There is no question that security is one of the most important objectives in 2024 and beyond. High-profile cyberattacks in the news emphasize that security is front and center for all organizations today, large or small. Windows Server is still a core technology for many businesses worldwide. What are Windows Server security best practices in 2024? Let’s look at best practices moving forward this year and beyond.
Secure hybrid configuration and Azure Arc-enabled servers
Microsoft Azure-Arc is an excellent solution that allows the on-premises or third-party cloud-hosted Windows servers to be brought under the Azure control plane. It is essentially an agent installed on your Windows Servers that allows you to integrate the Windows Server environment with your Azure portal.
It essentially allows your Windows Server to become a native citizen of your Azure environment, even though it isn’t housed in Azure. With this capability, security considerations must be made. How can you secure your Azure Arc-enabled servers?
Onboard your Azure Arc-enabled servers to Microsoft Defender for Cloud
Onboard your Azure Arc-enabled servers into Microsoft Defender for Cloud
- You will need to install the Log Analytics agent on the Arc-enabled server so the hybrid server will appear in Defender for Cloud
- You won’t be able to do this with the auto-deploy tools since Cloud Log Analytics doesn’t support these with Azure Arc-enabled server
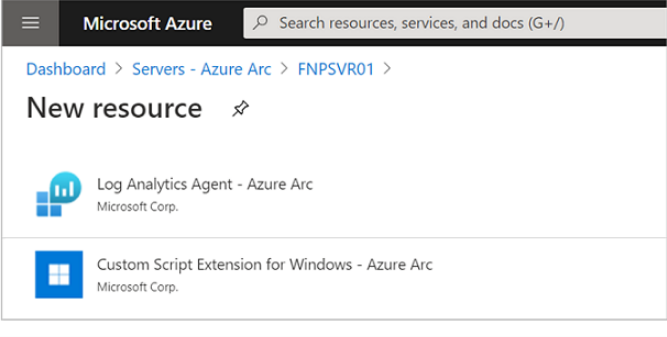
Enable the Log Analytics VM extension from the Azure portal.
You can do this from the Azure Portal > Servers – Azure Arc > Extensions > Add.
Adding a the Log Analytics Agent to the Azure Arc-enabled agent
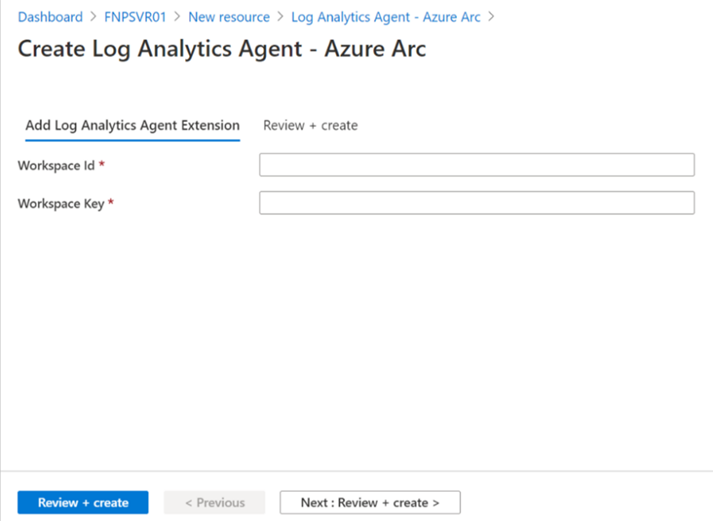
Next, just provide your Workspace ID and primary key.
Provide your workspace ID and primary key
Secure your Azure Arc-enabled servers with Microsoft Defender for Servers
To secure your Azure Arc-enabled servers, you can next enroll them in Microsoft Defender for Servers. It provides threat detection and enhanced security features for even more protection deeper protection. The features include file integrity monitoring, adaptive application controls, fileless security alerts, integrated Qualys vulnerability scanner, and others. It is one of the enhanced security features of Microsoft Defender for Cloud.
This module also includes Microsoft Defender for Endpoint, which works together to provide a comprehensive solution for EDR capabilities. When an alert is triggered, you will see this in Defender for Cloud. From Defender for Cloud, you can take a look at the Defender for Endpoint console and investigate the event leading up to the alert.
Threat intelligence for Azure Arc-enabled Servers with Microsoft Sentinel
Microsoft Sentinel is a SIEM and SOAR solution that is especially suited for hybrid and multi-cloud environments. It gives admins a single-pane-of-glass to detect attacks, perform proactive hunting of threats, and automate threat response.
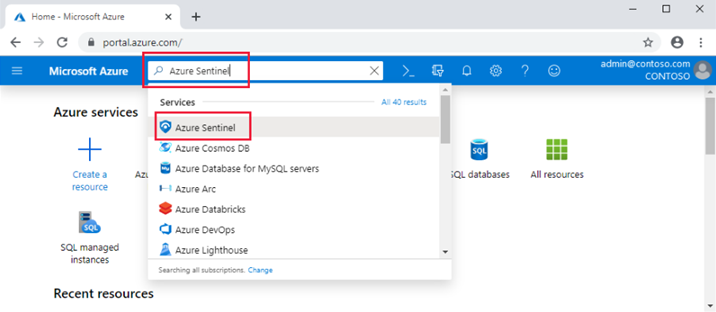
Microsoft Sentinel can be enabled on the Log Analytics Workspace. First, log into your Azure Portal and search for Microsoft Sentinel. Click Azure Sentinel.
Navigate to Microsoft Sentinel
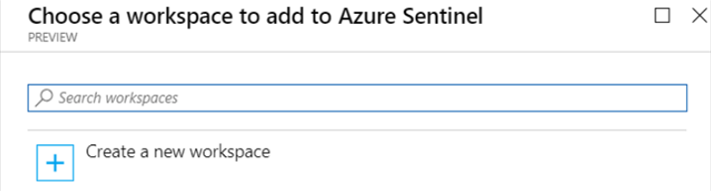
You will need to select the workspace to which the Azure arc-enabled server is connected. Then select Add Microsoft Sentinel.
Choosing or creating a new workspace
After you have connected your Arc-enabled servers, you will see data streaming into Microsoft Sentinel.
Secure DNS Client over HTTPS (DoH) in Windows Server 2022
One of the security advancements starting with Windows Server 2022 is DNS -over-HTTPS (DoH). When you enable DoH, DNS queries between the Windows Server 2022 host and a DNS server are secured using HTTPS. In contrast, in legacy versions of Windows Server, DNS queries are sent in plain text. An encrypted connection protects DNS queries from interception by an attacker or any third party.
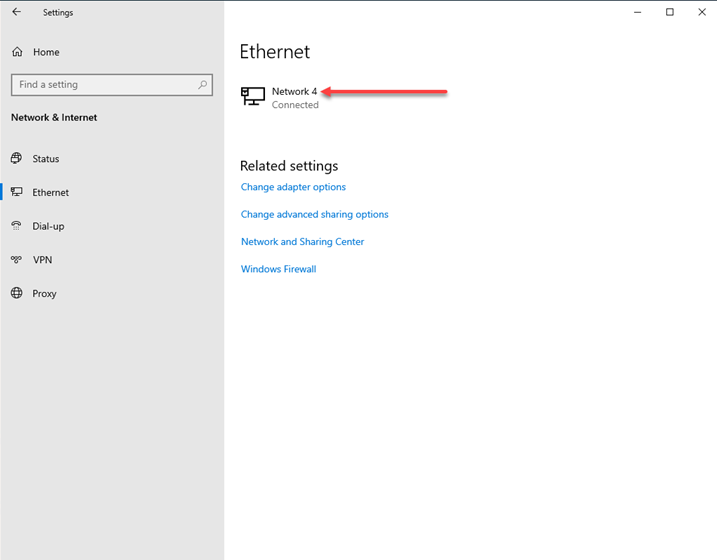
To enable DoH, navigate to your Network & Internet settings from the Windows Settings Control panel. Click the network connection you want to edit.
Editing your network connection
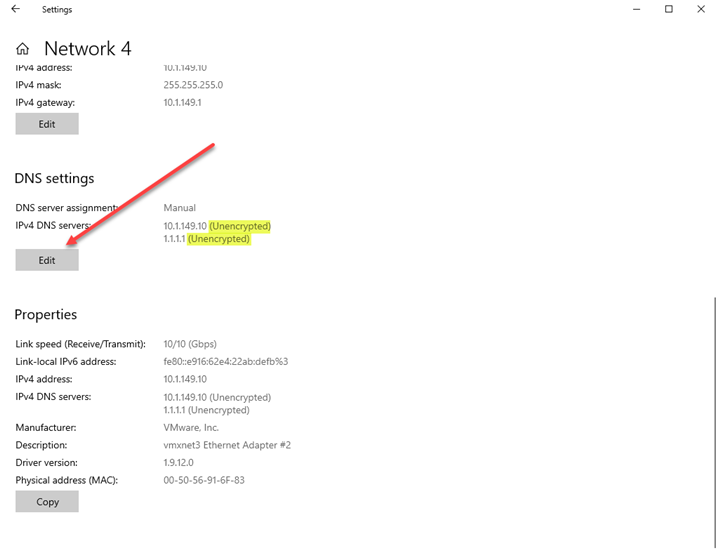
Next, scroll down to the DNS settings and click Edit. You will notice next to the DNS servers configured, we see (Unencrypted).
Editing the DNS server settings
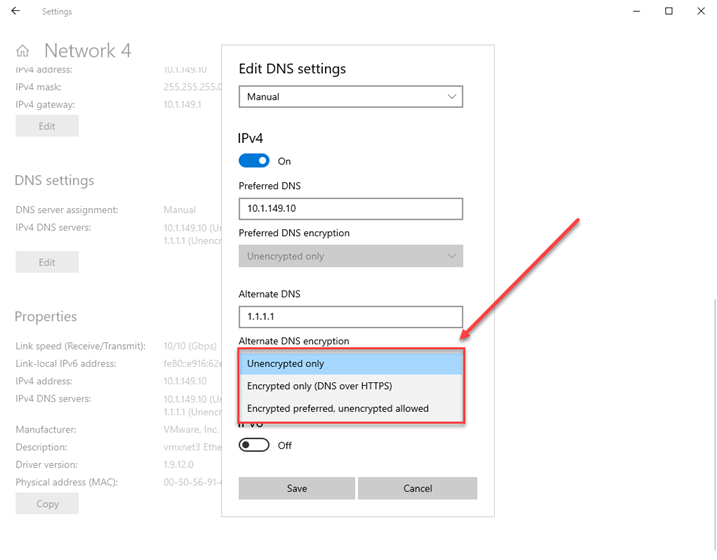
Finally, in the dropdown menu, we can set the DNS encryption. The choices include:
- Unencrypted only
- Encrypted only (DNS over HTTPS)
- Encrypted preferred, unencrypted allowed
Choosing the Encryption settings for DNS servers in Windows Server 2022
File sharing using SMB 3 protocol
You have likely noticed that SMB 1 is being deprecated across the board, and you shouldn’t be using it any longer with security in mind. SMB is the network file-sharing protocol that has long been used in the data center for applications or users to access files and other resources at a remote server location.
SMB is also used in server technologies like Storage Spaces Direct (S2D), Storage Replica, and others. SMB 3 is actually not a new instalment in Windows Server, as it has been around since Windows Server 2012. However, Microsoft has tweaked the implementation with each new version of Windows Server, including new features and capabilities.
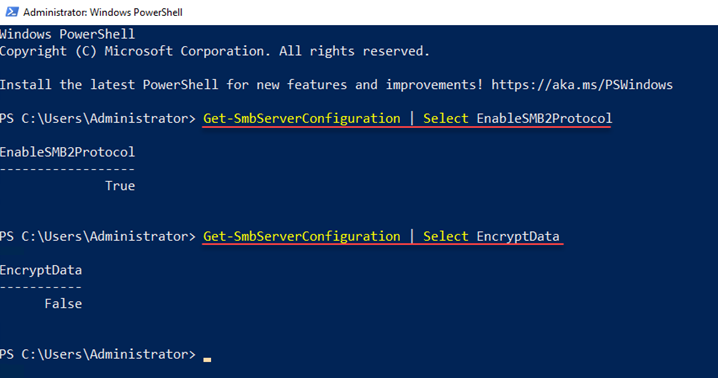
You will notice that SMB 3 is enabled along with SMB 2. This is the reason we are checking SMB 2 Protocol. You can use PowerShell to check if SMB 3 is enabled on a server using the PowerShell cmdlets.
##Get the status of SMB3 along with SMB 2
Get-SmbServerConfiguration | Select EnableSMB2Protocol
##See if encryption is enabled
Get-SmbServerConfiguration | Select EncryptData
##To enable SMB 2 and SMB 3
Set-SmbServerConfiguration –EnableSMB2Protocol $trueChecking the SMB 2 and SMB 3
Use Secured-core Server
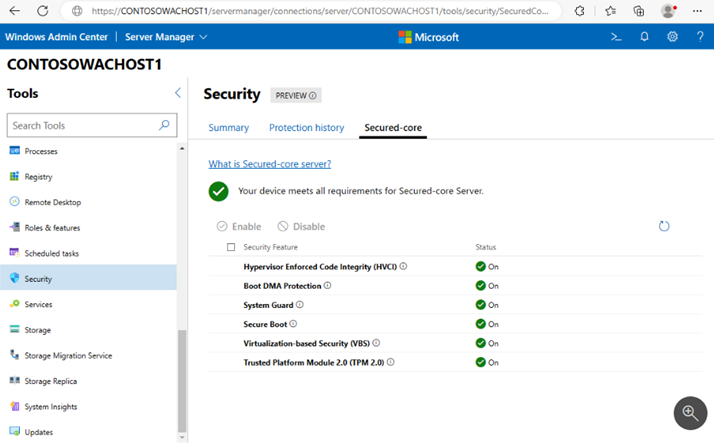
One of the other excellent security capabilities of modern Windows Servers is called Secured-core Server. Using technologies like TPM 2.0 and virtualization-based security, admins can quickly implement a set of recommended security best practices.
These features, capabilities, and configurations are exposed using Windows Admin Center. The requirements for Secure-core server include:
- Secure Boot
- Trusted Platform Module (TPM) 2.0
- System firmware must meet preboot DMA protection requirements and set appropriate flags in ACPI tables to opt into and enable Kernel DMA Protection.
- A processor with support for:
- Virtualization extensions
- Input/Output Memory Management Unit (IOMMU)
- Dynamic Root of Trust for Measurement (DRTM)
- Transparent Secure Memory Encryption is also required for AMD-based systems
In Windows Admin Center, these features are presented with a “green check” if the capabilities are found an enabled.
- Hypervisor-enforced Code Integrity (HVCI)
- Boot DMA protection
- System Guard
- Secure Boot
- Virtualization-based Security (VBS)
- Trusted Platform Module 2.0 (TPM 2.0)
Viewing Secured-core Server activation in Windows Admin Center
Wrapping up Windows Server hybrid security in 2024
Security remains a focal point for organizations and IT personnel in general. Modern versions of Windows Server contain many great features that provide modern security protections against many attack vectors. Microsoft has also engineered hybrid security solutions that integrate with Microsoft Azure (Entra) for even more modern security features. It allows you to extend your on-premises Windows servers to Microsoft Azure to benefit from Microsoft Defender for Cloud and Microsoft Defender for Servers to enable features like Microsoft Sentinel.
Modern Windows Server security is like the layers of an onion that provide numerous layers of protection against various attacks and security vulnerabilities. By using all of the features together, admins can create an extremely secure Windows Server environment that can withstand and be resilient against many attacks carried out by threat actors.
Keep in mind the security tools and capabilities highlighted in the post should be used in conjunction with basic security best practices and are not a replacement for good security hygiene all the way around, like role-based access, least privilege principles, strong passwords, MFA, and many others.