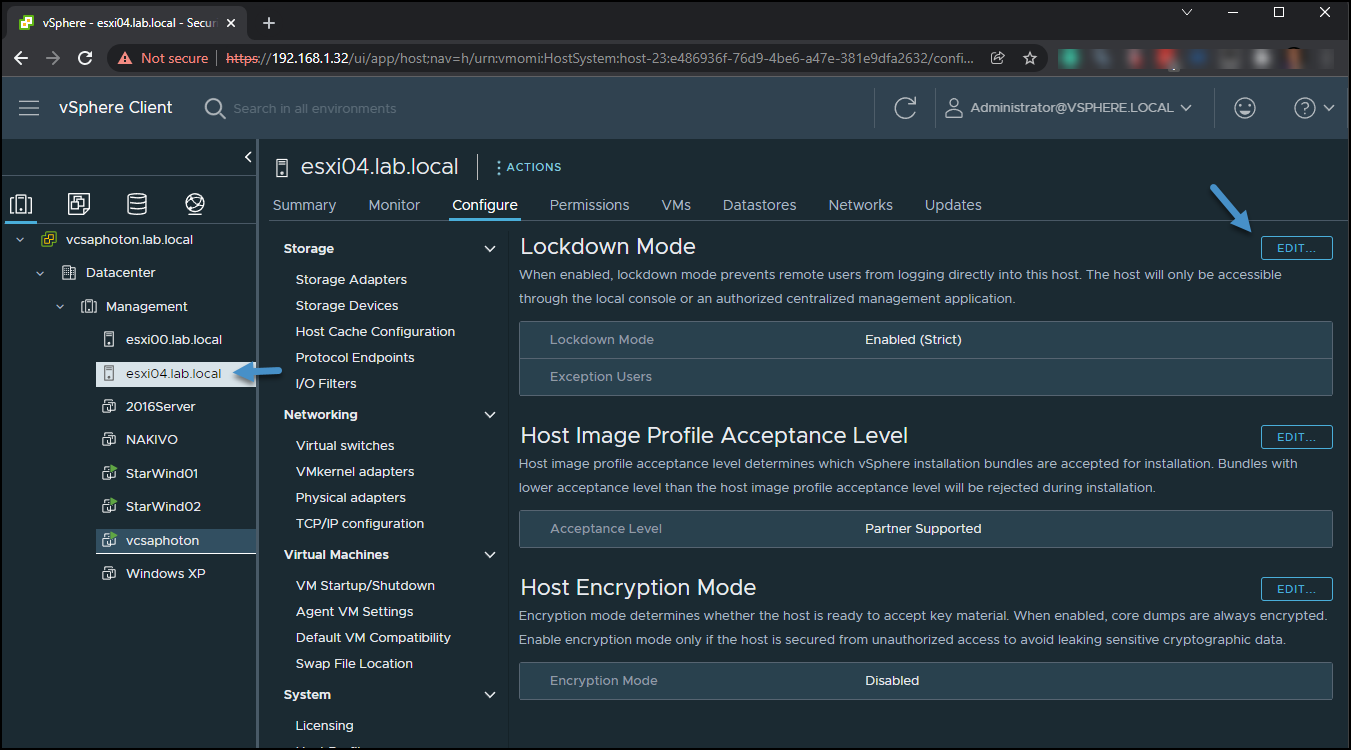
To enable or disable lockdown mode via vCenter, connect to your vCenter server > Select your host > Configure > Security Profile > Lockdown mode > Edit.
Enable or Disable Lockdown mode
You have then the option to select which mode you want to activate/deactivate via a radio button.
Normal or Strict Lockdown mode
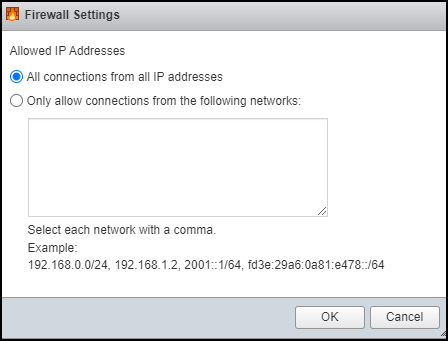
ESXi Firewall configuration
The firewall that ESXi has is enabled by default. You can enable or disable services through the ESXi host client. You can go to Networking > Firewall Rules. You’ll see that the VMware Host Client displays a list of active incoming and outgoing connections with the corresponding firewall ports.
ESXi Firewall settings
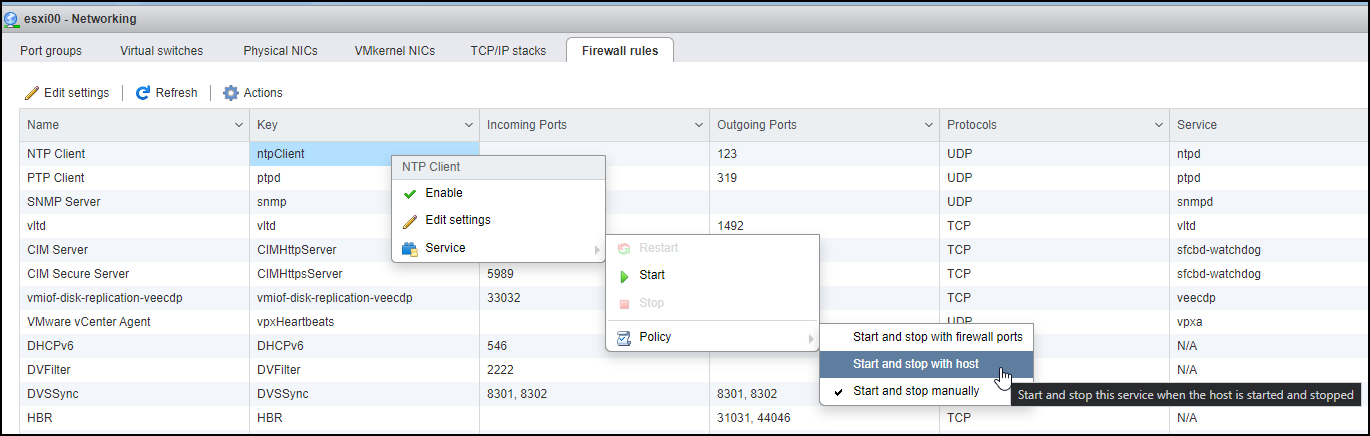
You can also use right-click on the screen and then select whether you want to enable the service and change the service and the policy settings. You might want to start the service when the host starts or when the firewall port is open or closed.
Enable service and Change policy for service settings
Final Words
VMware is pretty flexible to customization. The best way, of course, is probably, even for a small environment, to manage your ESXi hosts via vCenter Server. With the VMware vSphere Essentials edition (or Essentials Plus which has a vMotion license), you can manage up to 3 ESXi hosts which, for a small environment, is more than enough.
Lockdown mode is a very good way to protect your infrastructure by simply restricting the management to only via vCenter Server. Hackers and inside man threads won’t pass through.
An essential part of security and DR plans is definitely backup management. Let’s see if we can get you some tips in our next article. Restoring quickly and efficiently is key, but one has to keep in mind also off-site backups and their management.