Windows Sandbox is a “sandbox” application that allows you to create a secure and isolated environment from the host system so that you can run programs and files safely. Windows Sandbox is natively included in Windows 10 Professional and Windows 10 Enterprise.
Windows Sandbox architecture
This concept of sandbox is not new, but it was necessary to go through third-party software like VMWare or VirtualBox to run software in a protected environment.
When you run the Windows Sandbox, the application runs a new and independent instance of Windows 10. Any software installed in the Windows sandbox remains only in the sandbox and cannot affect the host. Once Windows Sandbox is closed, software and files are permanently deleted.
Prerequisites from Microsoft
- Windows 10 Pro, Enterprise or Education build 18305 or later (Windows Sandbox is currently not supported on Home SKUs)
- AMD64 architecture
- Virtualization capabilities enabled in BIOS
- At least 4 GB of RAM (8 GB recommended)
- At least 1 GB of free disk space (SSD recommended)
- At least two CPU cores (four cores with hyperthreading recommended)
Without additional settings, you will run the sandbox from scratch, but you can customize the sandbox with a configuration file. Windows Sandbox configuration files are formatted as XML and are associated with Sandbox via the .wsb file extension. So it is very easy to create your own configuration file, just create a text file named “myConfiguration.wsb”, then you need to populate this file. The extension file is very important, so do not forget to use the *.wsb. Now, you can easily control the following items:
- Virtualized GPU: Enable or disable the virtualized GPU.
<vGPU>value</vGPU> - Networking: Enable or disable network access within the sandbox.
<Networking>value</Networking> - Mapped folders: Share folders from the host with read or write permissions.
<MappedFolders>
<MappedFolder>
<HostFolder>path to the host folder</HostFolder>
<SandboxFolder> path to the sandbox folder</SandboxFolder>
<ReadOnly>value</ReadOnly>
</MappedFolder>
</MappedFolders> - Logon command: Execute a command when the Windows Sandbox starts.
<LogonCommand>
<Command>command to be invoked</Command>
</LogonCommand> - Audio input: Share the host’s microphone input into the sandbox.
<AudioInput>value</AudioInput> - Video input: Share the host’s webcam input into the sandbox.
<VideoInput>value</VideoInput> - Protected client: Apply additional security settings on the RDP session to the sandbox.
<ProtectedClient>value</ProtectedClient> - Printer redirection: Share printers from the host into the sandbox.
<PrinterRedirection>value</PrinterRedirection> - Clipboard redirection: Share the host clipboard within the sandbox.
<ClipboardRedirection>value</ClipboardRedirection> - Memory in MB: Assign the memory to the sandbox.
<MemoryInMB>value</MemoryInMB>
Please read the official documentation from Microsoft to know more about these items: https://docs.microsoft.com/fr-fr/windows/security/threat-protection/windows-sandbox/windows-sandbox-configure-using-wsb-file
Windows Sandbox Example
In this example, I will install the feature and configure my sandbox with a custom configuration file. This file will mount a folder located on my Windows 10 host. This folder will be mounted as read-only in my sandbox.
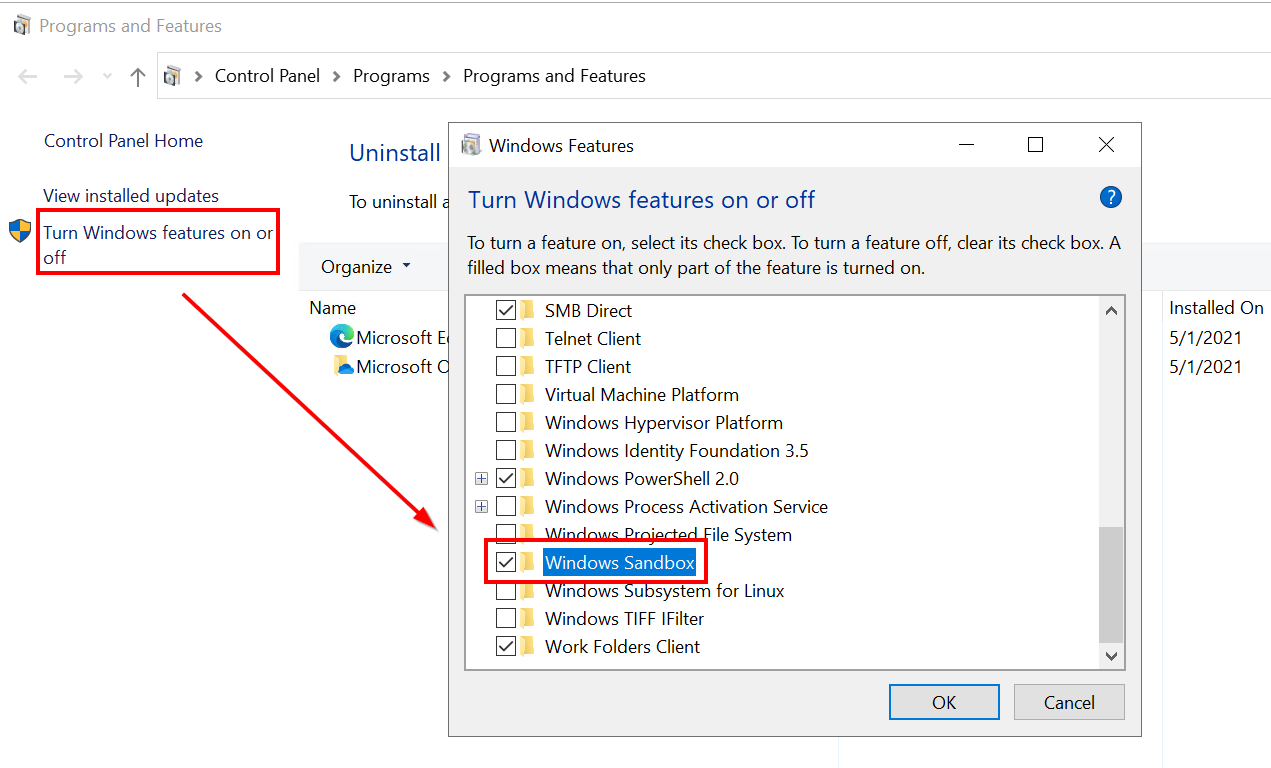
Open “Programs and Features” and select “Windows Sandbox” to install the feature.
Then, you need to restart your computer to enable the feature.
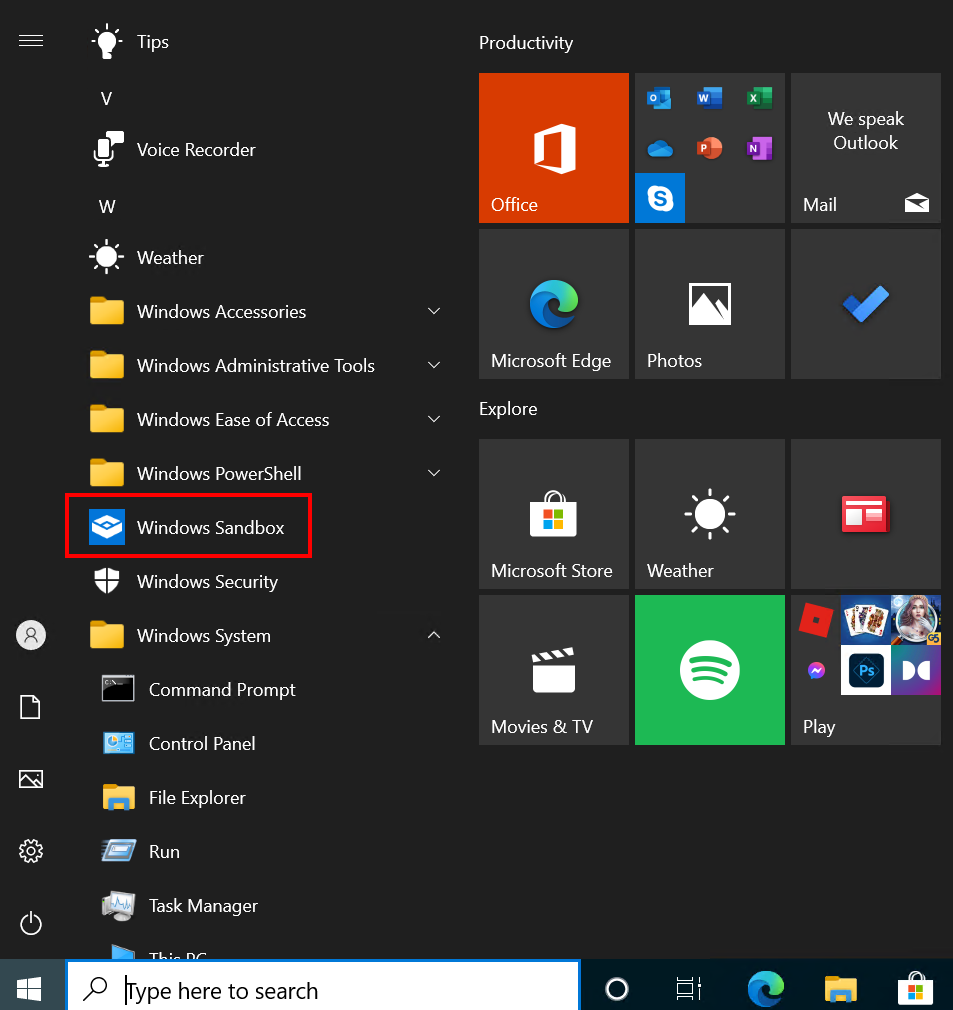
Once you have restarted your computer, open the Windows menu and search for “Windows Sandbox”
Click on the shortcut to open the sandbox without custom configuration. Wait a few seconds depending your computer performances.
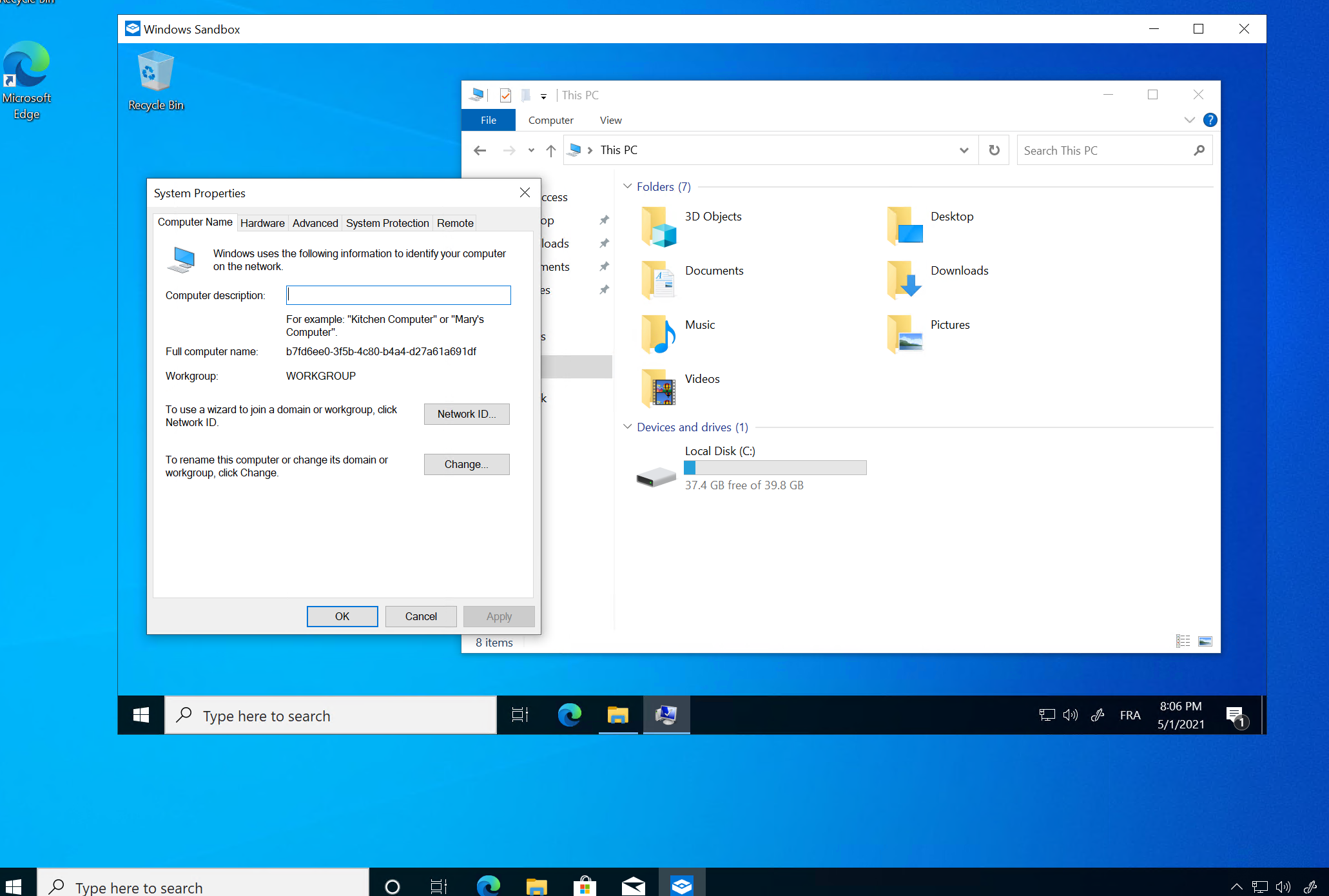
You will see that a new Window appears with a default Windows 10 installation. You can now use this sandbox to perform all the tests you want.
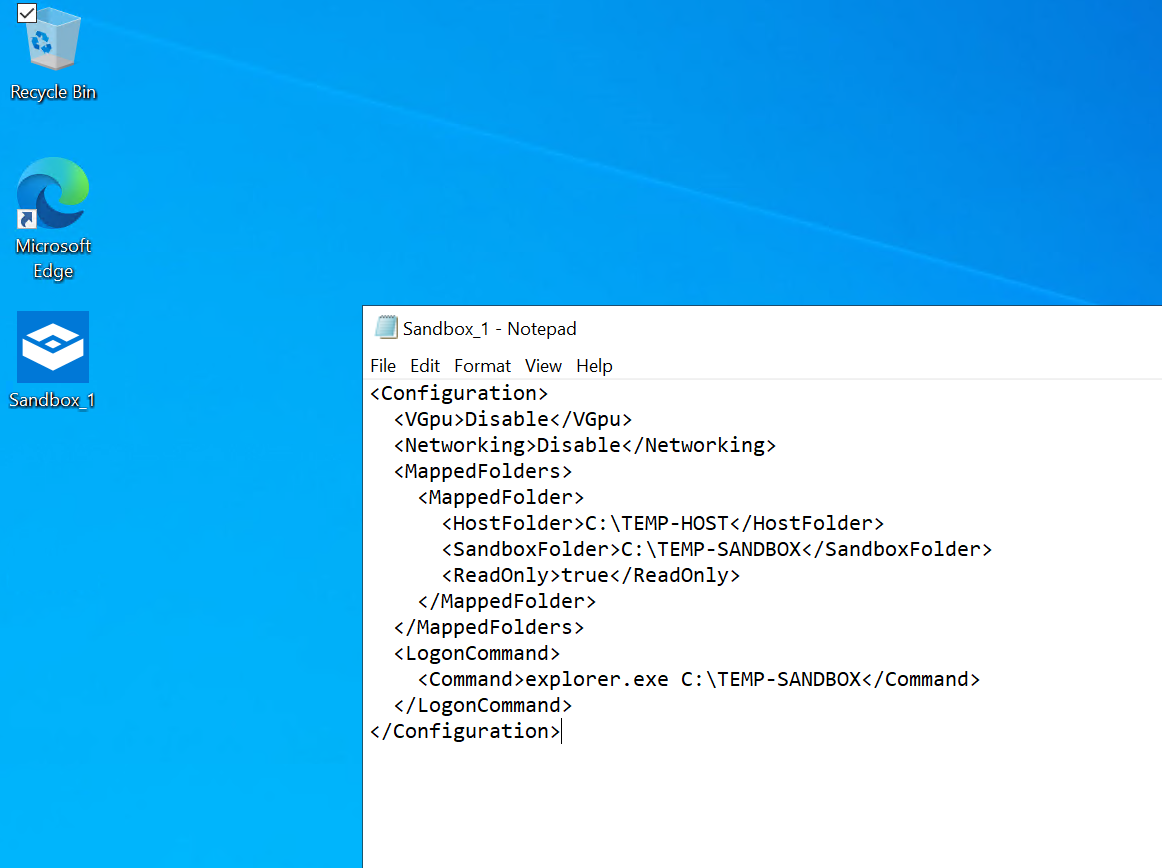
But now, you would probably need to customize your sandbox. Here is a configuration file that will map a folder from the host to the sandbox. Then, the configuration will run the “explorer.exe” process when the sandbox is started. Copy and paste the following code in notepad and save it. (do not forget the *.wsb extension file).
<Configuration>
<VGpu>Disable</VGpu>
<Networking>Disable</Networking>
<MappedFolders>
<MappedFolder>
<HostFolder>C:\TEMP-HOST</HostFolder>
<SandboxFolder>C:\TEMP-SANDBOX</SandboxFolder>
<ReadOnly>true</ReadOnly>
</MappedFolder>
</MappedFolders>
<LogonCommand>
<Command>explorer.exe C:\TEMP-SANDBOX</Command>
</LogonCommand>
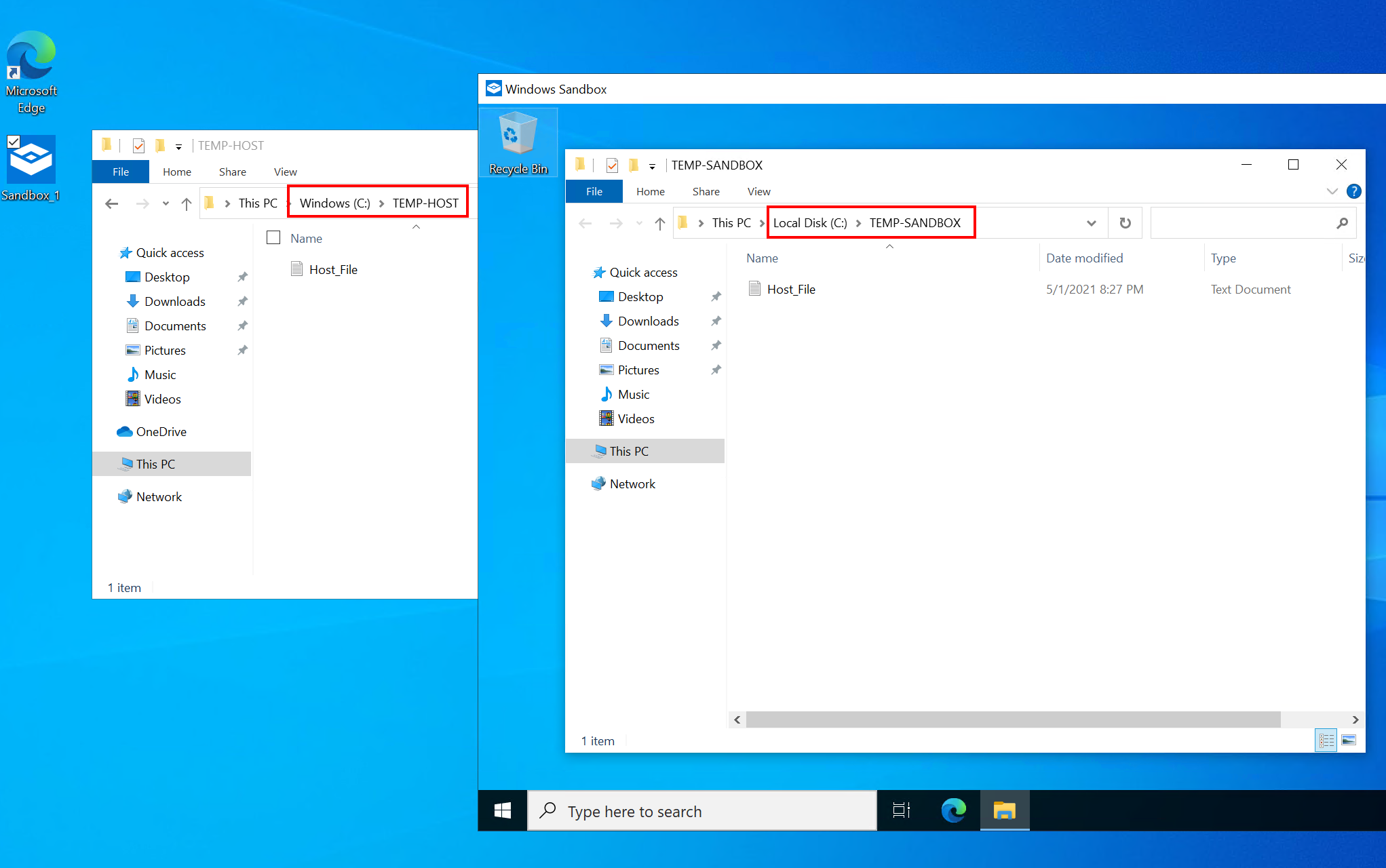
</Configuration>Then, double click on the shortcut to run the sandbox. You can confirm that ”explorer.exe” is opened when the sandbox is started and the same txt file is visible from the host and from the sandbox.
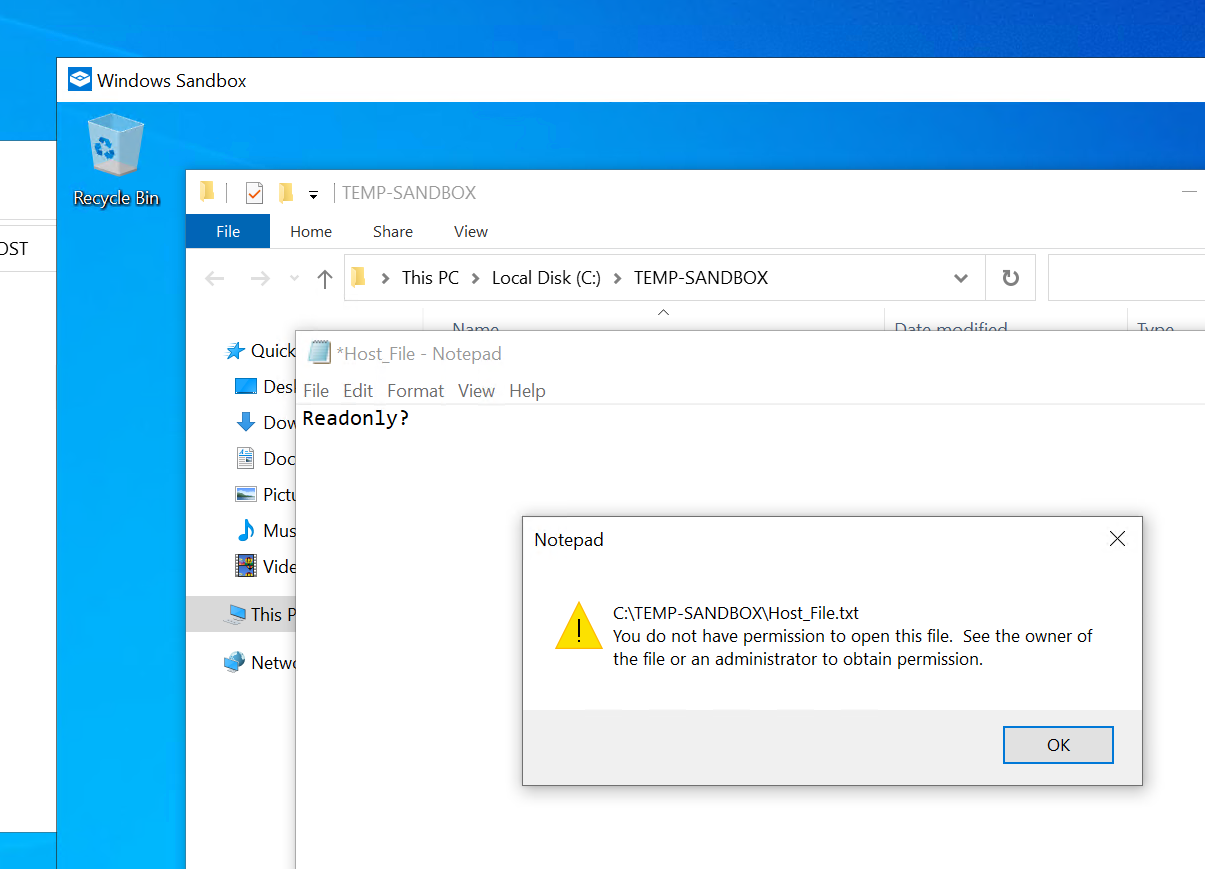
Let’s try to modify the txt file to confirm the read-only mode. To remember, if you want to disable the readonly mode, just update this line:
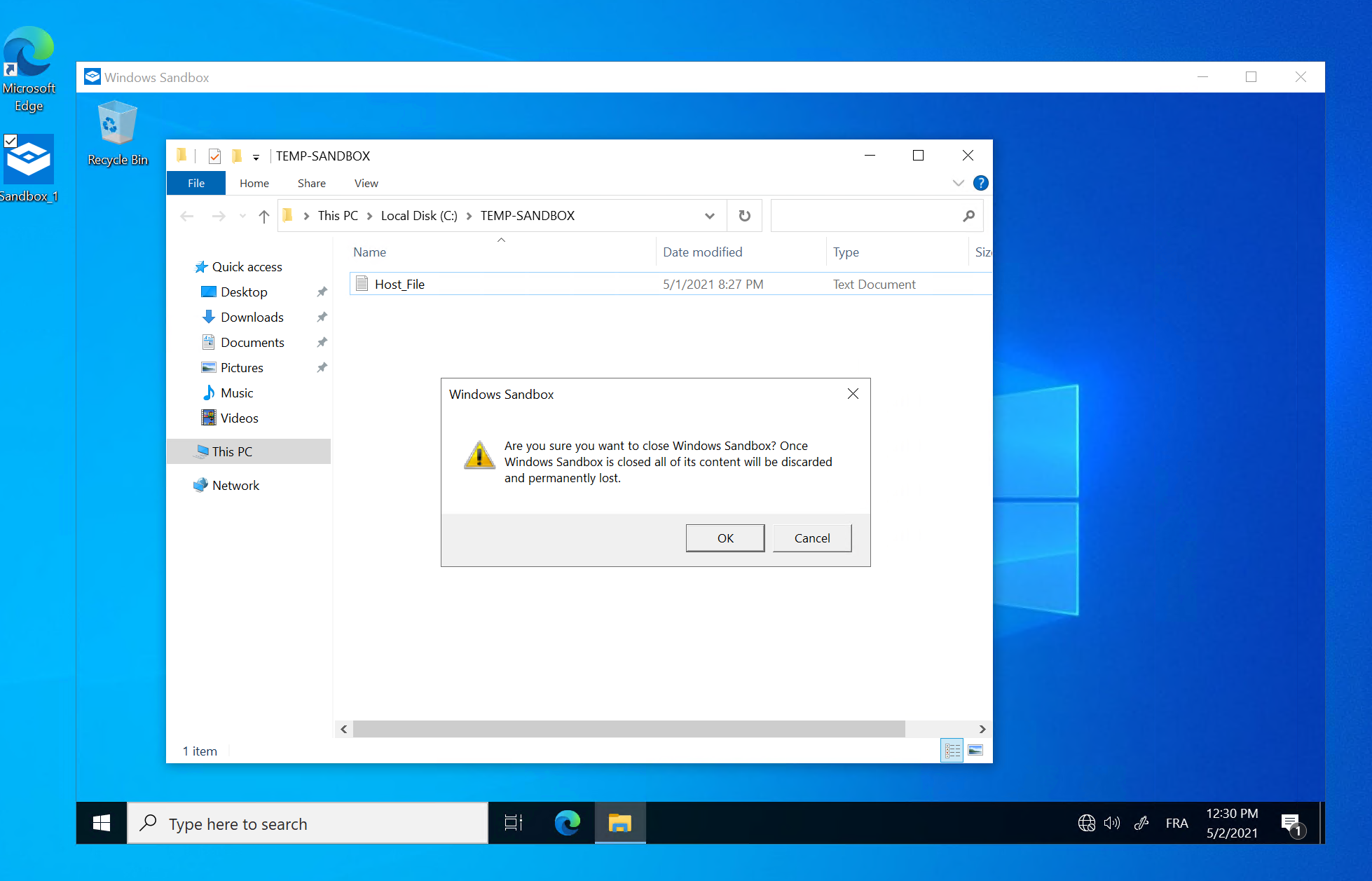
<ReadOnly>true</ReadOnly>To finish, as explained at the beginning of this article, when you will close the sandbox, you will be prompted that all the content will be deleted: