Introduction
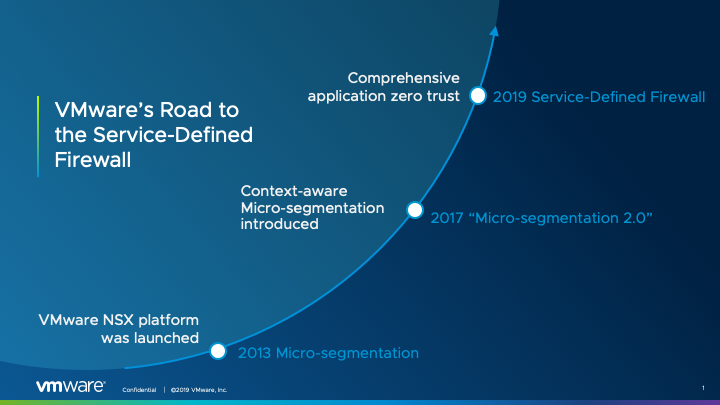
VMware did a lot of work paving the way to the industry-first Service-Defined Firewall. Previously, they developed AppDefense, vRealize Network Insight, and NSX-T/NSX-V solutions, and the company decided to go beyond. With all these solutions as a groundwork, VMware introduced the first ever Service-defined Firewall in March 2019. In this article, I’m going to take a closer look at this solution.
How everything started
Back in 2013, VMware released VMware NSX-T – the network virtualization solution for aggregating virtual networks in the complex hybrid hypervisor and container environments. I won’t discuss it here since I believe most of you is already familiar with this product.
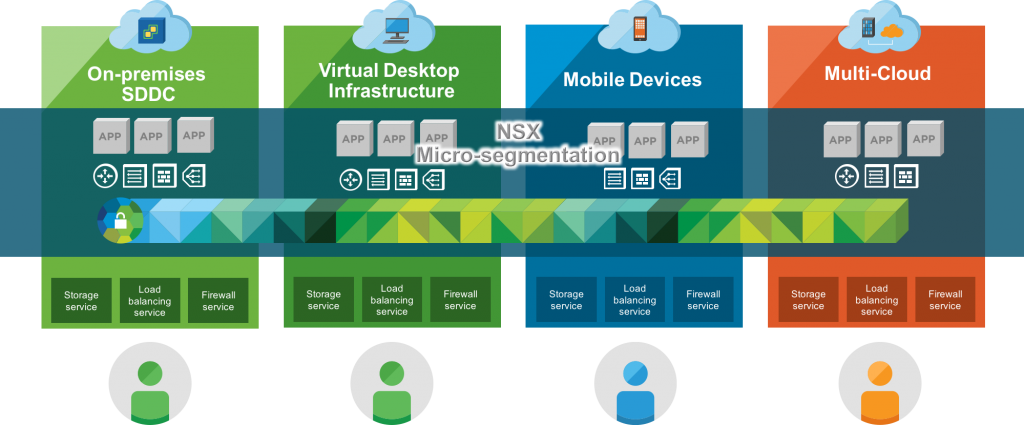
Later, VMware presented vRealize Network Insight (vRNI, formely Arkin) – a solution that augments a VMware NSX installation. It provides single pane of glass for the VMware NSX environment and implements microsegmentation for application on a network level, also it includes tools for monitoring application traffic flows and troubleshooting, as well as other features for reporting and insight into the SDN traffic flows.
It is designed for building highly available and secure network infrastructures spanned across multiple clouds.
Of course, most of you already know of AppDefense (announced at VMworld 2017). This solution introduces a new model for application protection into virtualized and cloud environments. AppDefense examines the normal behavior of an operating system and applications, track their current state and notify a system administrator and automatically take action if something weird is going on.
Let’s look under the hood
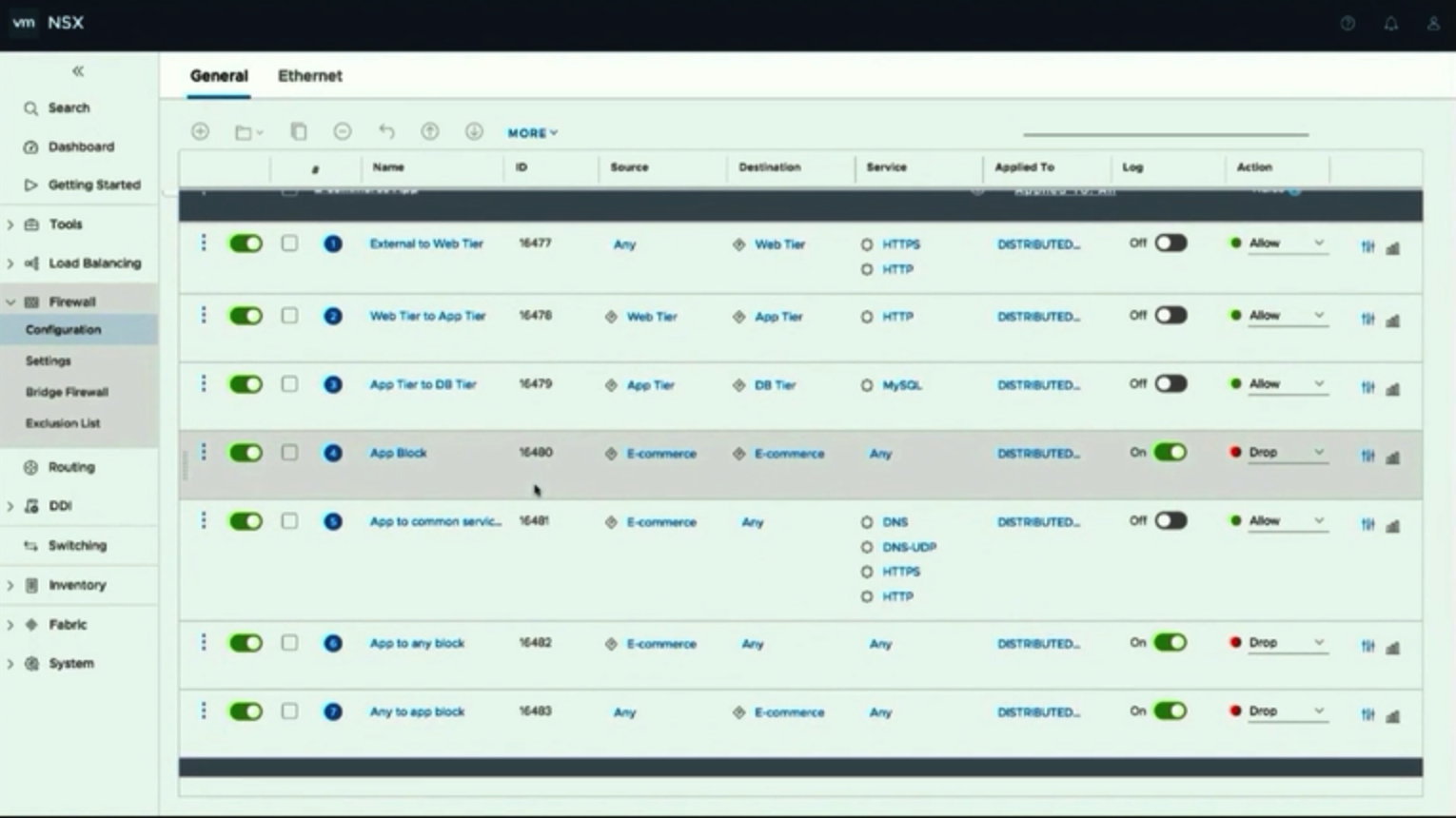
Service-Defined Firewall implements microsegmentation for protecting virtual environments (c.f. service insertion and guest introspection). This mechanism involves monitoring applications’ network activity on the hypervisor level (i.e., data is taken from NSX or directly from ESXi servers). In this way, with microsegmentation in place, it is impossible to manipulate intrusion detection tools from inside of the guest OS.
The most interesting thing about VMware Service-Defined Firewall is its ability to create application- and microservice-level policies. And, it is a great alternative to setting up policies on OS, server, or port levels, you know! All you need is just to set up the policies and rules for a new application, and they will be propagated to servers and ports. Being pretty intuitive, this feature makes it far easier to implement new services in terms of their protection and maintenance while moving virtual machines within and between datacenters.
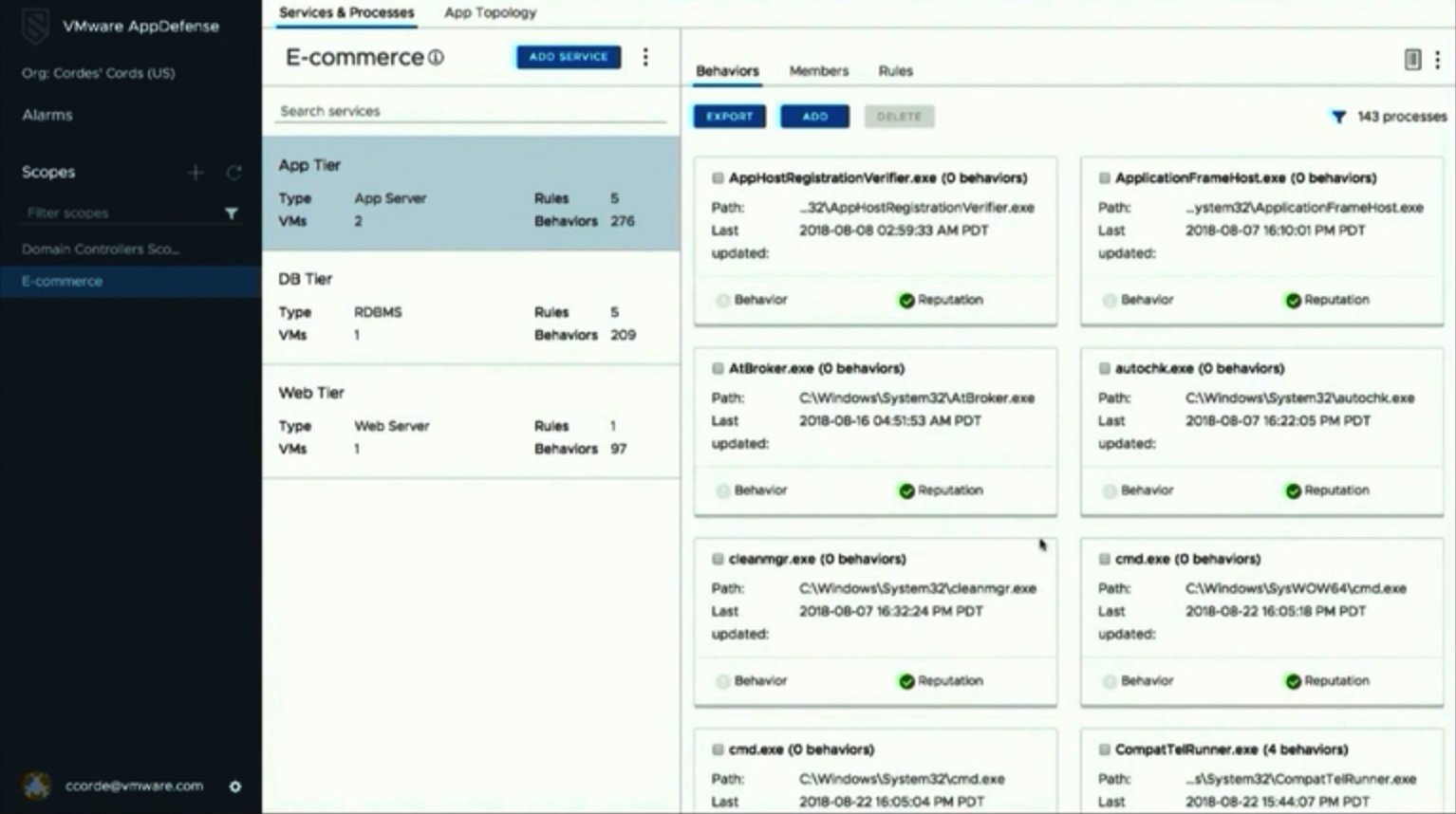
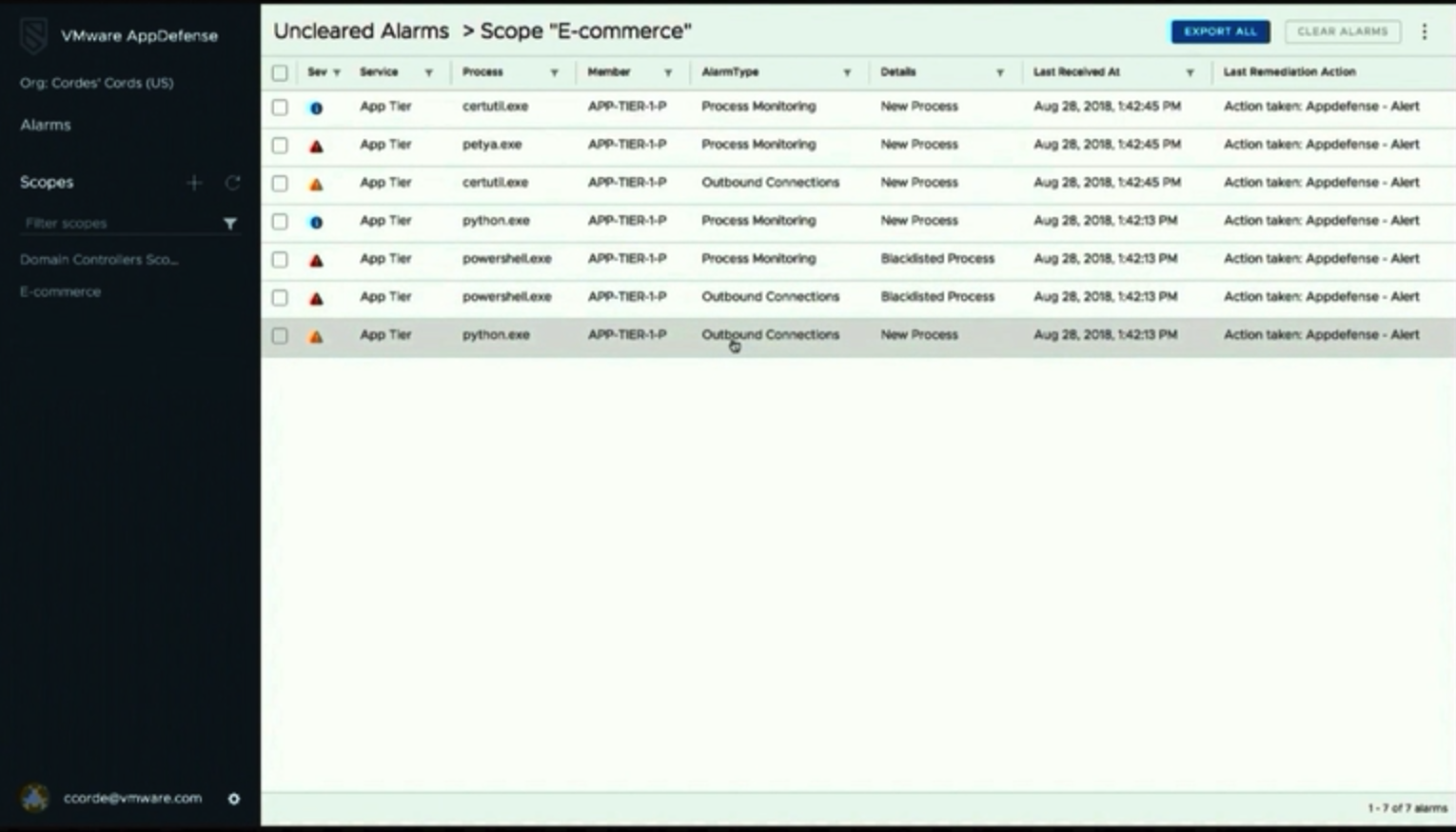
Generally speaking, VMware Service-Defined Firewall leverages and expands AppDefese features: it determines policies for applications on a network level, than creates the baseline (i.e., datacenter normal behavior) and notifies administrators about any deviations from it. Here is an example of the Uncleared Alarms view in the AppDefense console:
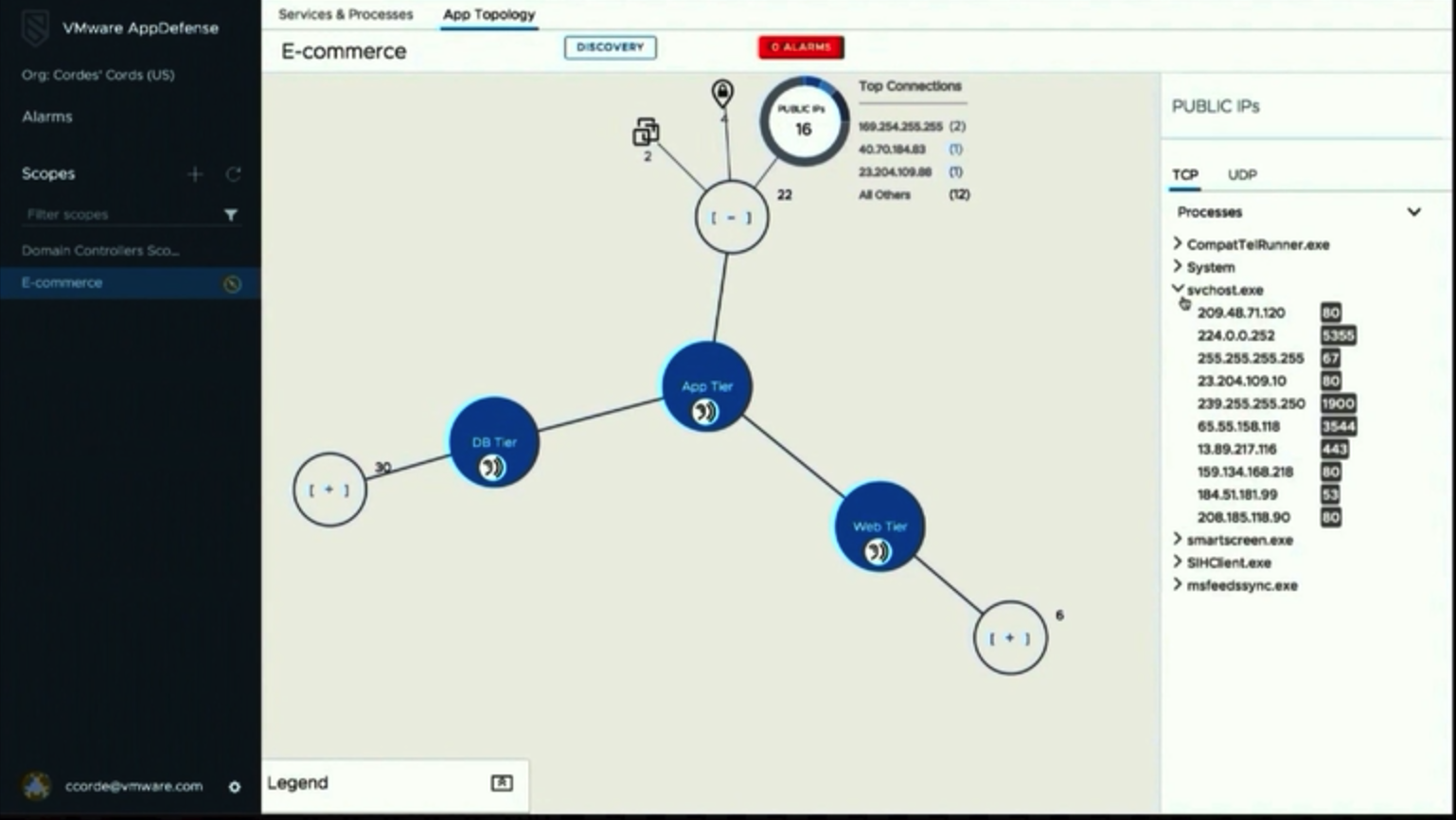
AppDefense also enables to create an app topology that allows users to limit interactions between applications to specific objects and ports. In addition, VMware Service-Defined Firewall can generate the templates for the specific policies to provide better protection for individual applications.
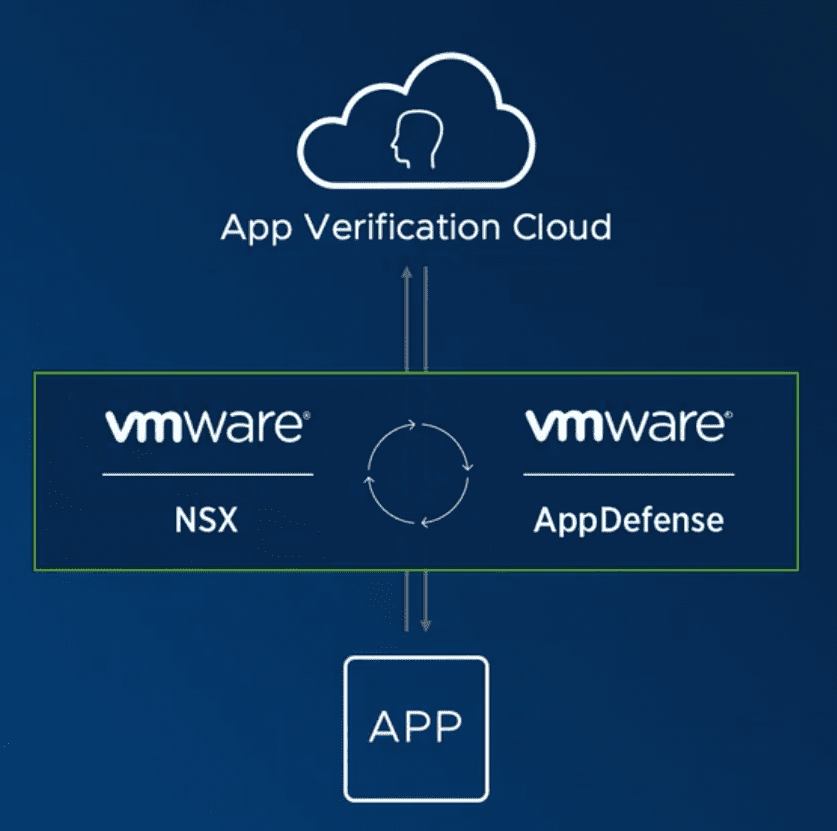
Pinpointing suspicious activity is performed by the Application Verification Cloud. It analyzes information from the millions of virtual machines all over the world and defines the “normal behavior” of microservices through machine learning algorithms. That system works great for any detecting deviations from normal performance.
Why there’s a buzz about Service-Defined Firewall
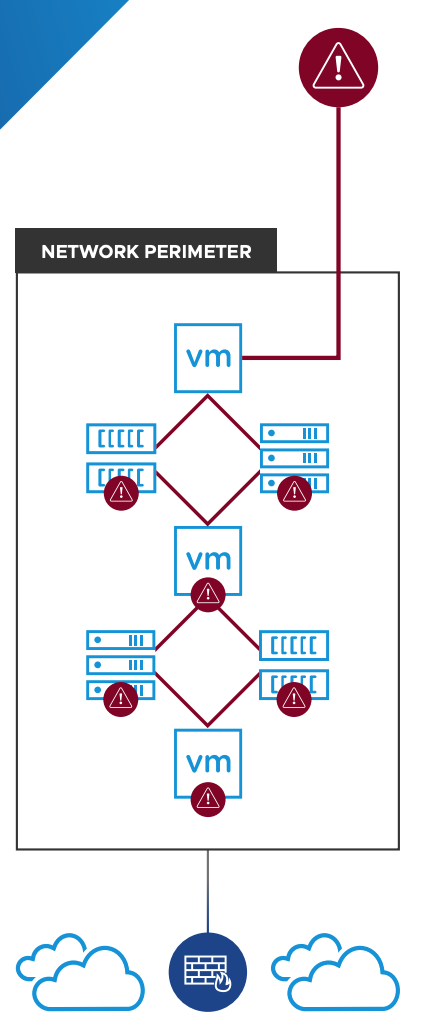
The traditional means of applications protection within an IT environment are mainly focused on ensuring security just on a network perimeter level so that everything inside could be considered secure.
Interestingly, the most dangerous attacks often come from the inside of infrastructures. Malware studies environment architecture and interactions, then, once it is done with analysis, it is spreading all over the datacenter using its vulnerabilities.
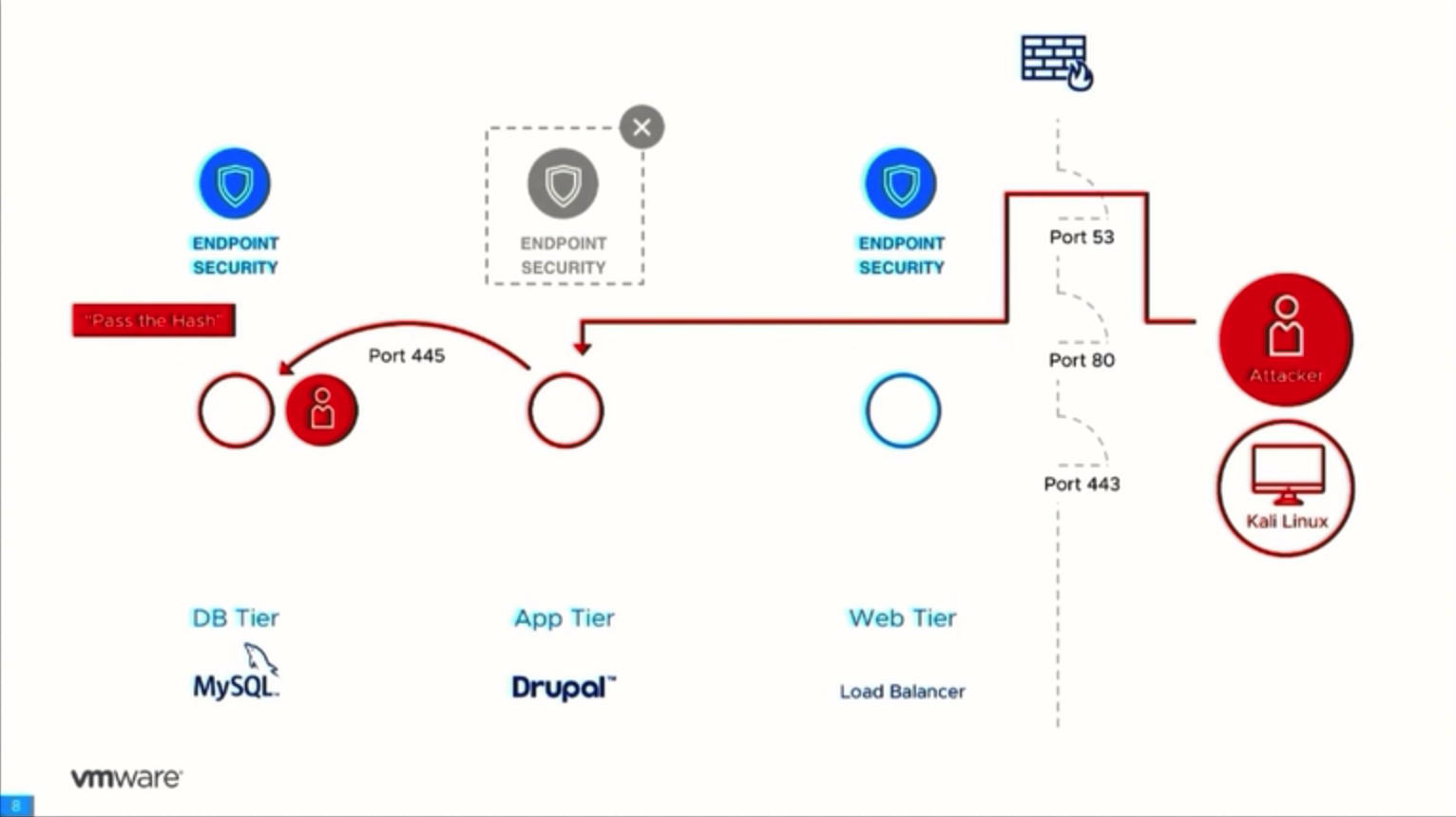
There might also be the case when the attack comes through the open ports (e.g., web servers or application servers). Once intruders gain administrator rights, the malicious code disables antiviruses and “disarms” any other means of protection. Eventually, the malware gets access to any datacenter systems (e.g., databases).
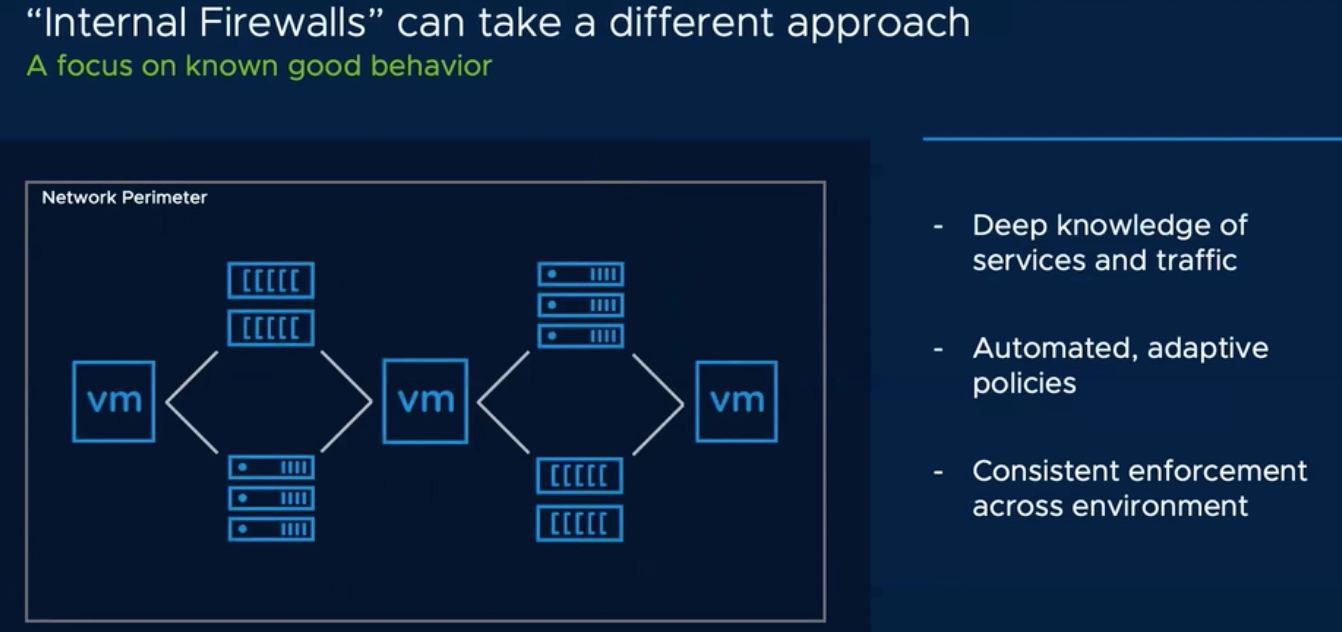
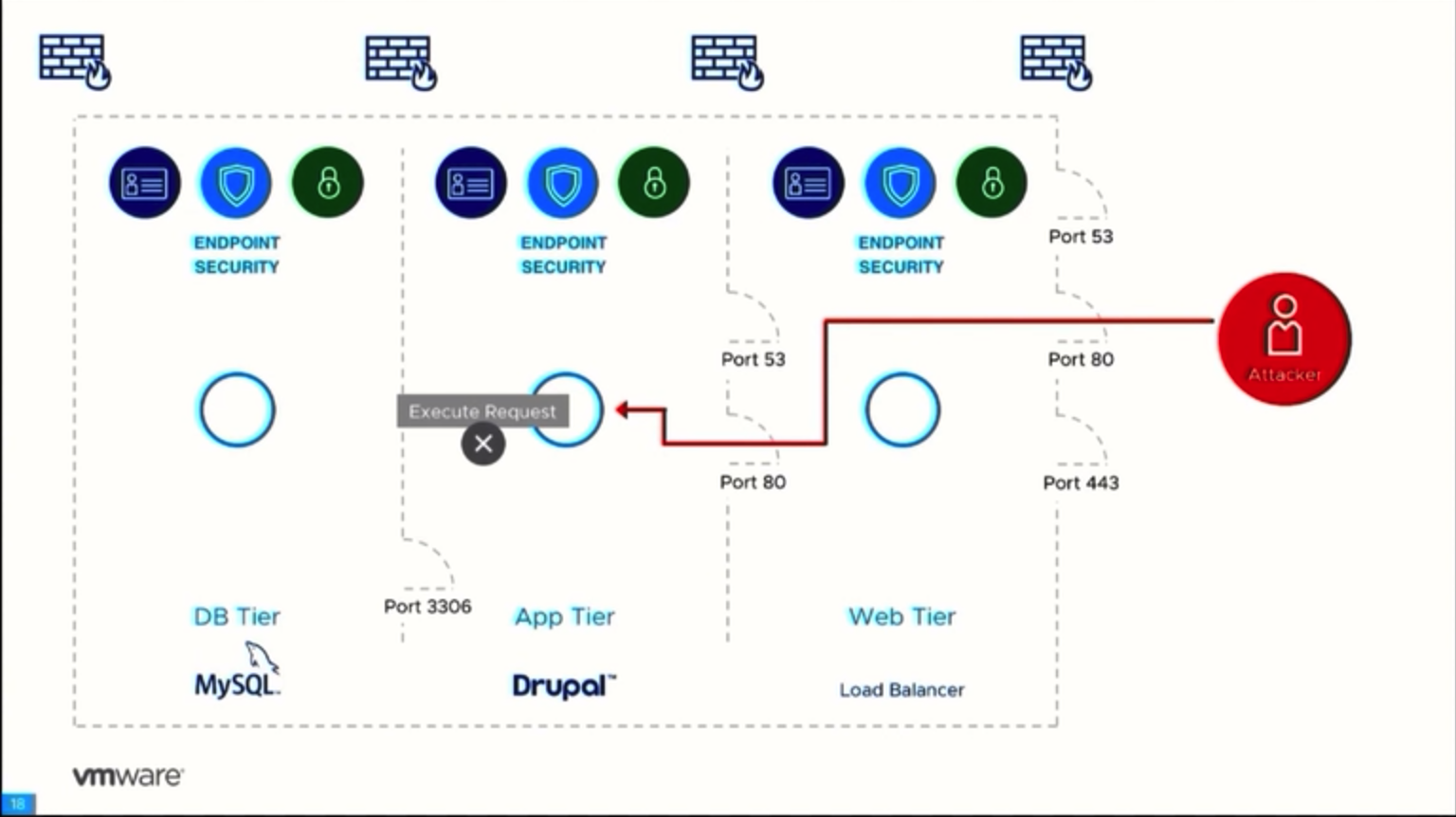
VMware Service-Defined Firewall, in its turn, employs a whole other approach to IT environment protection. The Firewall applies the Zero Trust strategy, which means that not a single one network component is deemed trustworthy, implying that any network connection can be dangerous. It runs application analysis inside the network perimeter (internal network firewalling). Service monitoring is done on hypervisor level and on level-7 of OSI model (L7 packet inspection), without involving guest OS agents.
The Firewall almost eradicates the probability of attack via the public ports. Any suspicious activity, such as gaining shell access or disabling an antivirus, will be blocked and logged.
It is also possible to retrieve security logs where all blocked queries will be listed.
Evidently, such model better on every level than multi-agent systems because in the latter cases malware can get control over these agents. Another score for VMware Service-defined Firewall is its full-software implementation. The thing is that the hardware firewalls are barely scalable. They are also difficult to manage. For instance, applications can move between servers and datacenters, bypassing the security checks while migrating from an infected server to a healthy one.
Some more materials on the Service-Defined Firewall
- The main page VMware Service-defined Firewall
- Service insertion and guest introspection
- Validation Report of the Service-Defined Firewall by Verodin
- Lab report VMware NSX Micro-Segmentation Hands-on Lab
- Enabling Zero Trust Security Through Network Virtualization And MicroSegmentation
- Micro-segmentation with Service Insertion
- YouTube channel on VMware NSX
Conclusion
VMware Service-Defined Firewall is a game changer in the world of virtualized environment security. Designed with all VMware developments in that field, the solution provides robust functionality for preventing and fighting off both internal and external attacks.