VMware has released recently their latest VMware Tools v12 packages. This release is a major release of VMware Tools because it covers some critical vulnerabilities, Guest OS product updates support and also backward compatibilities with older VMware products.
One of the first new features within VMware tools is a possibility to manage Salt Minion through guest variables. Salt Minion is able to automate, execute remote tasks and change configs.
In fact, with Salt you can execute multiple commands across thousands of systems in seconds with a single execution.
For example, you want to set up a load balancer in front of a cluster of web servers. So you want usually to setup the load balancer first, if not the traffic won’t be sent to the right direction.
Once done, you can then apply the same matching configuration consistently across the whole cluster. You can orchestrate the config application across clusters. A basic Salt implementation consists of a Salt master managing one or more Salt minions.
Salt installation is done through distribution packages where the main two are Salt-master and salt-minion. Packages exists for major Linux distributions (RedHat, Debian) or you can use a platform agnostic installation via Python package installation.
There is also a Salt Bootstrap project allowing you to use script that install Salt on any Linux/Unix platform. The script install system packages and enables salt services automatically.
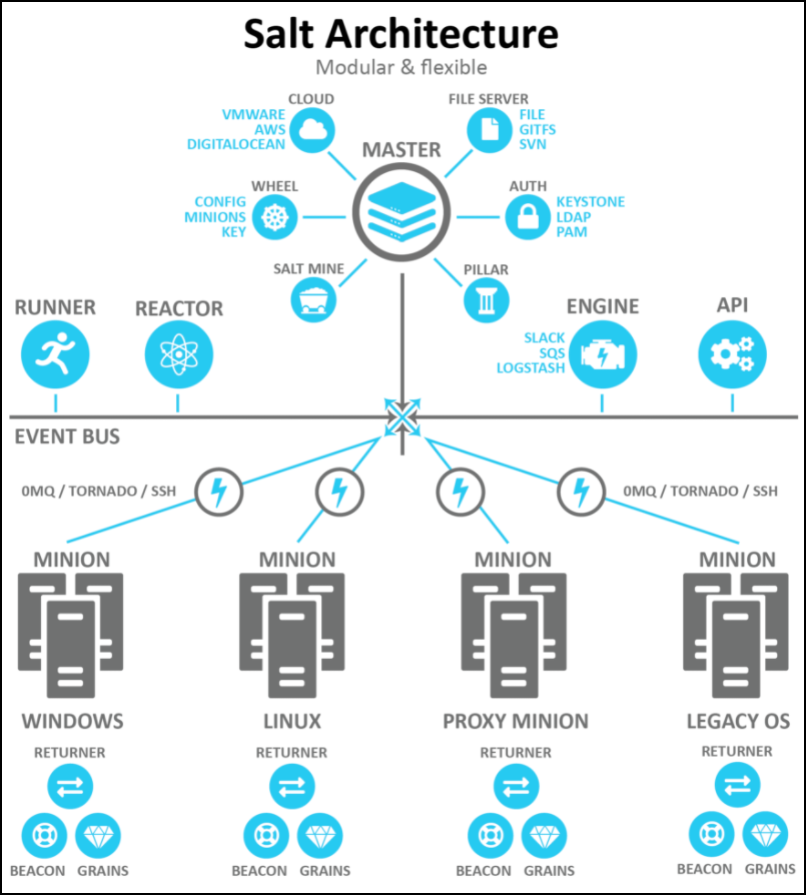
Salt Minion Architecture
Salt needs a Salt Minion to be deployed in the guest. Salt Minion specific guest variables are set on the host side and those are then read by VMware Tools inside guest. VMware Tools is able to fetch the Salt Stack bundle and spins up a Salt Minion instance inside the guest.
For Windows guests, only x64 architectures are supported, from Windows 8 and higher systems. By default, the Salt Minion feature is enabled.
What’s New in VMware Tools v12
The latest version of VMware Tools brings some innovative approach and has:
- Salt Minion – Support for managing Salt Minion through guest variables. Check out the details here – Enable Salt Minion Using VMware Tools.
- New Guest OS support – Added Windows 11 and Windows Server 2022 support.
- Latest Open SSL – OpenSSL version has been updated to 3.0.0 version.
- Containers Logs collection – Support for gathering and publishing list of containers running inside Linux guests. See Configure ContainerInfo for Linux.
- New Vulnerabilities Patches – We have a resolution of CVE-2022-22943. Check out this page at VMware to stay protected and safe from malware and ransomware – https://www.vmware.com/security/advisories/VMSA-2022-0007.html.
- Bugs resolution – For issues resolved in this release, see Resolved Issues section.
Upgrade to the latest VMware Tools v12
There is not a new way to upgrade. Just follow the typical message you’ll see within the status bar of your VM – “A newer version of Tools is available for this VM”.
With VMware vSphere, use this workflow. Log in to vCenter Server, select a host or cluster, and on the Virtual Machines tab specify the virtual machines on which to perform a VMware Tools upgrade.
The VMware Tools v12 does not come out with latest update of ESXi 7.0 U3c. It is a separate download.
On VMware ESXi hosts, for guest operating systems that do not have the necessary VMware Tools ISOs bundled, users must set up the “ProductLockerLocation” variable on all the VMware Tools ISO images to manage VMware Tools on these guests. Check the VMware Knowledge base article at https://kb.vmware.com/s/article/2004018 .
Download VMware Tools v12 from this page.
Screenshot from “In-guest” installation shows the Salt Minion components available as a default selection within the Windows Guest.
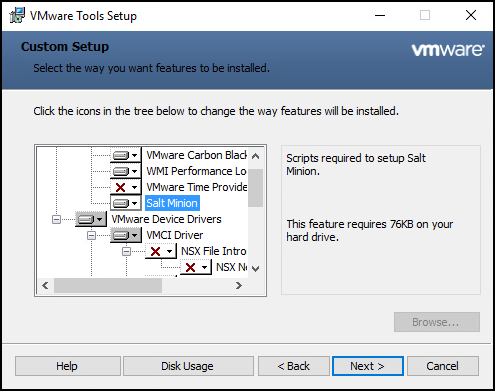
VMware Tools has default selection of Salt Minion Component
There is a detailed step-by-step on how to enable Salt Minion in Windows based guests here.
Phasing out some components in the next version of VMware Tools
This is interesting note as VMware plans to remove certain components from the next release of VMware tools. This is typically to product shift direction.
The next major release of VMware tools won’t have PVSCSI for certain Guest OS. The PVSCSI floppy images for supporting OS versions Vista, Server 2008, and Windows 7 will be removed in the next release of VMware Tools.
Also, VMXNET 2 network adapter will be removed so the users who has been using this adapter on Windows Server 2008 R2, make sure to update to VMXNET 3. This typically involves a reconfiguration of the network stack.
Typically, with this kind of migration, you’ll want to export your network config to a file, then import it once the new VMXNET3 drivers are installed.
Export your current IP settings to a text file. Use the following command:
|
1 |
<em>netsh -c interface dump > c:\\MySettings.txt</em> |
Import your IP settings and change them, just enter the following command in a Command Prompt window (CMD.EXE):
|
1 |
<em>netsh -f c:\\MyAnotherSettings.txt</em> |
Wrap Up
VMware Tools packages are essential part of the VMware vSphere infrastructure. If you run just a few VMs you can probably go and do an “in-guest” update. However, when you manage larger vSphere infrastructures, you’ll most likely want to setup a ProductLockerLocation variable and just copy the newest VMware tools images there once they are released.
With complex clustered environments with creation and configuration of dozens of VMs daily you better prepare to a possibility of automation and mass-configuration. Having your infra ready for that isn’t something I would not take seriously.
Security and ransomware protection comes even before that. Up to date systems are necessary to ensure the integrity of the whole environment. Remember that the hackers don’t attack only production systems and that’s why that even a monitoring and non-production VMs has to be updated and patched. Hackers always seeks how to enter the environment with least effort.


