Organizations can use Azure Active Directory (AD) authentication in order to login to their Azure virtual machines running:
- Windows Server 2019 Datacenter edition (Preview)
- Windows 10 1809 and later (Preview)
- CentOS 6, CentOS 7
- Debian 9
- openSUSE Leap 42.3
- RHEL 6, RHEL 7
- SLES 12
- Ubuntu 14.04 LTS, Ubuntu Server 16.04 et Ubuntu Server 18.04
One of the biggest advantages to use Azure AD to authenticate to VMs is to centrally control and enforce policies. It means that you can use Azure Role-Based Access Control (RBAC) and Azure AD Conditional Access in order to control who can access a VM.
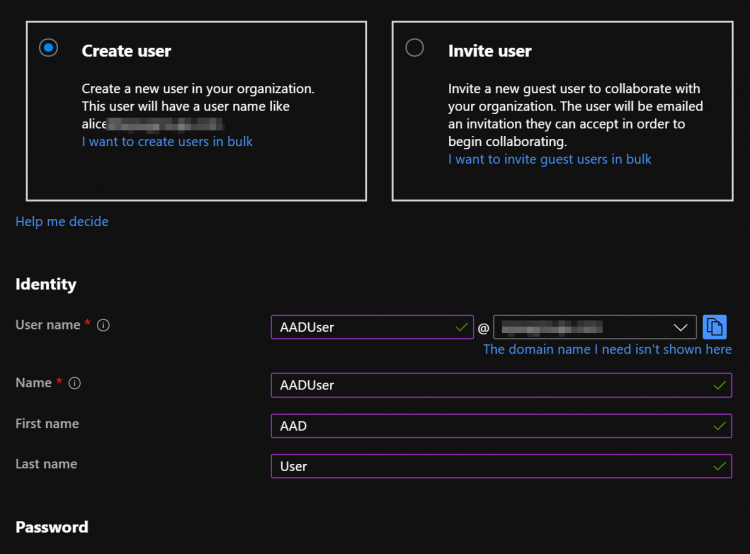
Let’s start by creating a new Azure AD User named “AADUser”.
Windows Virtual Machine
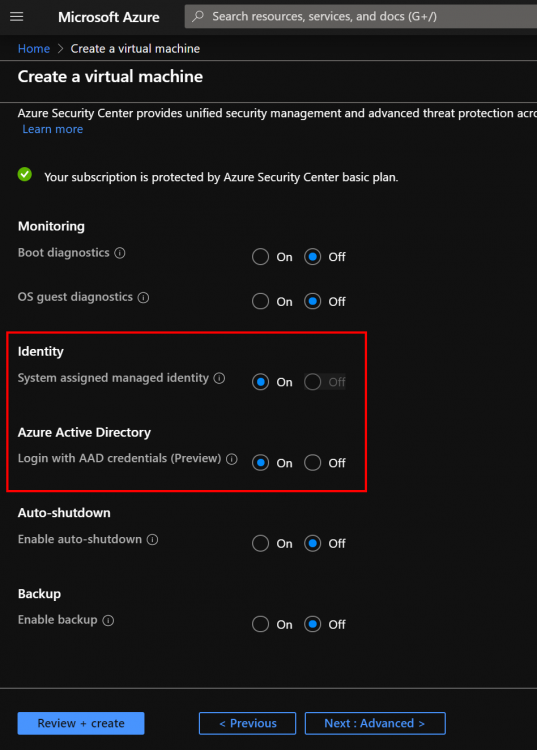
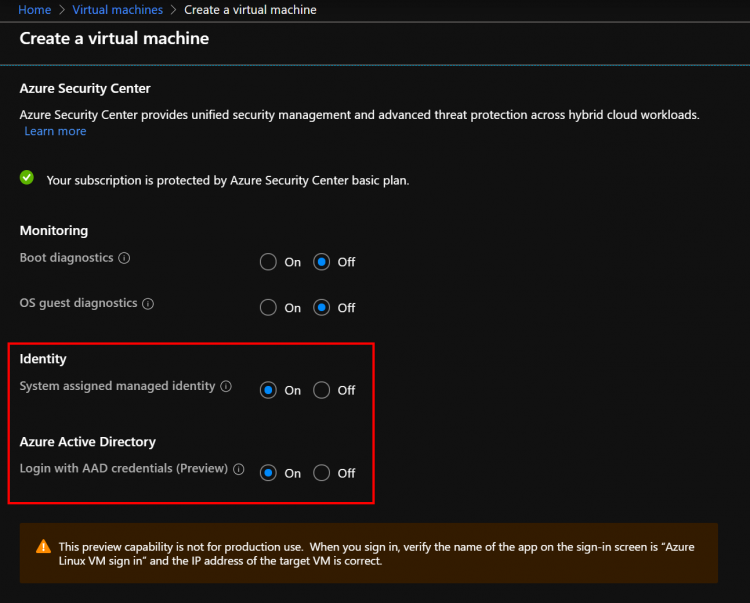
Once the Azure AD user is created, we can create a Windows Virtual Machine in order to test the Azure AD authentication. During the creation wizard, you must enable the following options:
When you will enable Azure AD option, the “identity” option will be enabled automatically. Once the VM is created, you must assign the following role to your Azure AD user:
- Virtual Machine Administrator Login: Users with this role assigned can log in to an Azure virtual machine with administrator privileges.
- Virtual Machine User Login: Users with this role assigned can log in to an Azure virtual machine with regular user privileges.
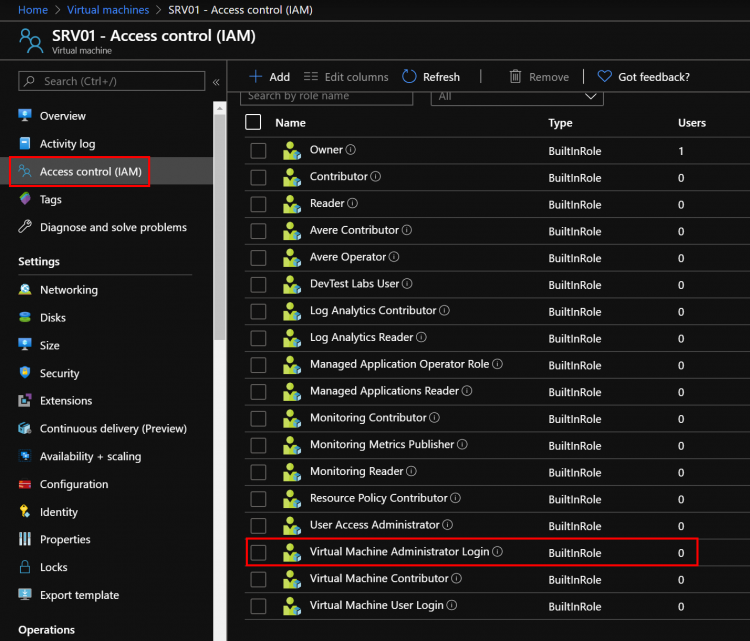
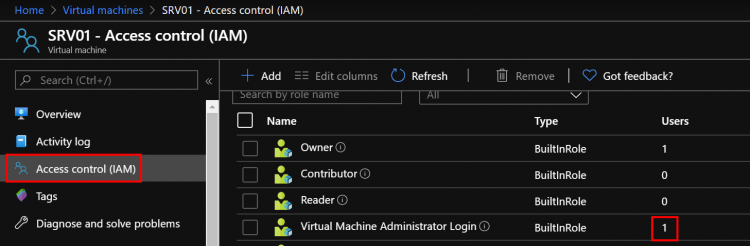
Navigate to the Virtual Machine overview page and select Access control (IAM) from the menu options. As shown below, there are no users allowed at this step.
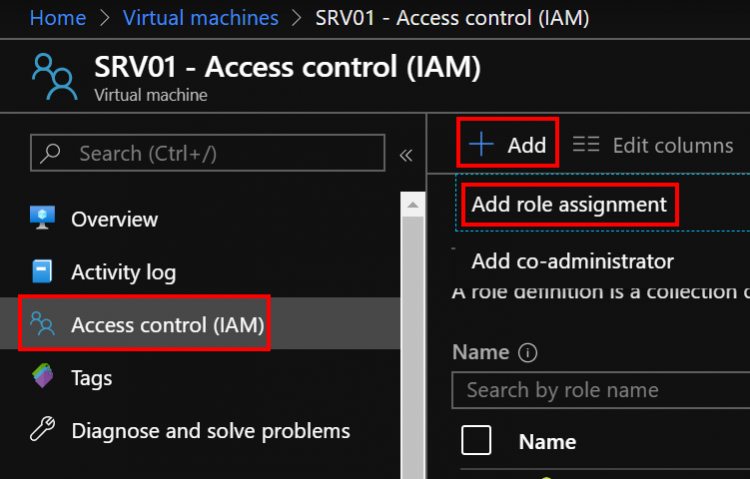
- Select Add
- Add role assignment to open the Add role assignment pane.
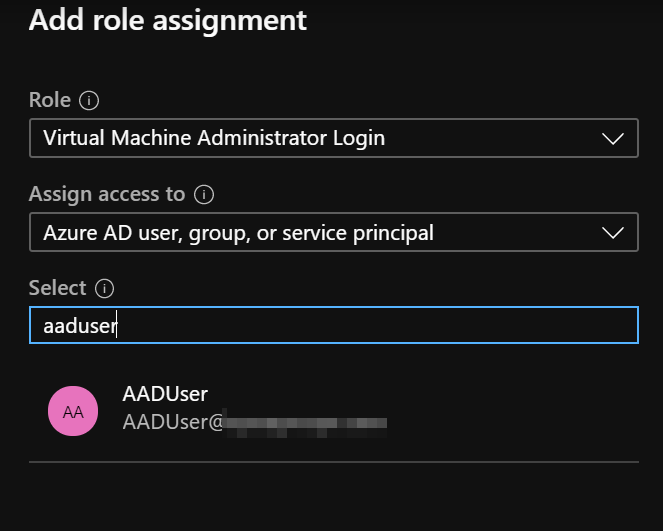
- In the Role drop-down list, select the role “Virtual Machine Administrator Login”
- In the Select field, select the Azure AD user created previously
- Select Save, to assign the role.
As shown below, we can confirm that the user has been affected to the role.
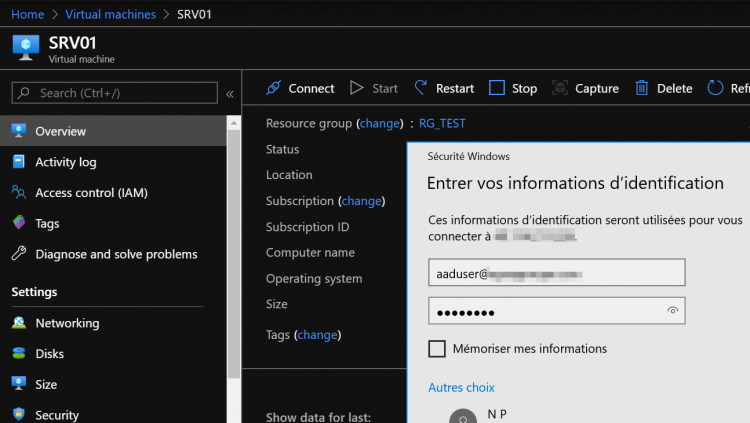
Next, you can start the Virtual Machine and test if you can sign in with your Azure AD user:
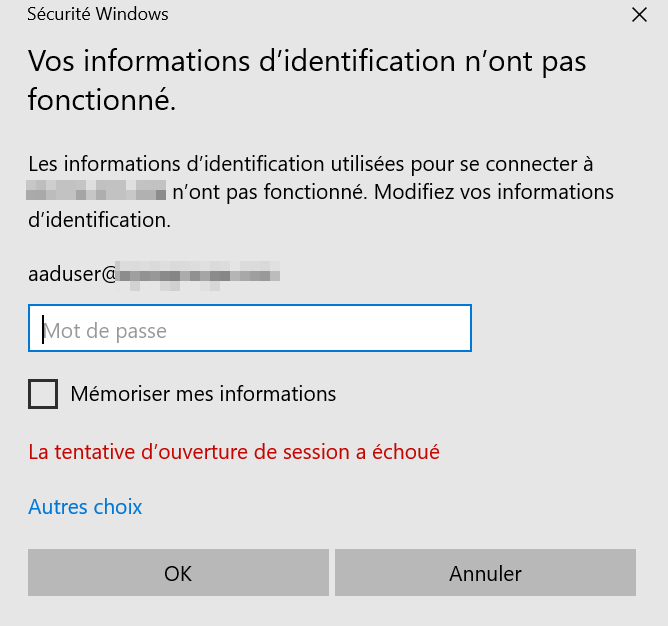
At this step, you should get the following error message: “the logon attempt failed”:
Verify that the Windows 10 PC you are using to initiate the remote desktop connection is one that is either Azure AD joined, or hybrid Azure AD joined to the same Azure AD directory where your VM is joined to.
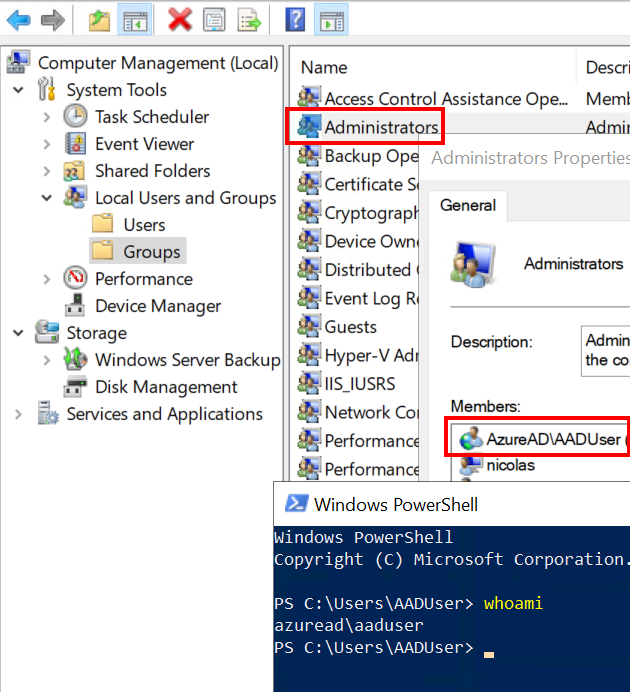
When you are logged in to the Virtual Machine, you can confirm the following information:
Linux Virtual Machine
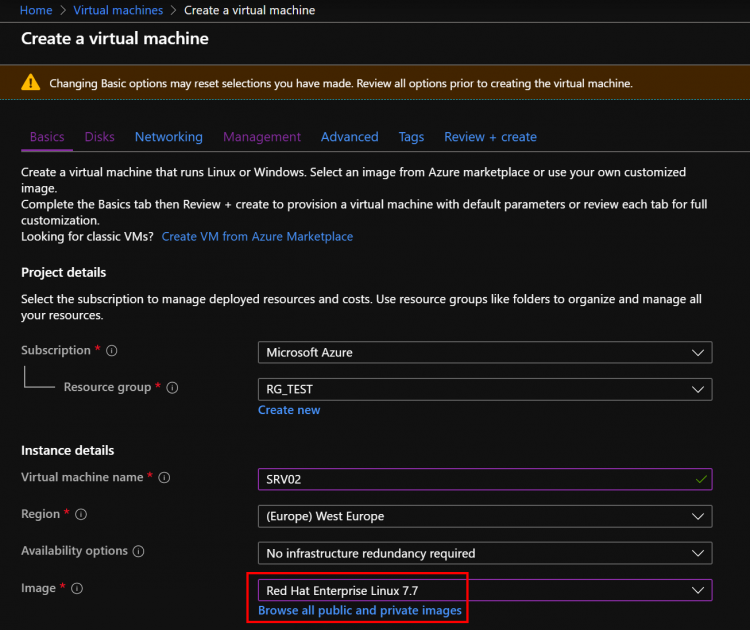
If you use Azure to run Linux Virtual Machines, you can use your Azure AD credentials to logon to your Linux session. During the provisioning wizard, you must select the image:
And then, enable the Azure AD option.
Now, you can assign the role to your Azure AD user (the same step we performed previously for the Windows Virtual Machine) and start the SSH session.
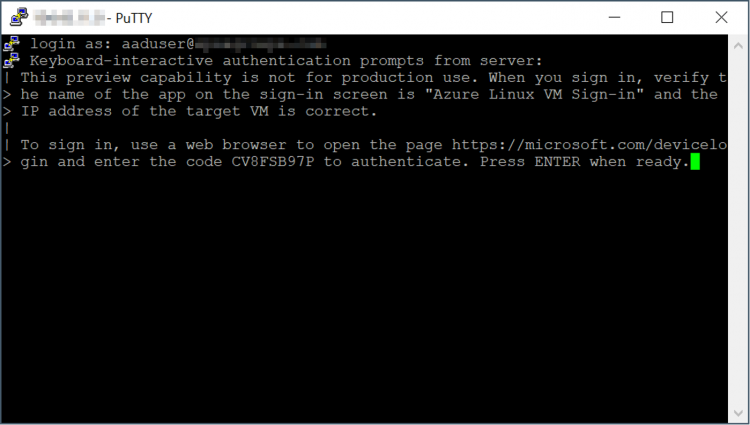
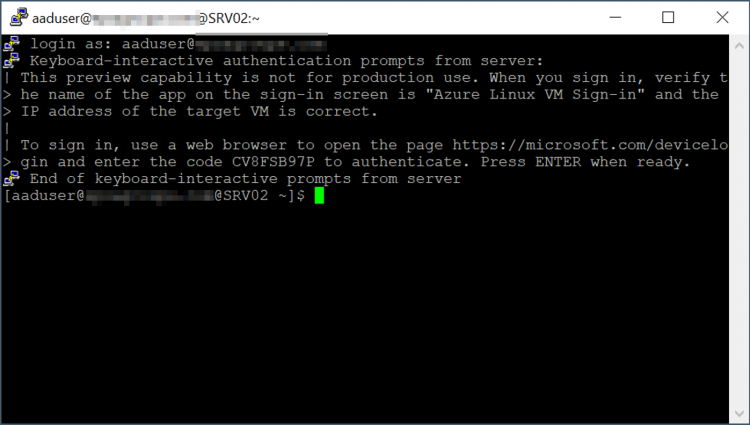
You will get the following message asking you to logon to https://microsoft.com/devicelogin and enter the authentication code:
Once you validate the authentication code, you can close the browser window and you can press ENTER to work on your Linux VM.
Conclusion
Thanks to the Azure AD Authentication feature, we can now use Azure AD identities to sign in to Virtual Machine (Linux and Windows). There are some prerequisites, but it works great and it is a nice feature to simplify the management of your identities.